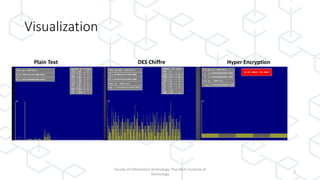
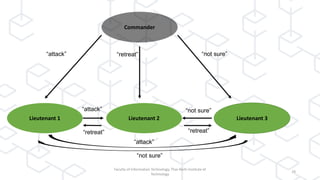
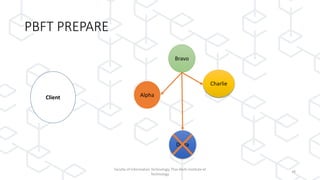
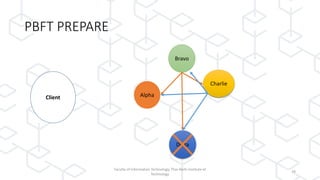
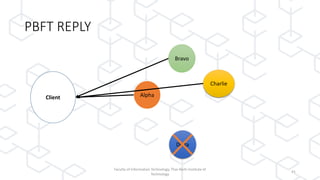
The document discusses concepts related to blockchain technology, specifically the CAP theorem and the Byzantine Generals Problem, as presented in a lecture by Dr. Ferdinand Joe John Joseph at the Thai-Nichi Institute of Technology. The CAP theorem states that in a distributed database, only two of the three guarantees (consistency, availability, and partition tolerance) can be met at the same time, while blockchain focuses on availability and partition tolerance with some level of consistency. Additionally, the Byzantine Generals Problem illustrates the challenges of achieving consensus in distributed systems, applying this to blockchain's mechanism where all nodes must reach agreement despite potential corruption.