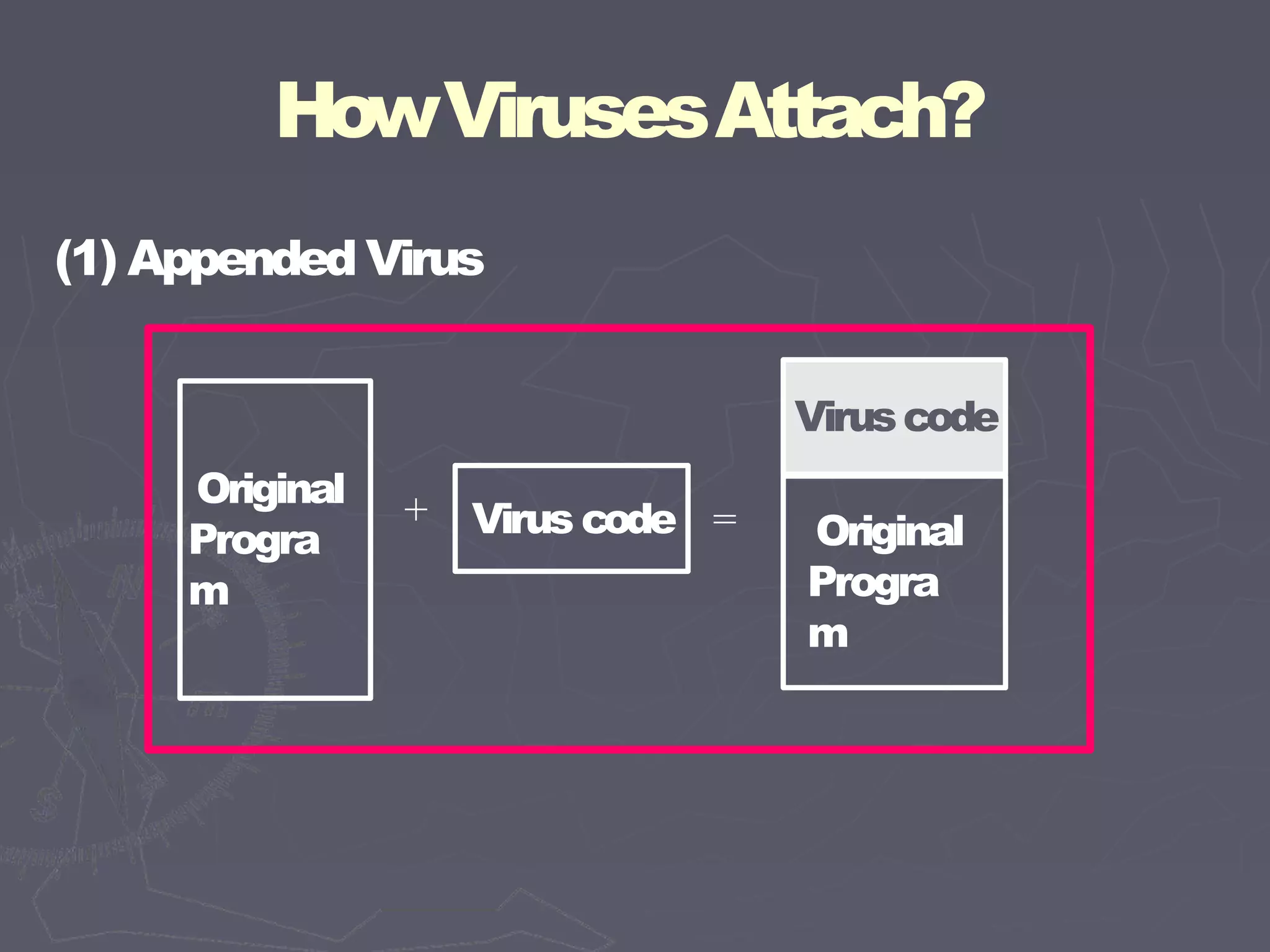
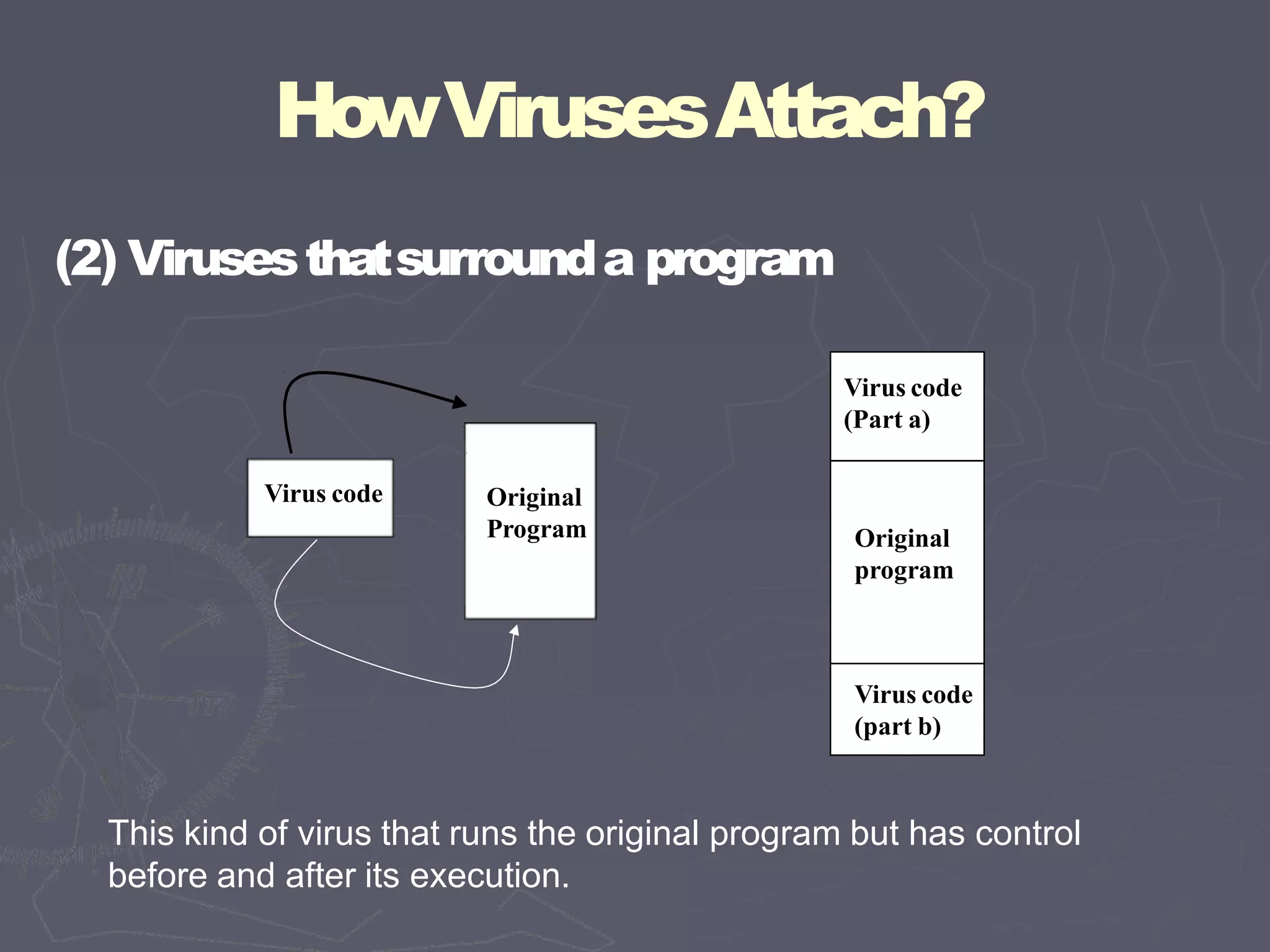
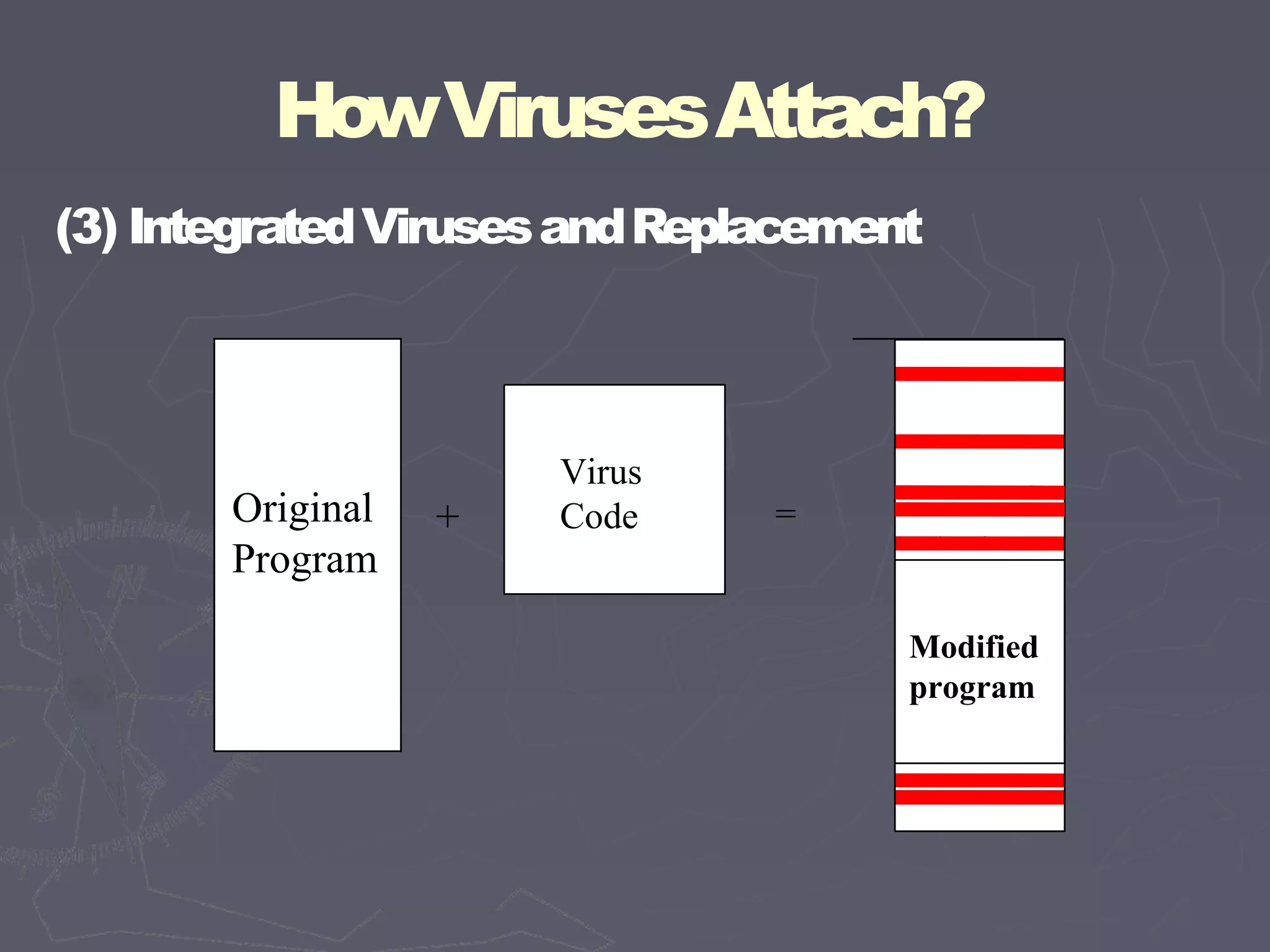
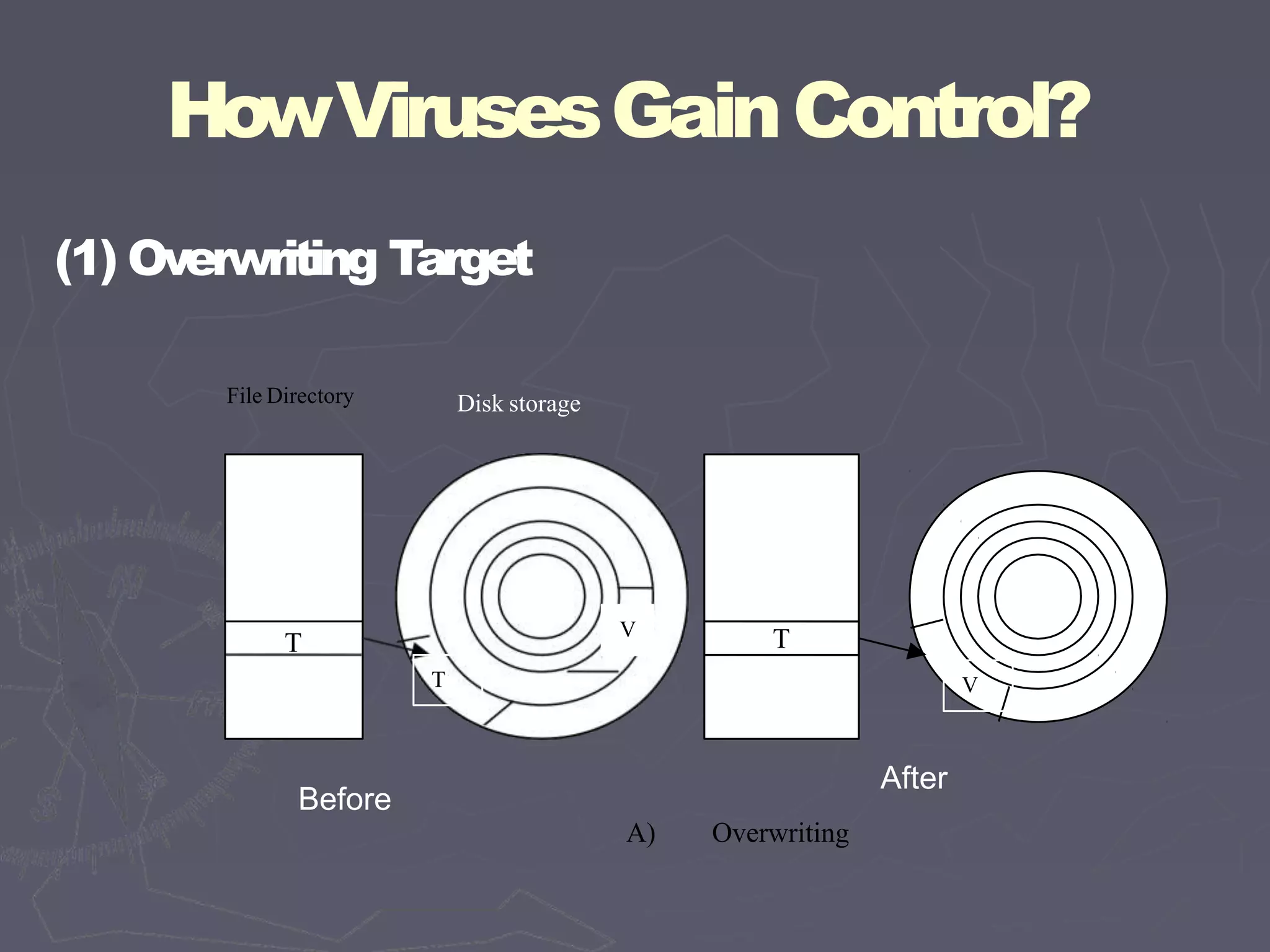
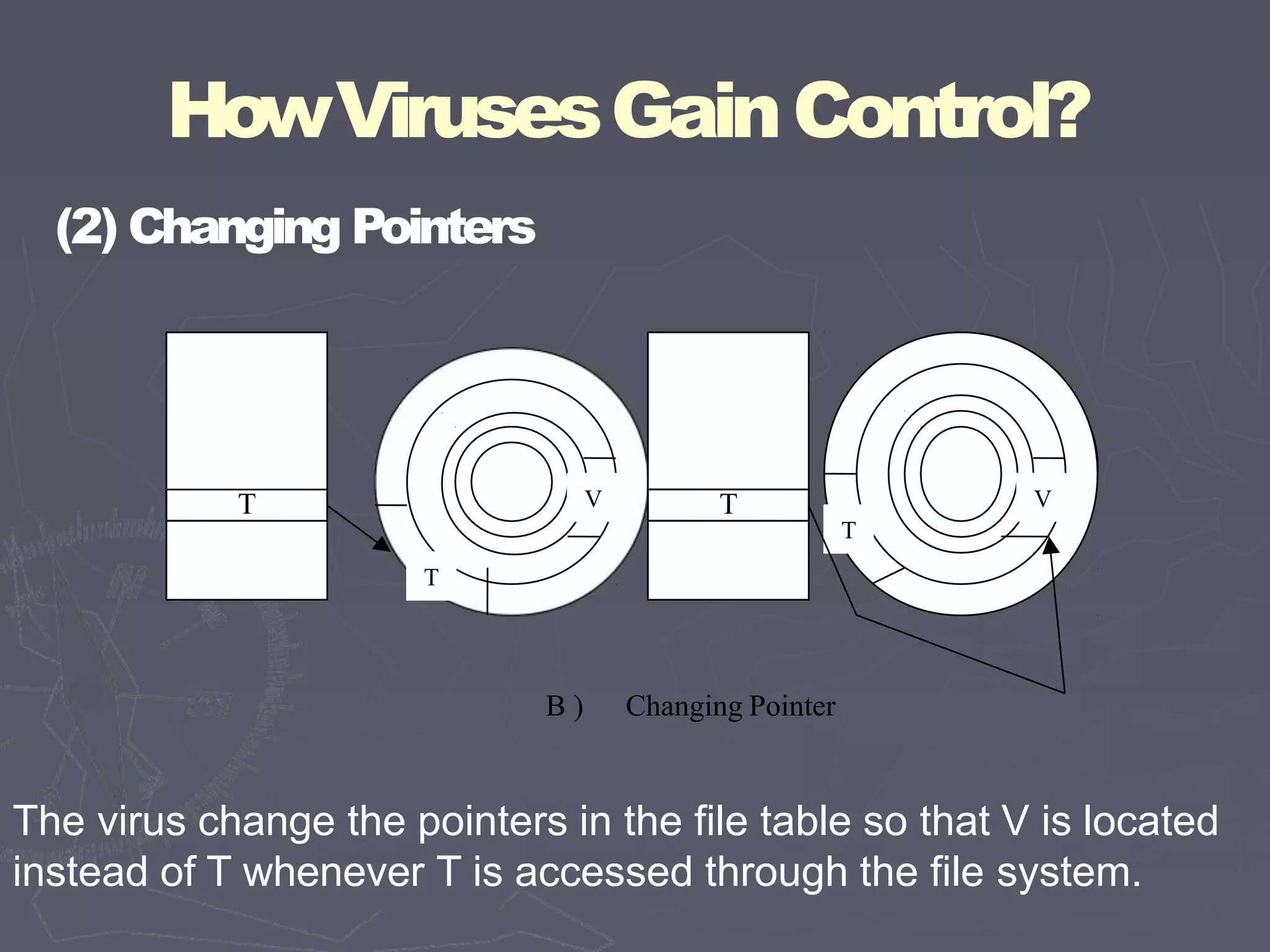
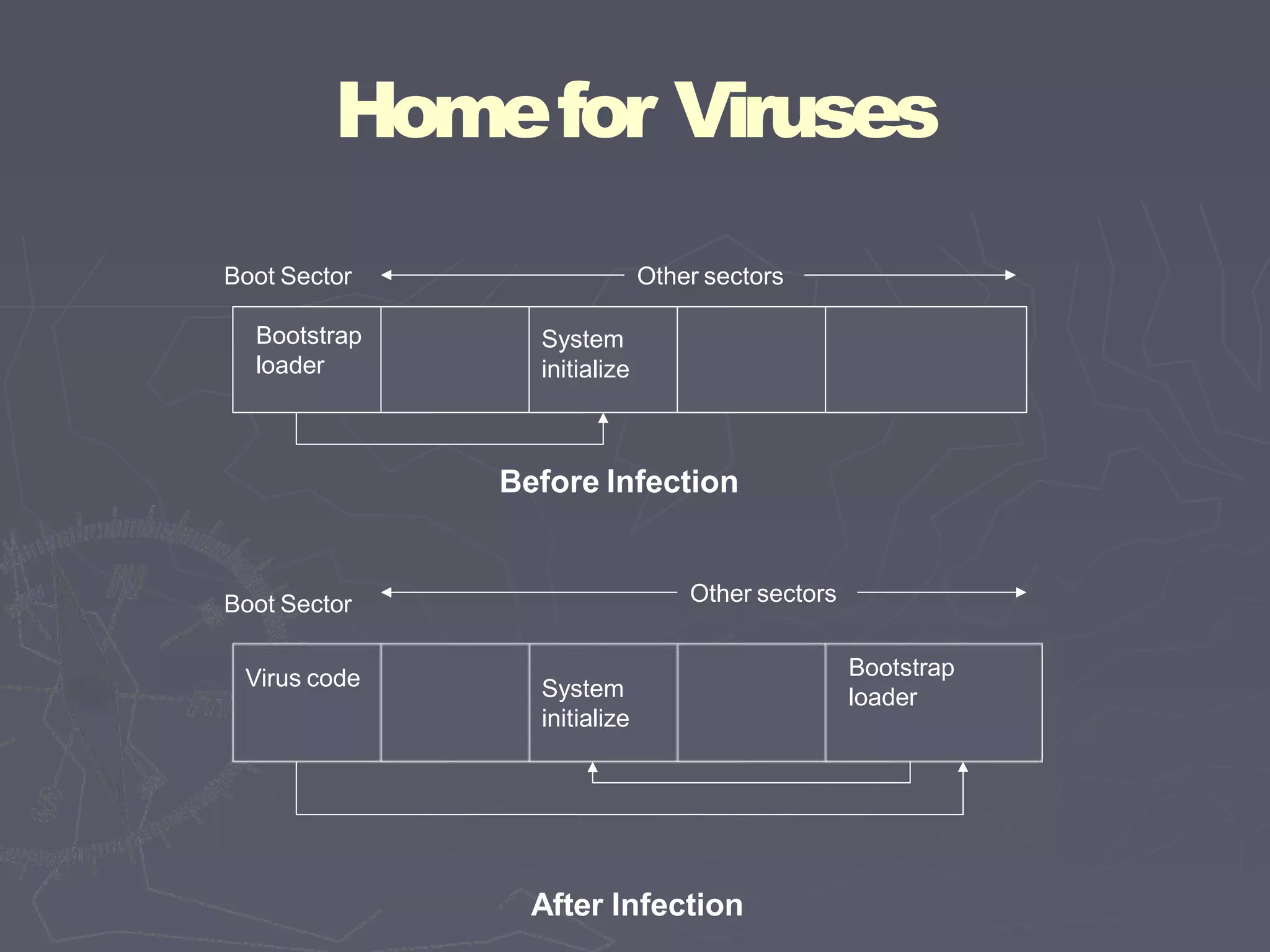
This document discusses different types of malicious code such as viruses, Trojan horses, logic bombs, and worms. It defines each type and provides examples. Viruses can attach to programs by appending code, surrounding code, or integrating with/replacing code. They gain control by overwriting targets or changing pointers. Common places for viruses include boot sectors, system files, and memory-resident programs. Viruses can be detected through their storage patterns, execution patterns, and transmission patterns. Prevention methods include using trusted software sources, testing new software in isolation, and regularly using virus detectors.