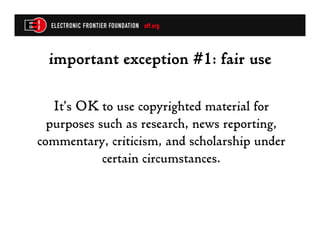
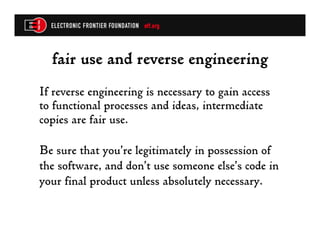
The document discusses the unique legal considerations in mobile security research, highlighting the risks of lawsuits or prosecution related to unauthorized access and copyright infringements. Key legal frameworks include contract law, computer crime laws, and copyright laws, which dictate how researchers can legally interact with software and devices. It emphasizes the importance of obtaining legal advice, understanding applicable agreements, and ensuring compliance with laws to minimize risks during research.






![unauthorized access
The CFAA prohibits, among other things,
“intentionally access[ing] a computer without
authorization or in excess of authorization, and
thereby obtain[ing] . . . information from any
protected computer.”
18 U.S.C. § 1030(a)(2)(C).](https://image.slidesharecdn.com/hofmanncansecwest2012-120718132228-phpapp02/85/Legal-Issues-in-Mobile-Security-Research-15-320.jpg)





![important exception #2: Section 117
The owner of a copy of a computer program
may copy or adapt it as “an essential step
in the utilization of the computer program
with a machine[.]”](https://image.slidesharecdn.com/hofmanncansecwest2012-120718132228-phpapp02/85/Legal-Issues-in-Mobile-Security-Research-26-320.jpg)