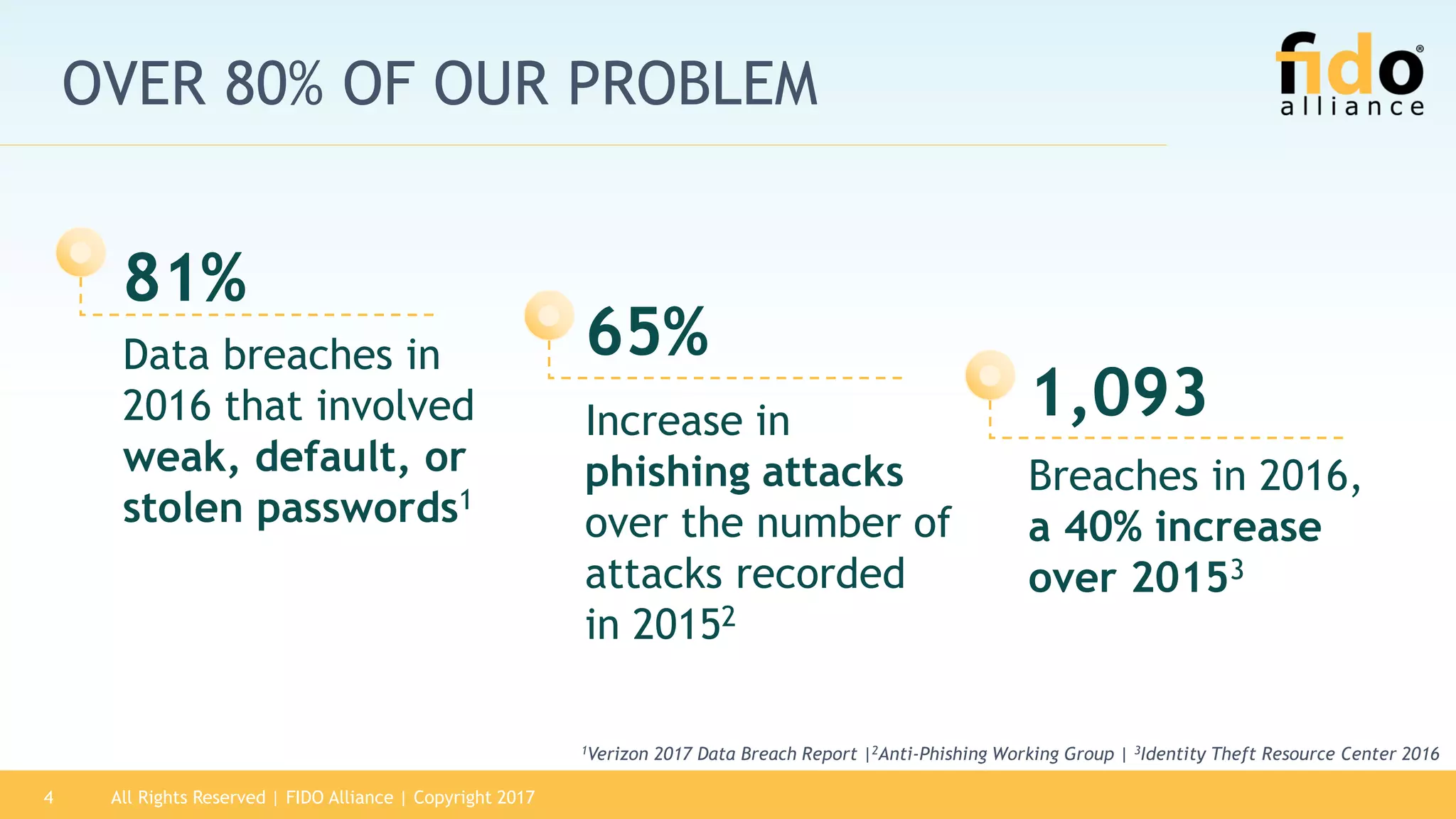
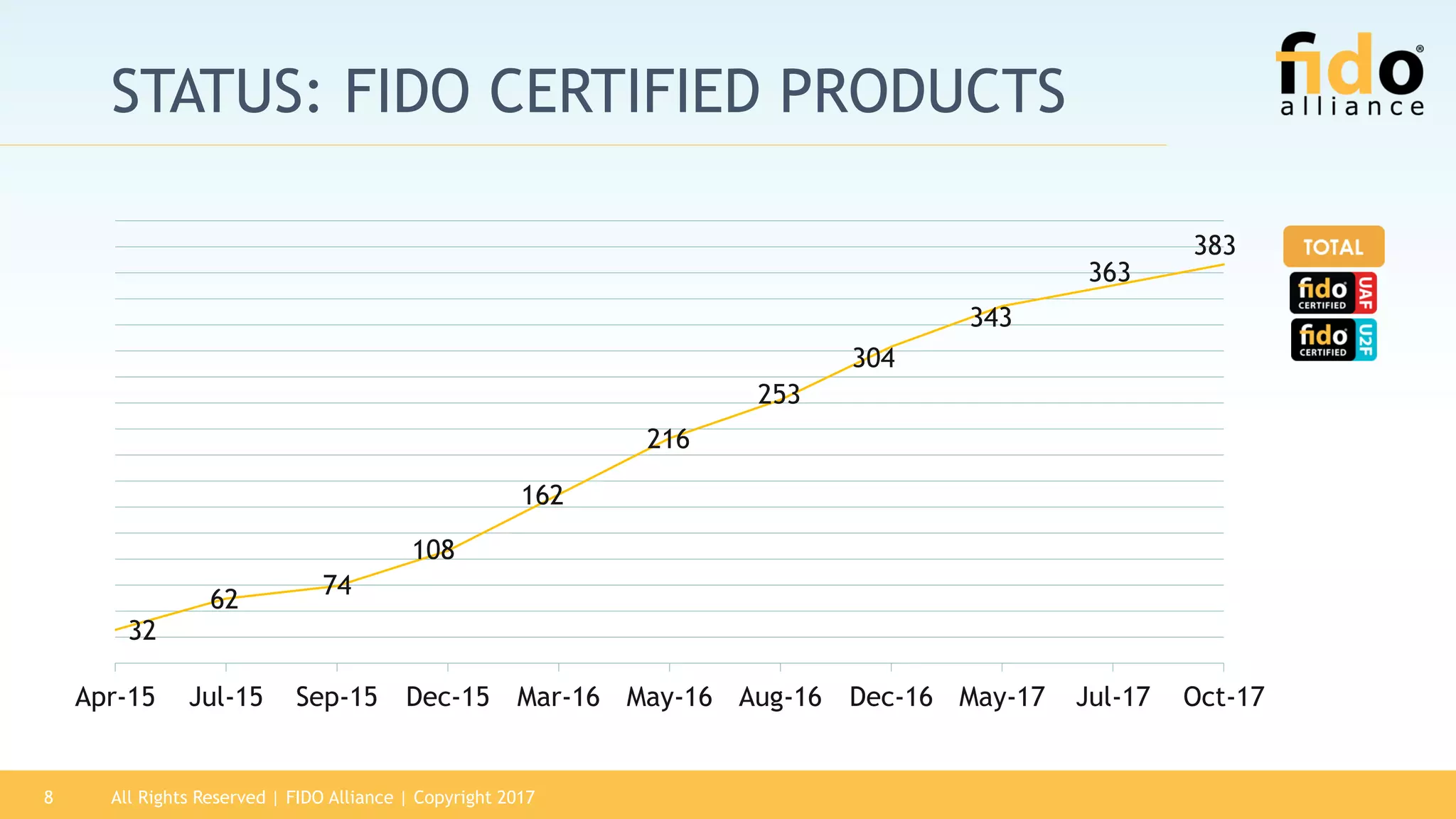
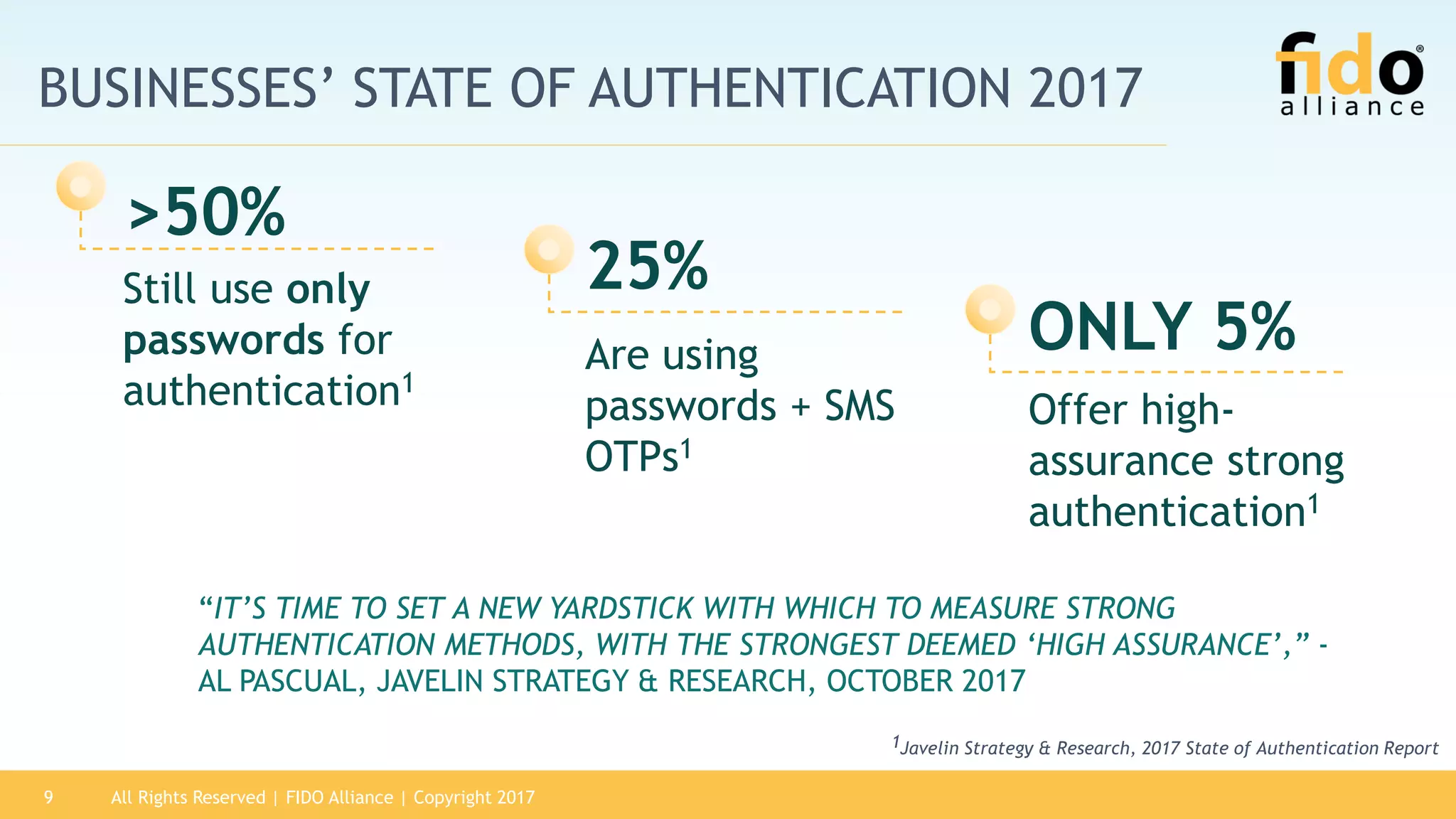
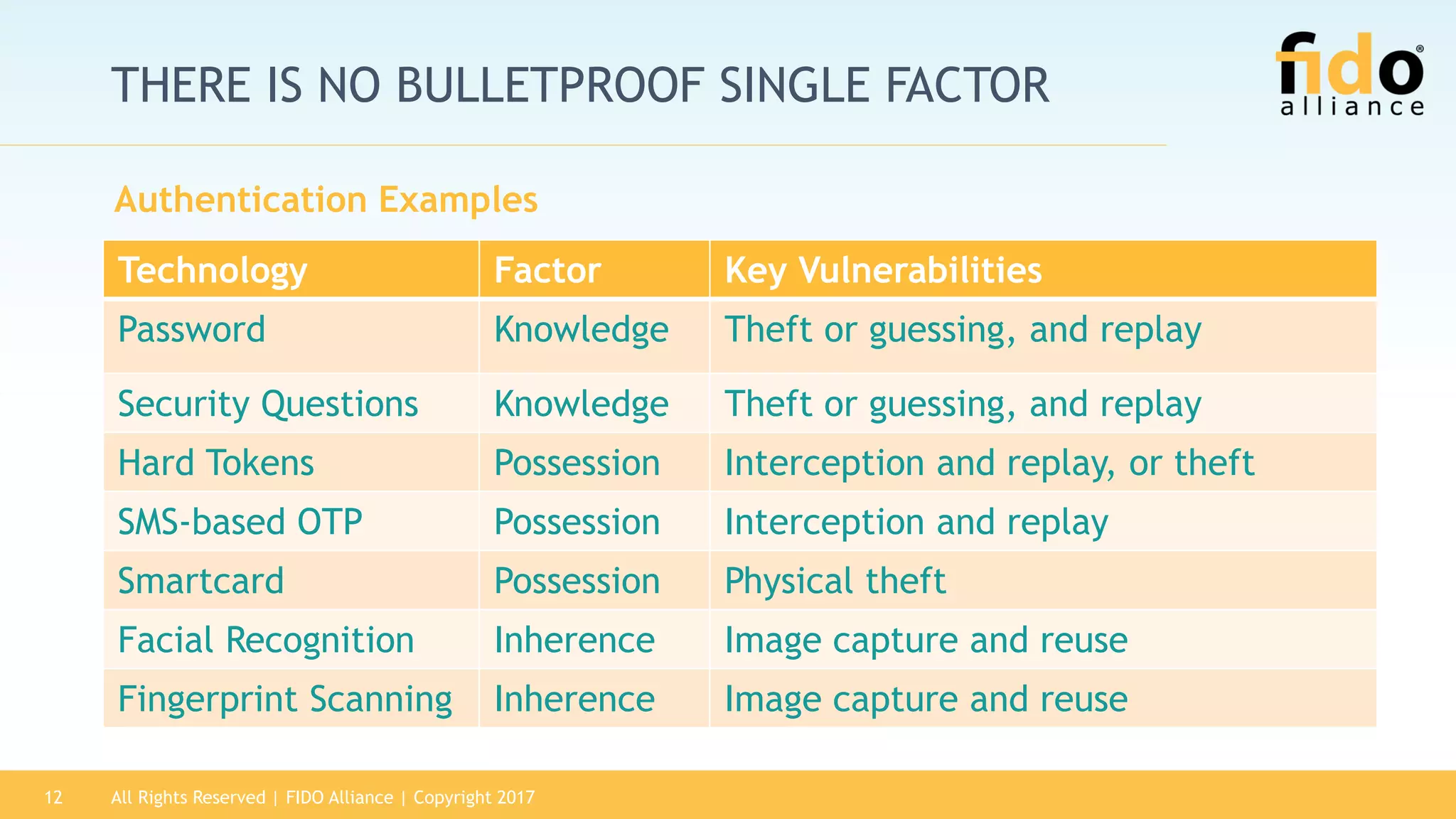
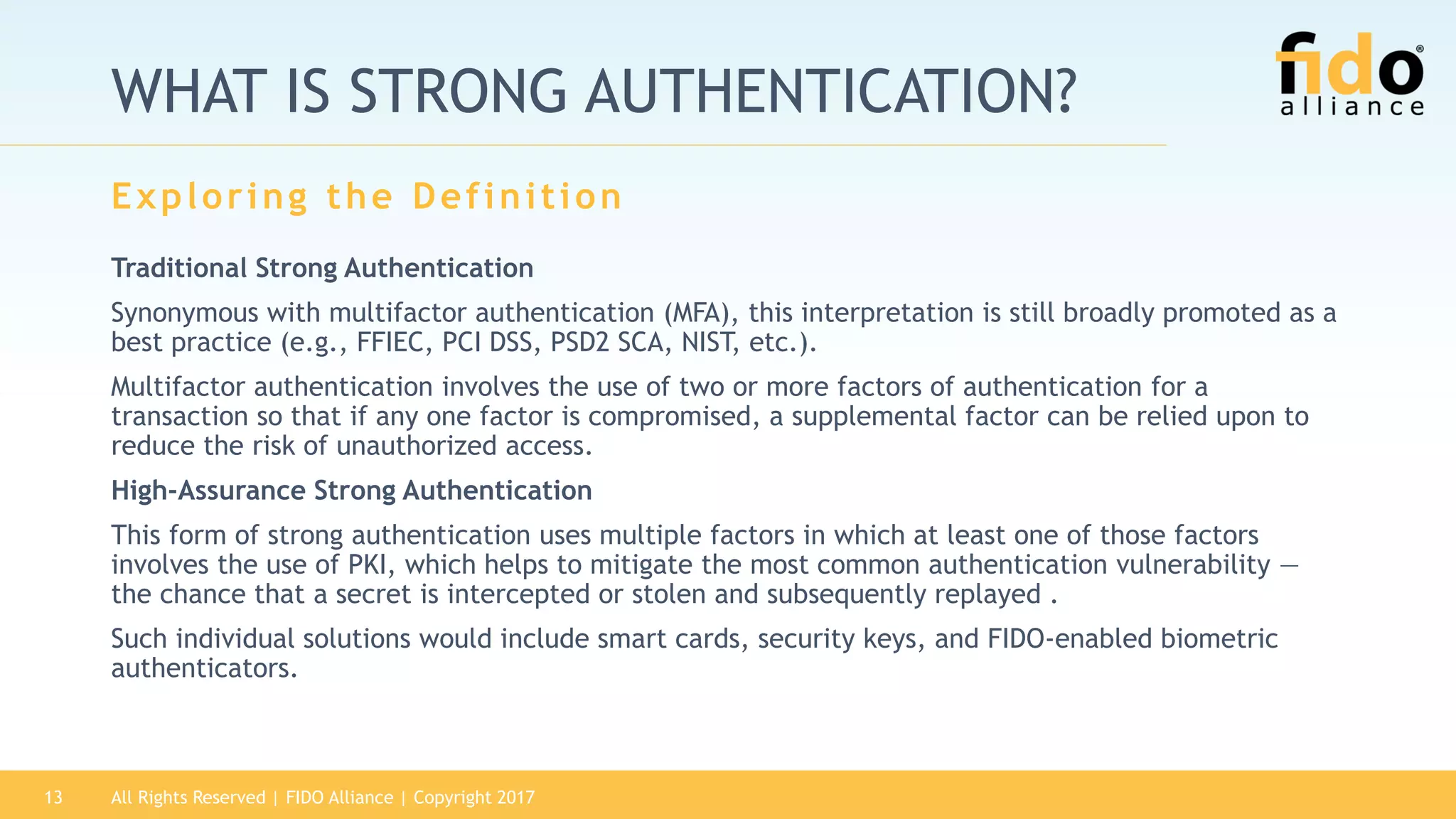
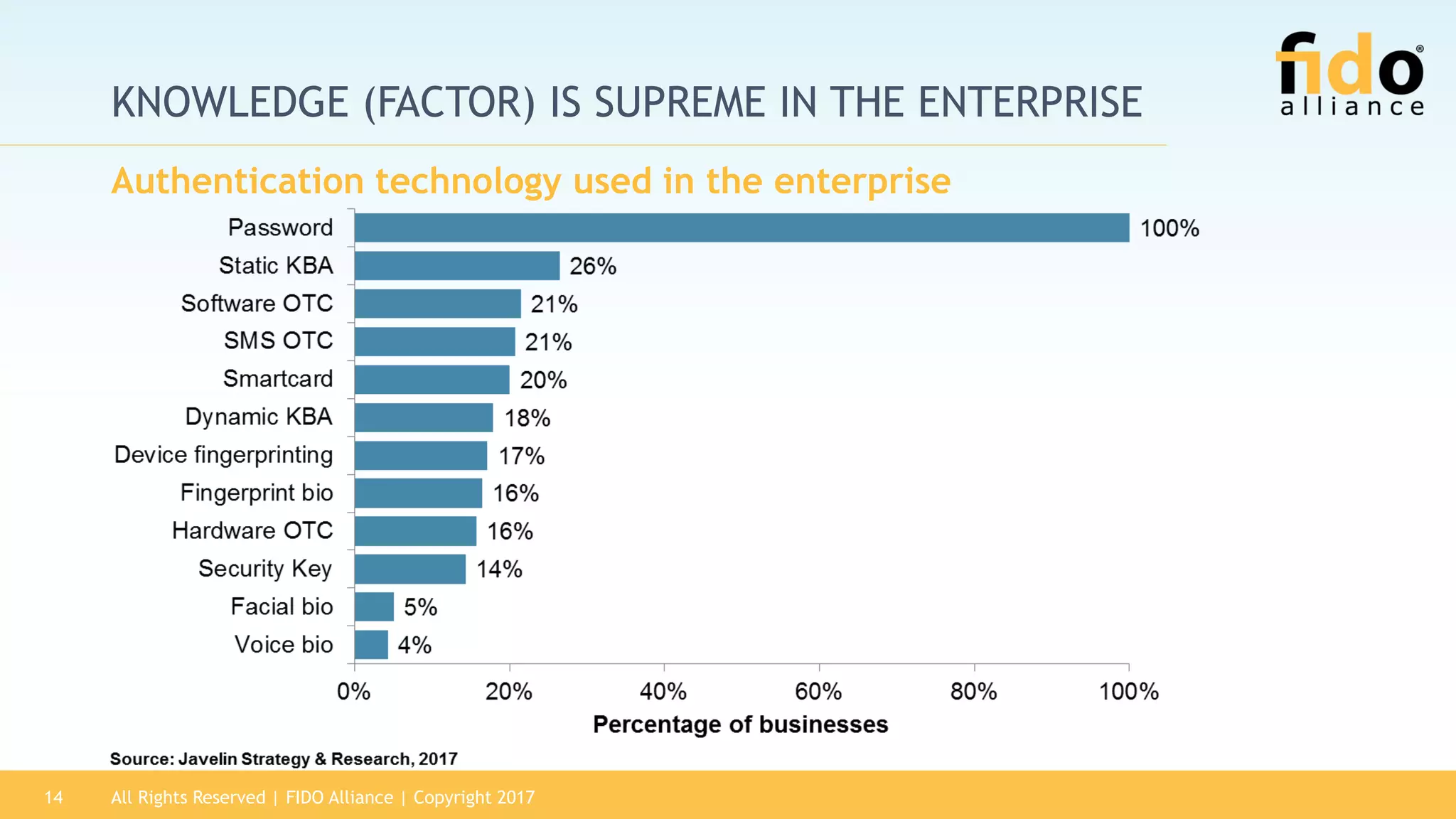
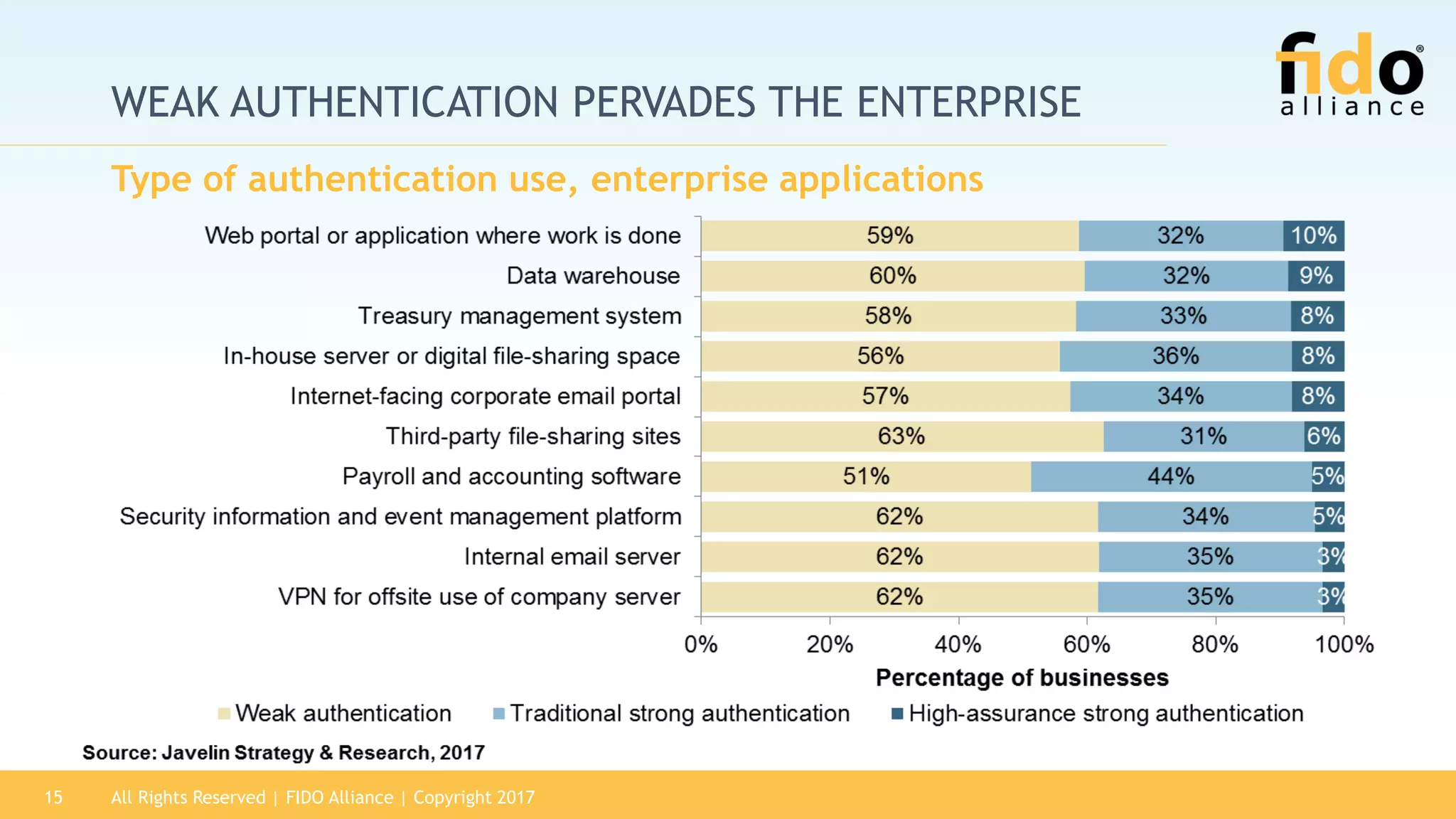
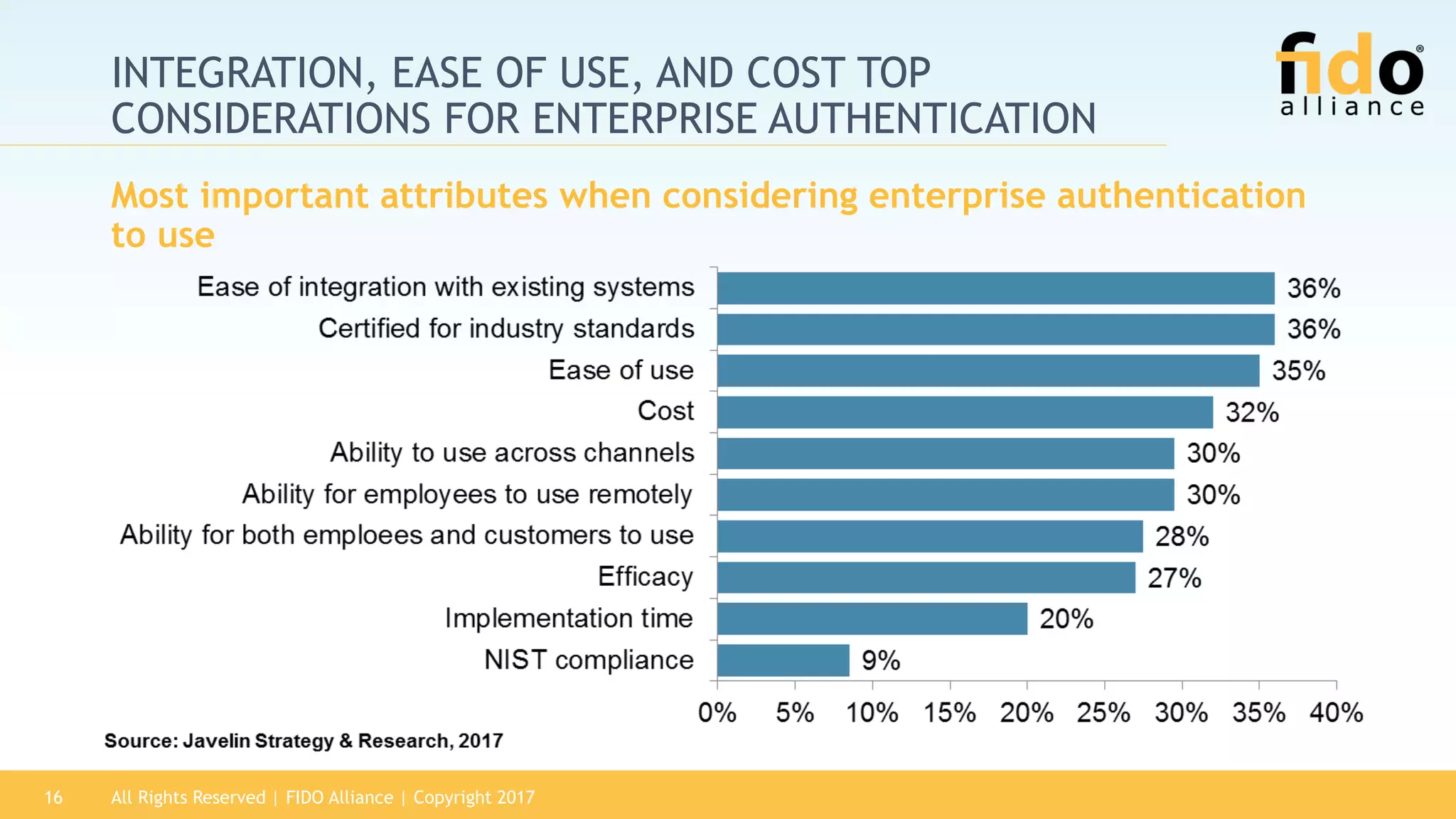
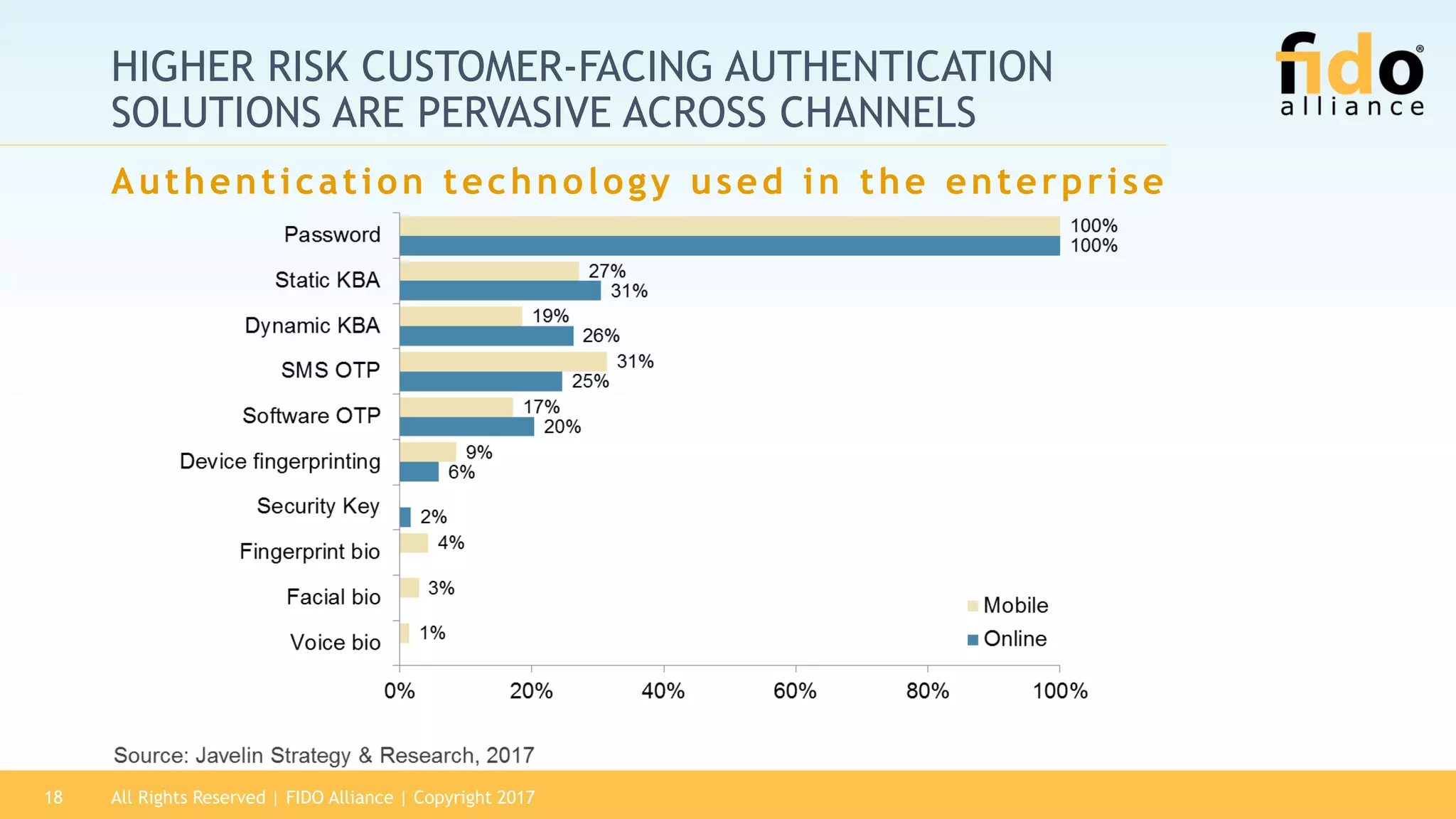
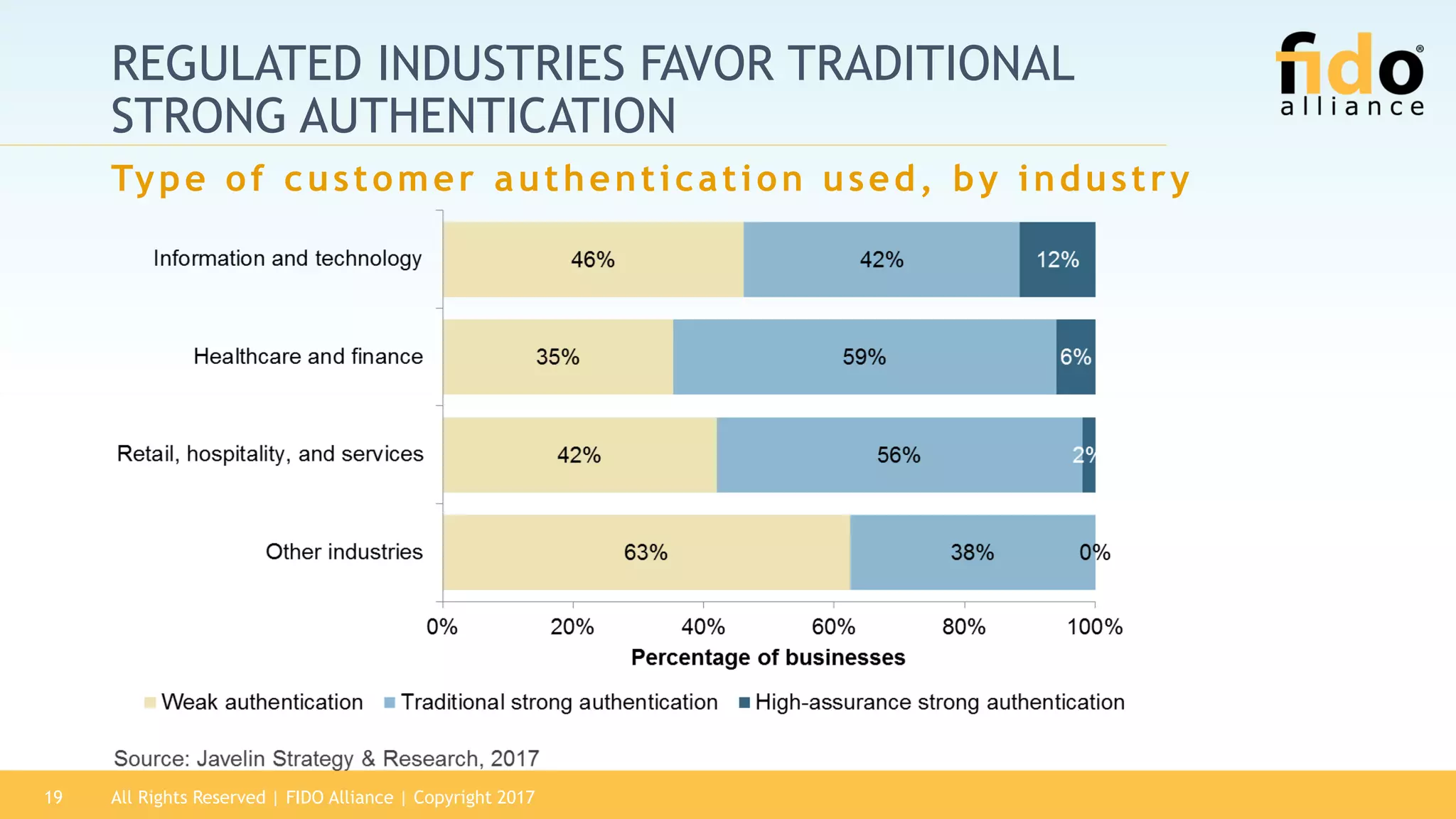
The 2017 State of Authentication report highlights the increasing risks associated with weak passwords and the rise in data breaches, emphasizing the need for more robust authentication methods. The report, sponsored by the FIDO Alliance, explores the current state of authentication in the U.S. and advocates for high-assurance strong authentication incorporating public key cryptography. It identifies key vulnerabilities in existing authentication technologies and the importance of integrating stronger methods to enhance security against unauthorized access.