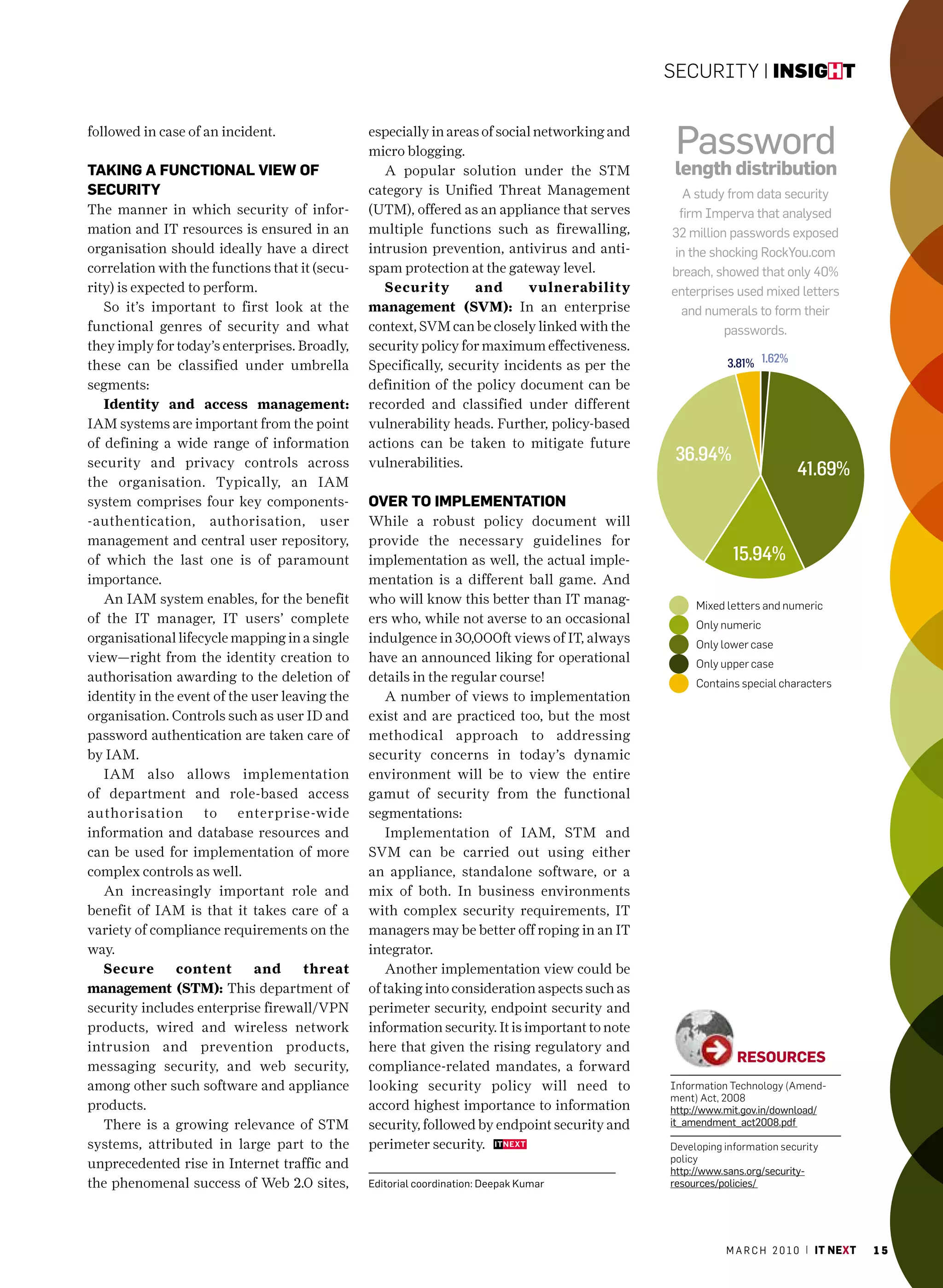
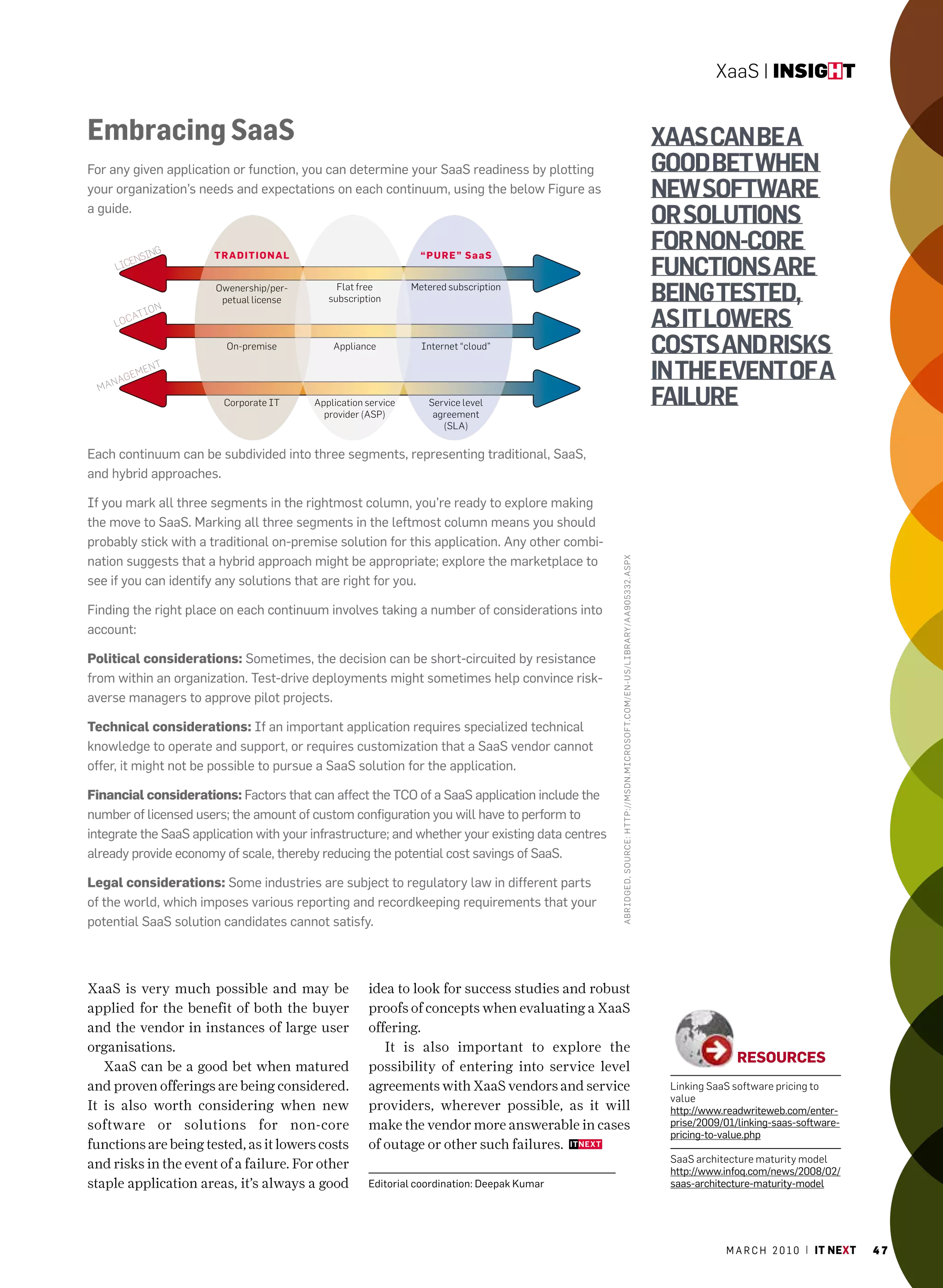
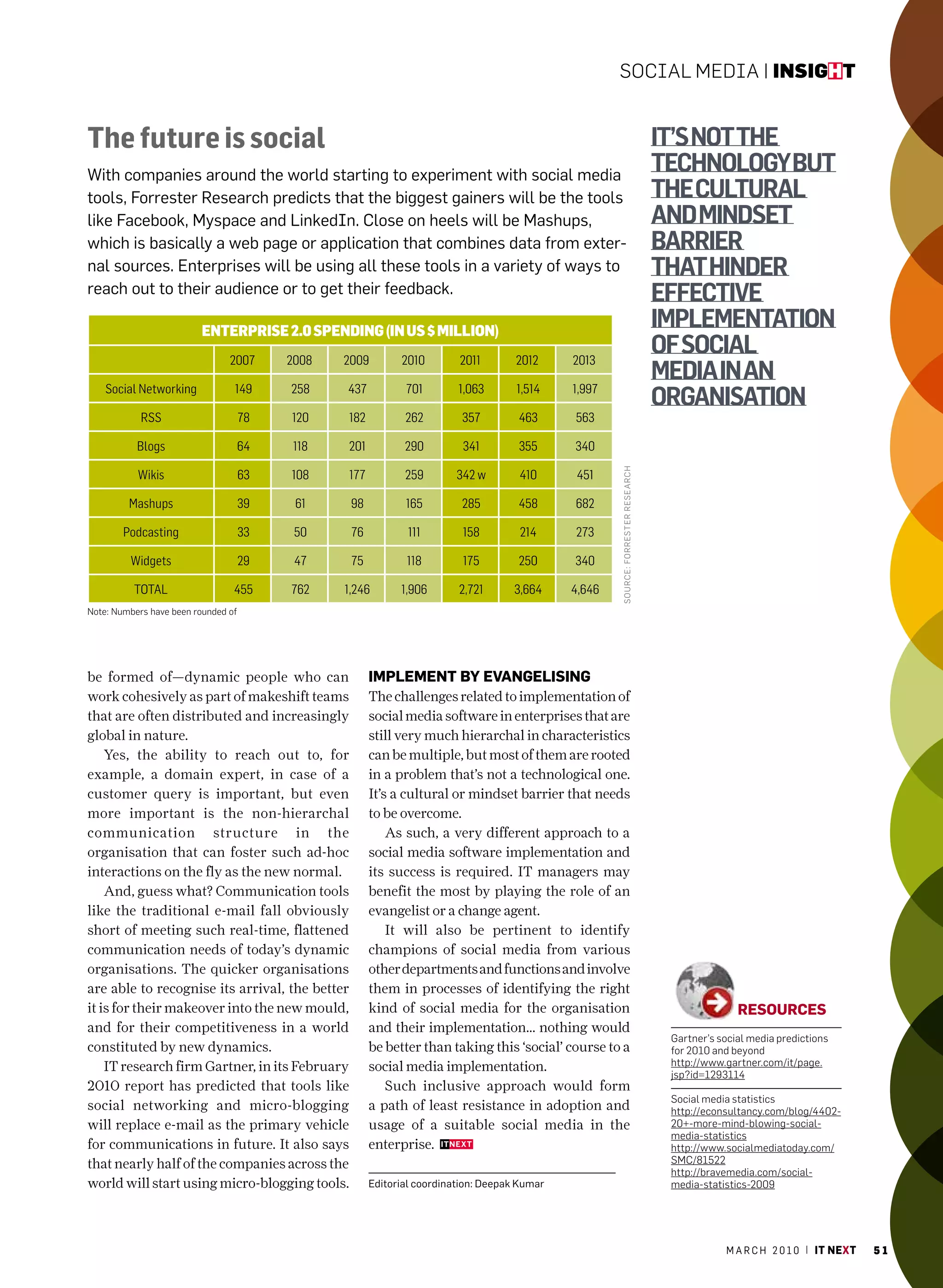
The March 2010 issue of 'IT Next' celebrates community-driven content creation inspired by Wikipedia, showcasing contributions from over 40 IT managers. It discusses technology trends and challenges faced by IT leaders, emphasizing the importance of collective knowledge in shaping industry insights. The edition reflects the successes of collaborative content creation while highlighting key articles on emerging technologies and management practices.