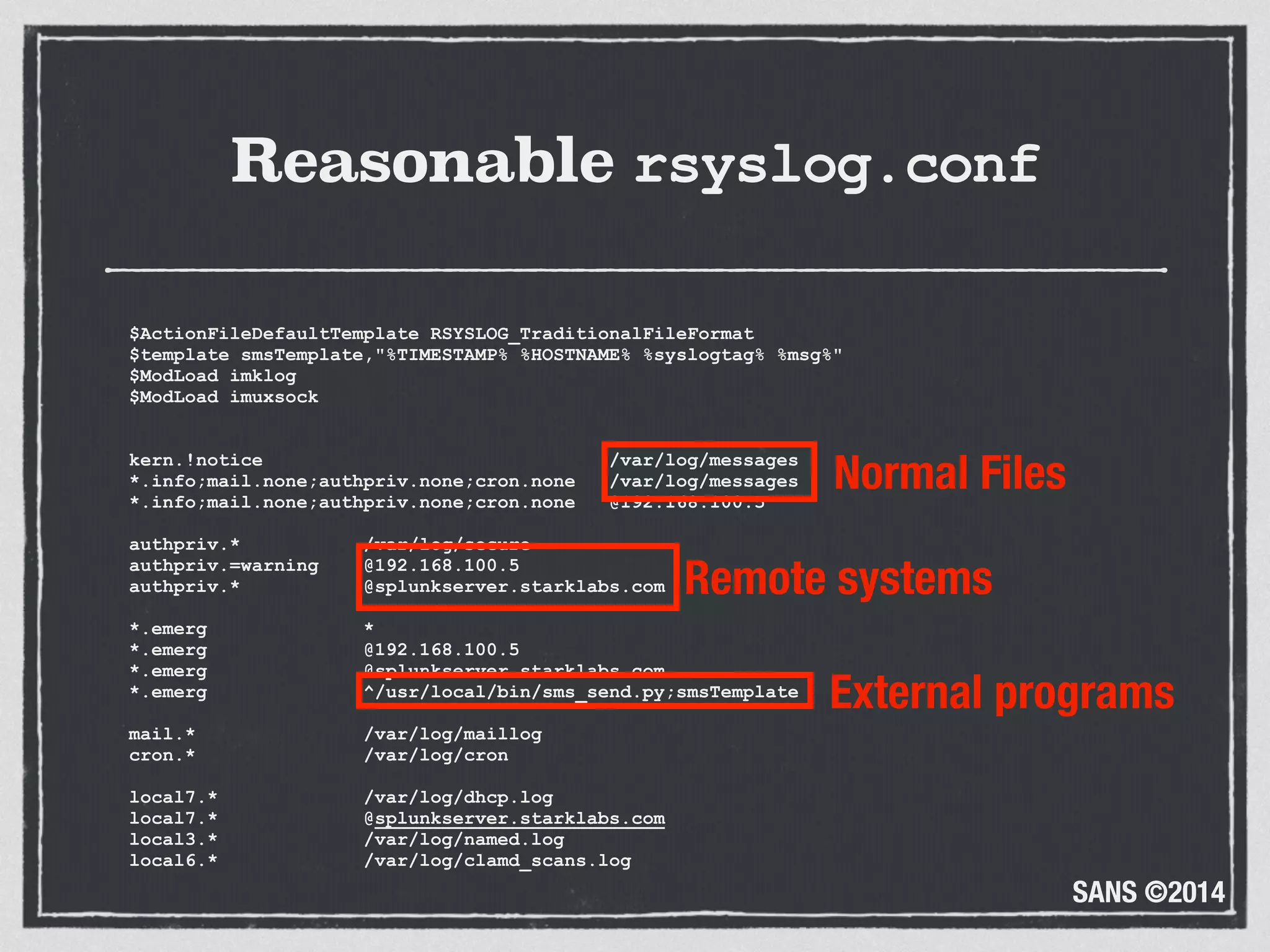
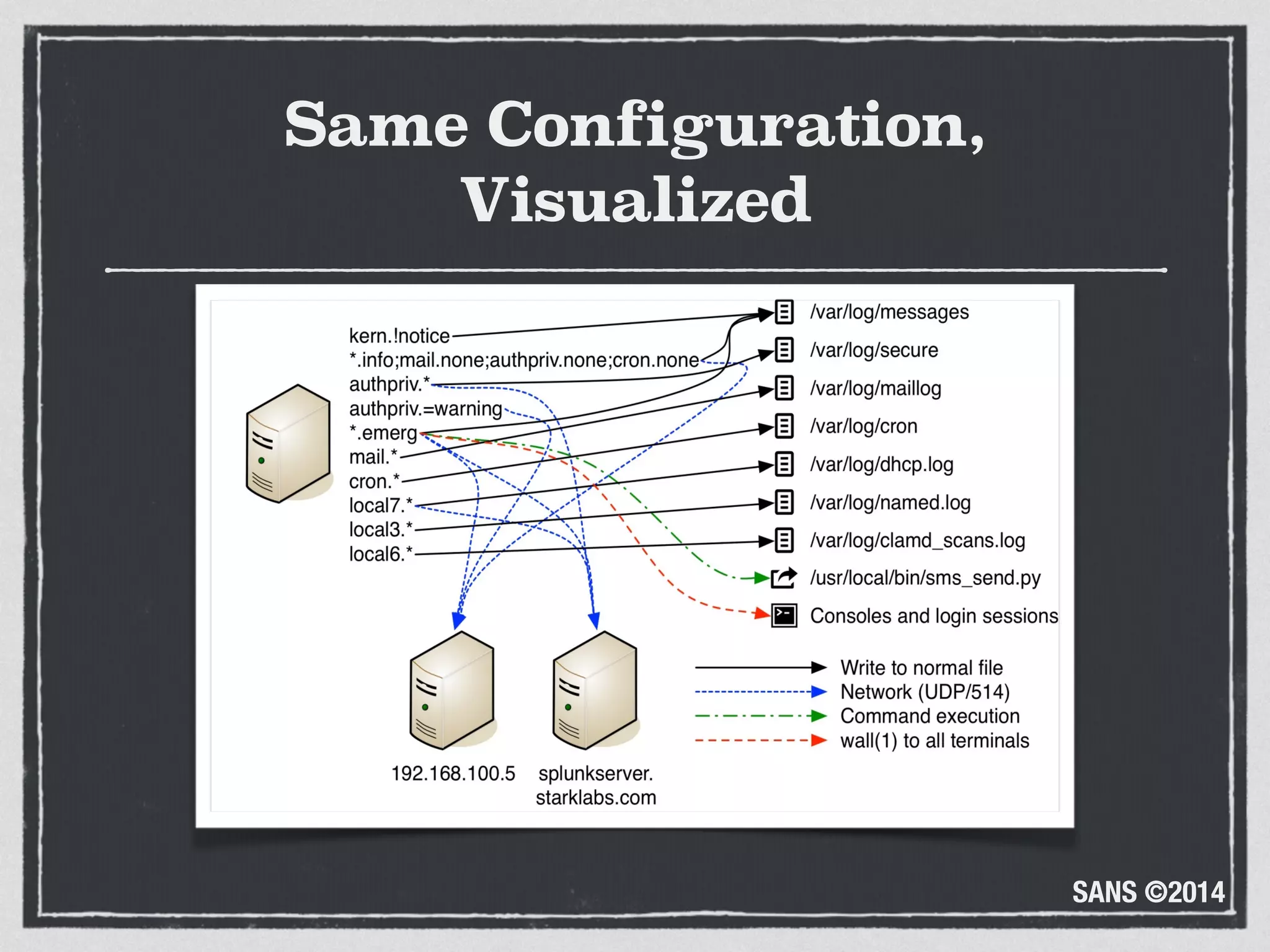
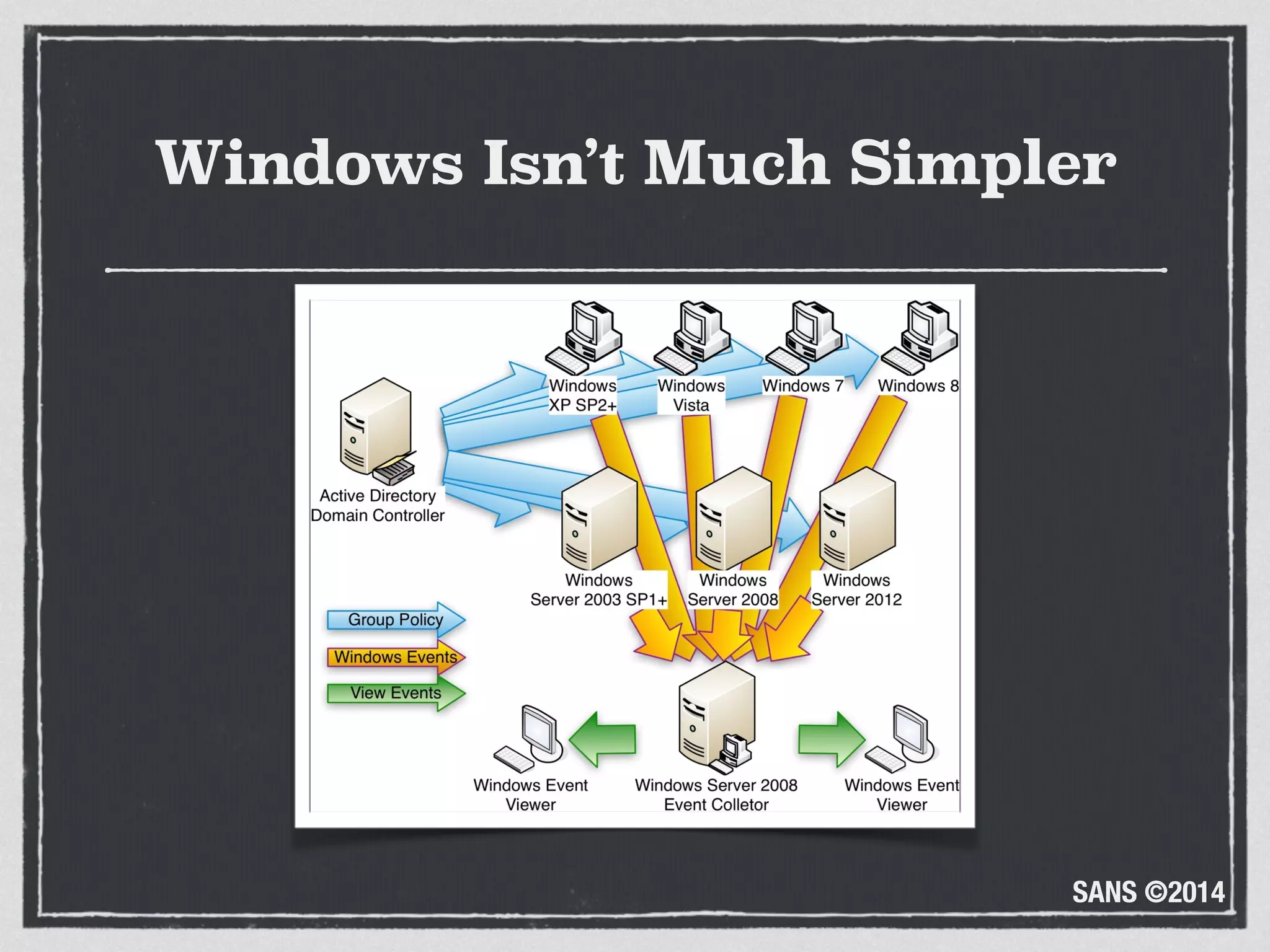
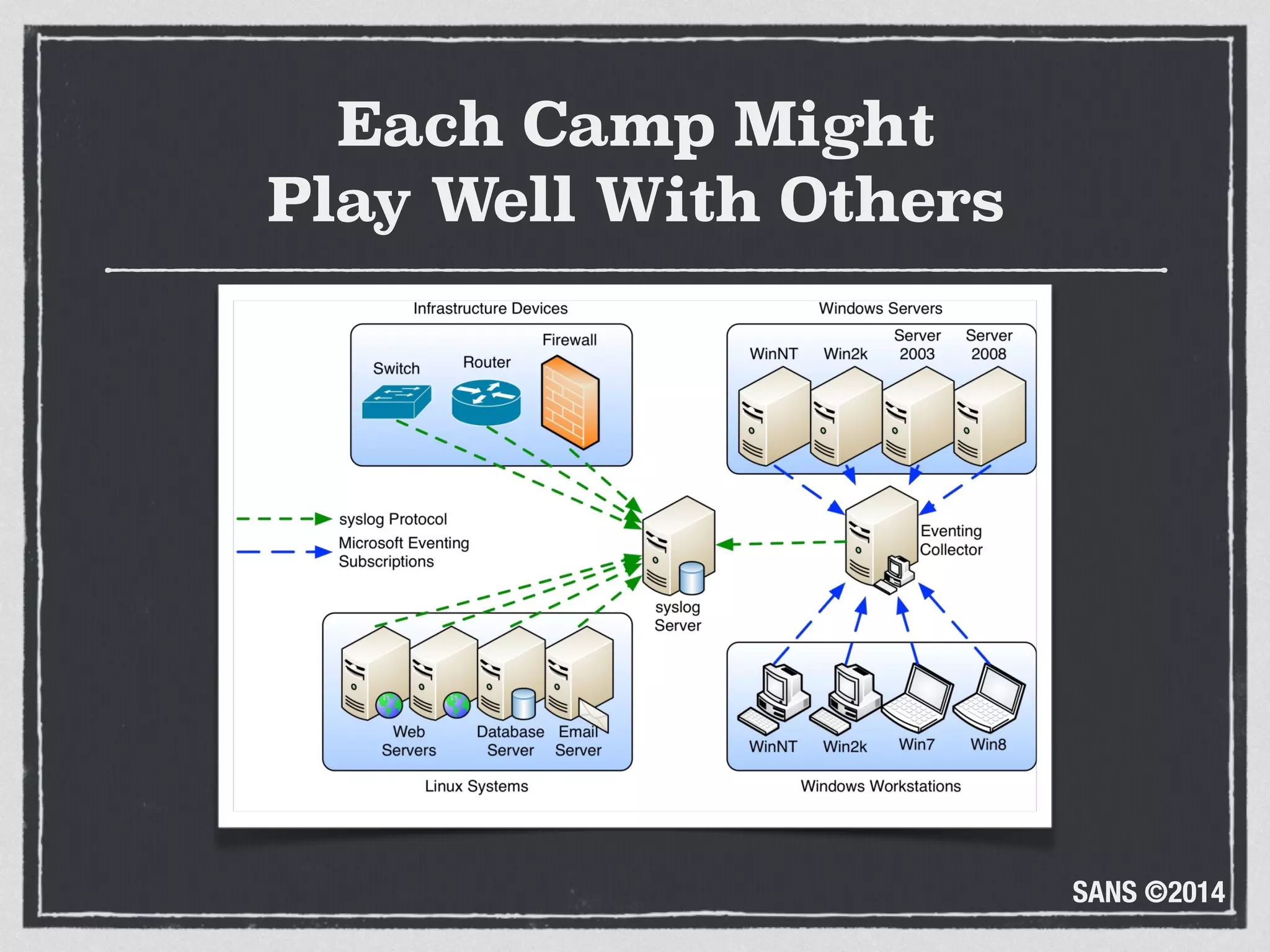
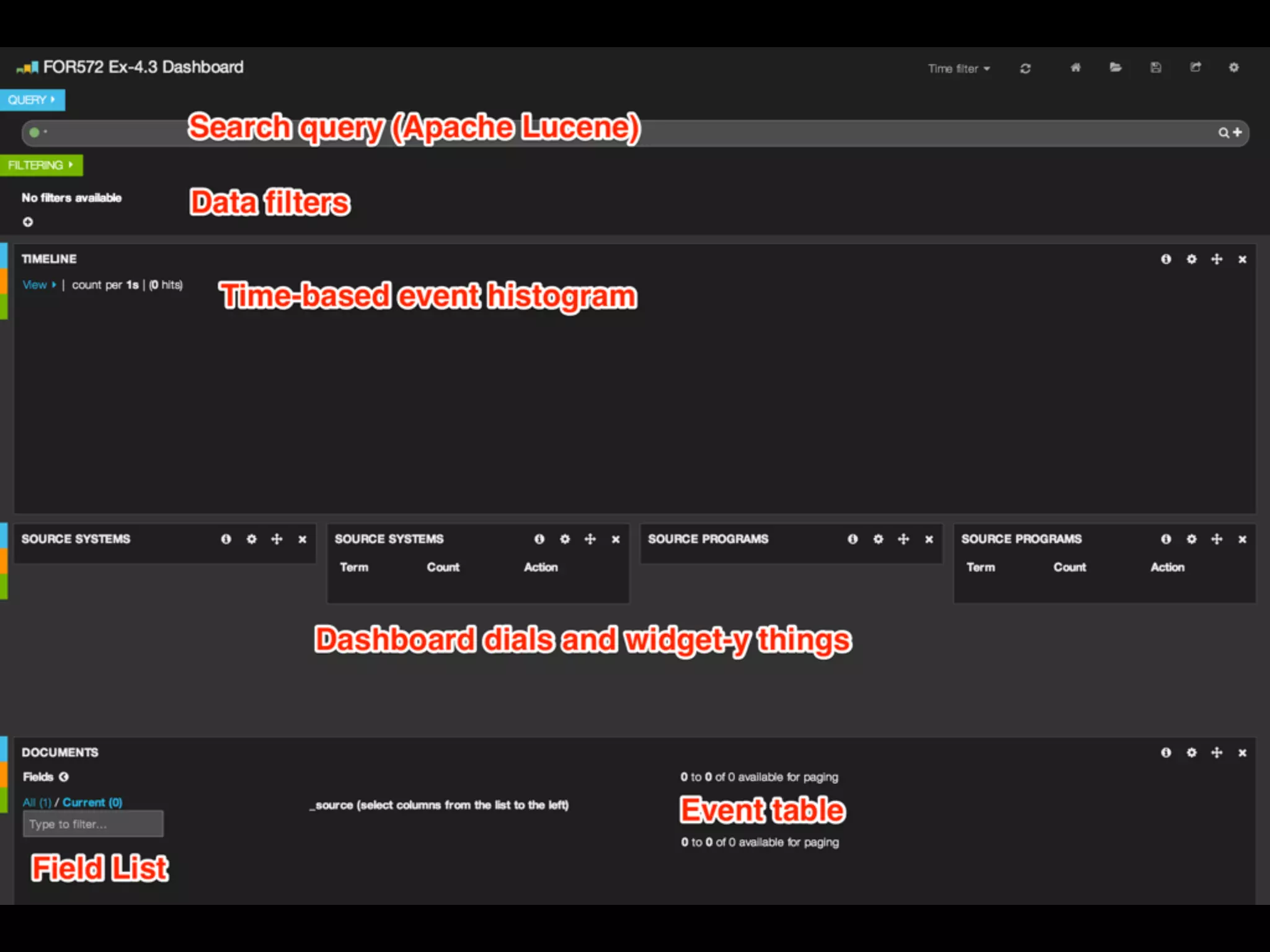
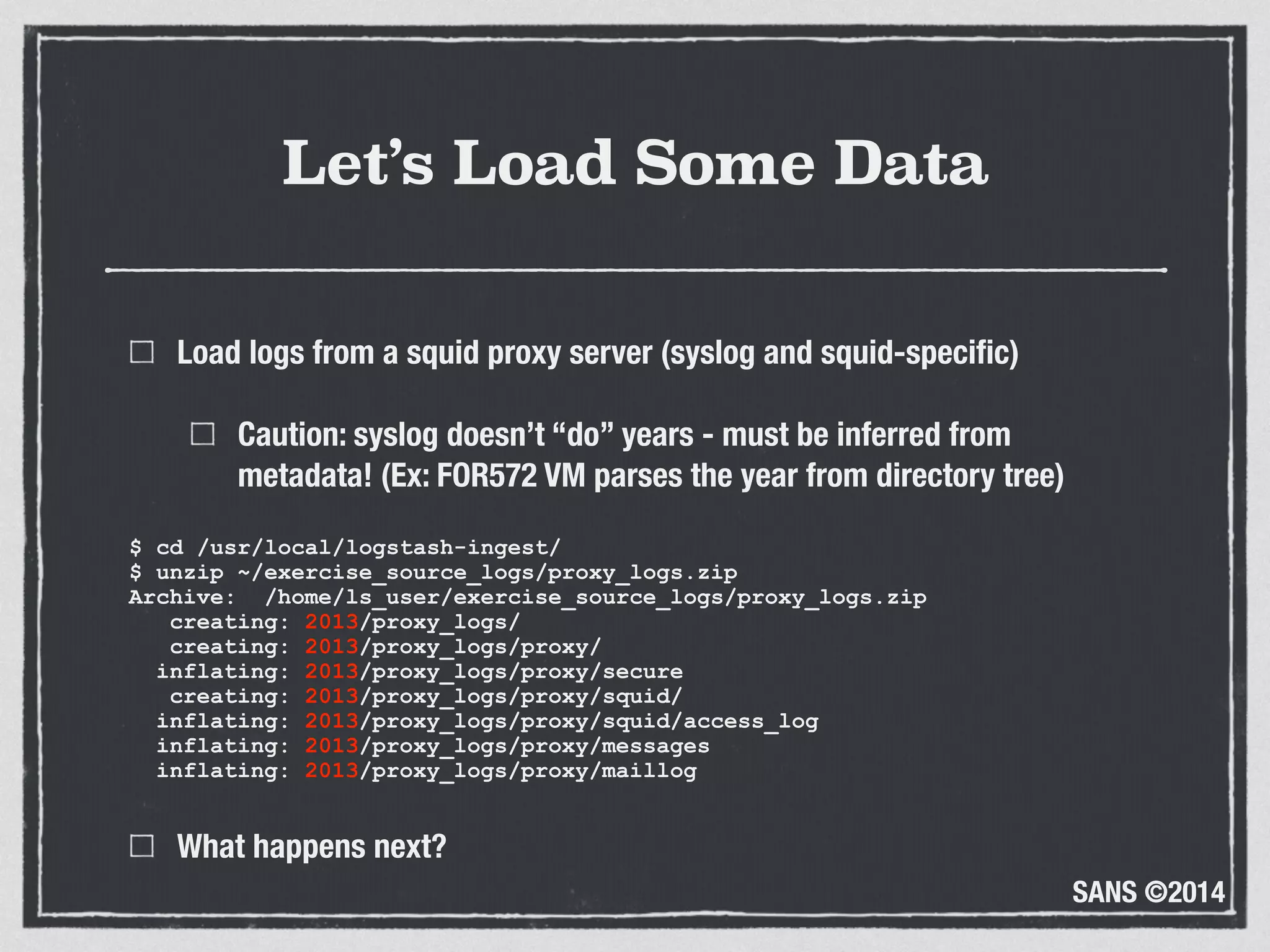
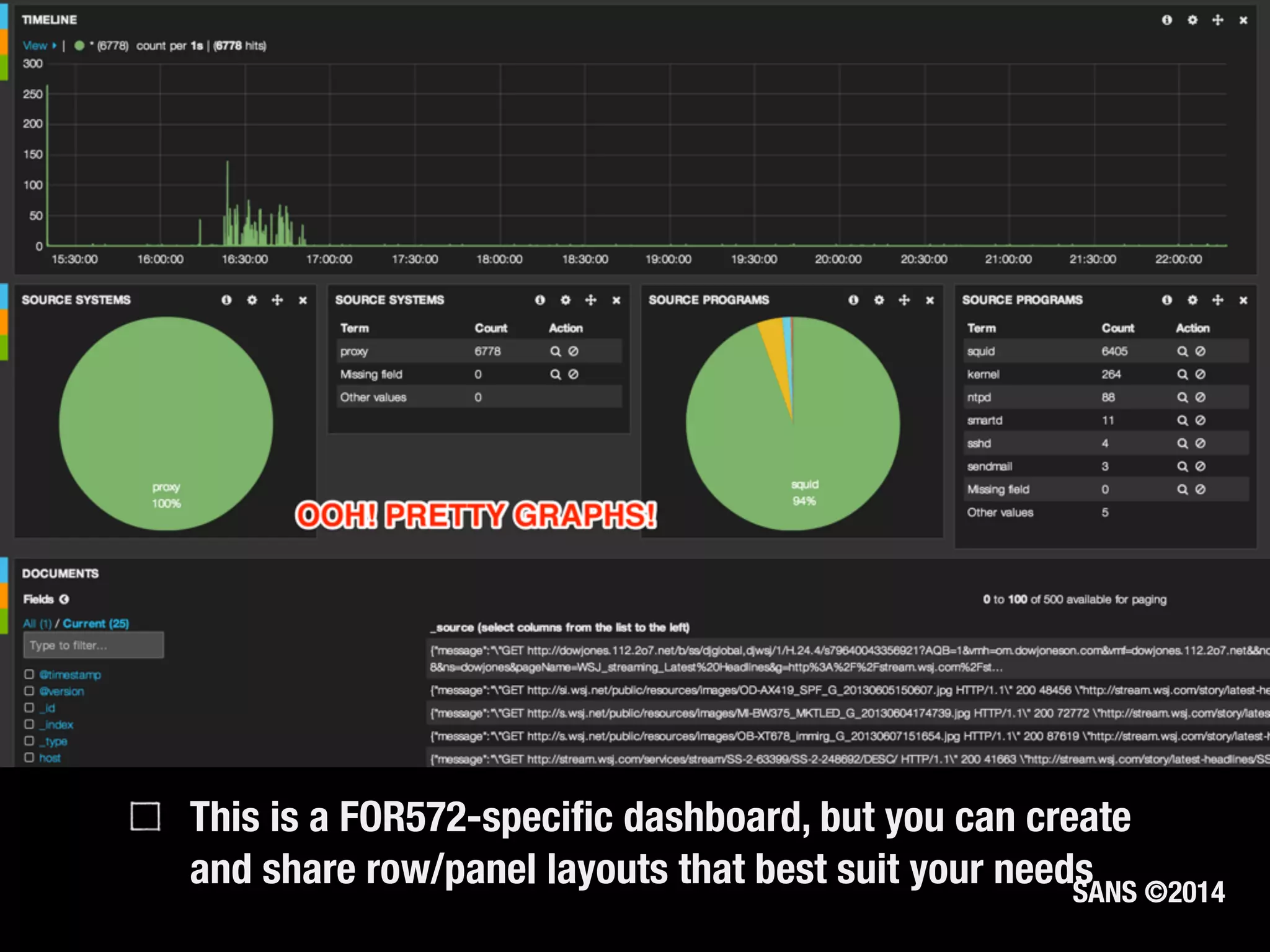
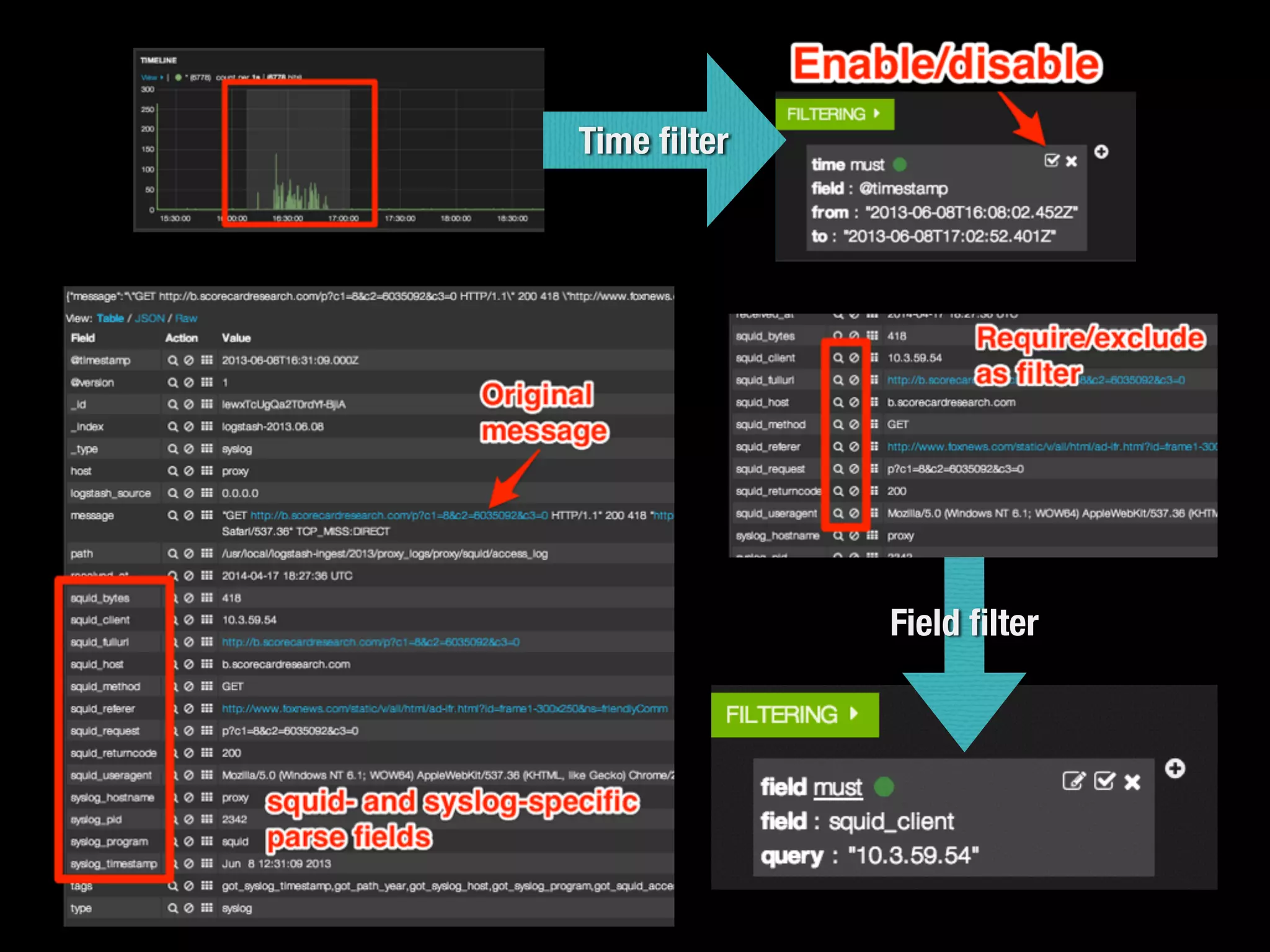
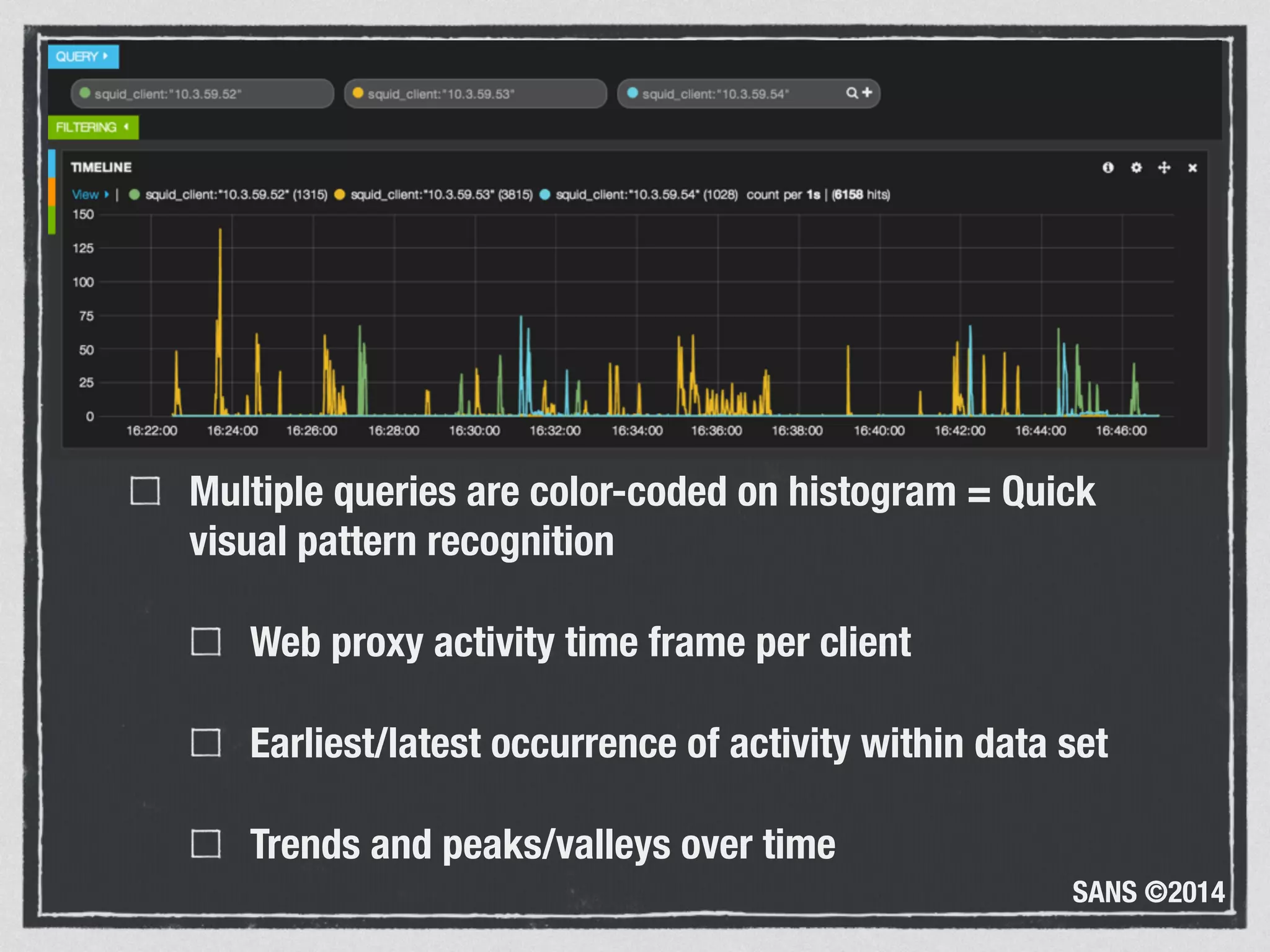
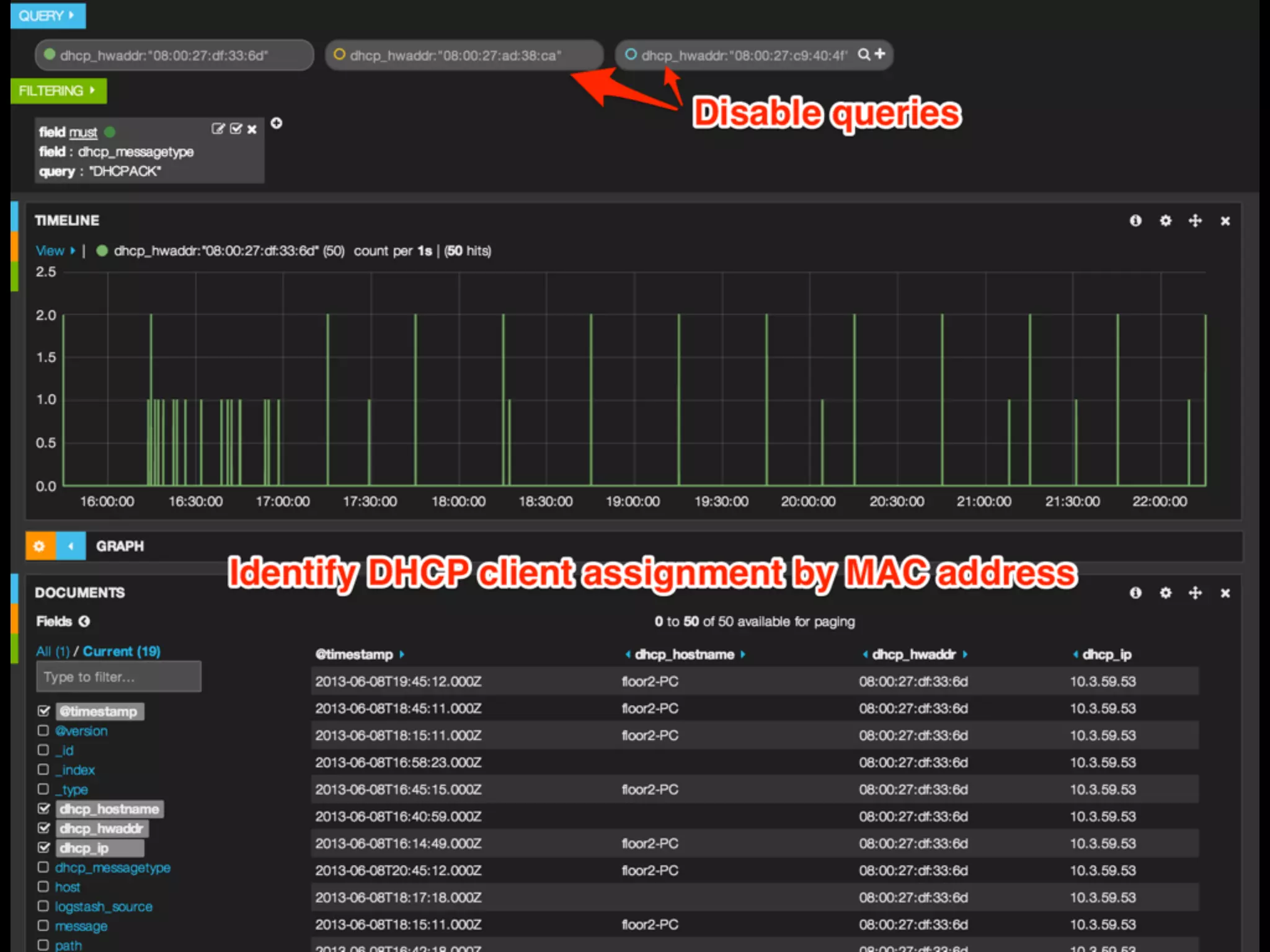
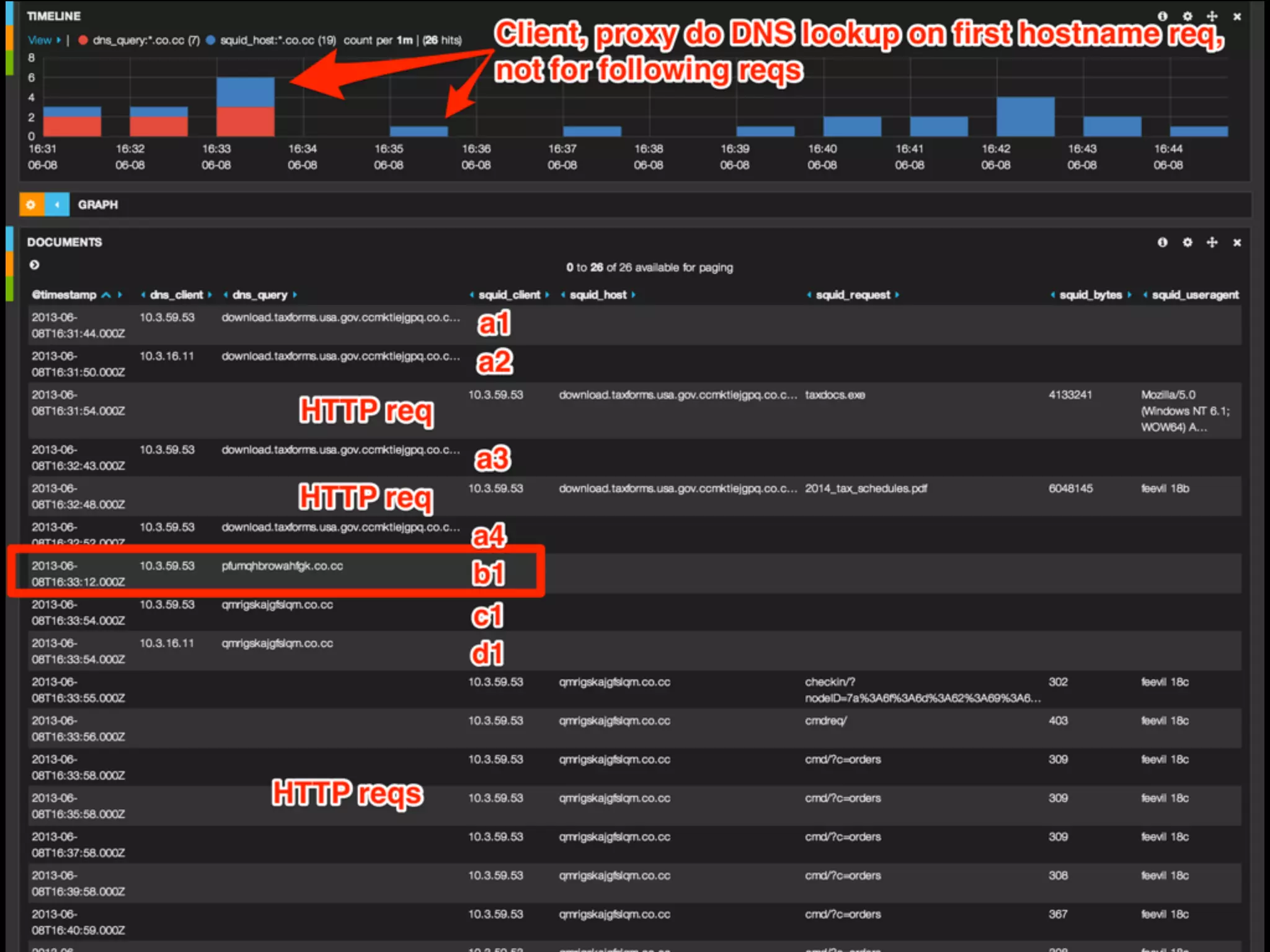
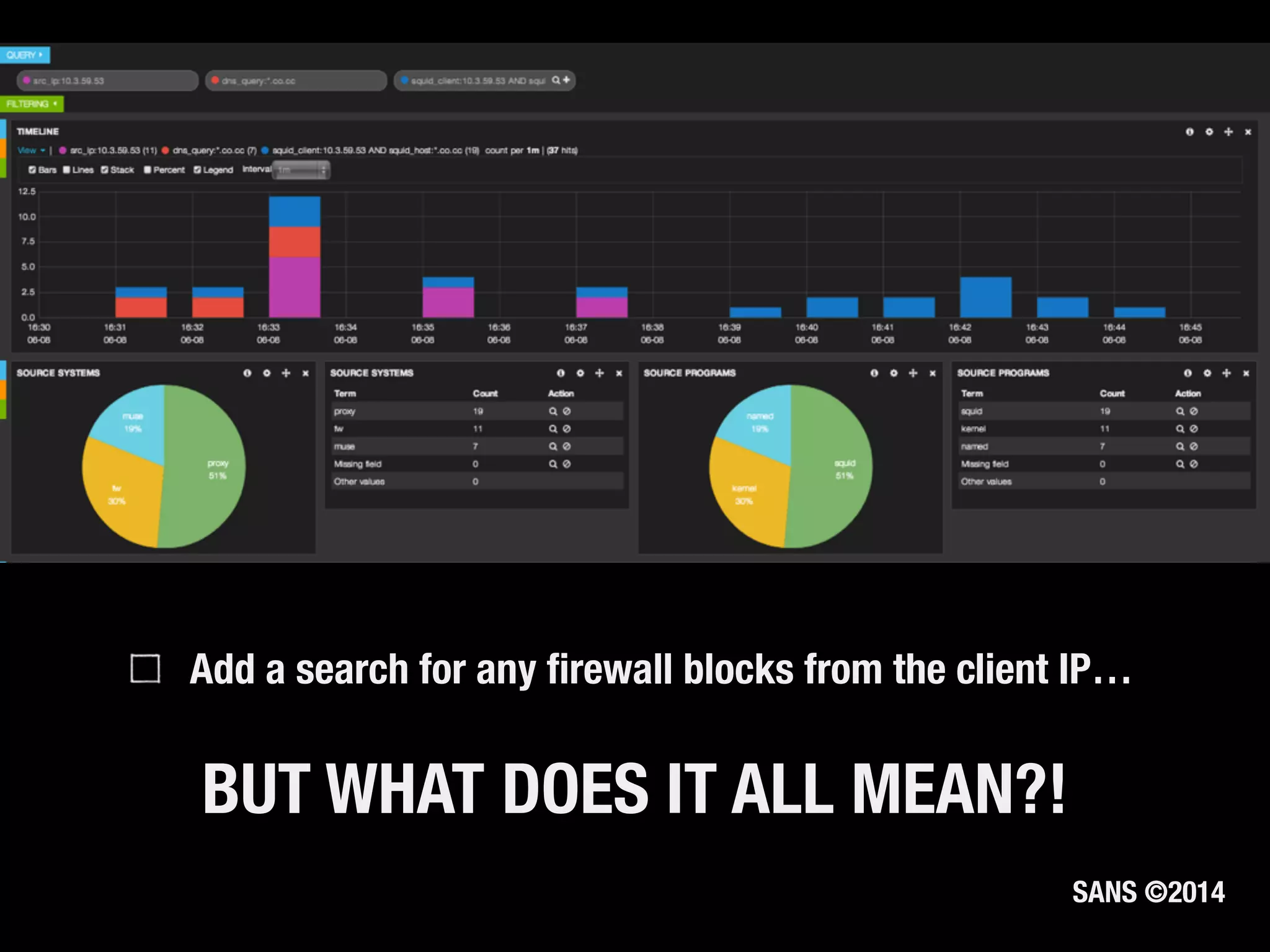
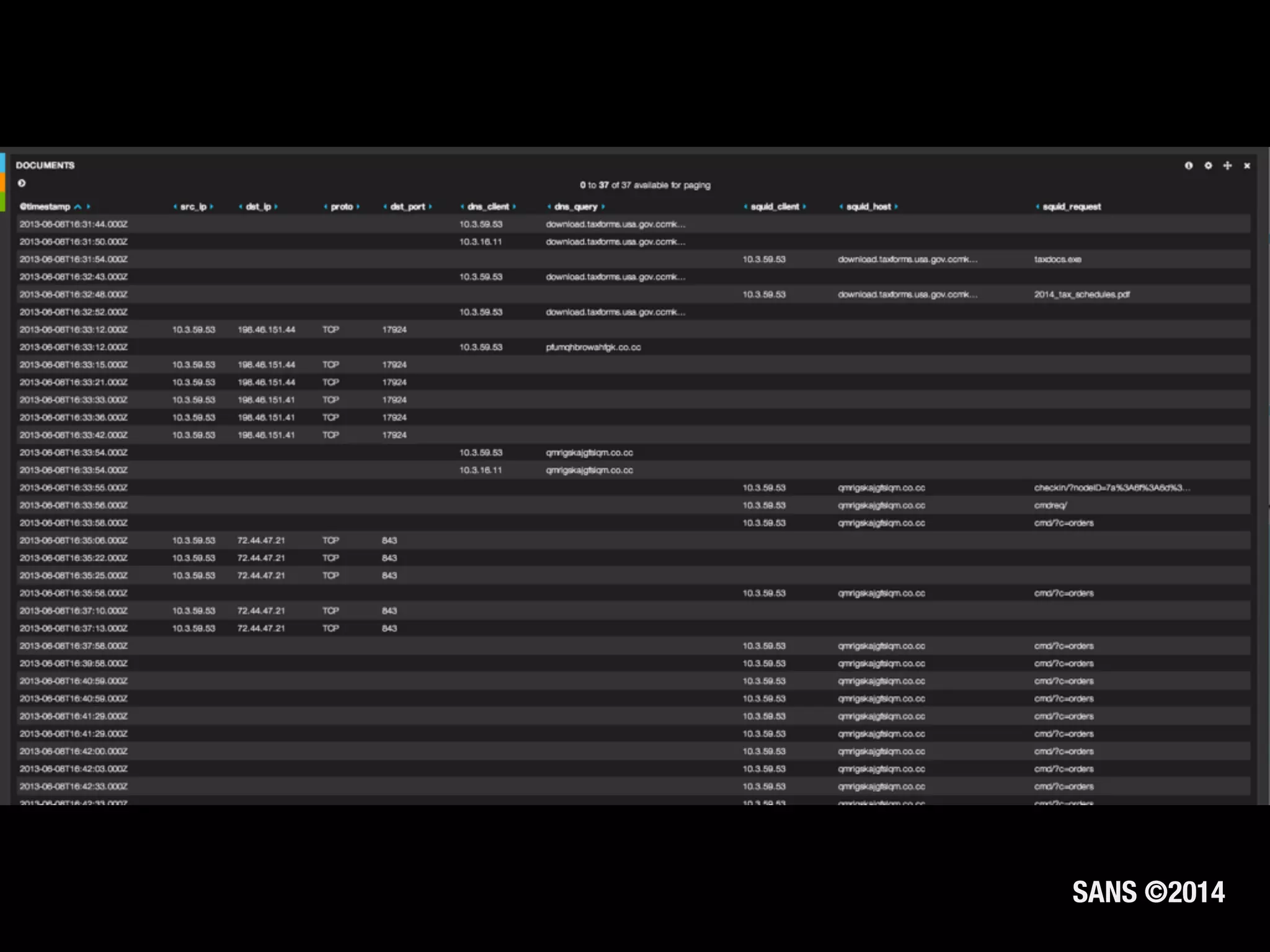
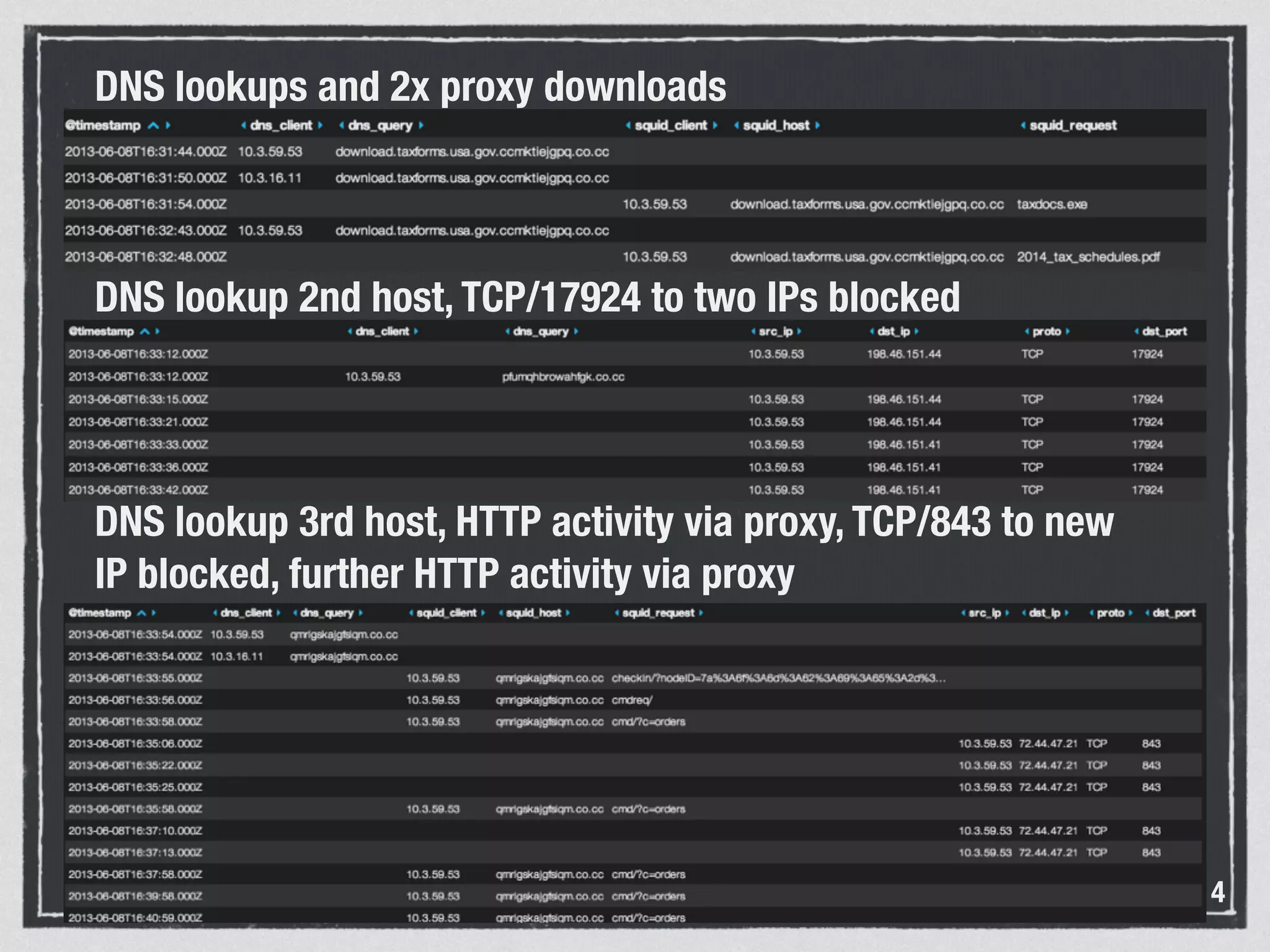
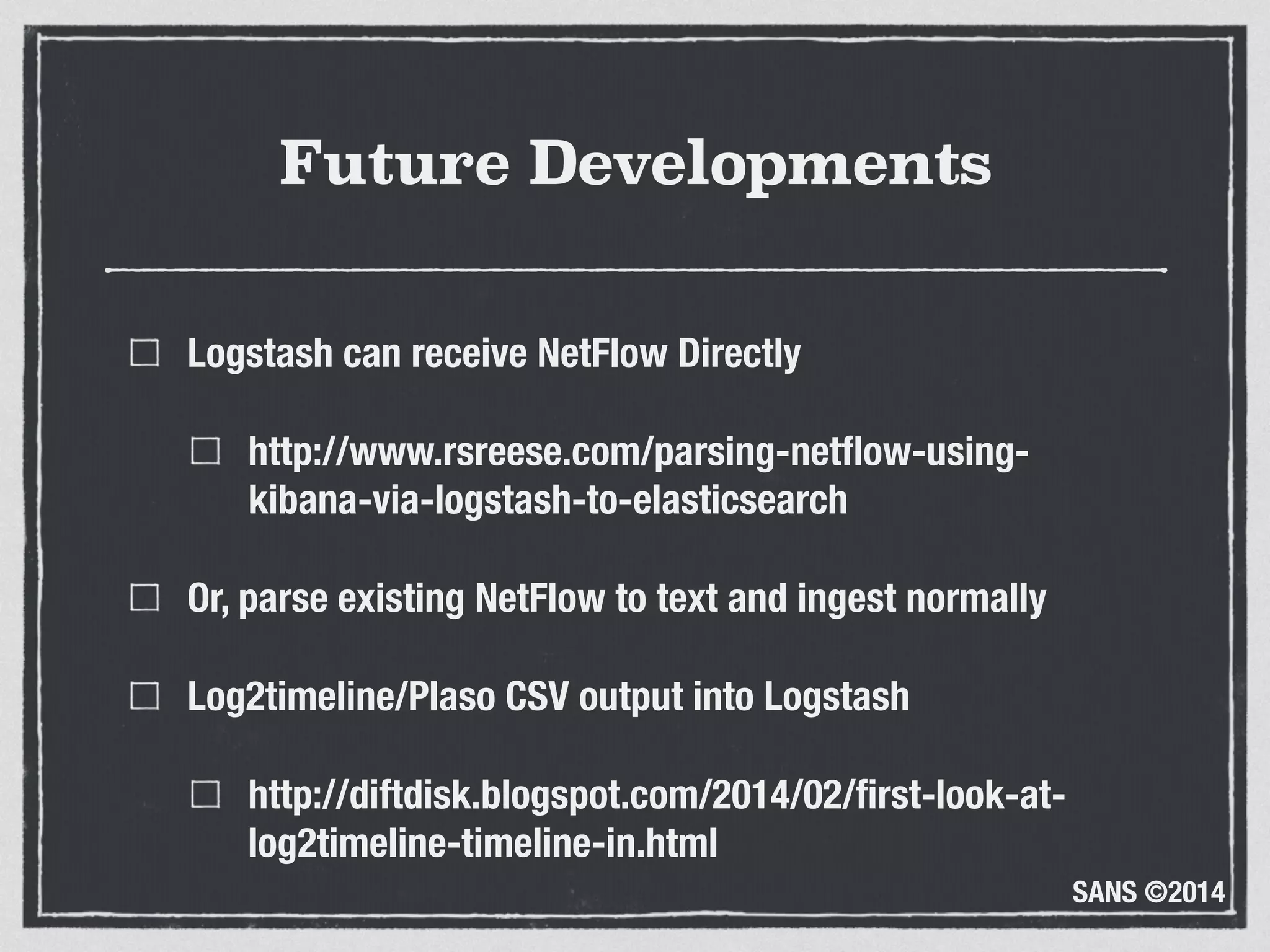
The document discusses the importance of logs in network forensics investigations. It introduces Logstash, an open-source tool for centralized log aggregation and analysis. Logstash allows ingestion of logs from many sources in various formats, filtering and parsing of logs, and output to search databases. The document demonstrates using Logstash to ingest sample log files to provide a holistic view of network activity for investigation.