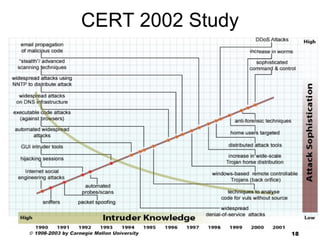
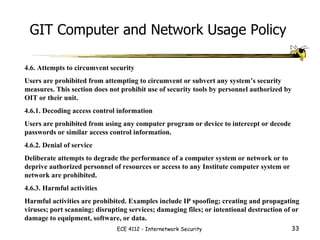
The document discusses the ethics of ethical hacking and vulnerability assessments. It outlines common steps that attackers and security professionals take, such as reconnaissance, scanning, gaining access, and maintaining access. It also discusses laws related to computer crimes and guidelines for properly disclosing software vulnerabilities.