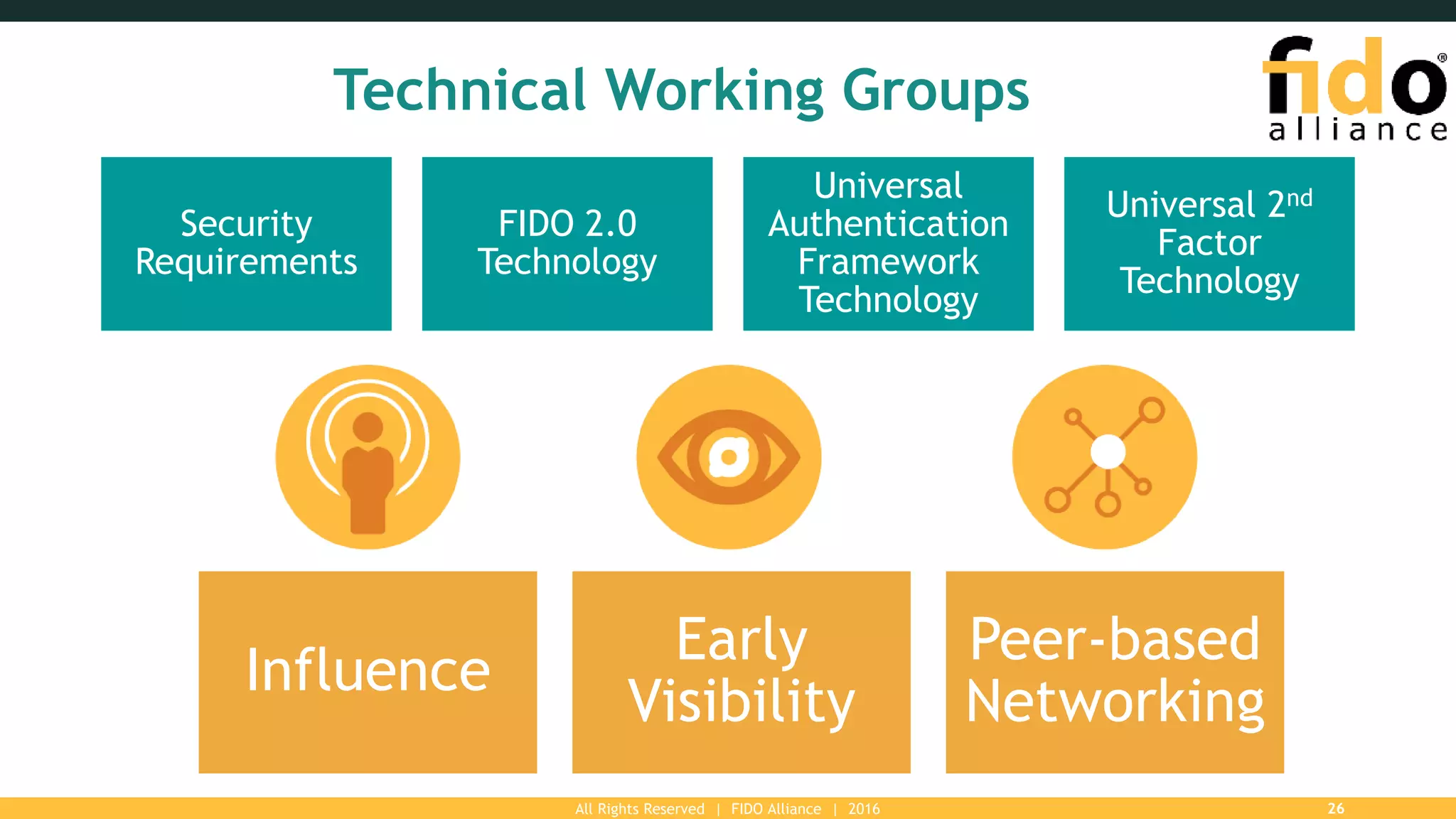
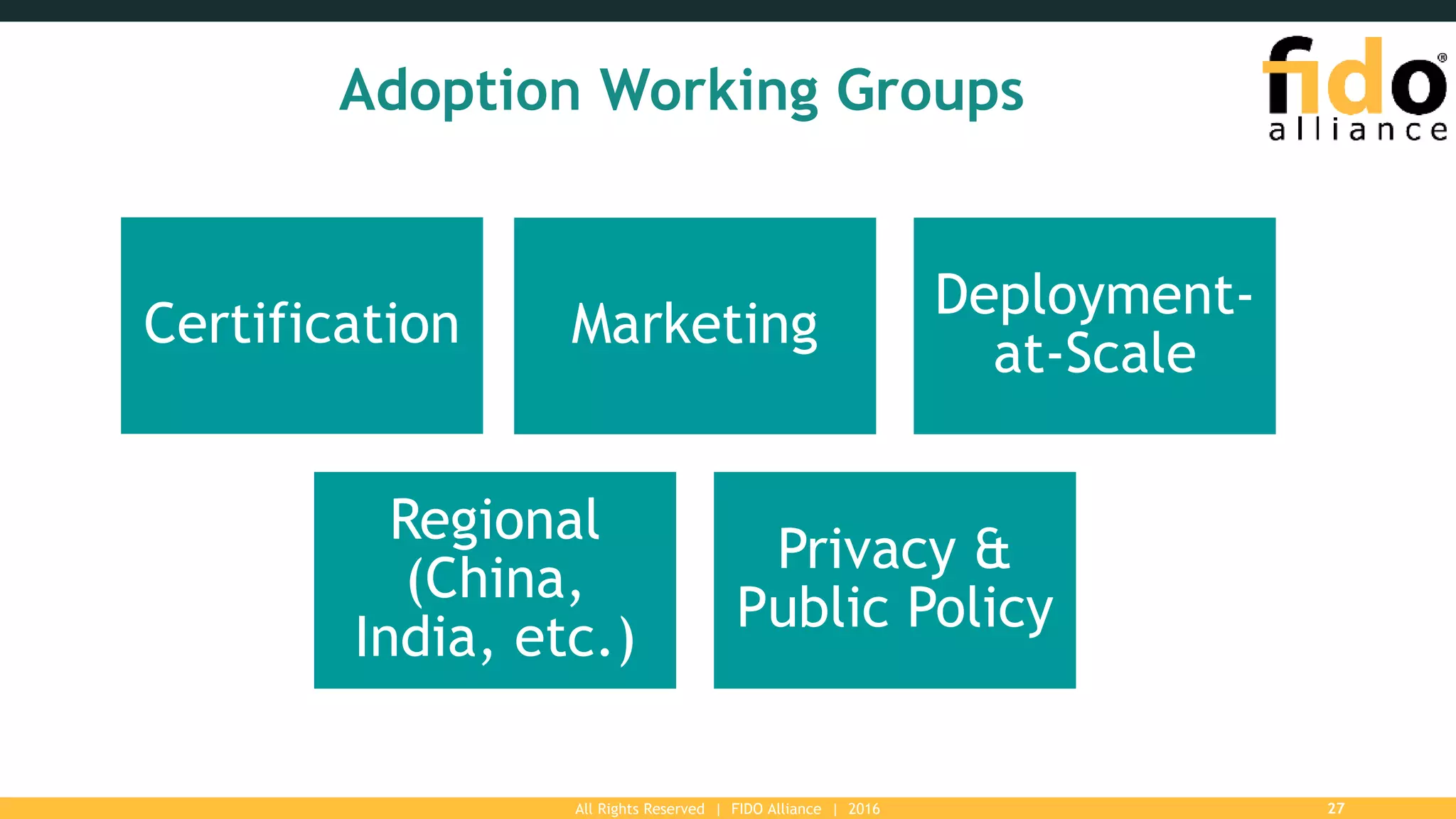
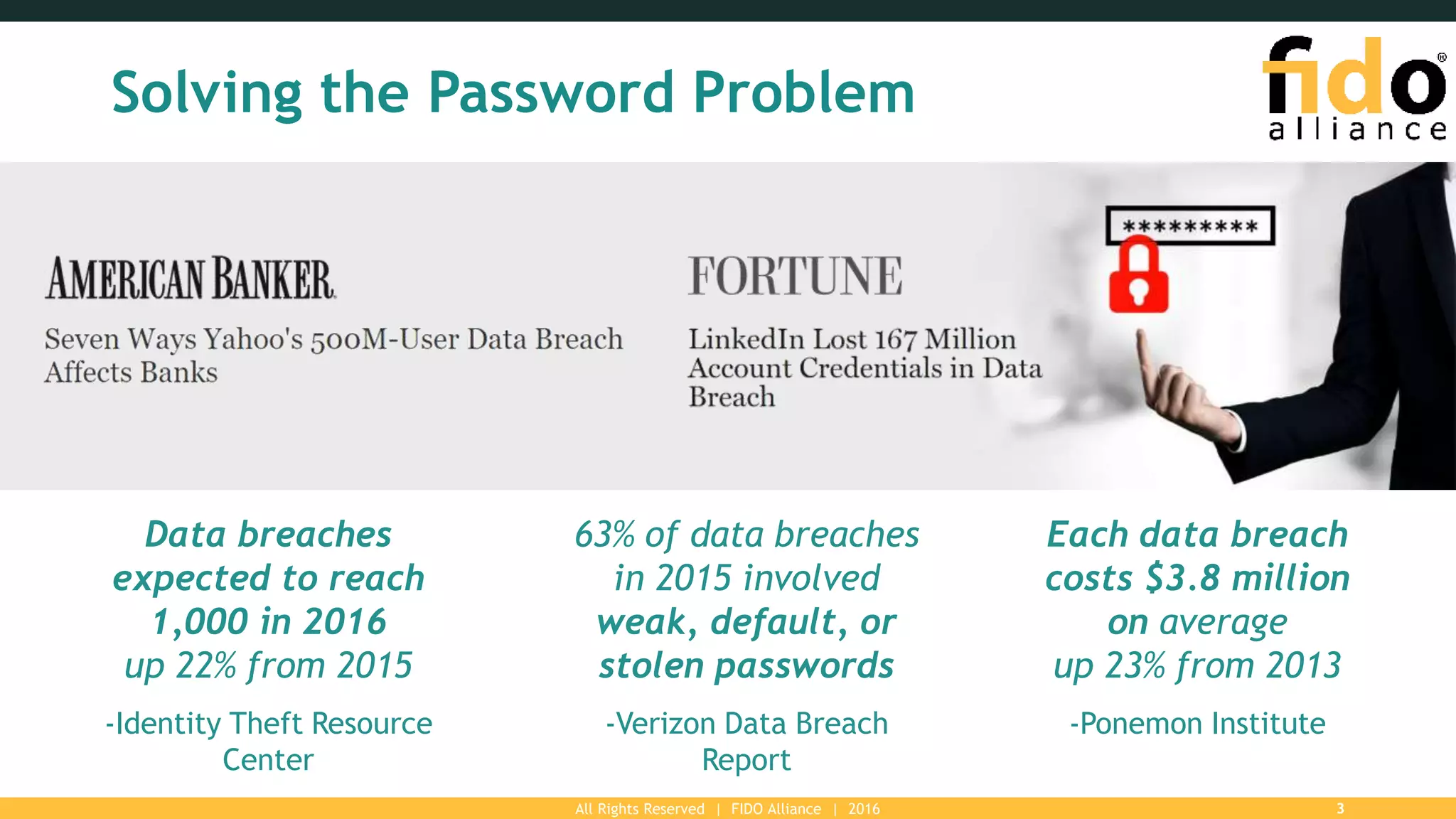
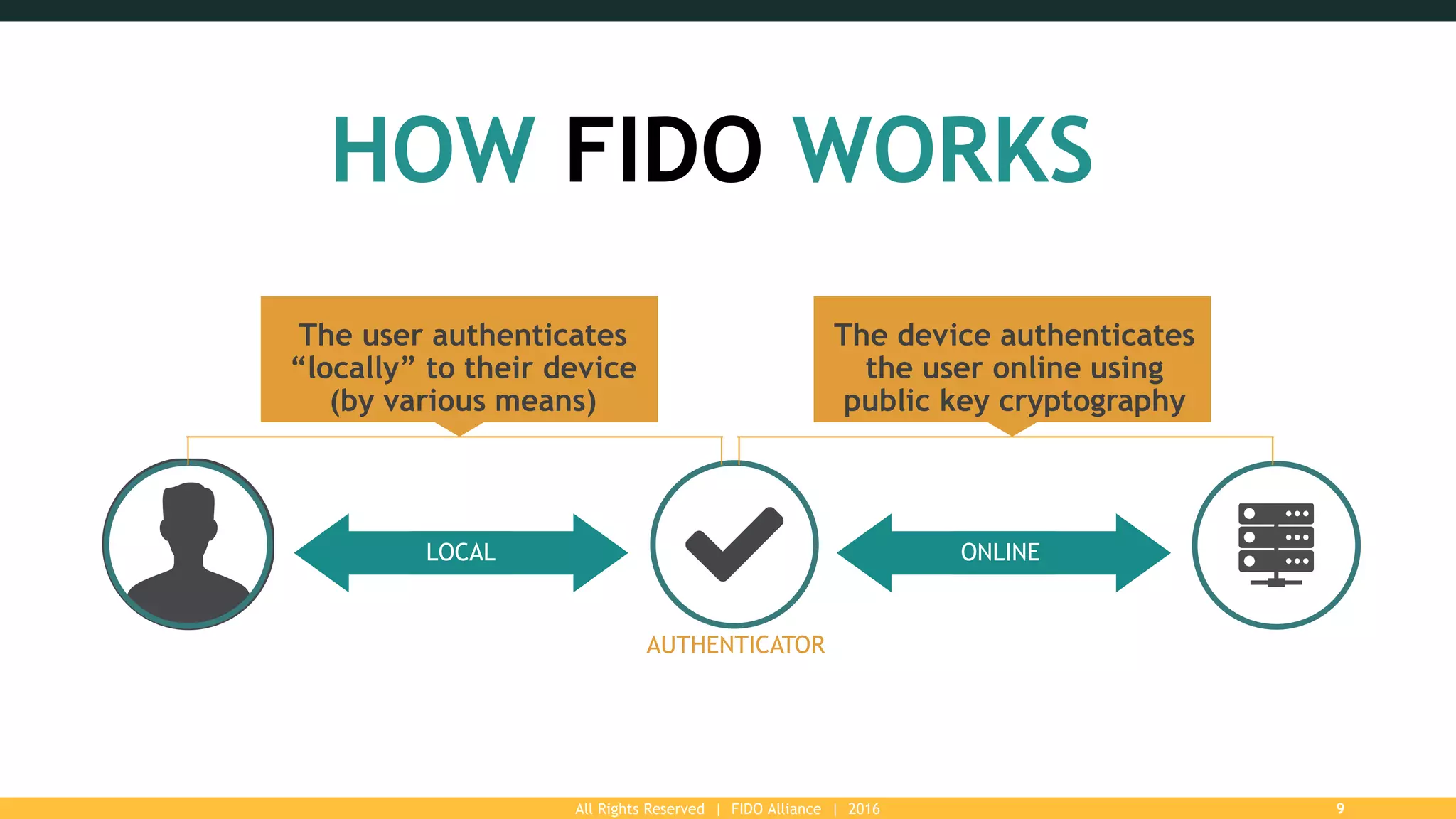
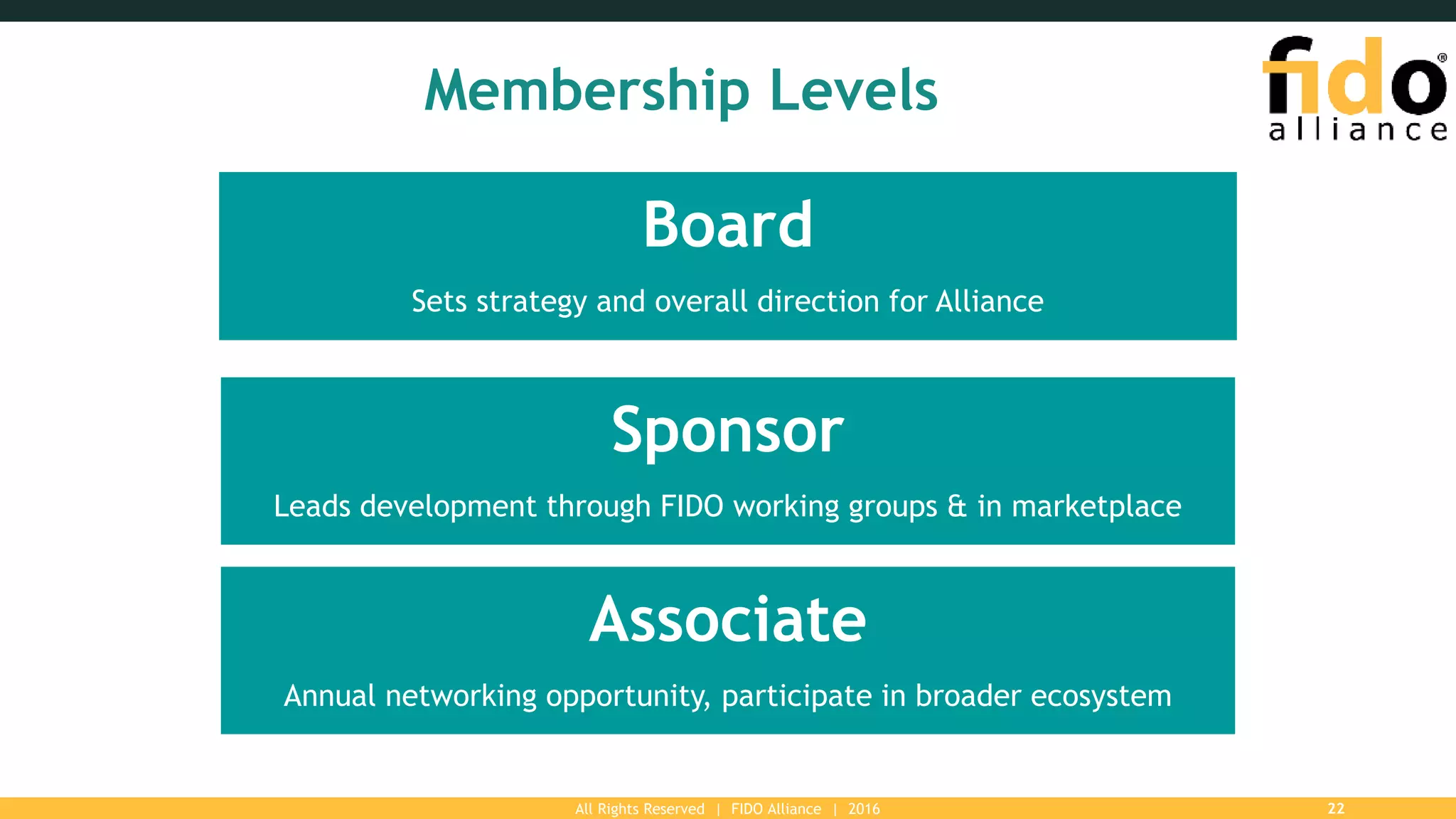
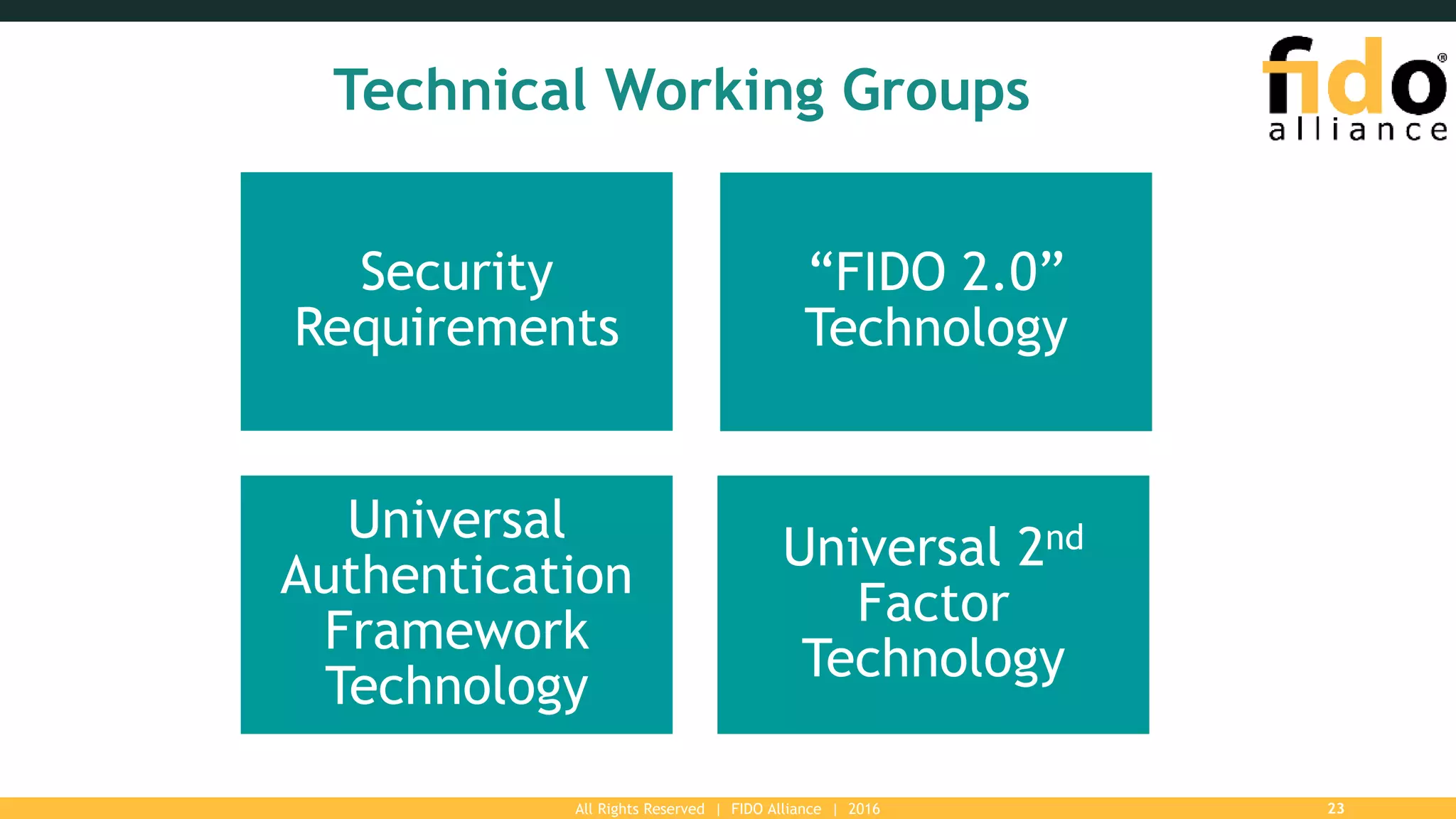
The FIDO Alliance is a global organization aimed at solving the password problem by providing improved authentication standards, which reduce data breaches and enhance security for users and enterprises. With over 250 member organizations, it promotes interoperable and certified solutions across various platforms, ensuring better user experience and privacy protection. The document outlines the value of FIDO membership, including influence on specifications, marketing support, and access to technical resources.














![All Rights Reserved | FIDO Alliance | 2016 25
“The IPR Promise” Process - 6.2.1.1
“For each Working Group in which one or more Bound Entities
participates, Signatory, on behalf of itself, all its Related Entities and its
and their successors in interest and assigns, promises not to assert its or
its Related Entity’s Granted Claims against any Participant in such
Working Group for its Public Permitted Uses or Working Group Permitted
Uses, subject to the terms and conditions of this Agreement. [...]”
• A reciprocal promise to not assert patents against the
normative requirements in FIDO specification
• Enables unencumbered growth of FIDO ecosystem
http://fidoalliance.org/membership/details](https://image.slidesharecdn.com/fidothevalueofmembershipdec2016-161207014439/75/FIDO-The-Value-of-Membership-25-2048.jpg)