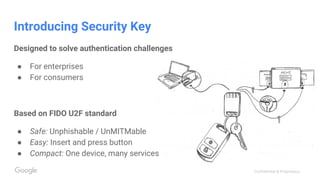
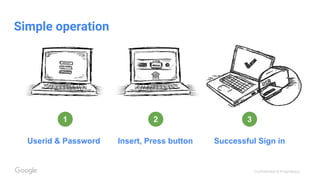
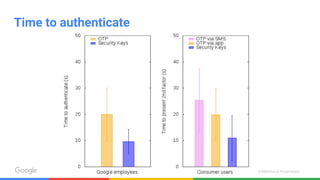
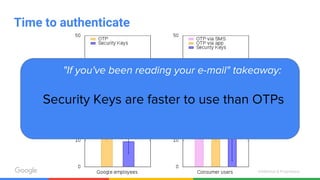
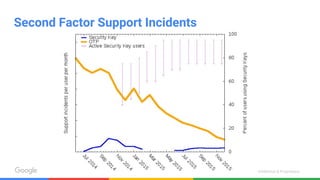
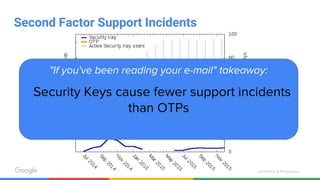
The document discusses the inadequacies of traditional passwords and the rise of phishing attacks, highlighting the introduction of security keys based on the FIDO U2F standard as a more secure, user-friendly authentication solution. It emphasizes Google's implementation and benefits of security keys, including faster authentication and fewer support incidents compared to one-time passwords. The document also outlines potential use cases and resources for adopting this technology.


![Confidential & Proprietary
Passwords are broken
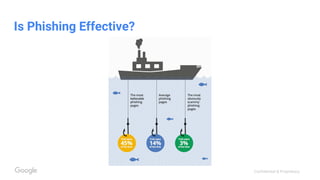
Phishing has become increasingly sophisticated
● More than ⅔ of incidents [in 2015] … involved phishing. With a 23%
effectiveness rate*
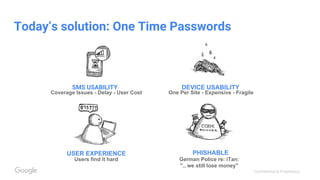
● OTPs help against shared password, but it’s not safe to rely on them for
phishing
* http://www.verizonenterprise.com/DBIR/2015/
REUSED PHISHED KEYLOGGED](https://image.slidesharecdn.com/05gdasherbecomingunphishable-170628165802/85/Becoming-Unphishable-4-320.jpg)