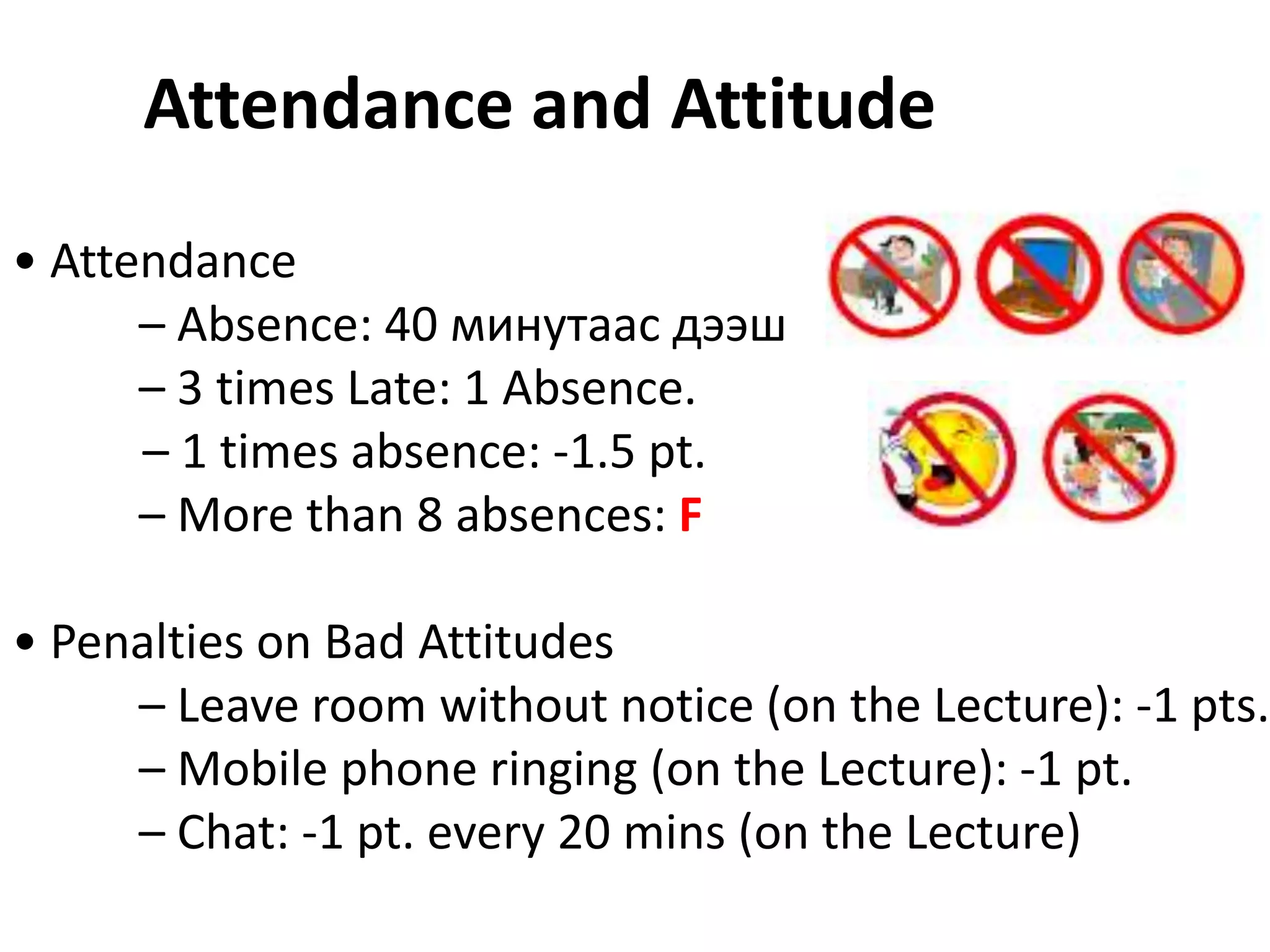
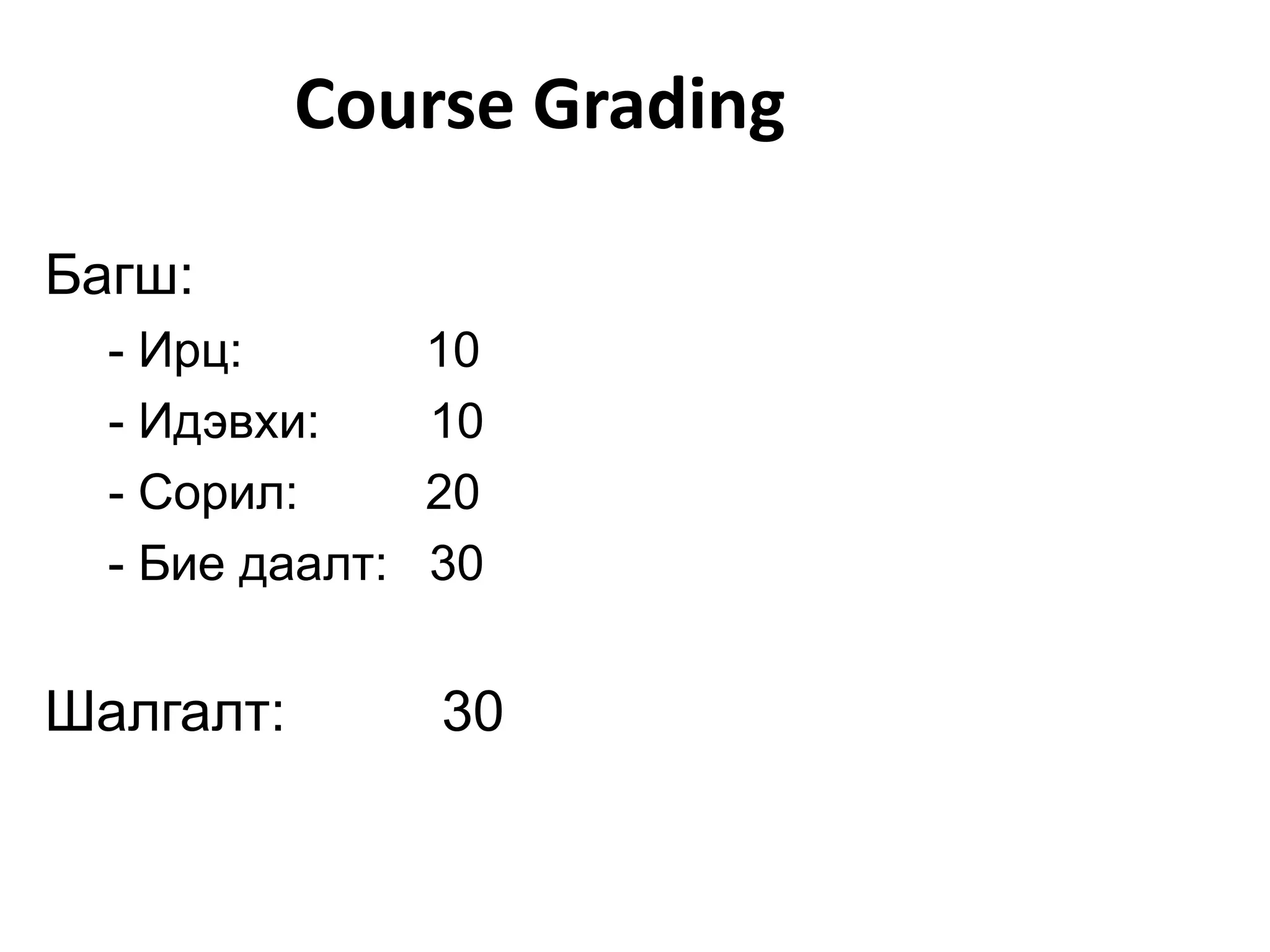
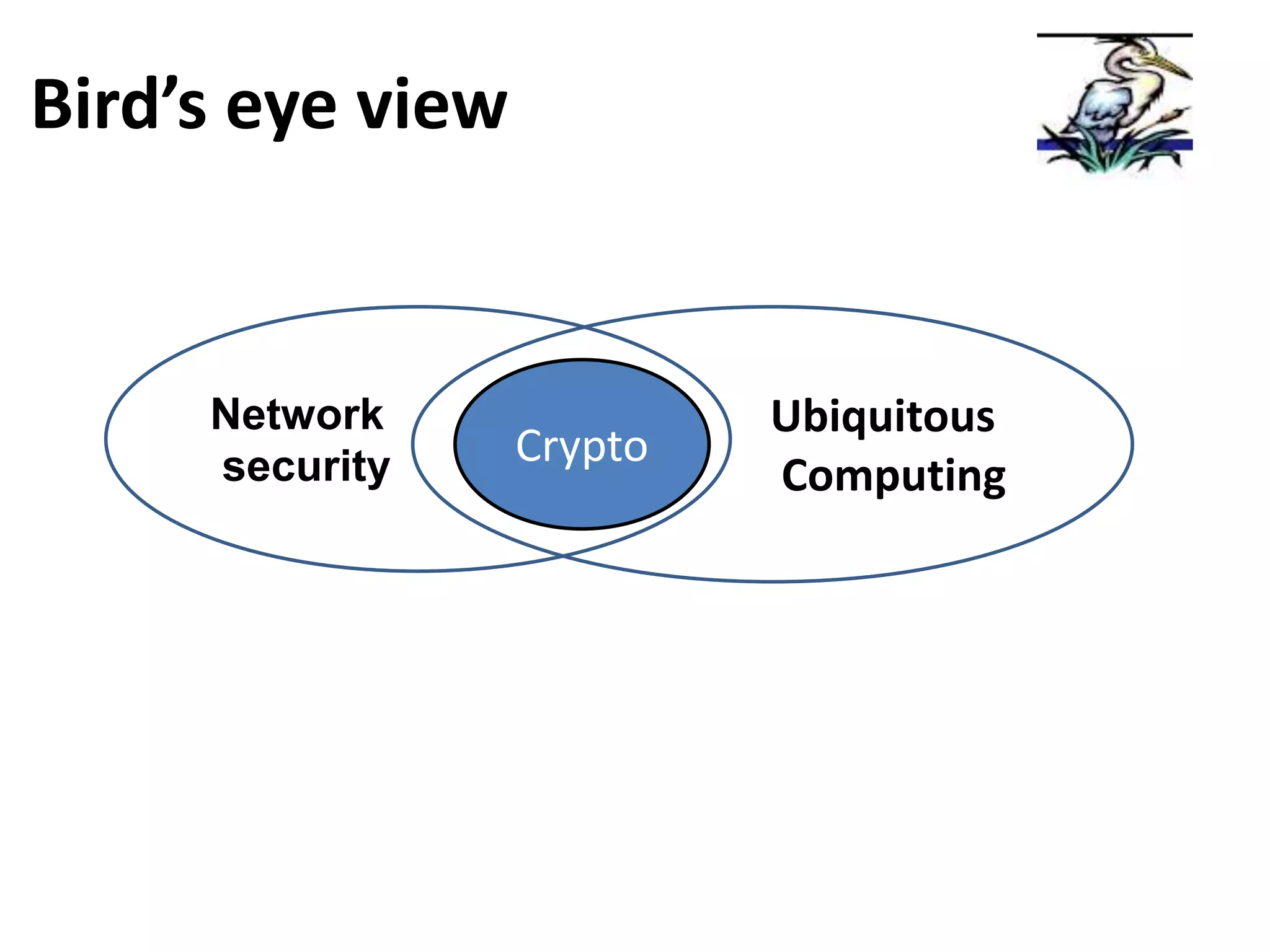
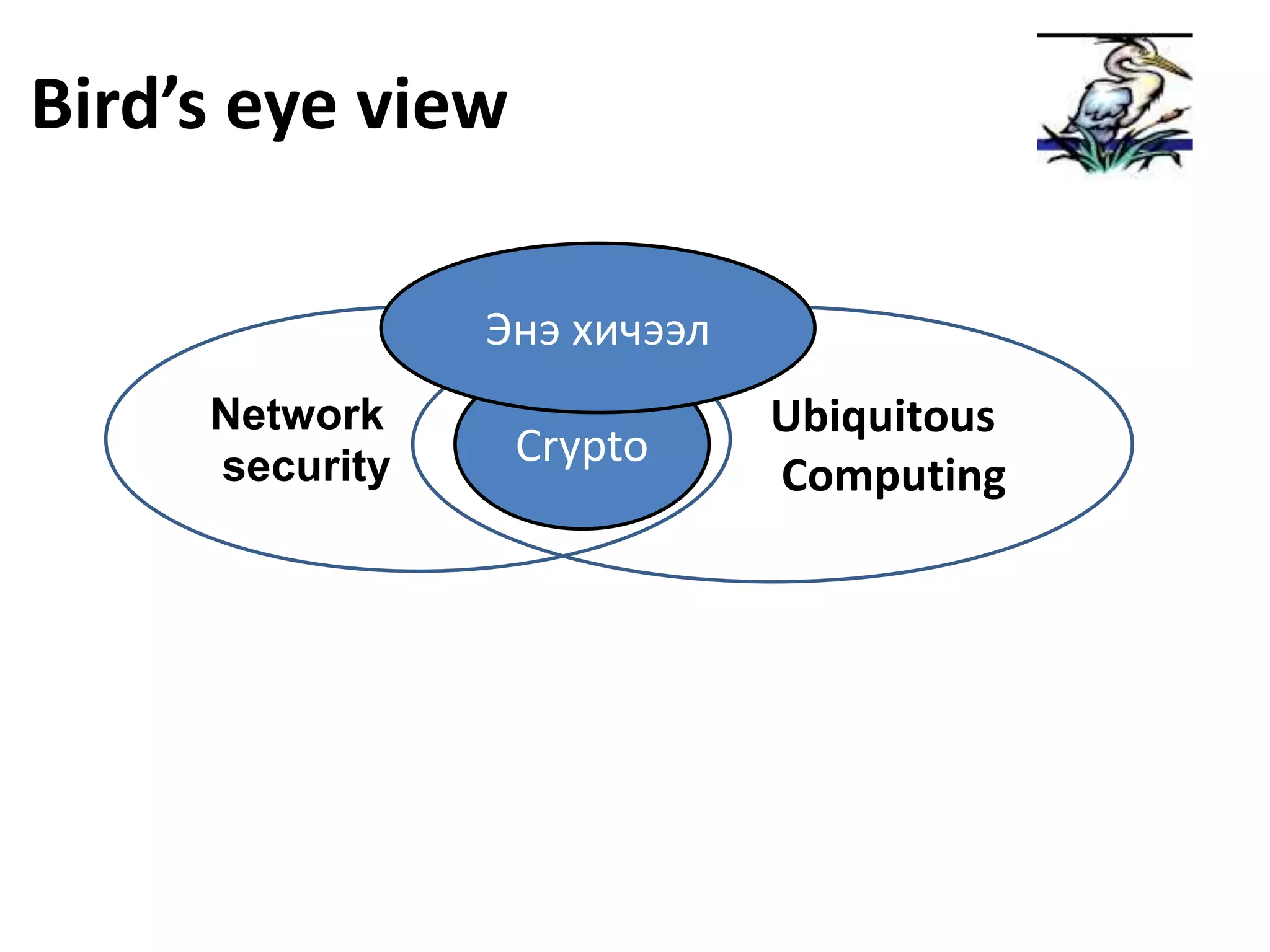
This document provides information about an information security course being taught in 2011. The instructor's contact information is provided. Prerequisites for the course include at least one course in computer networks, network programming, wireless networks, or mobile communications, as well as at least one course in network security, cryptography, data structures, or computer algorithms. Attendance policies state absences over 8 will result in failing the course. The course grading breakdown is provided, with exams, assignments, projects, and class participation accounting for grades. Required textbooks are not listed, as all materials will be provided. References on network security are also recommended.