Embed presentation
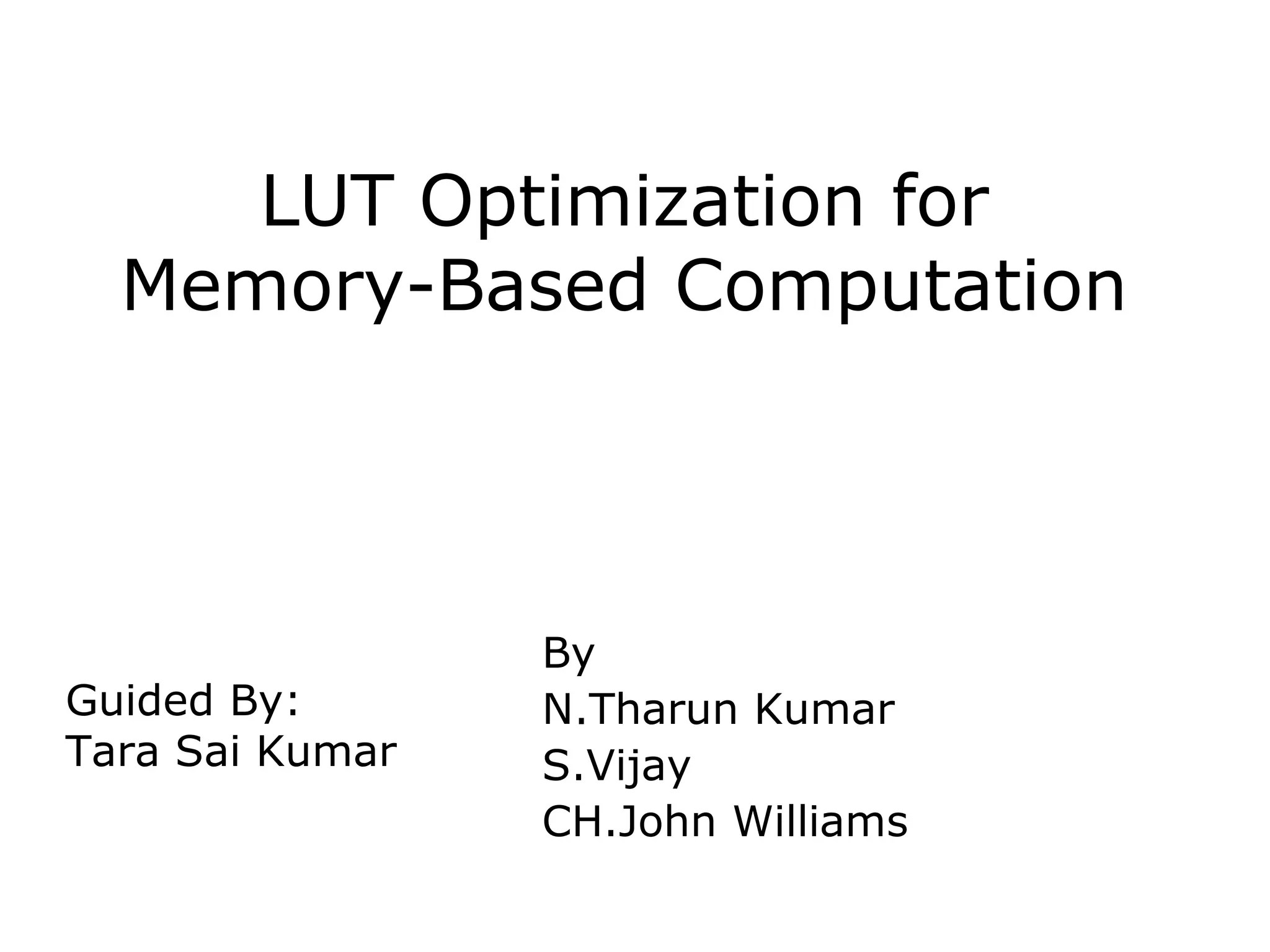





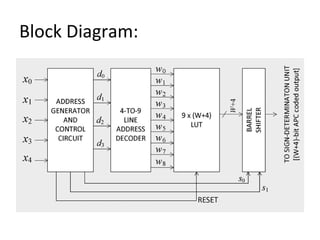



This document describes a proposed LUT optimization technique for memory-based computation. The authors aim to design an APC-OMS combined LUT structure to efficiently perform the multiplication of a W-bit fixed coefficient A with a 5-bit input X. This would reduce the size of the LUT to one-fourth that of a conventional design by applying a modified form of the Address Pre-Computation (APC) and Orthogonal Matching Search (OMS) techniques. A block diagram and benefits are presented, showing the combined approach can cut the area-delay product over 30% for 16-bit widths and 50% for 32-bit widths compared to conventional signed-digit multipliers.










