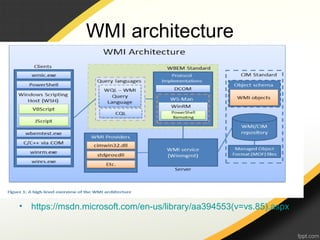
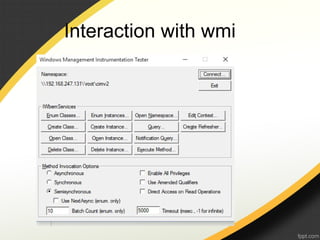
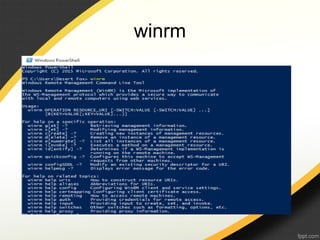
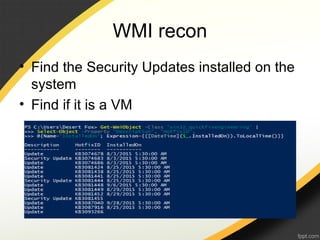
The document discusses Windows Management Instrumentation (WMI) and its use in malware attacks, detailing its architecture, querying capabilities, and types of eventing. It provides a timeline of specific malware incidents leveraging WMI, including methods of infection and how attackers manipulate WMI for remote code execution. Additionally, it outlines potential defenses against such abuses of WMI within systems.