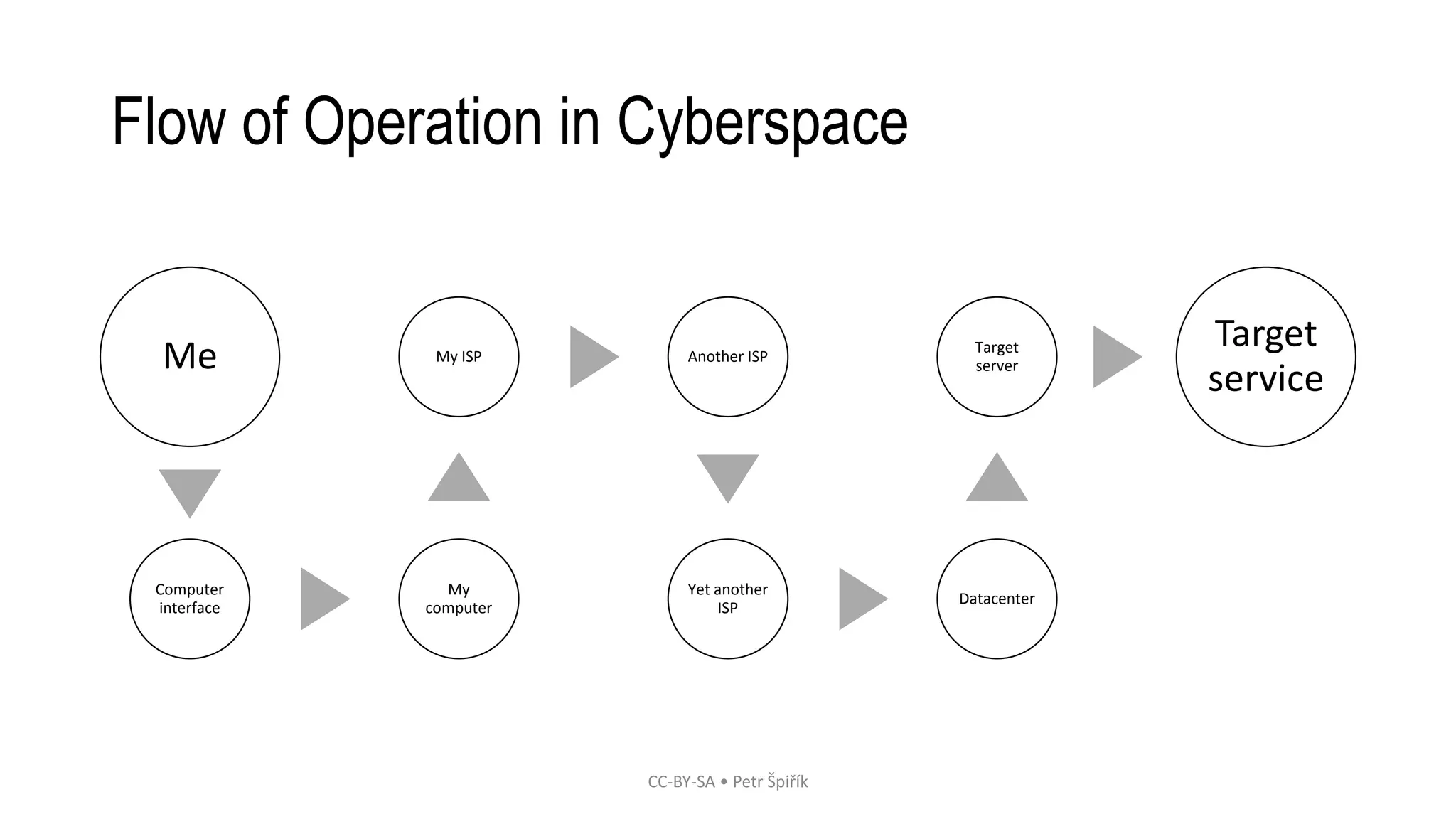
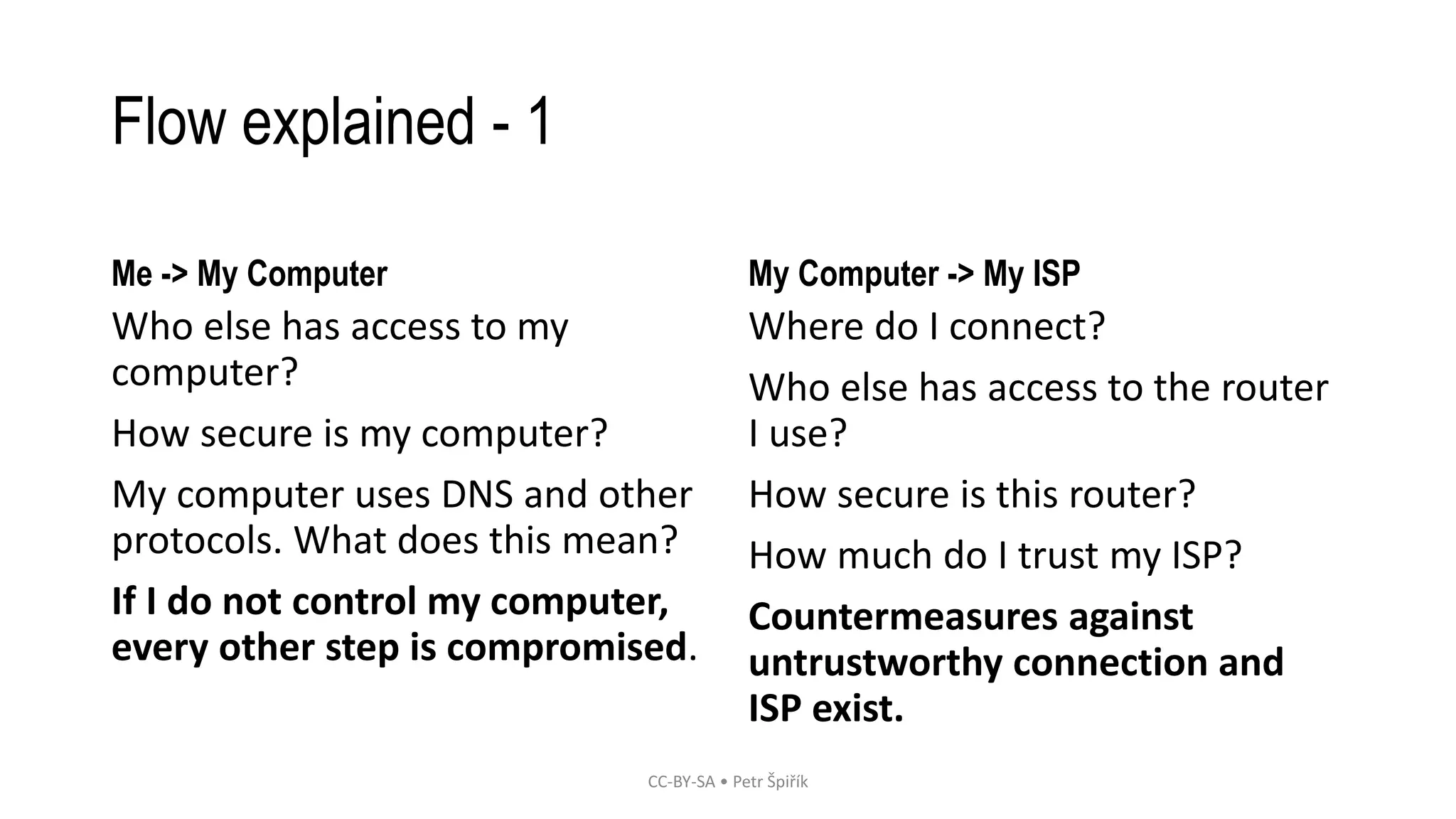
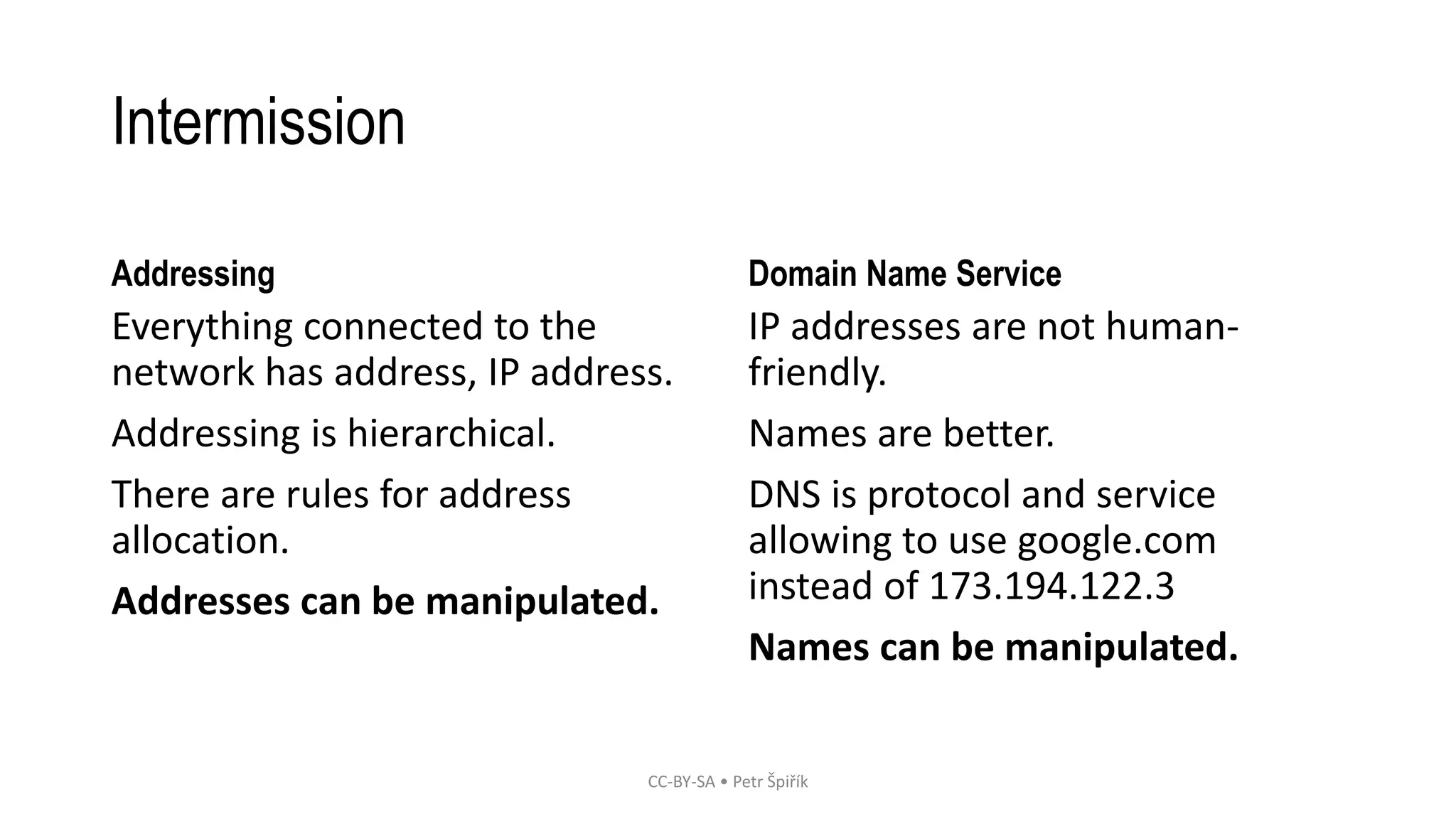
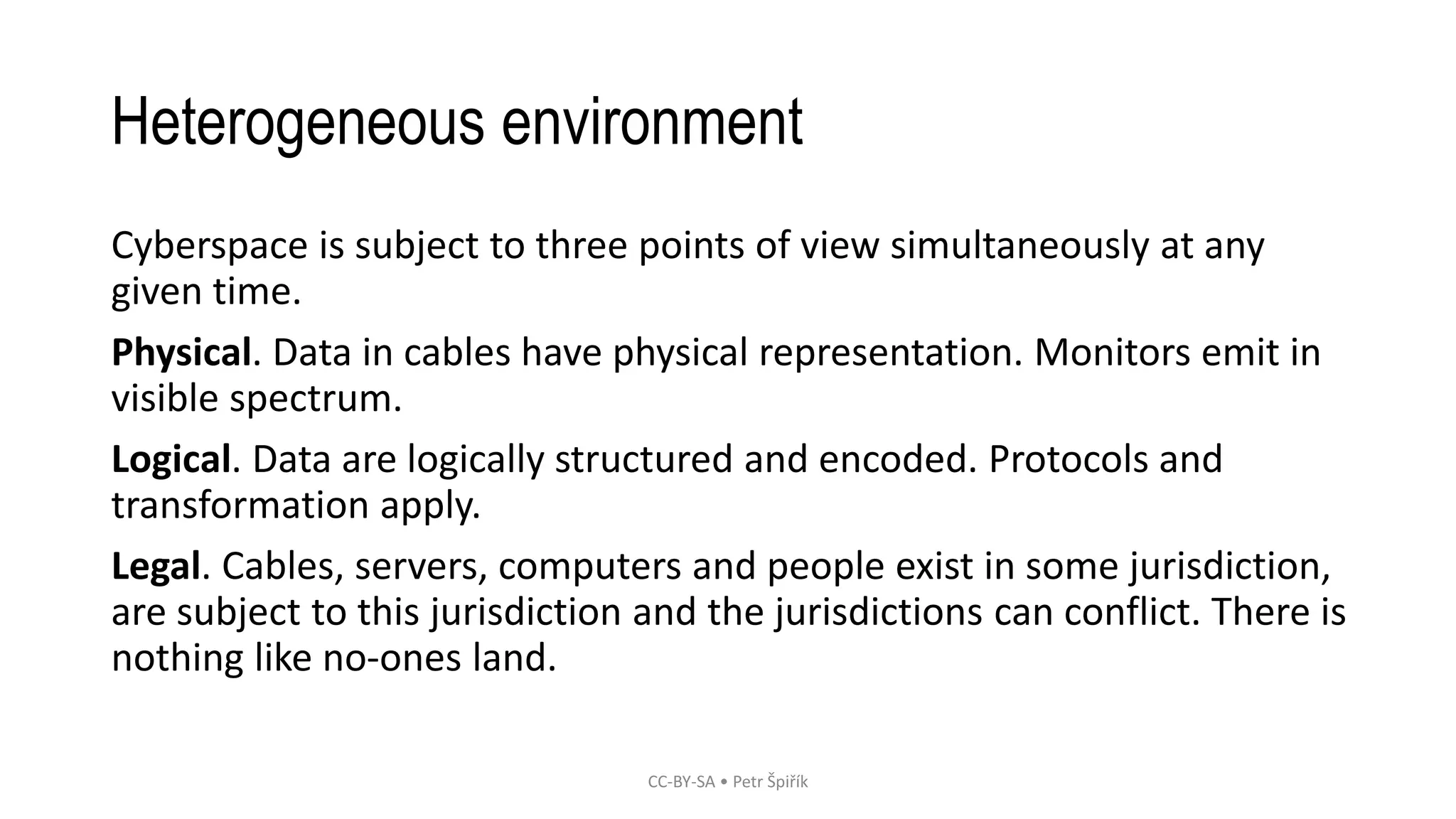
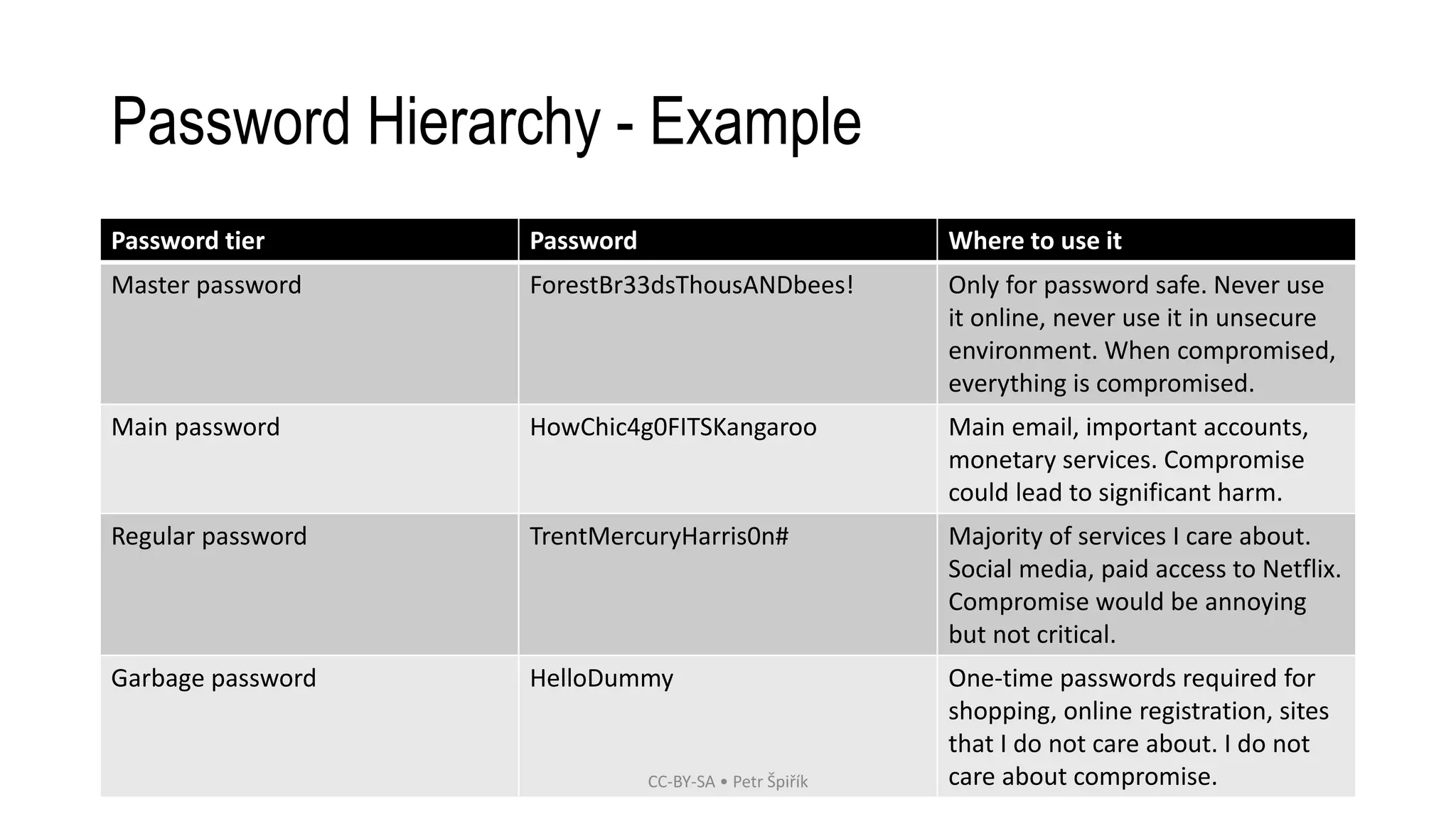
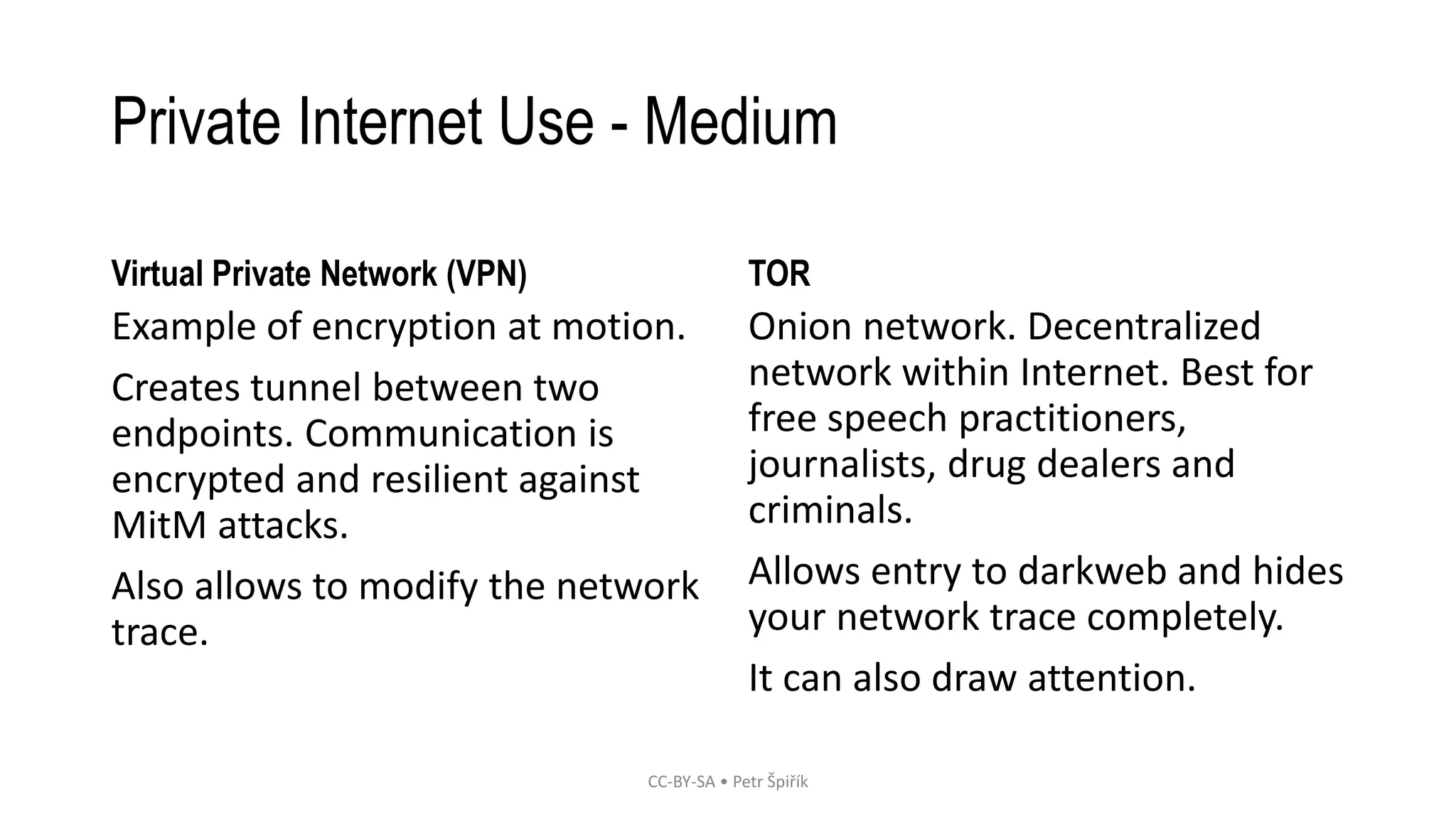
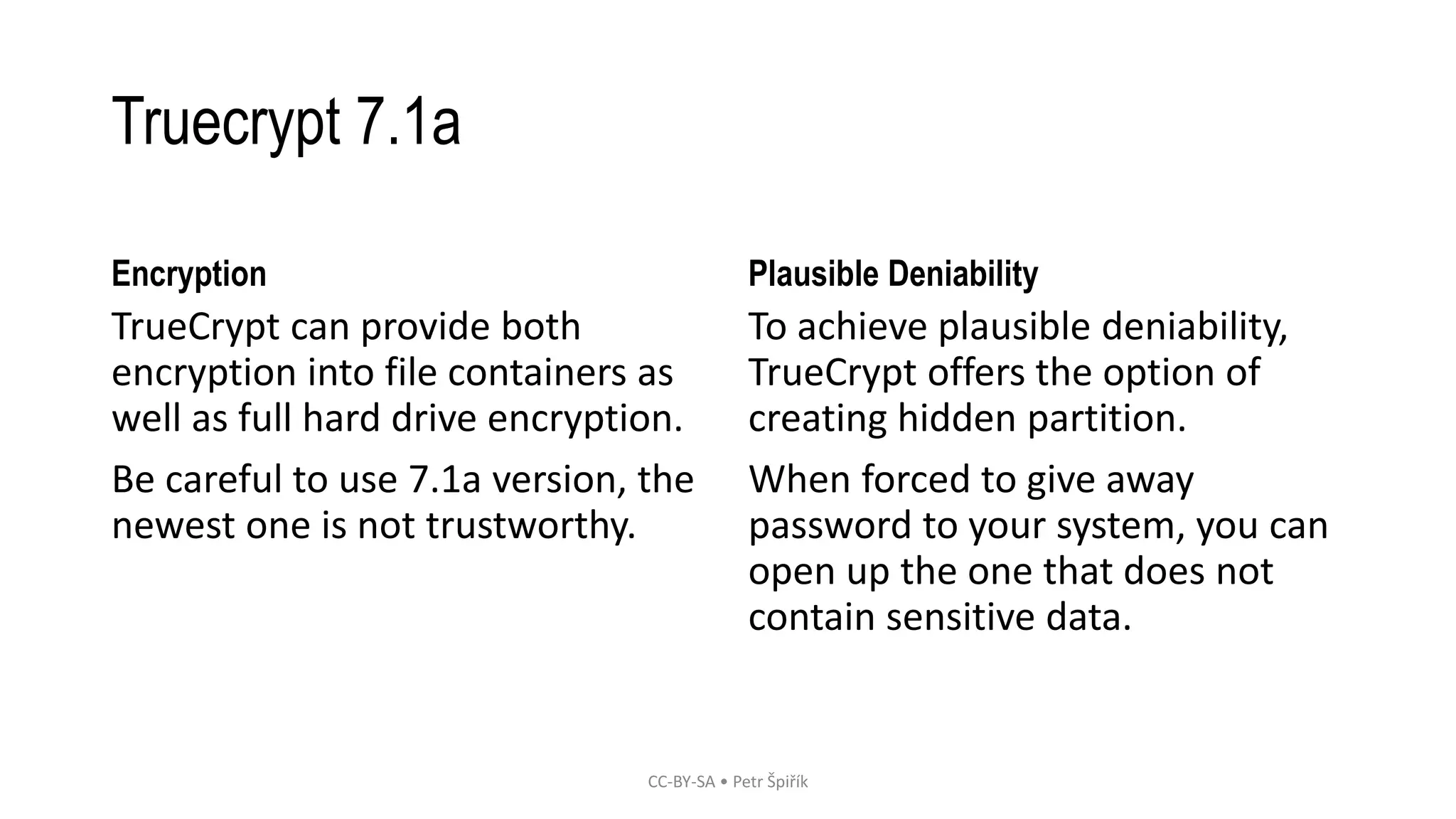
The workshop led by Petr Špiřík focuses on educating participants about operational security (opsec) in cyberspace to mitigate risks from malicious actors. Key topics include understanding cyberspace basics, identifying threat actors, analyzing attack vectors, and implementing risk management strategies. Participants are encouraged to engage actively in discussions and share concerns regarding their digital security practices.