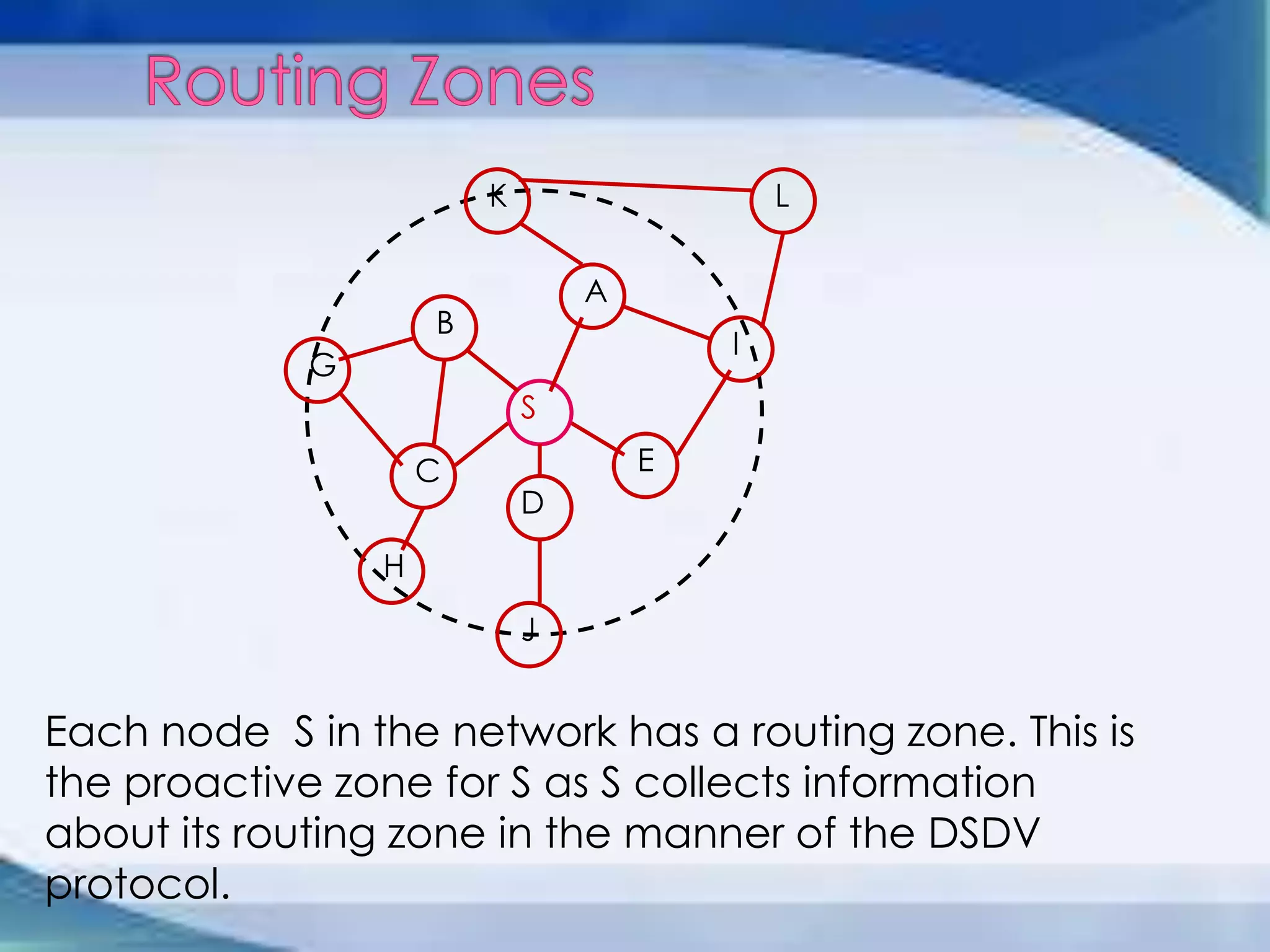
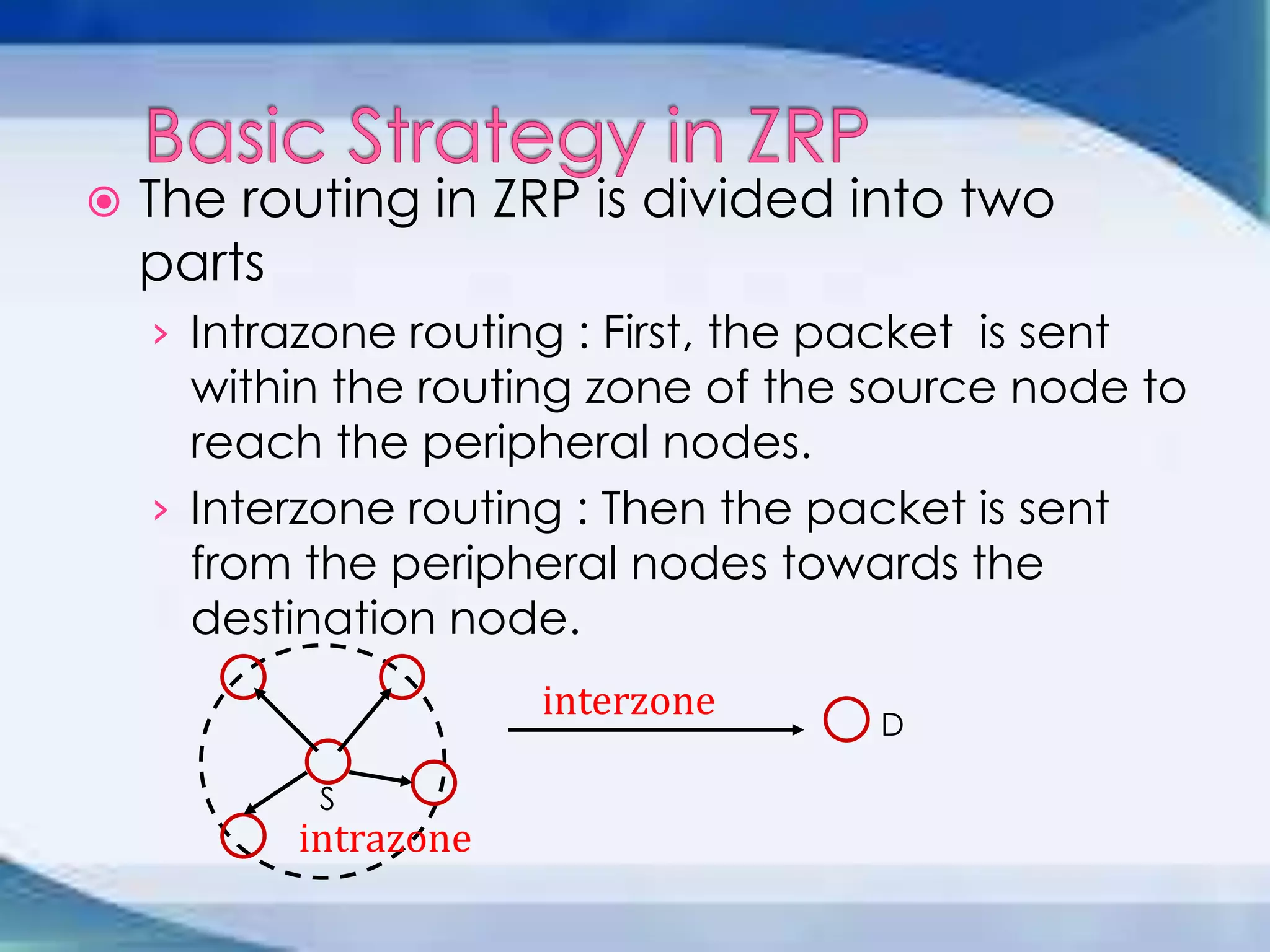
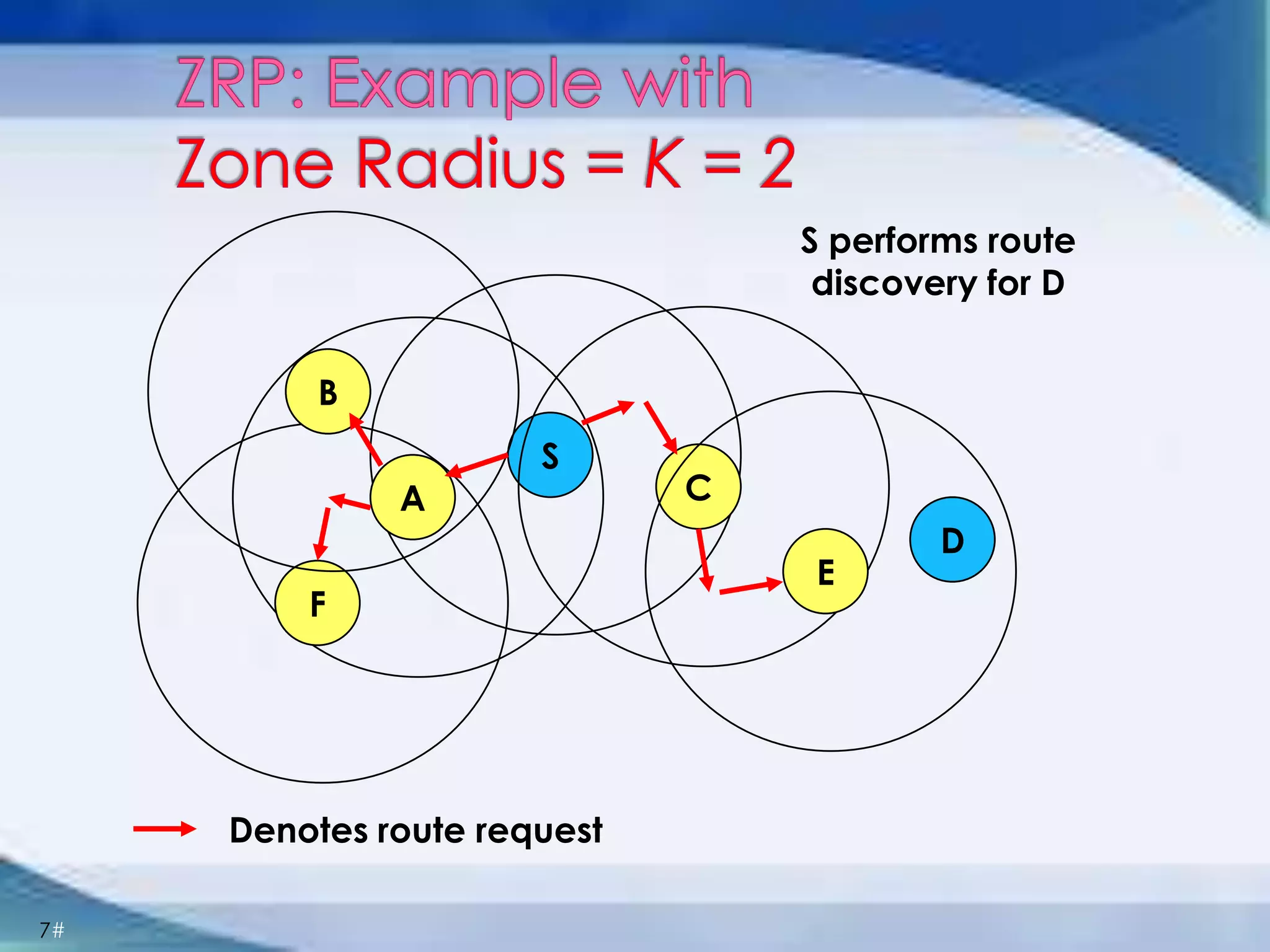
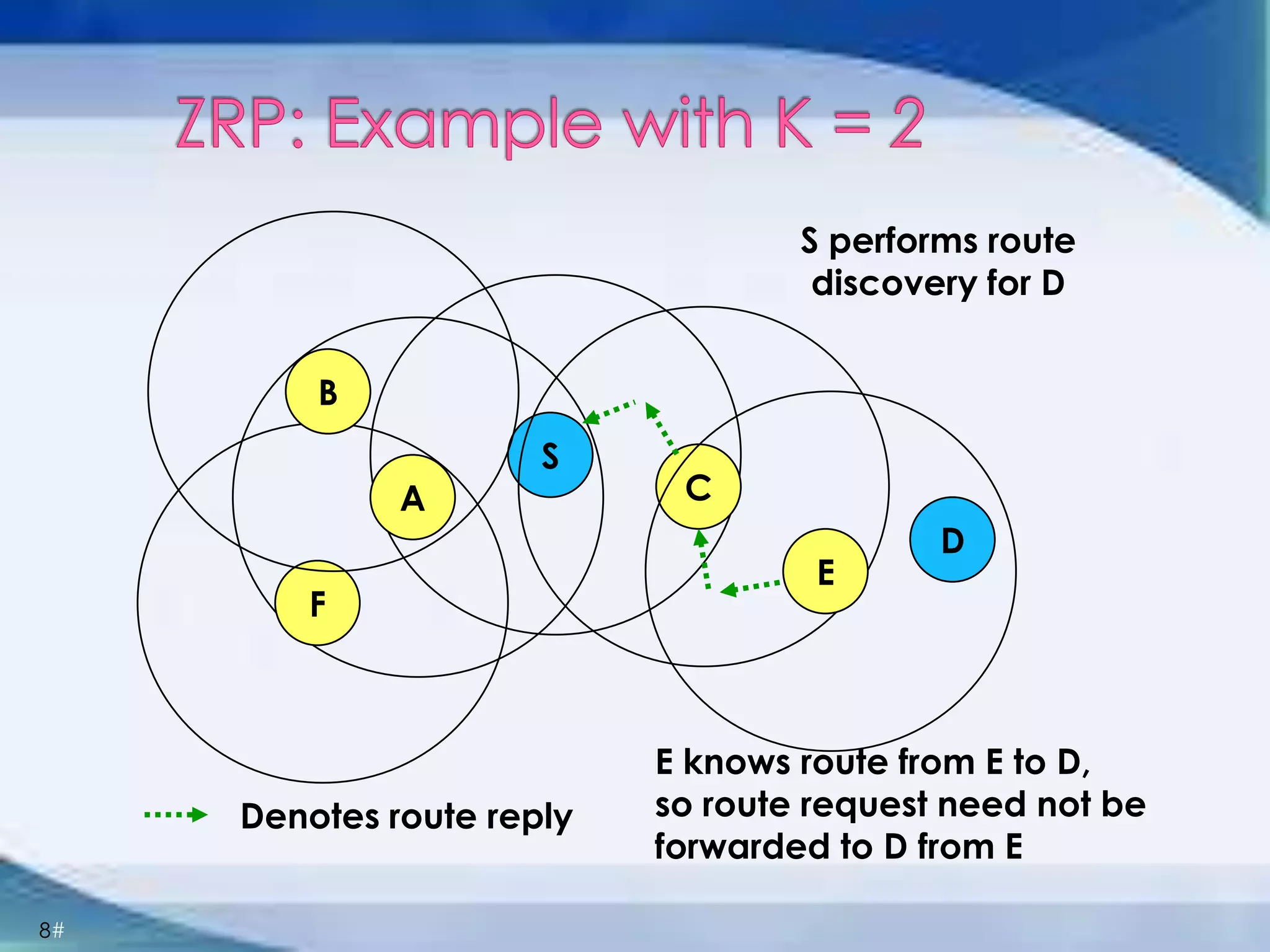
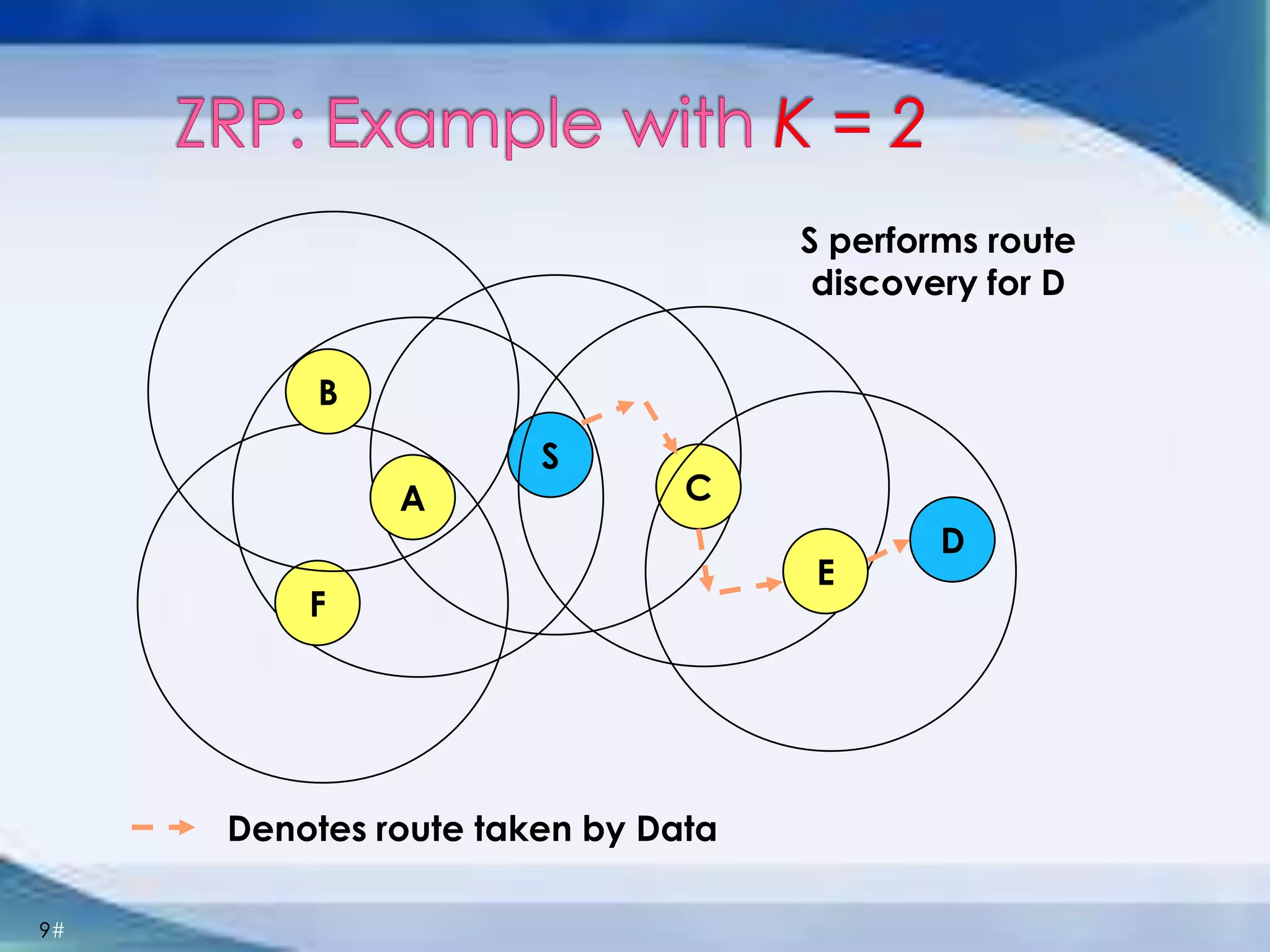
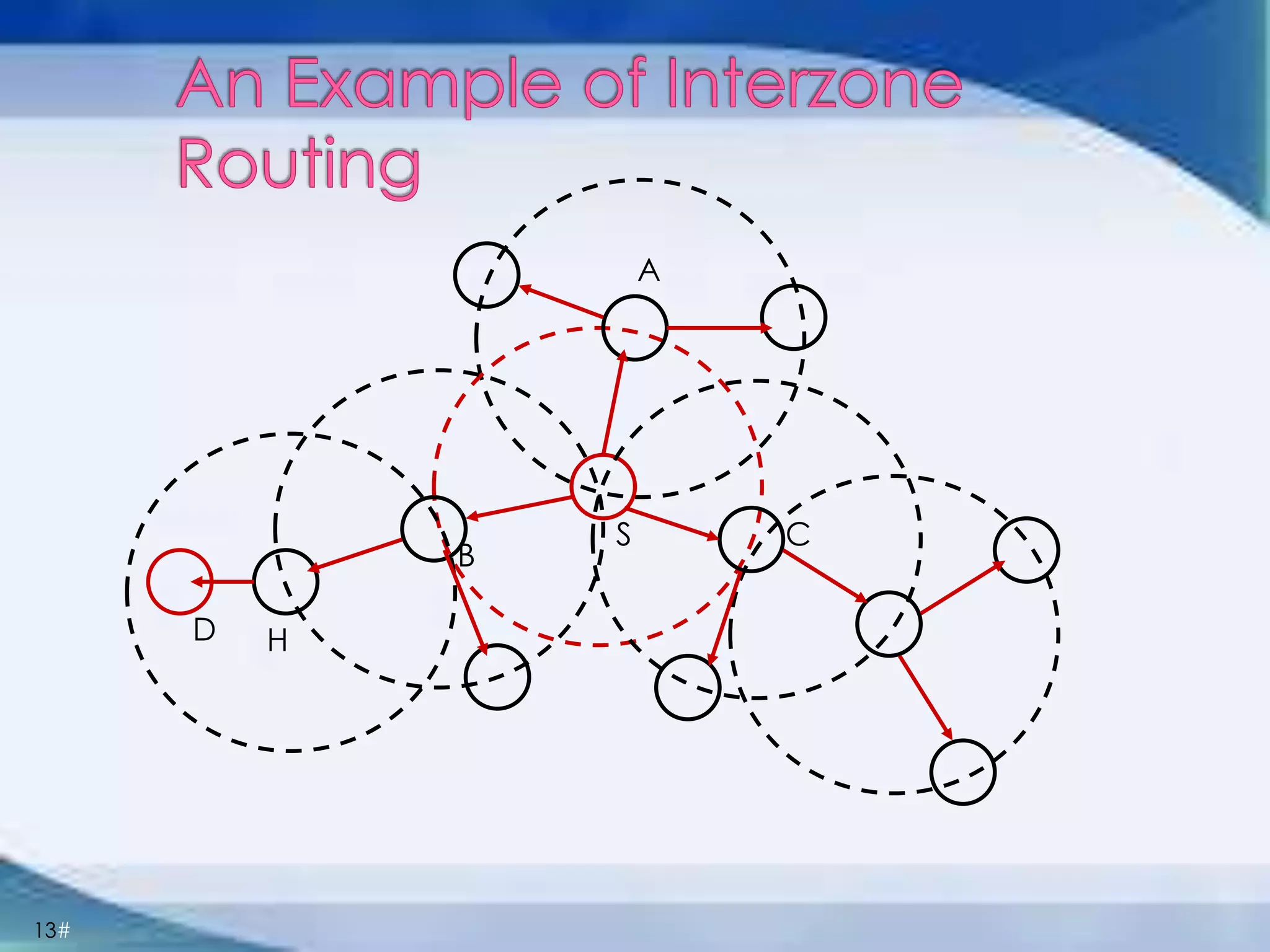
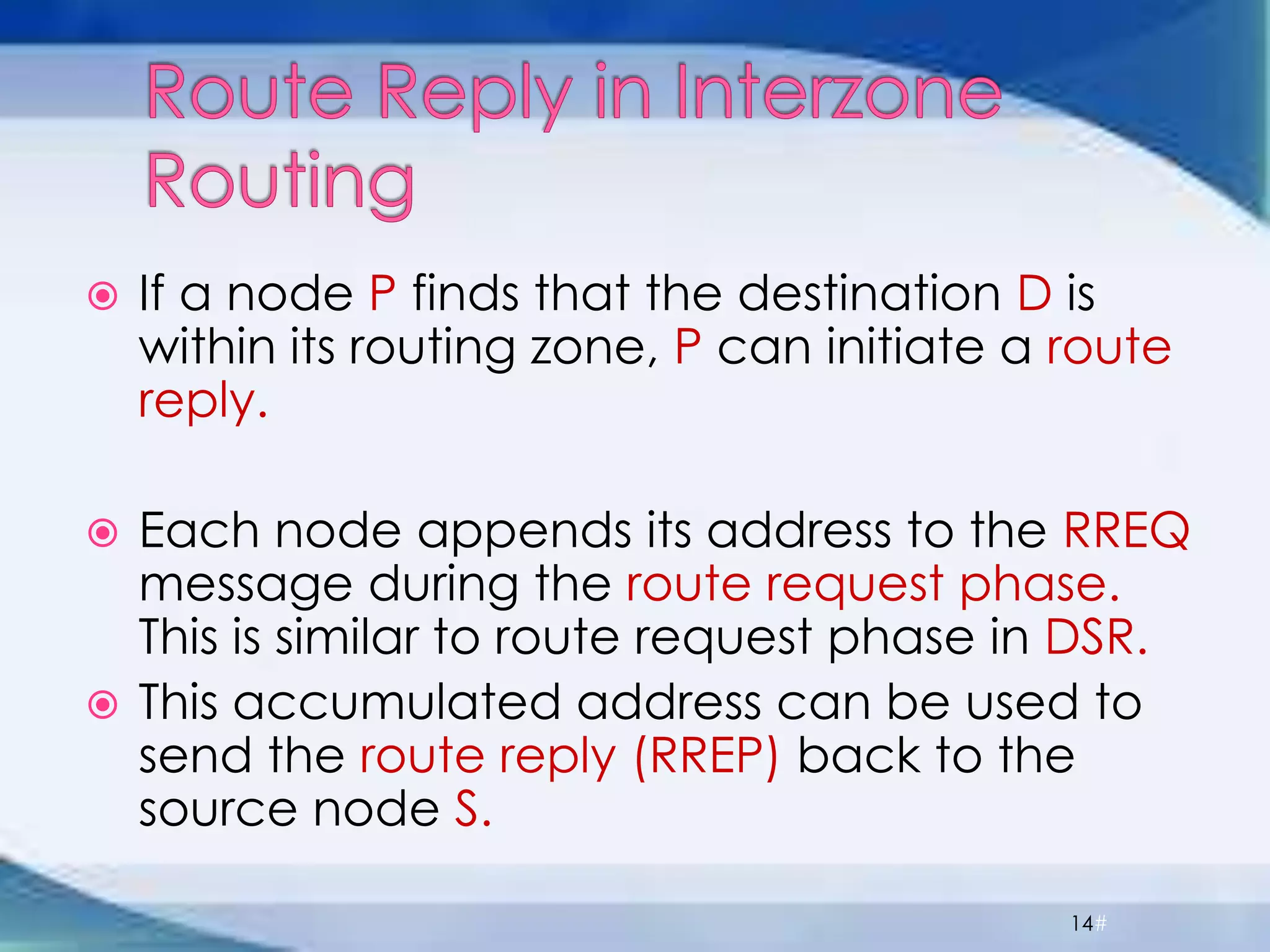
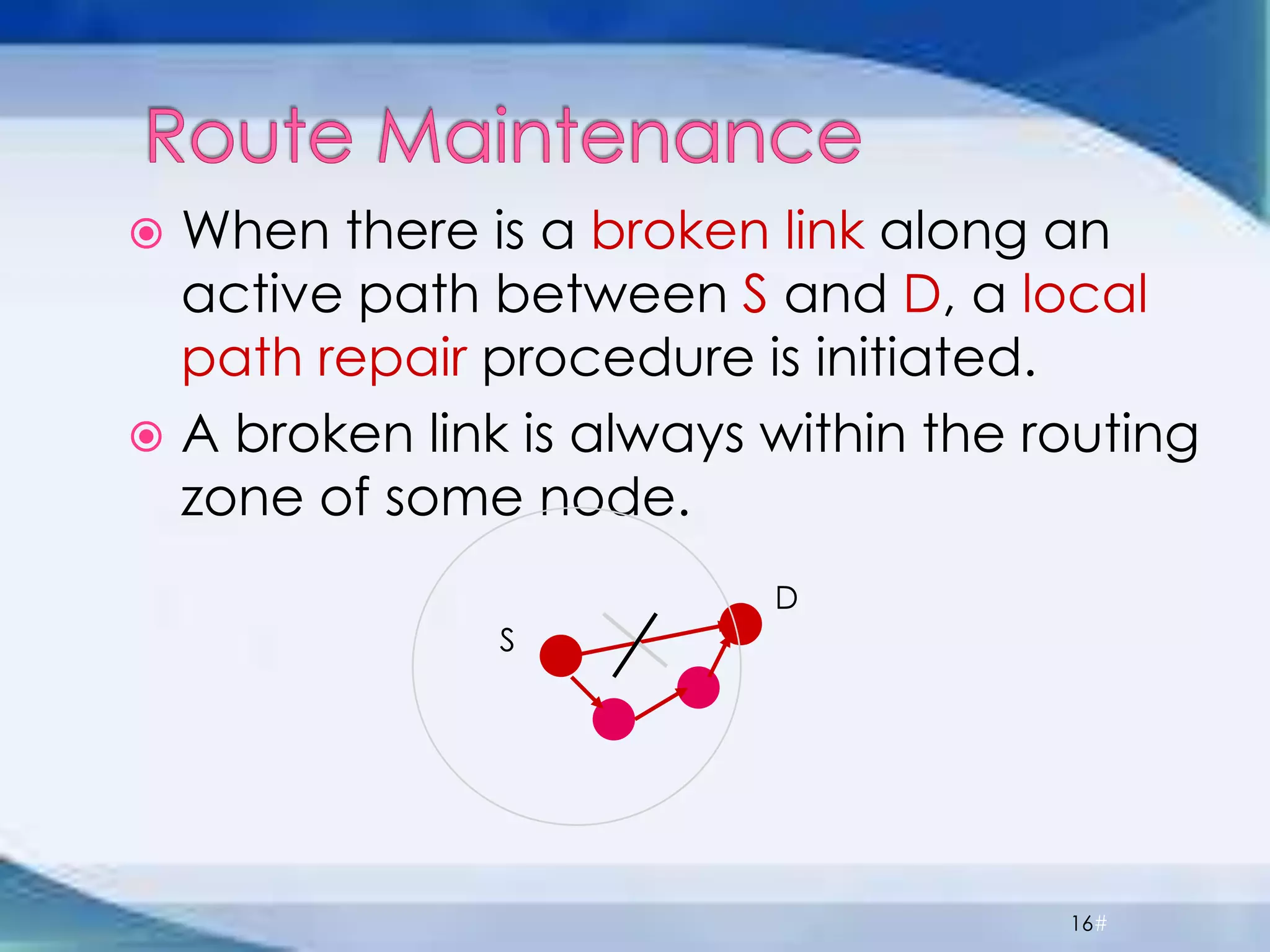
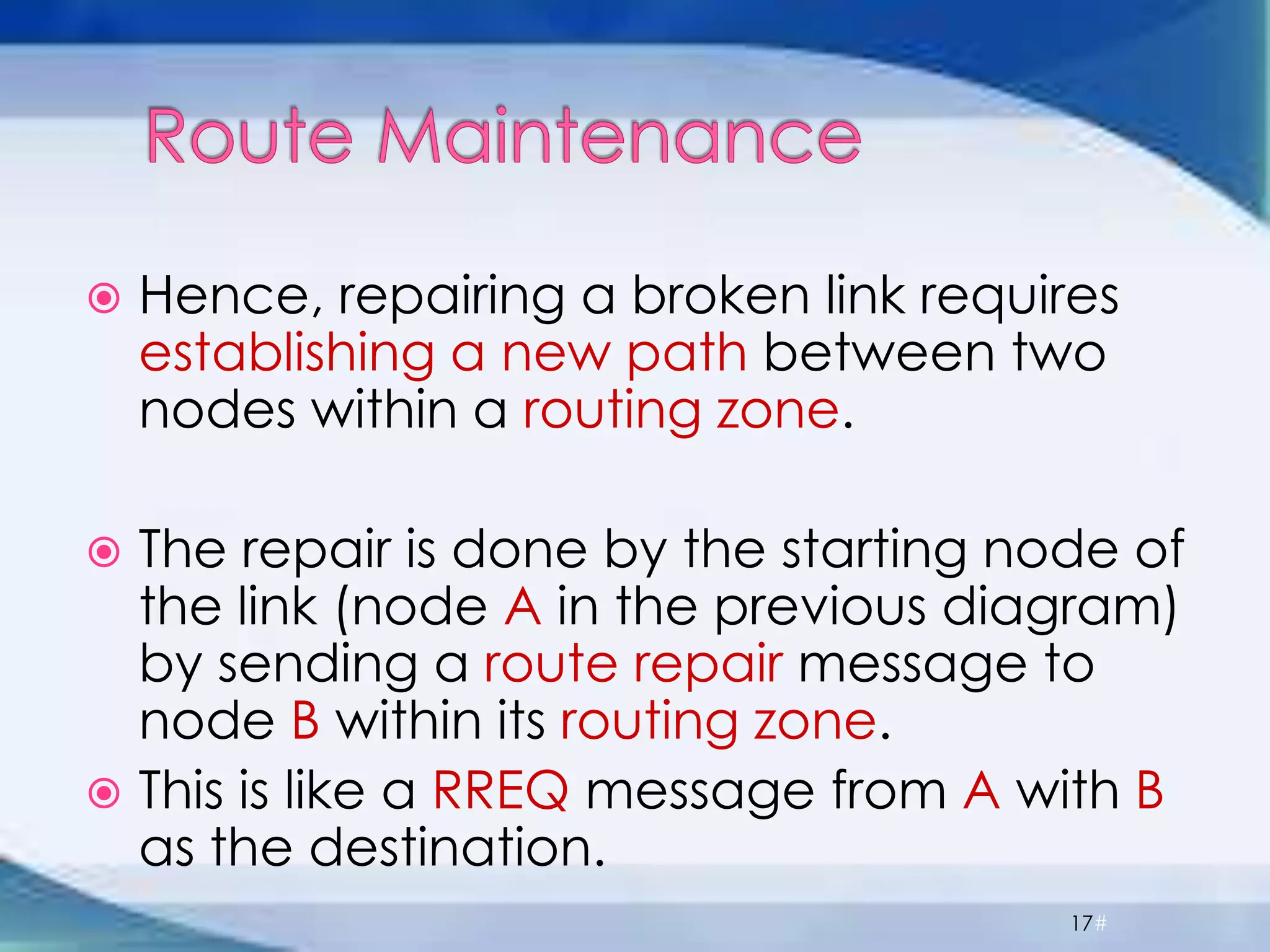
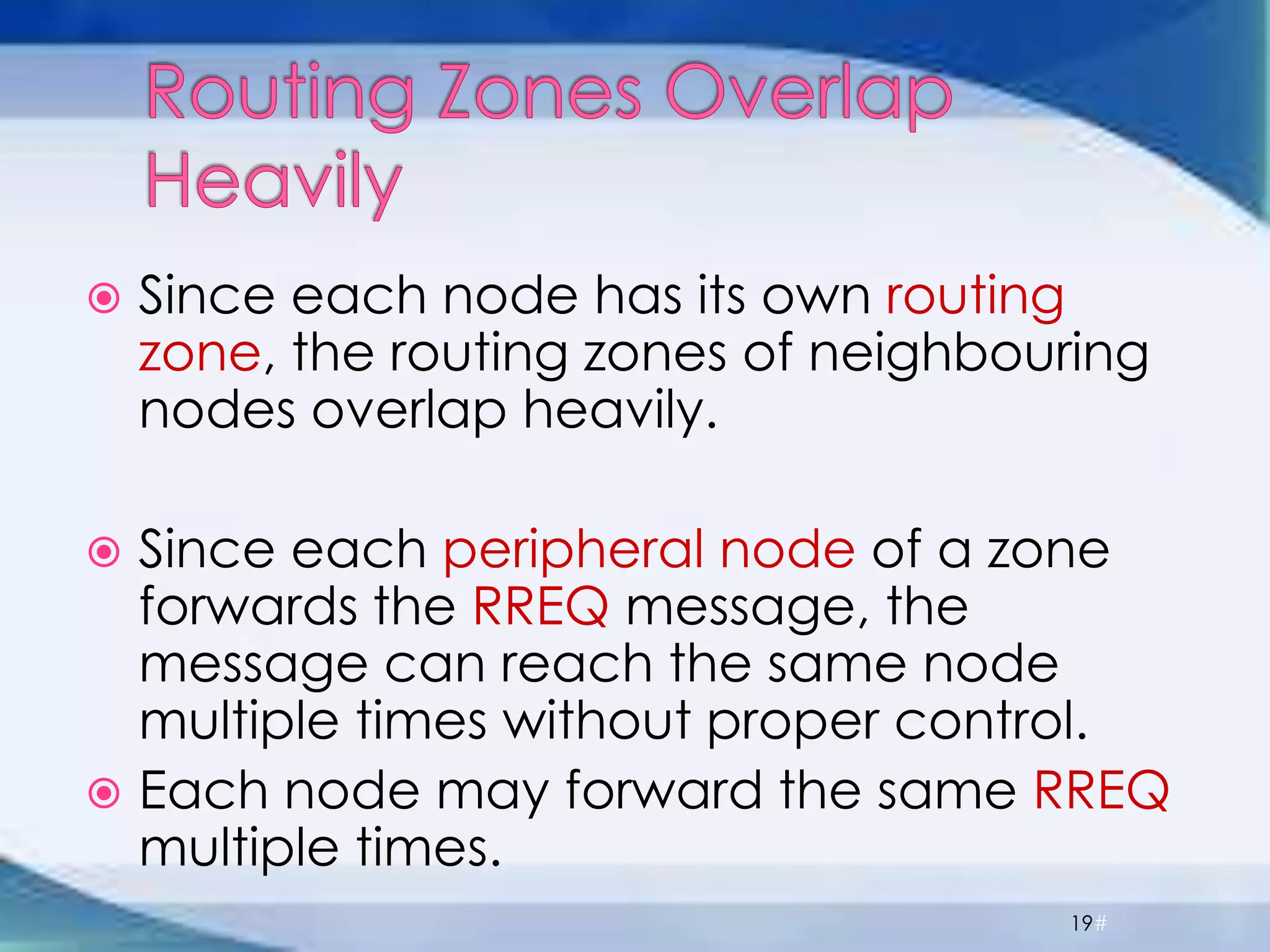
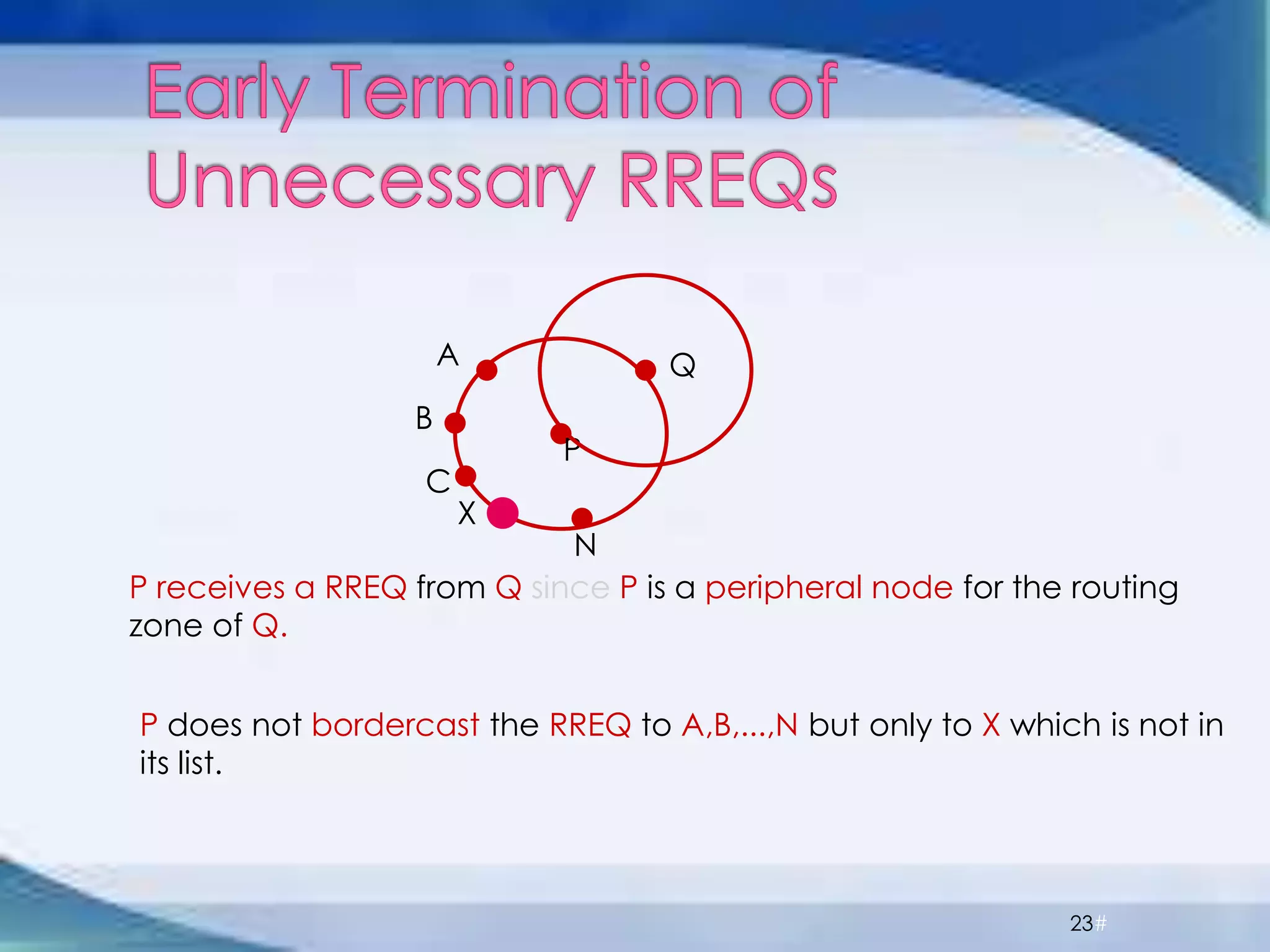
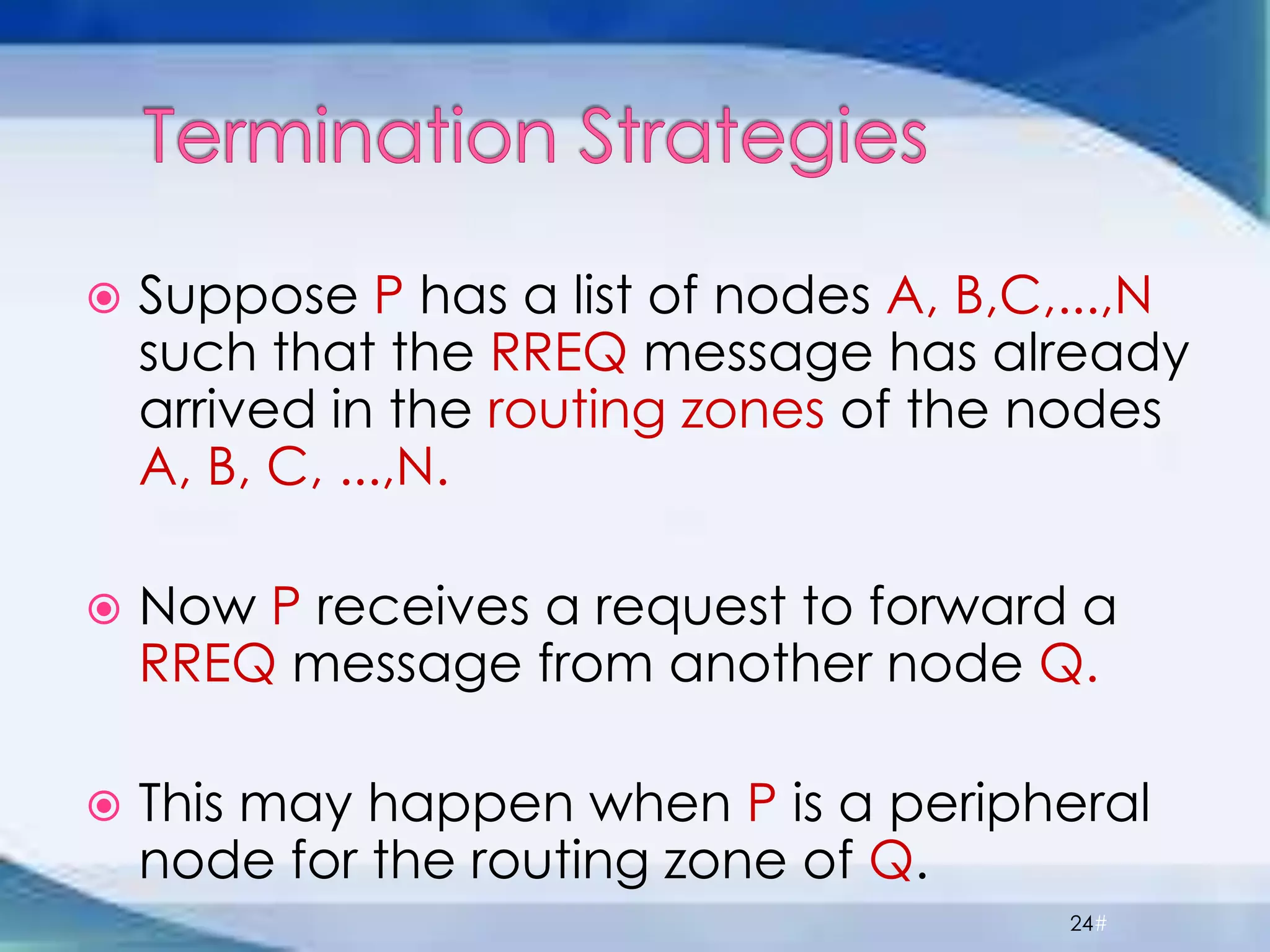
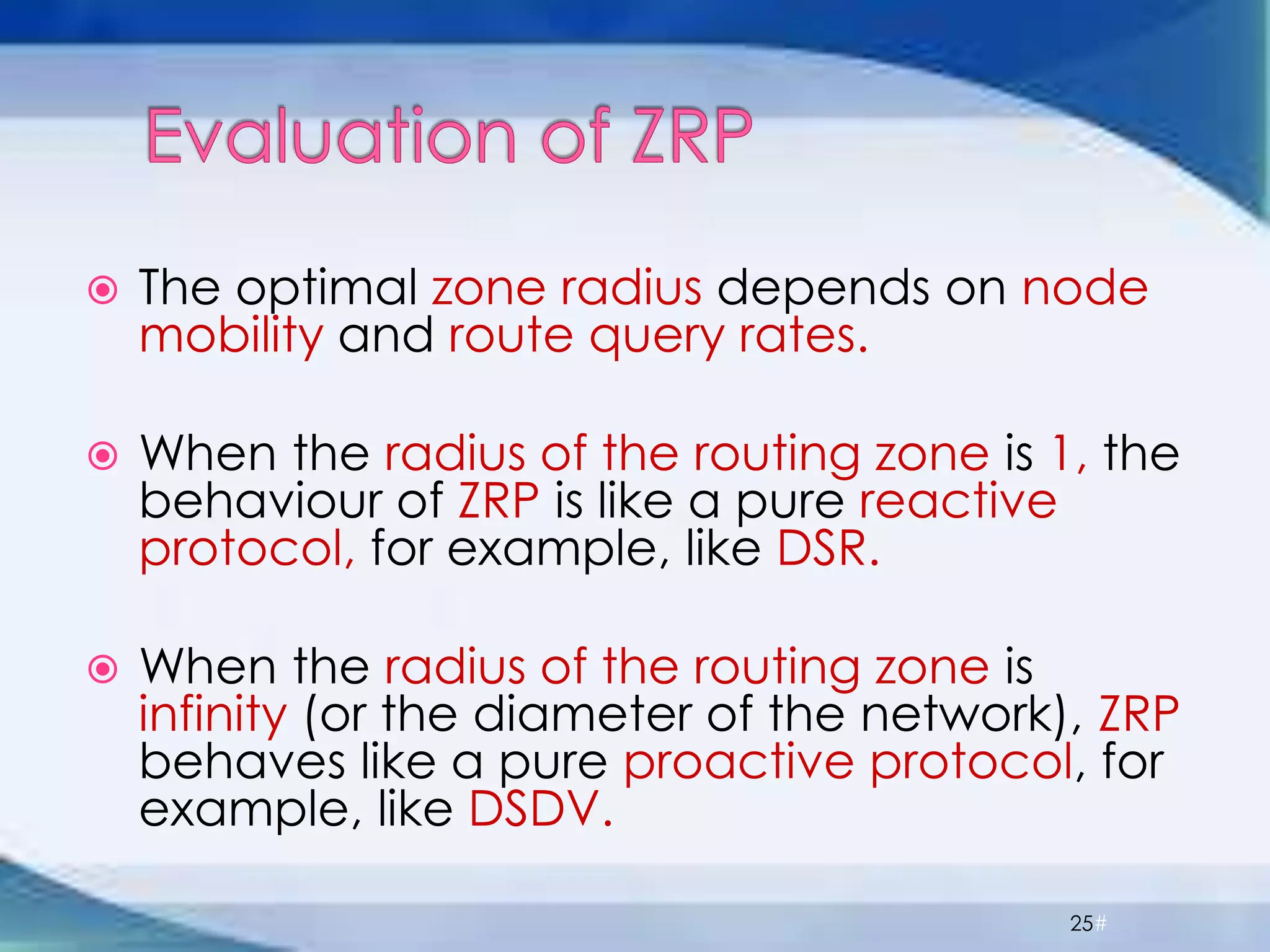
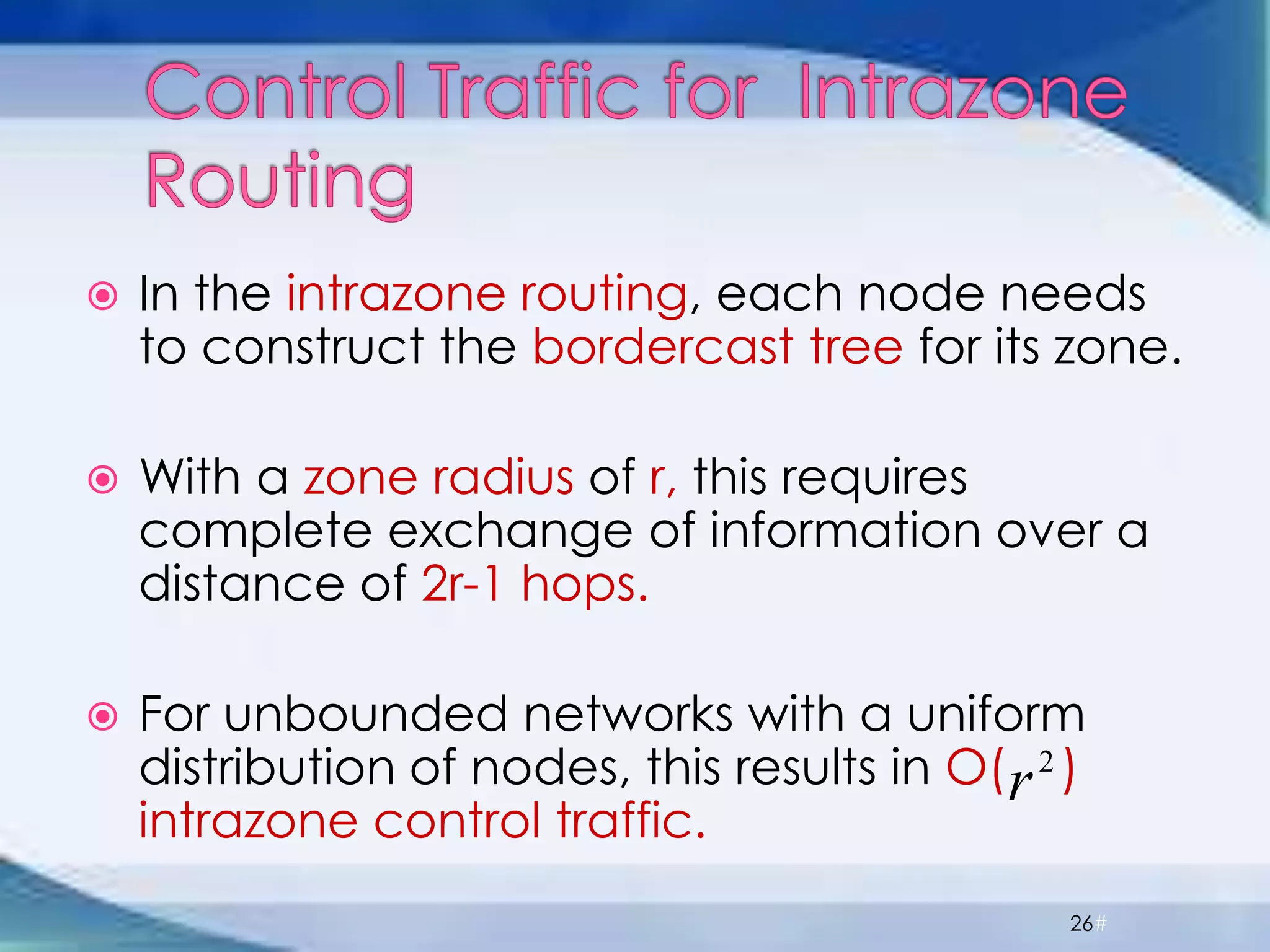
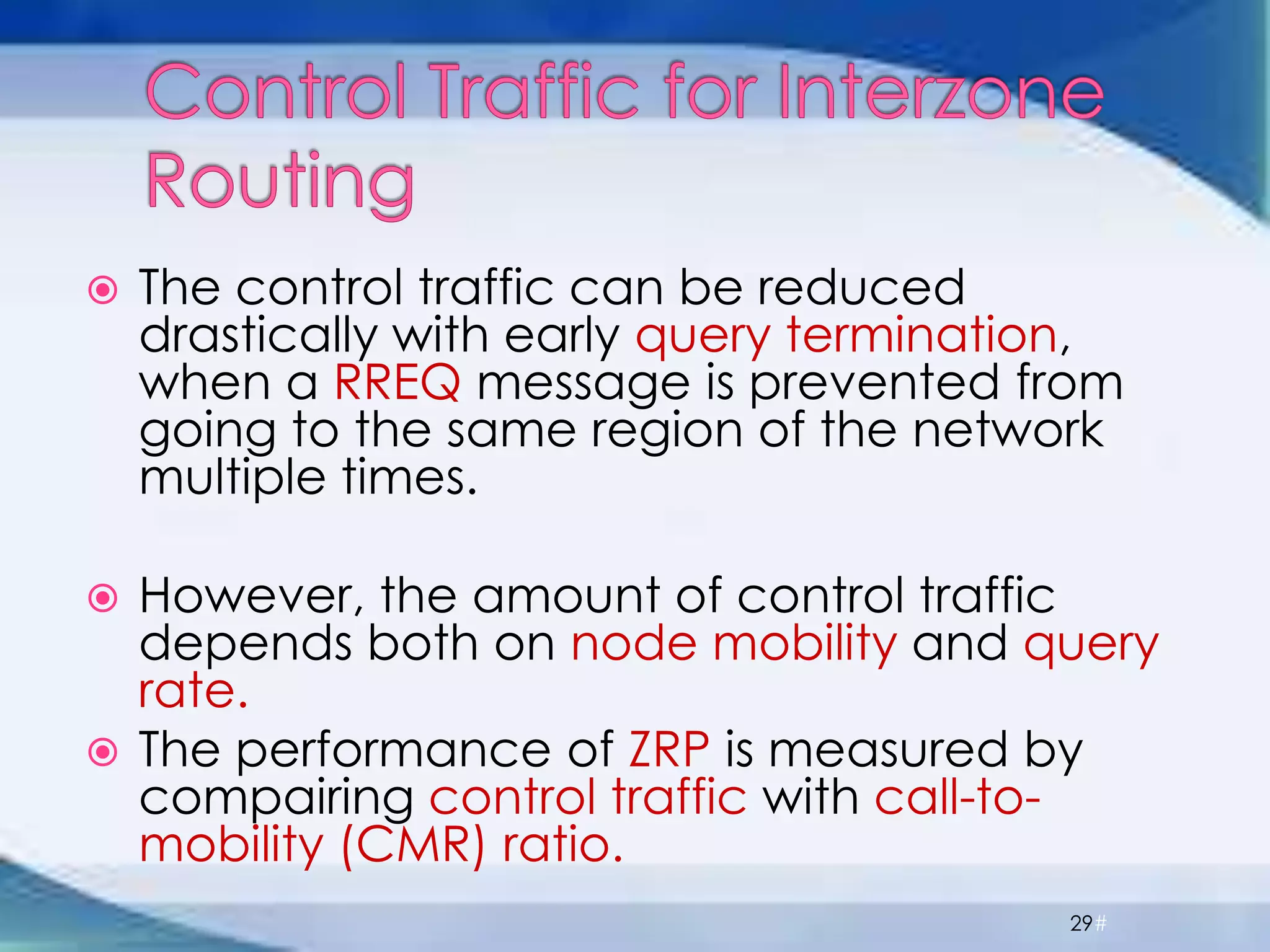
ZRP divides routing into intrazone and interzone routing. Intrazone routing uses a proactive approach to route packets within a node's routing zone. Interzone routing uses a reactive approach where the source node sends route requests to peripheral nodes when the destination is outside its zone. The optimal zone radius depends on factors like mobility and query rates, with smaller radii preferred for higher mobility. ZRP aims to reduce routing overhead through techniques like restricting floods and maintaining multiple routes.













![ On the other hand, CMR is low if mobility is
high.
In such a case, the routing zone
maintenance becomes very costly and
smaller routing zones are better for
reducing control traffic.
An optimally configured ZRP for a CMR of
500 [query/km] produces 70% less traffic
than flood searching.
31#](https://image.slidesharecdn.com/zrpupdate-130423153138-phpapp01/75/Zone-Routing-Protocol-31-2048.jpg)
