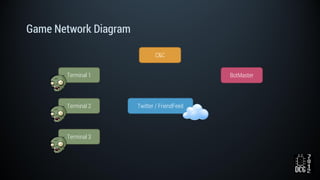
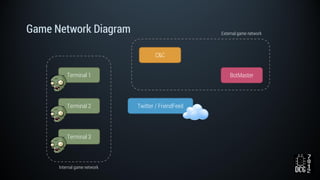
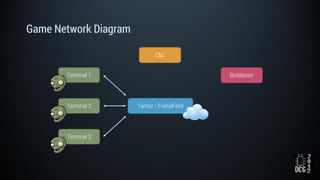
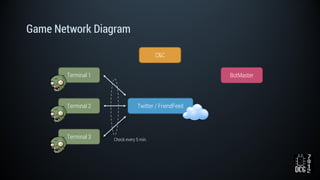
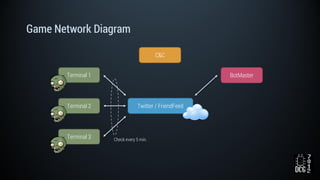
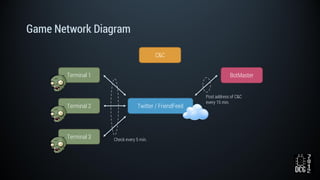
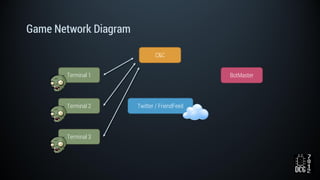
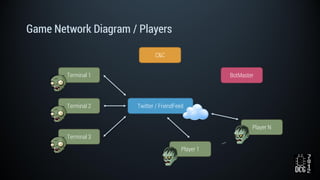
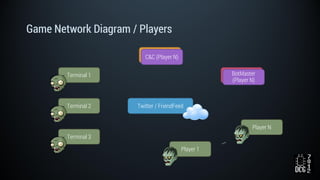
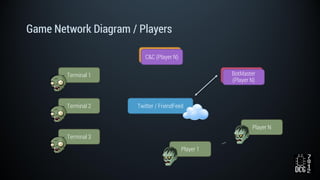
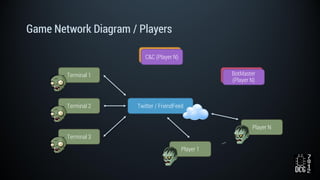
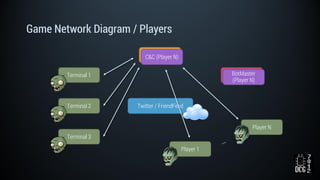
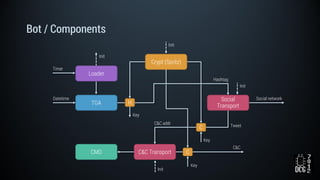
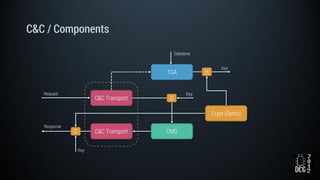
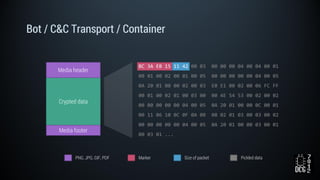
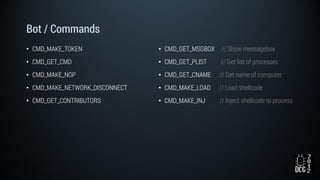
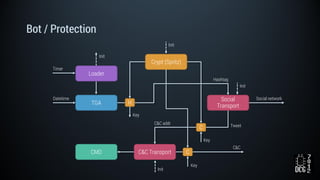
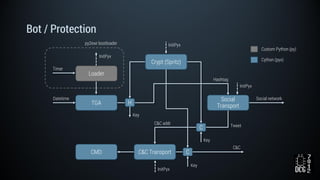
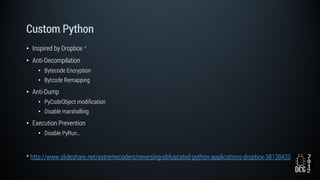
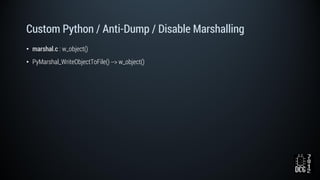
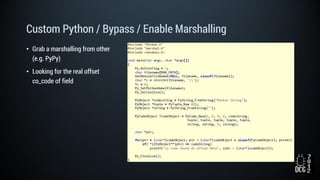
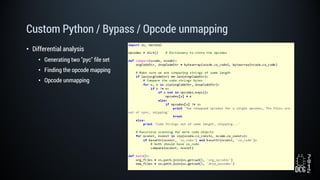
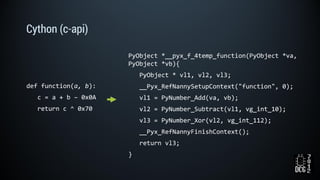
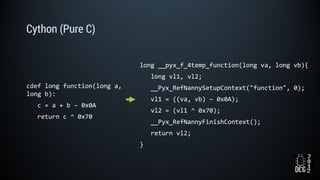
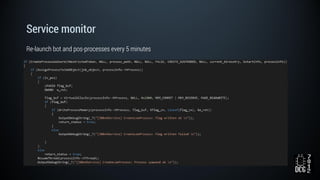
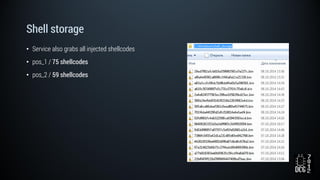
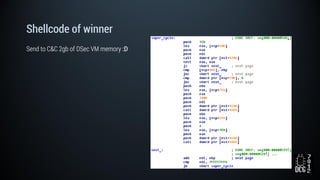
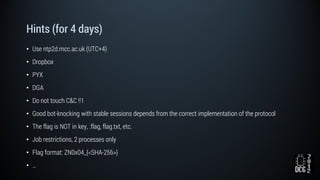
The document describes a simulated hacking game scenario involving a compromised POS terminal infected with malware. It details the components of the botnet architecture including bot nodes, command and control infrastructure, and social media propagation. Diagrams show the network layout and communication channels. The document also examines the bot's components, capabilities, and protection mechanisms such as bytecode encryption and anti-debugging techniques. Hints are provided to help players progress in the game by bypassing defenses and achieving objectives over multiple days.