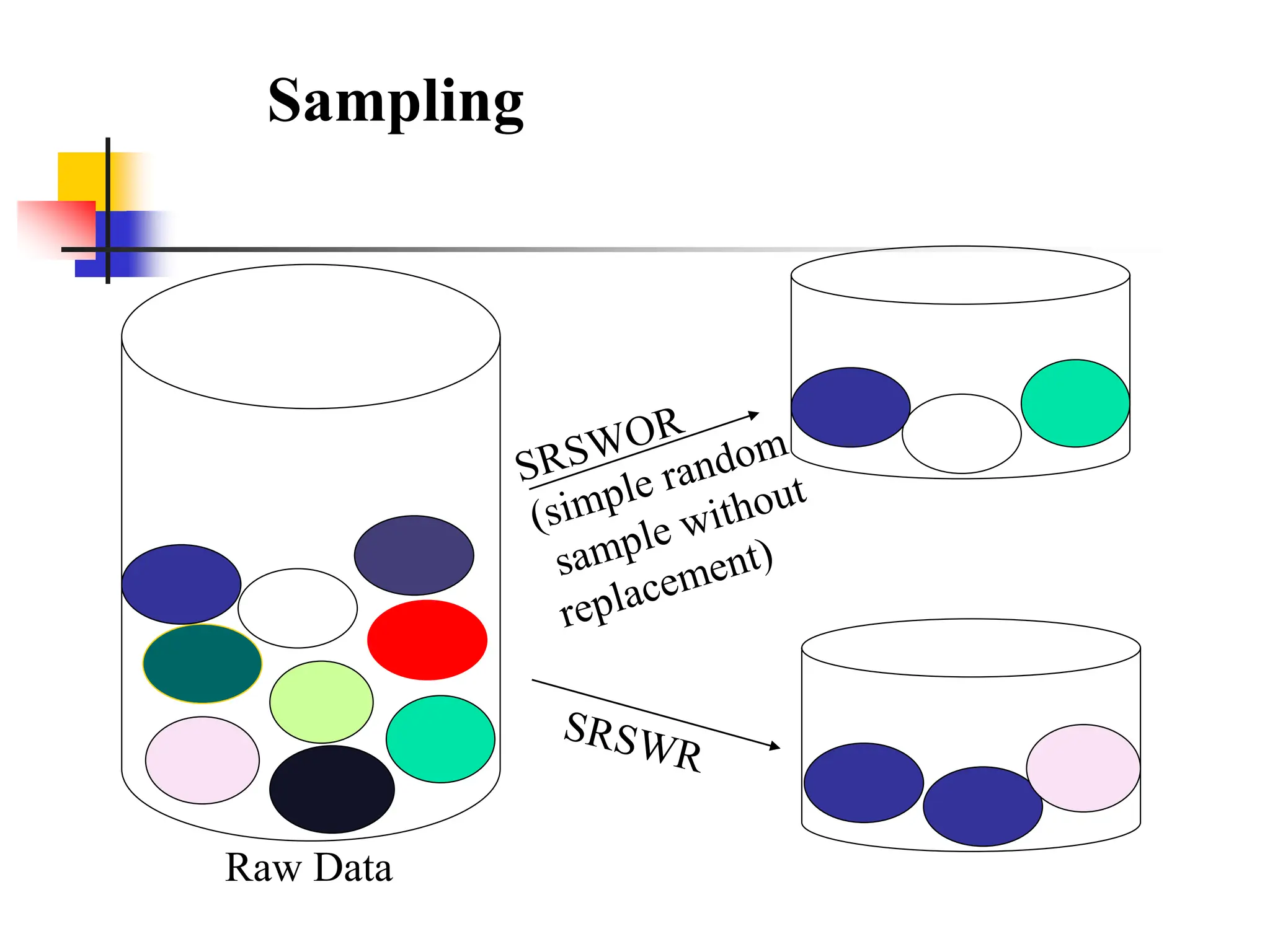
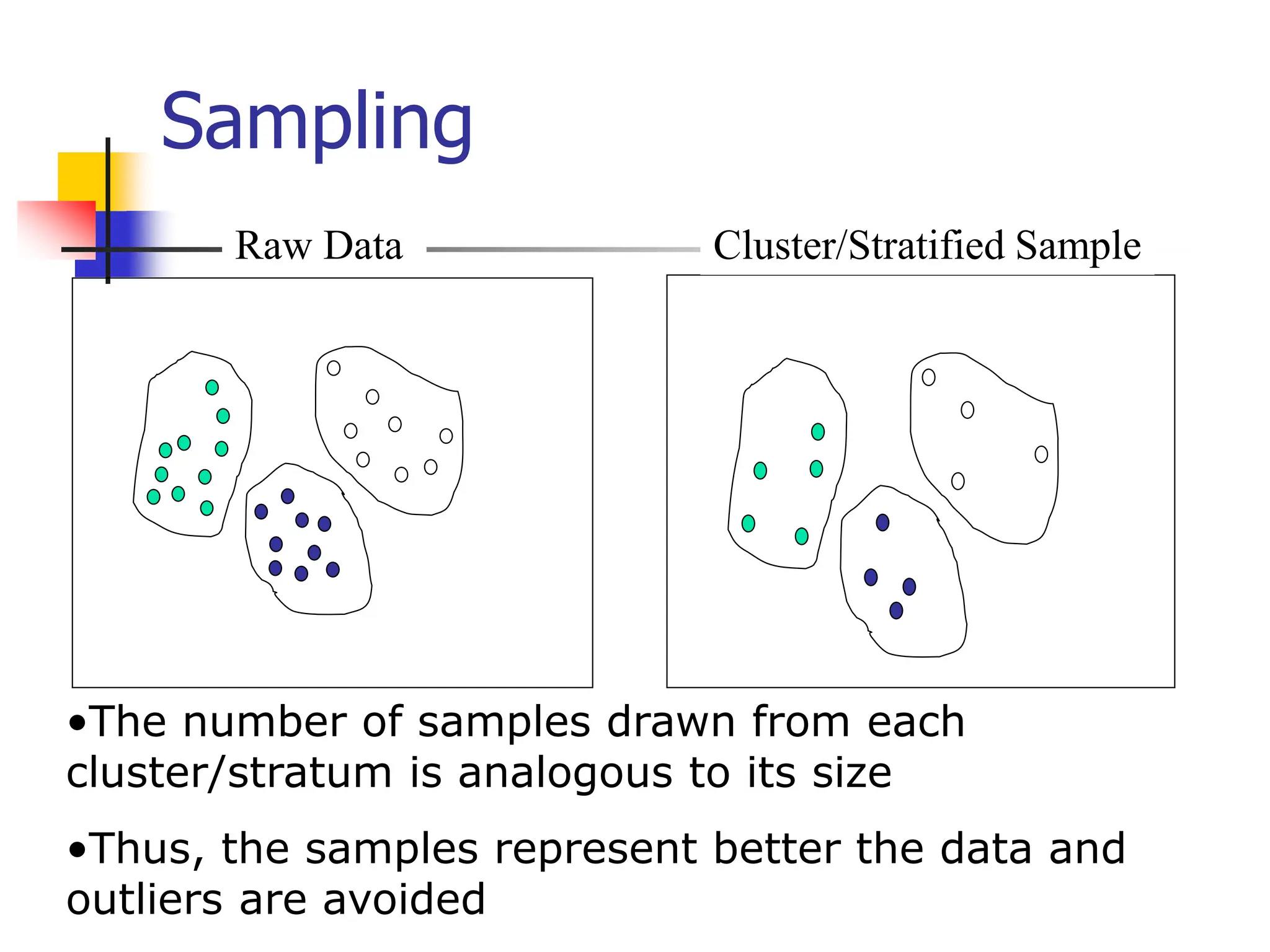
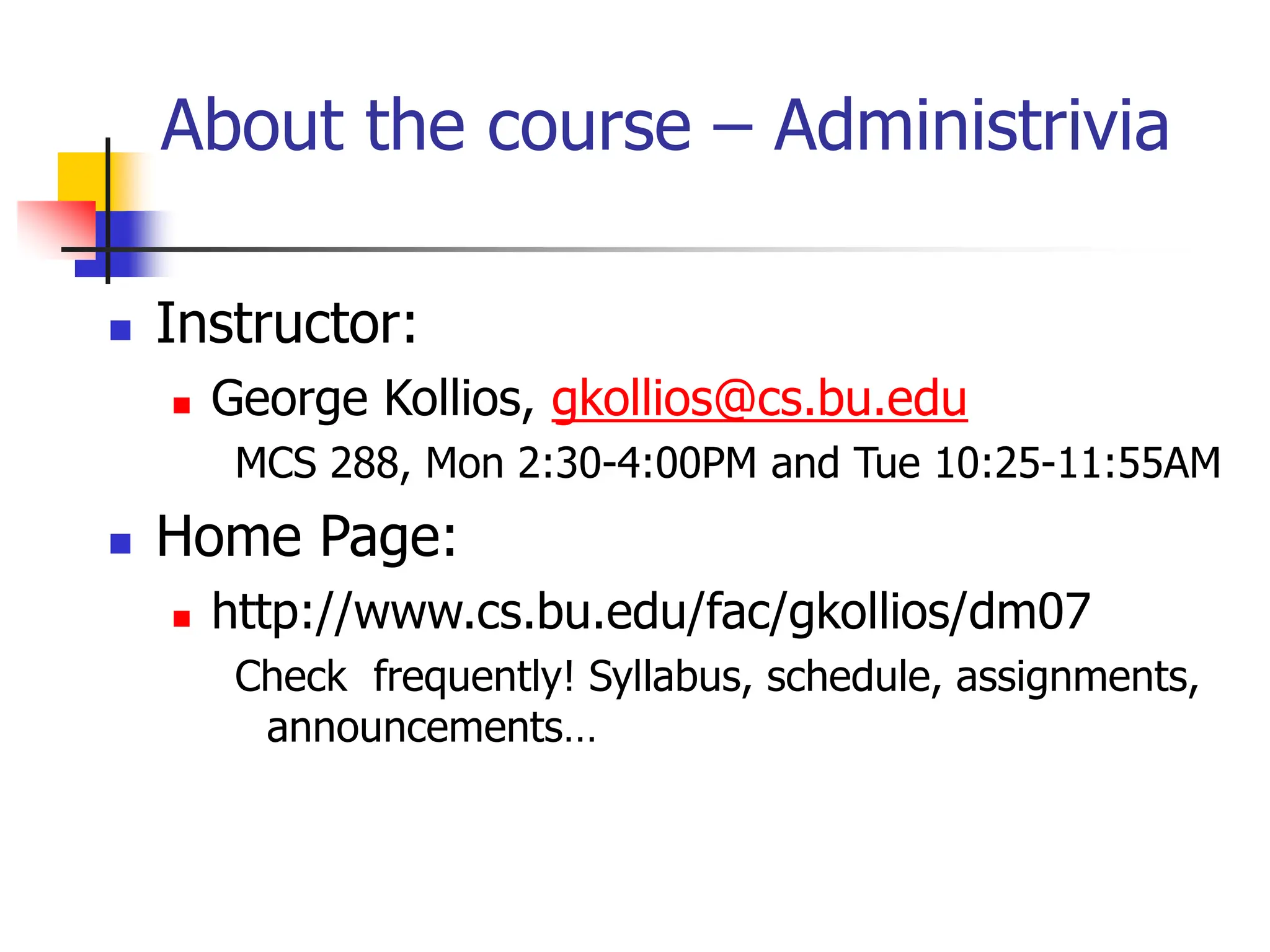
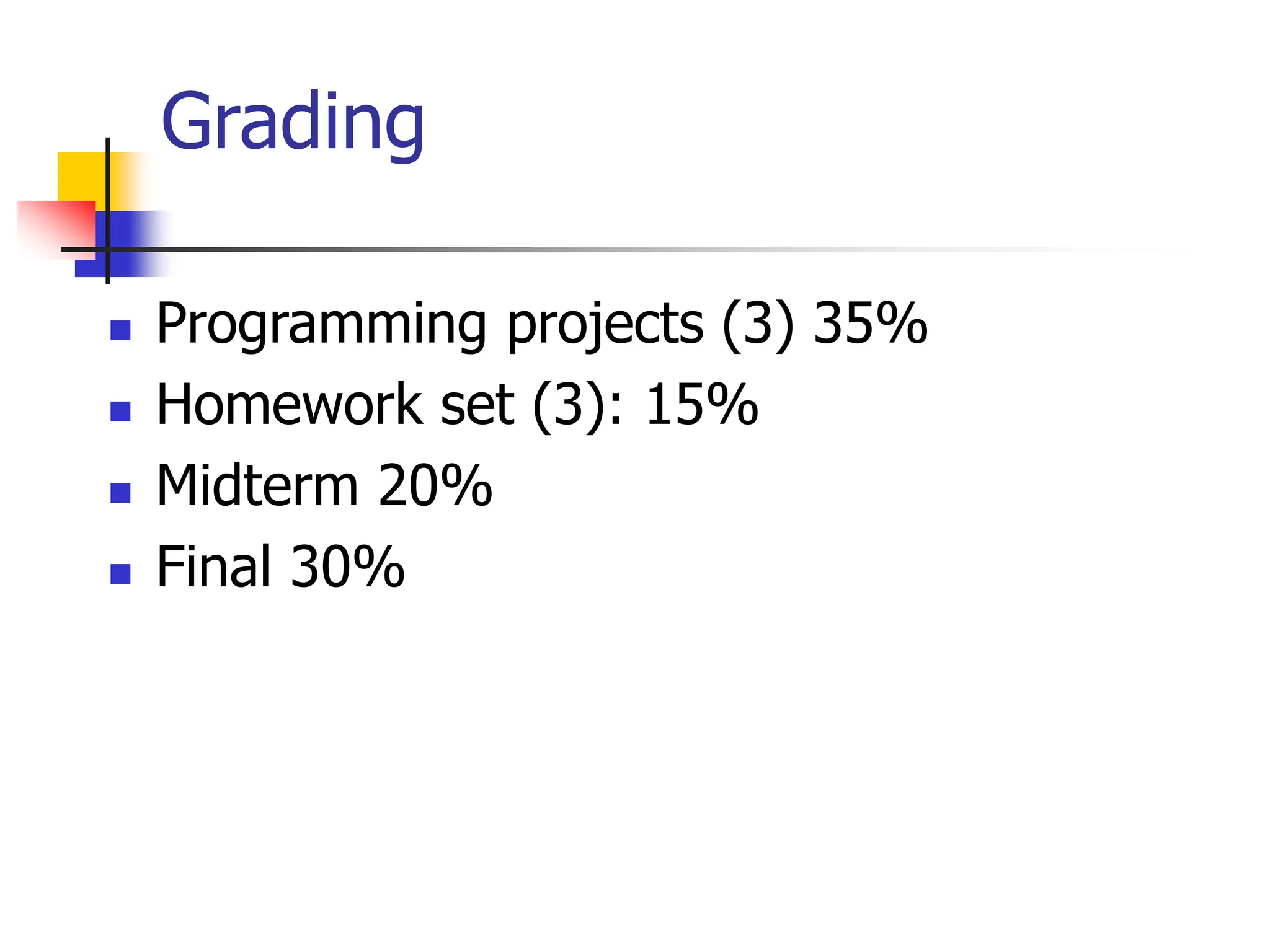
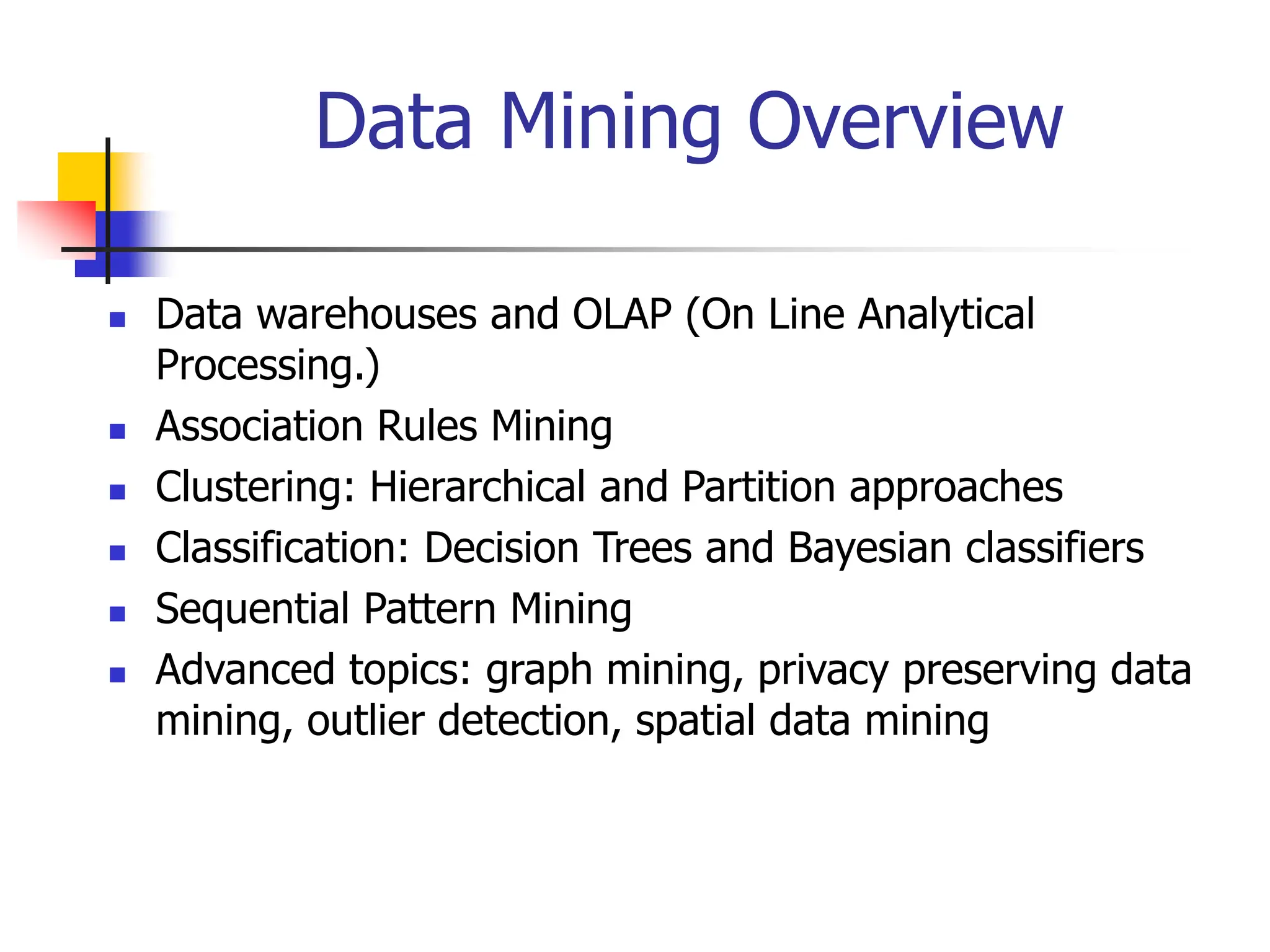
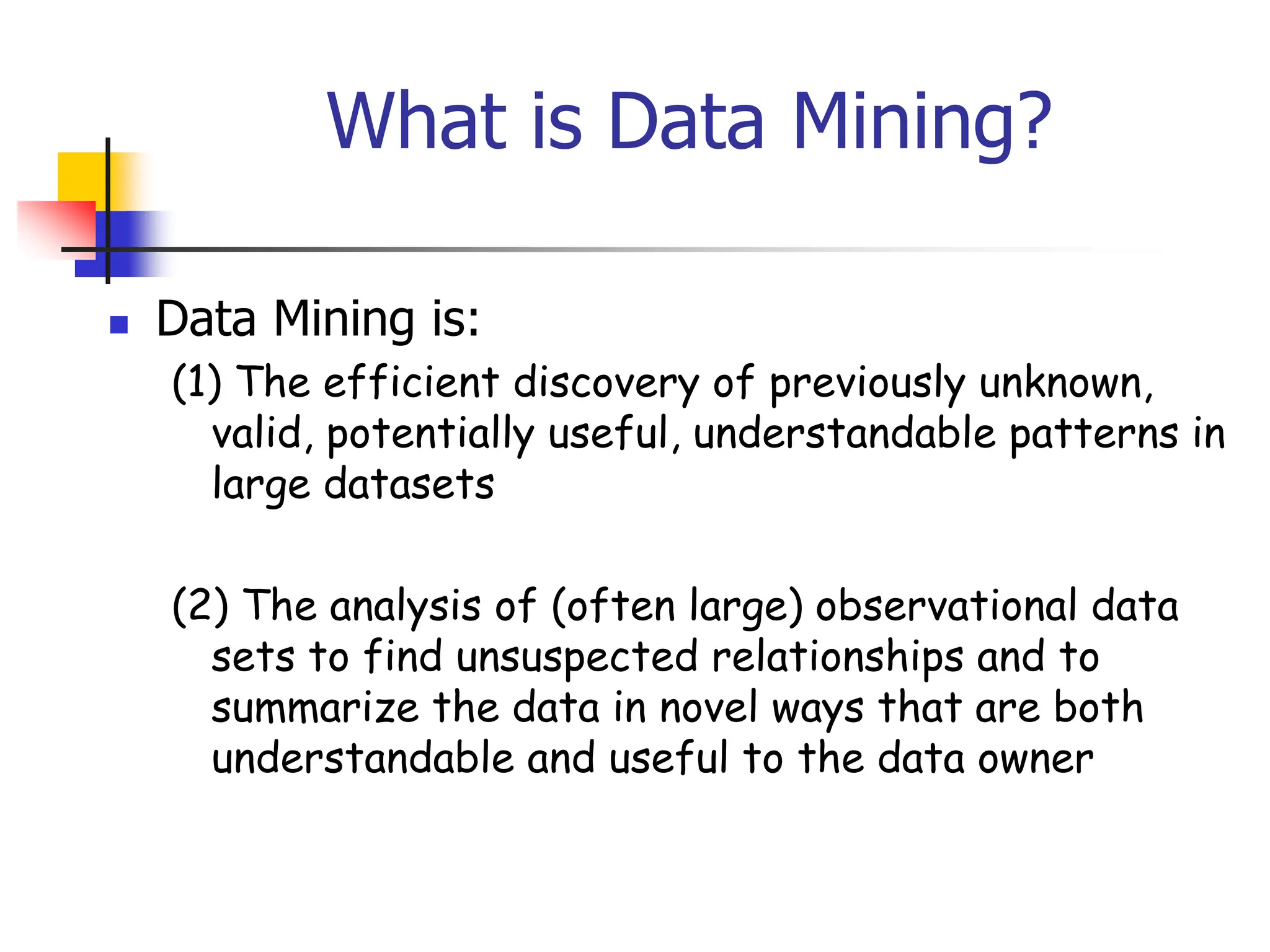
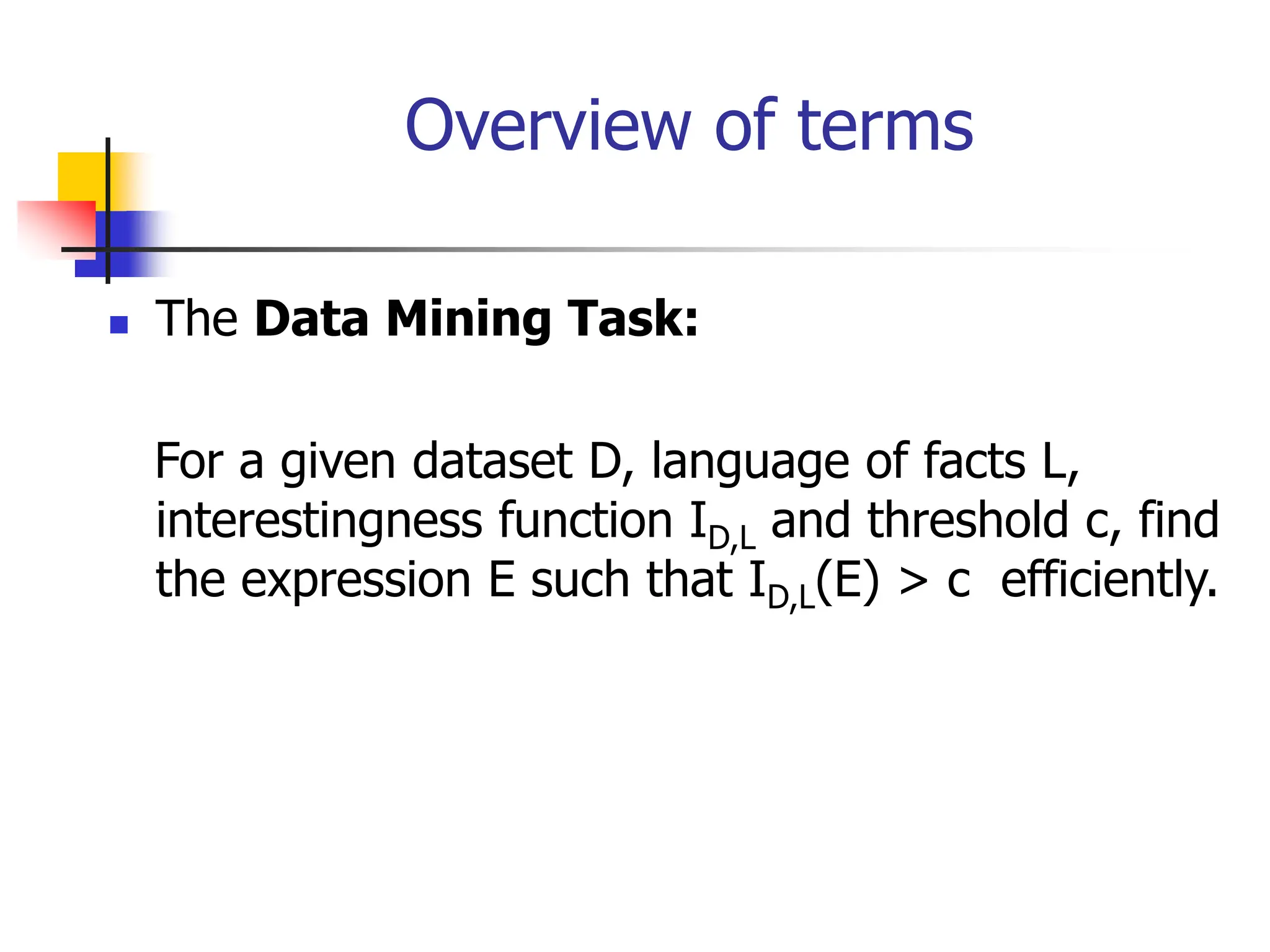
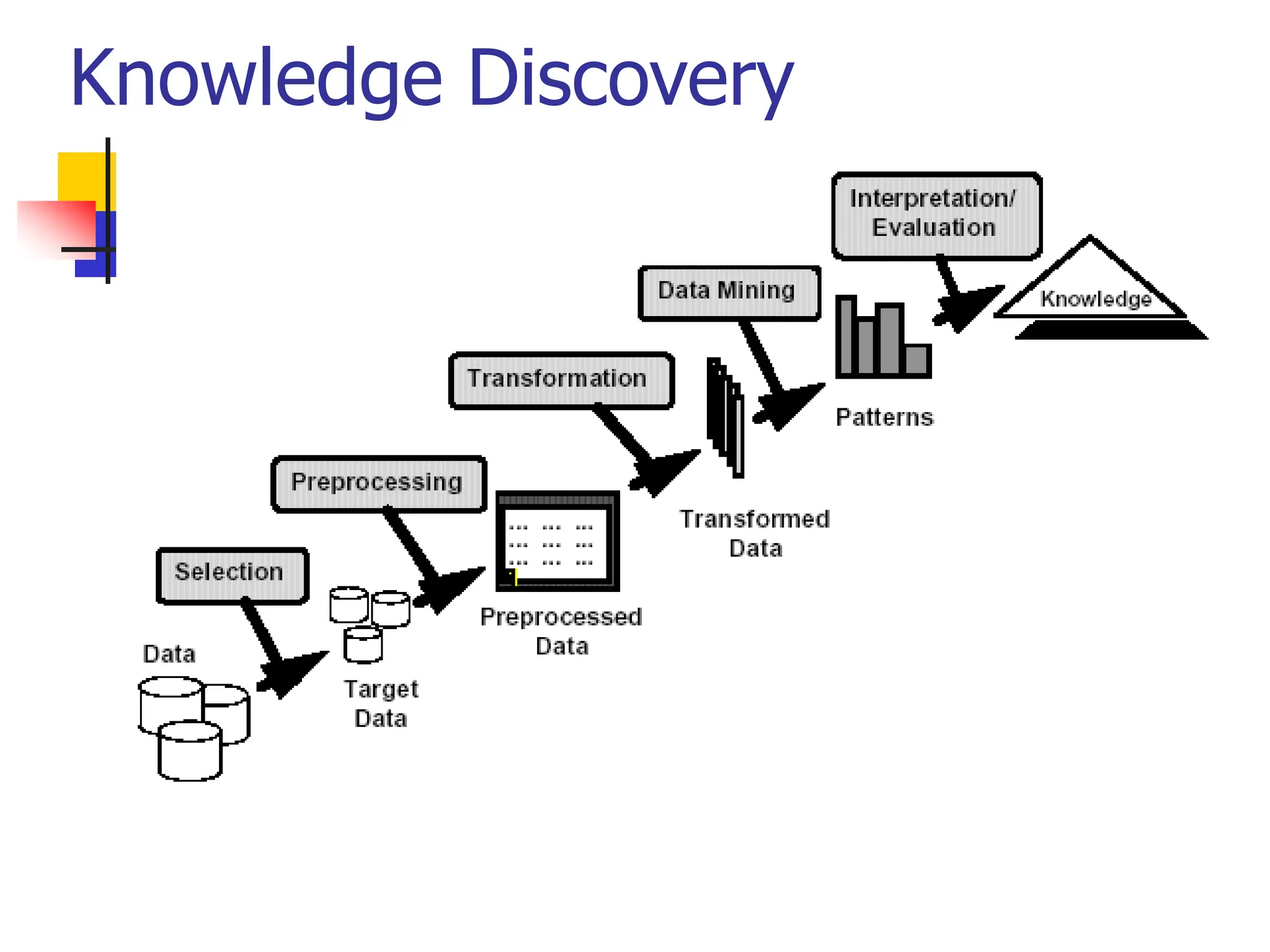
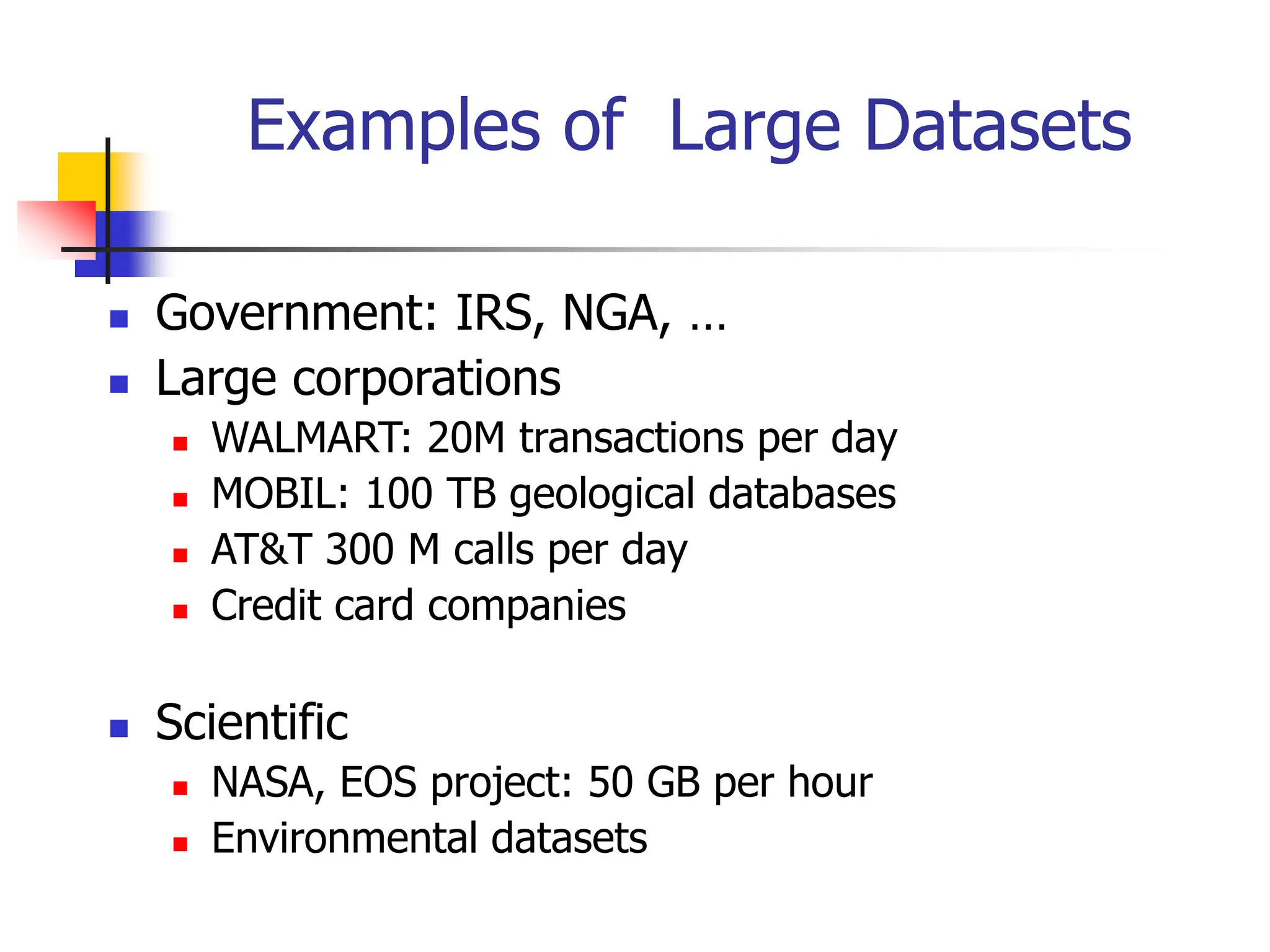
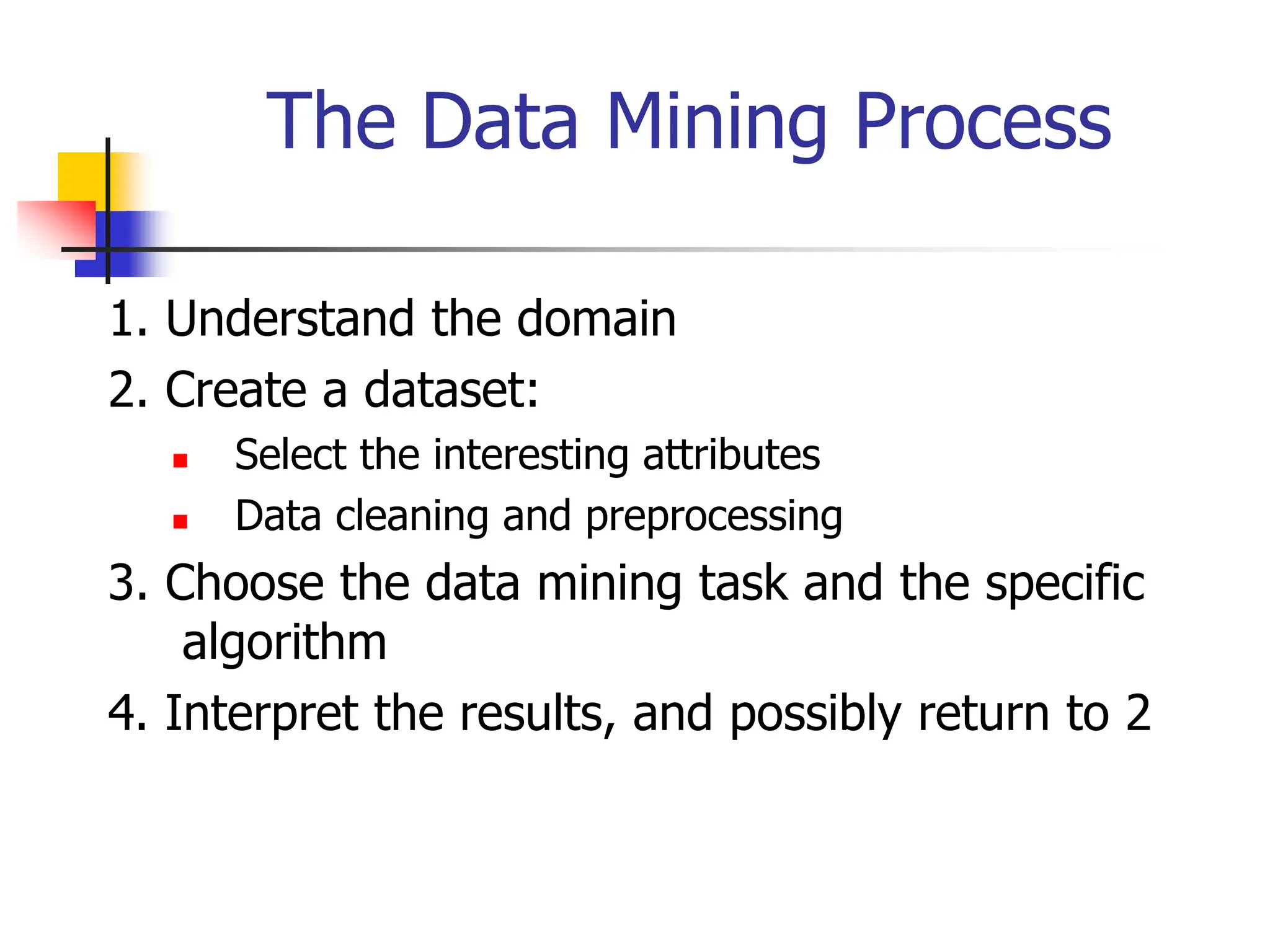
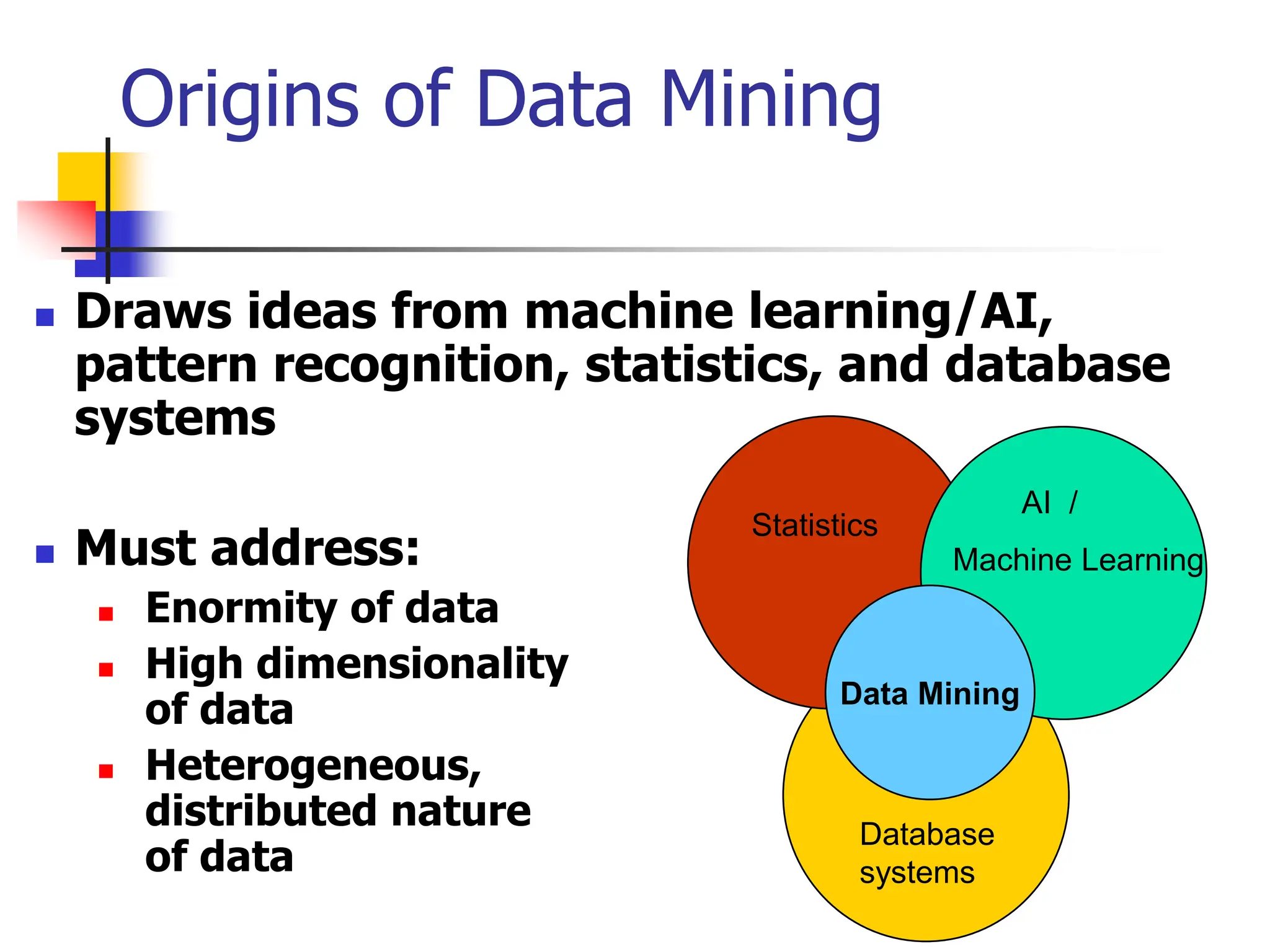
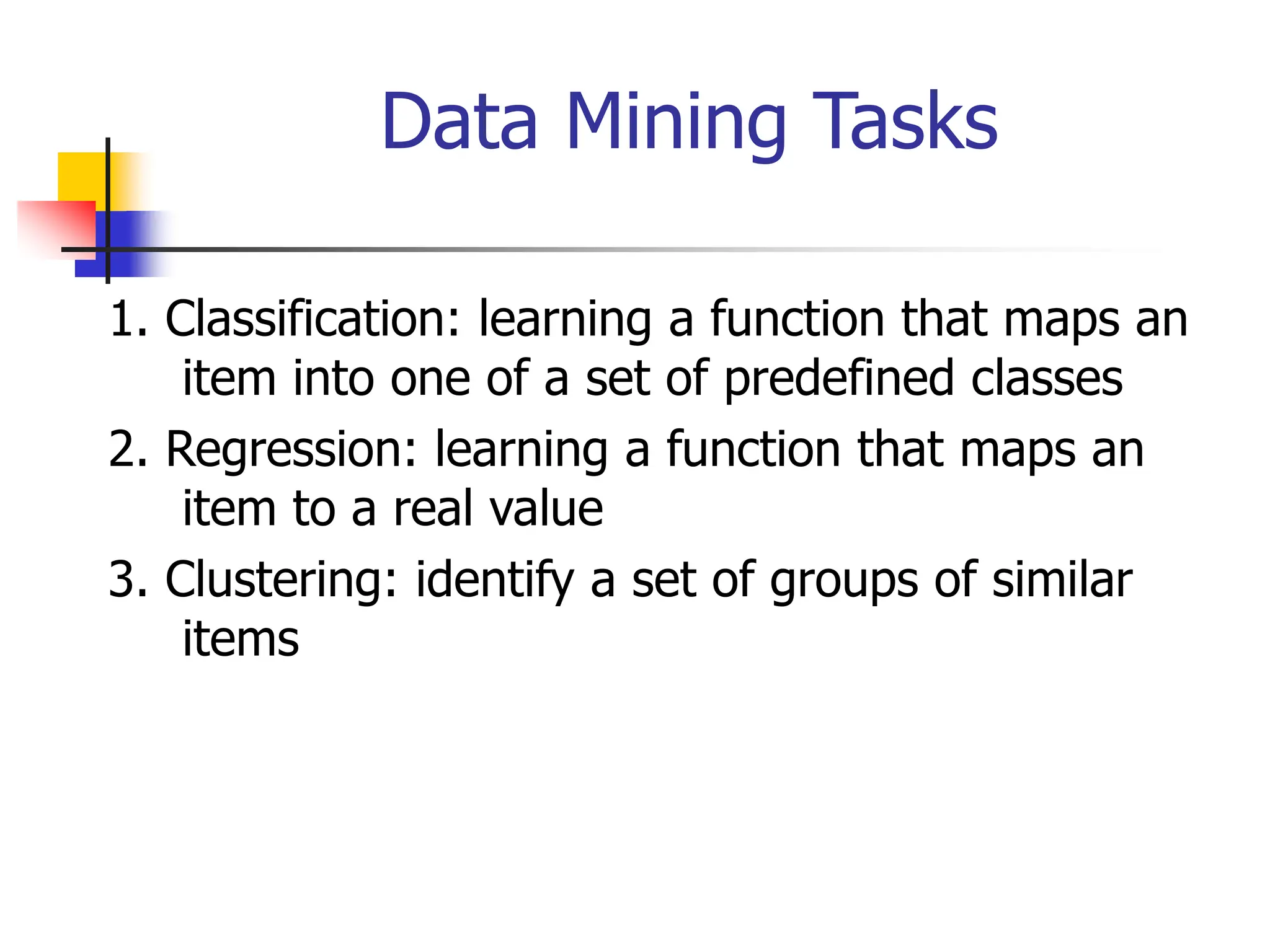
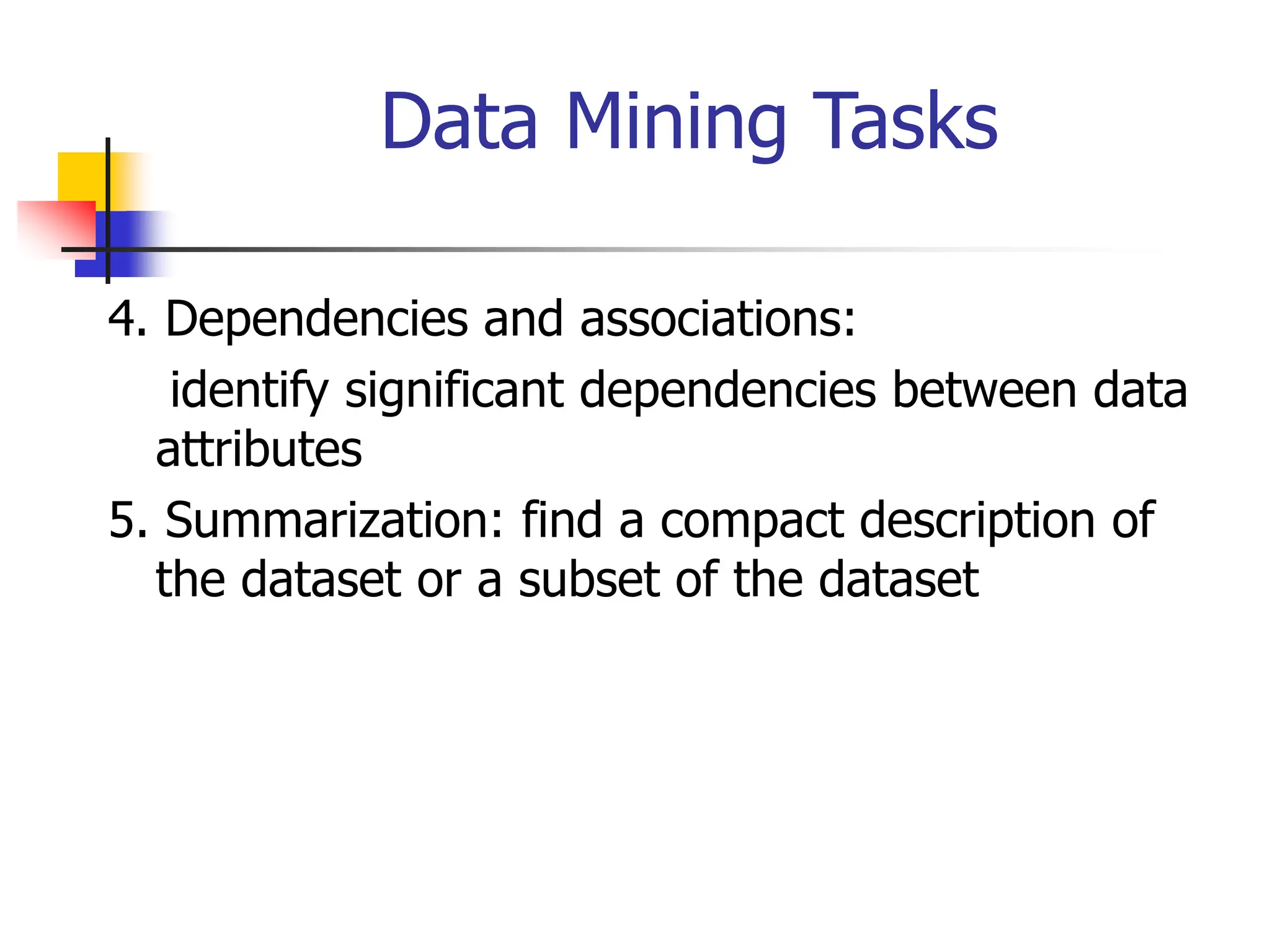
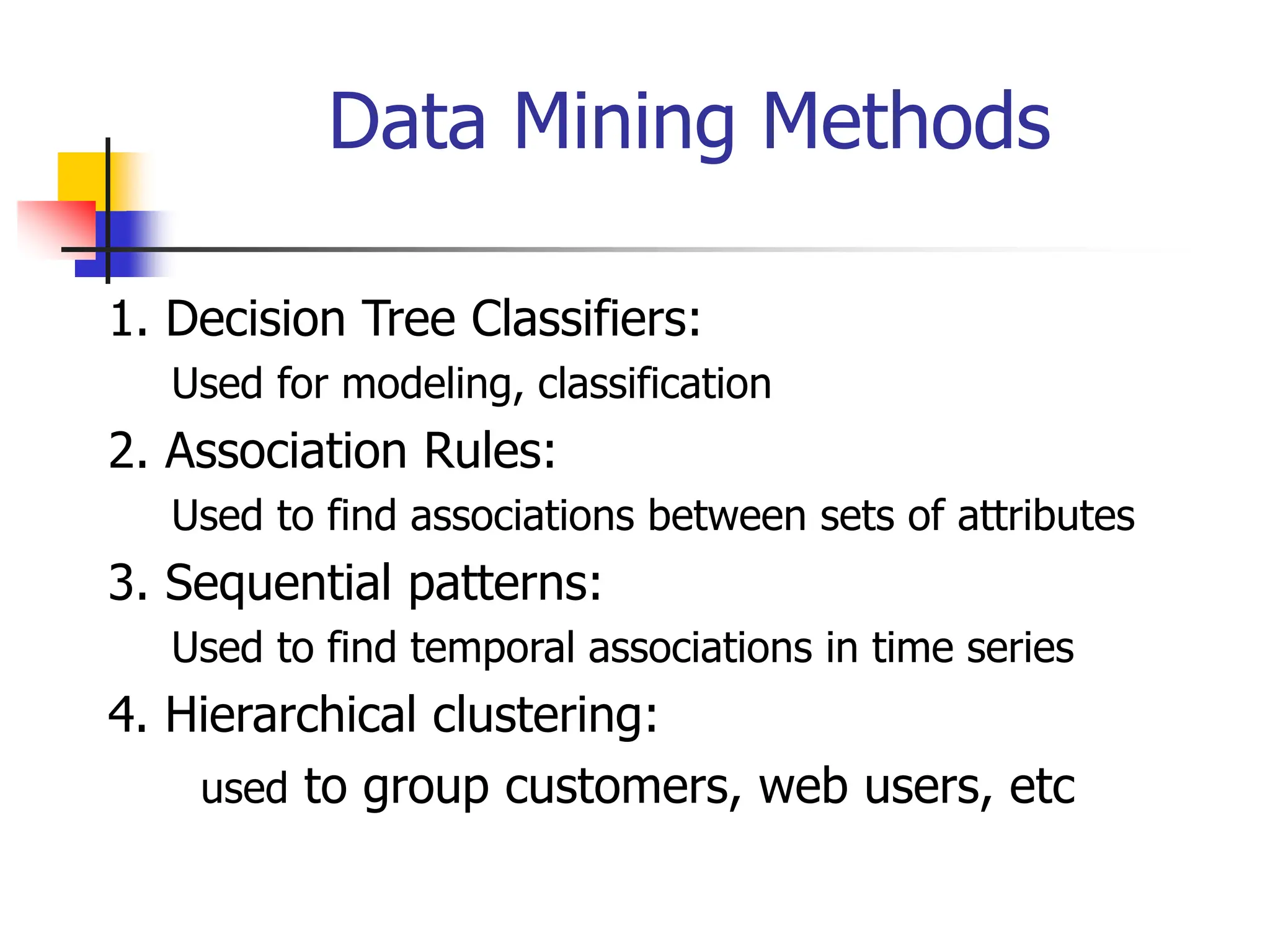
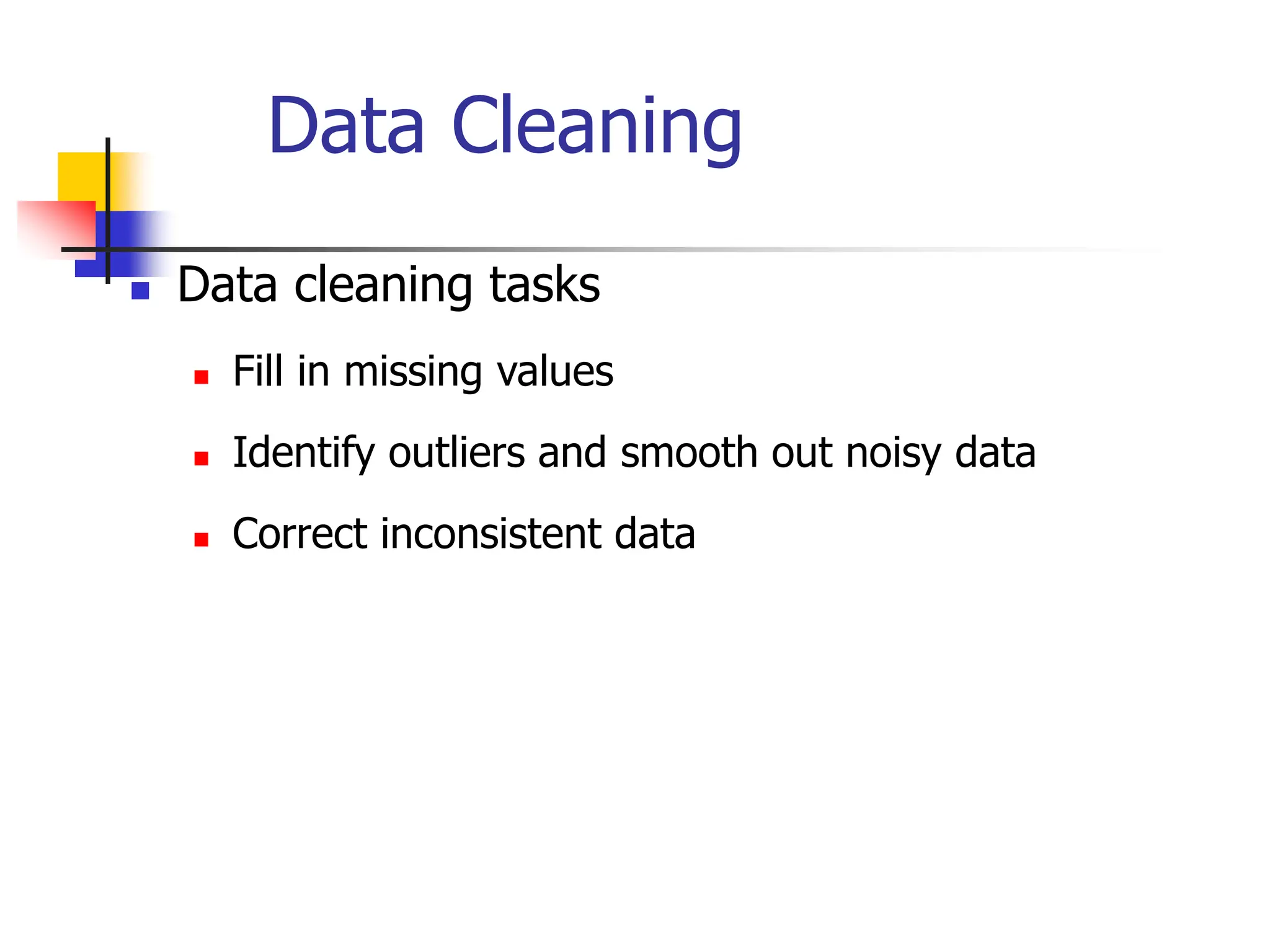
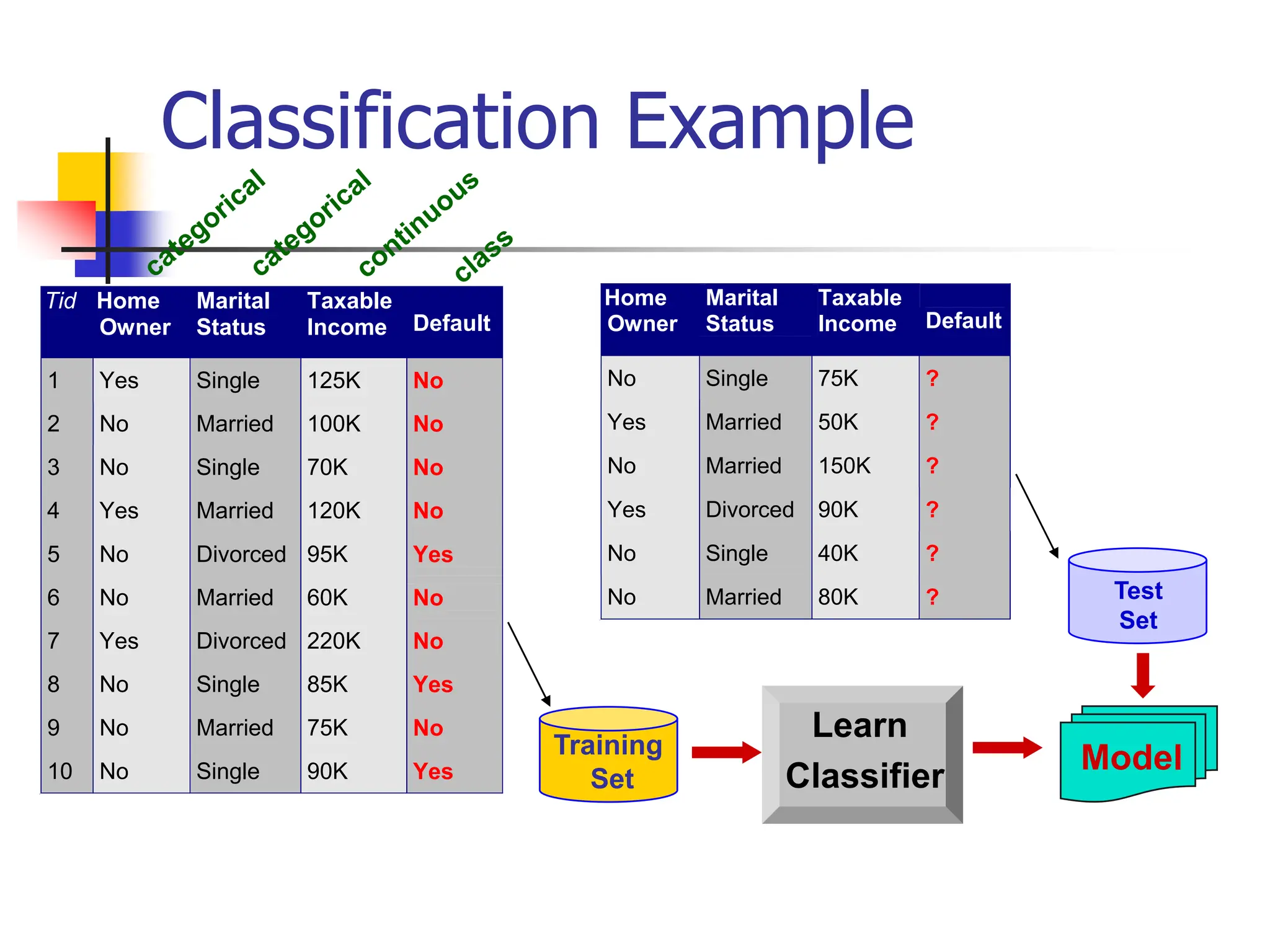
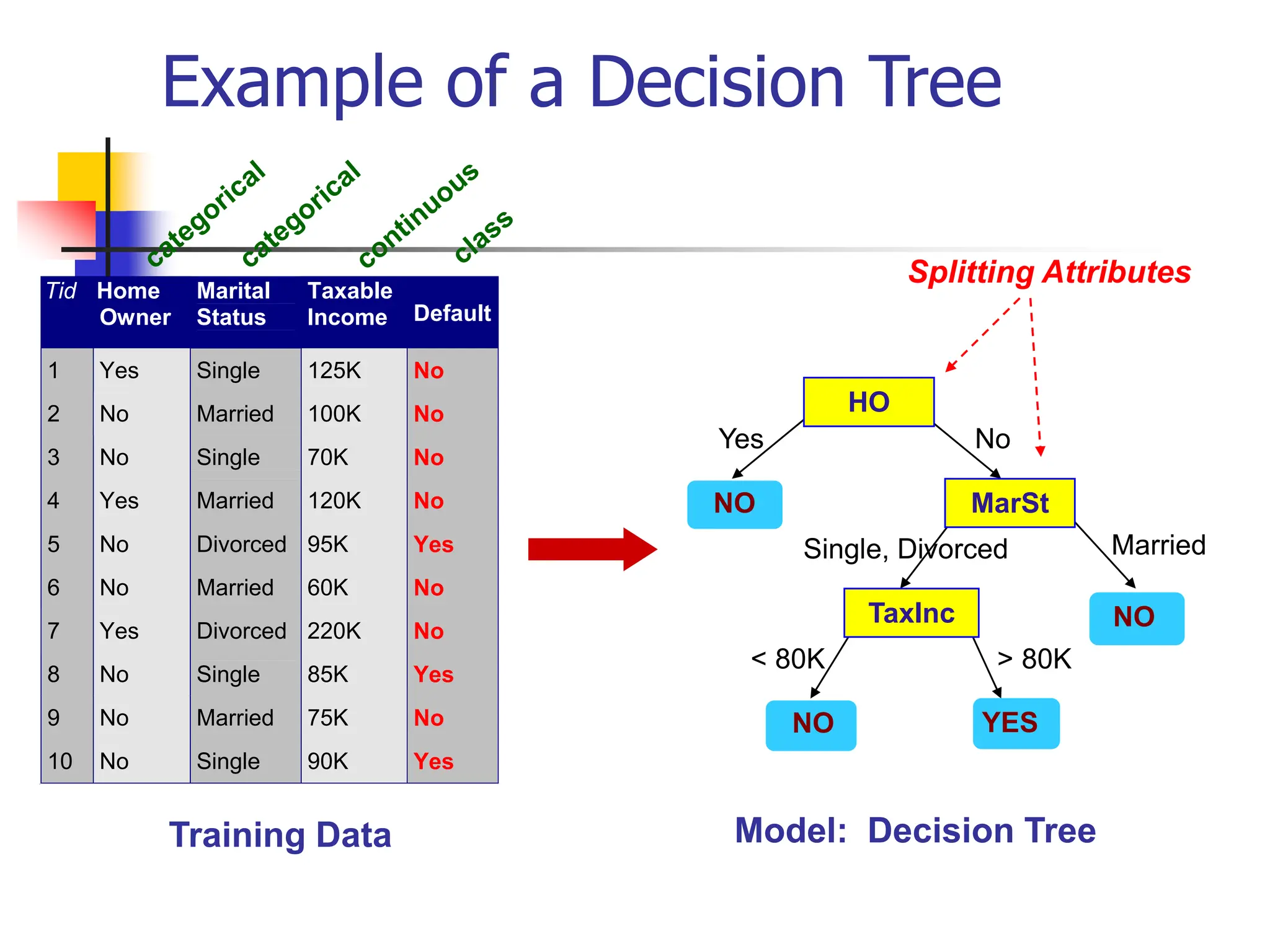
This document provides an overview of a data mining course. It discusses that the course will be taught by George Kollios and will cover topics like data warehouses, association rule mining, clustering, classification, and advanced topics. It also outlines the grading breakdown and schedule. Additionally, it defines data mining and describes common data mining tasks like classification, clustering, and association rule mining. It provides examples of applications and discusses the data mining process.






![Classification: Application 1
Direct Marketing
Goal: Reduce cost of mailing by targeting a set of consumers
likely to buy a new cell-phone product.
Approach:
Use the data for a similar product introduced before.
We know which customers decided to buy and which decided
otherwise. This {buy, don’t buy} decision forms the class attribute.
Collect various demographic, lifestyle, and company-interaction
related information about all such customers.
Type of business, where they stay, how much they earn, etc.
Use this information as input attributes to learn a classifier model.
From [Berry & Linoff] Data Mining Techniques, 1997](https://image.slidesharecdn.com/lect1-240214064901-bf650a29/75/lect1lect1lect1lect1lect1lect1lect1lect1-ppt-24-2048.jpg)