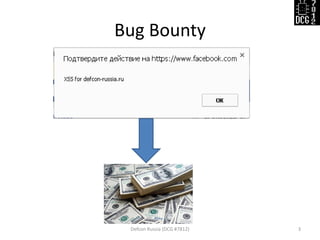
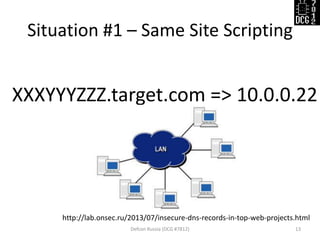
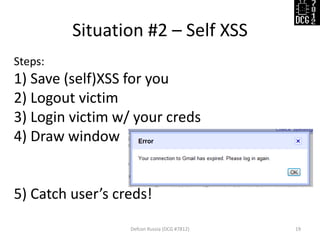
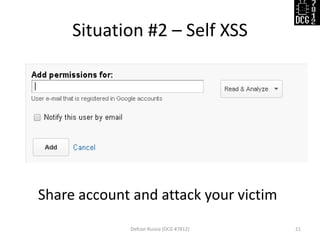
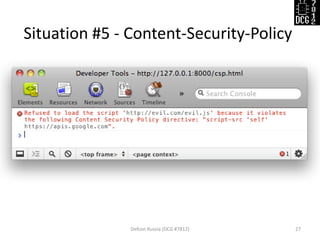
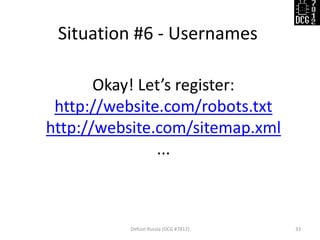
The document discusses various security vulnerabilities demonstrated during the Defcon Russia conference, specifically focusing on issues like Cross-Site Scripting (XSS), CSRF, and the impact of improper cookie settings. Several real-world scenarios are provided to illustrate these vulnerabilities, including the consequences of self-XSS and HTTP referer misuse. It also highlights the partial support of Content Security Policy across different browsers and concludes with an invitation for questions from the audience.