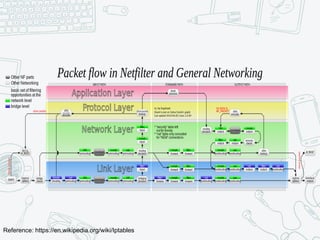
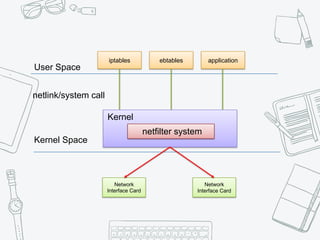
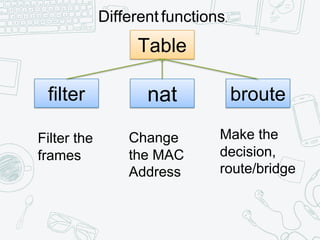
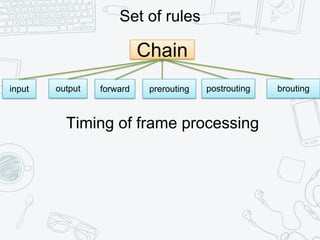
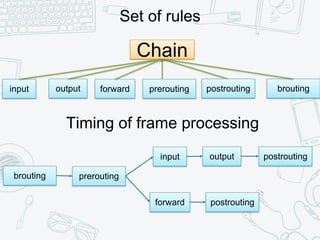
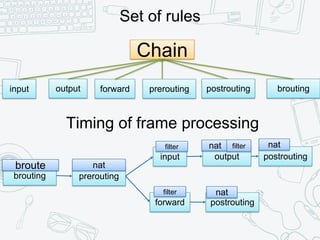
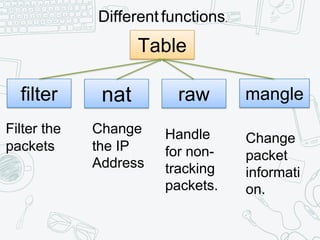
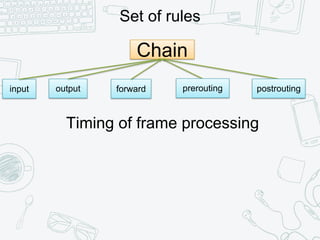
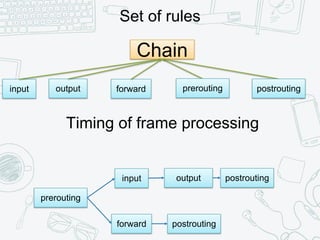
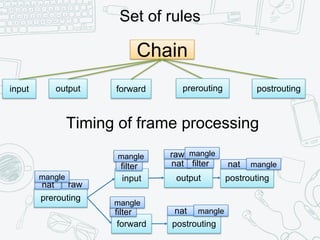
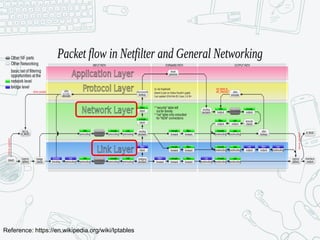
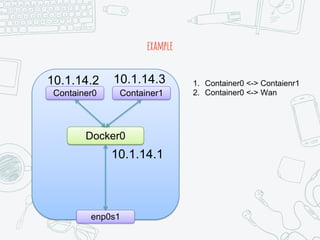
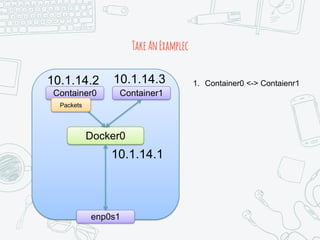
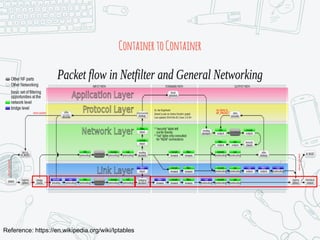
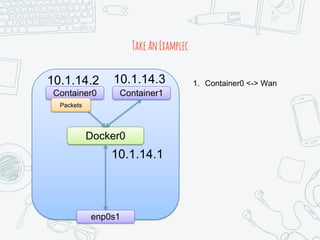
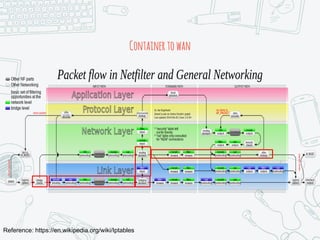
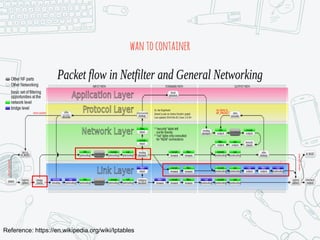
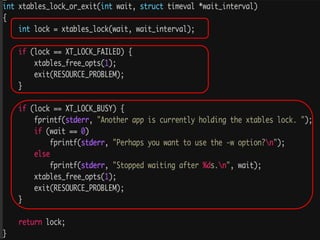
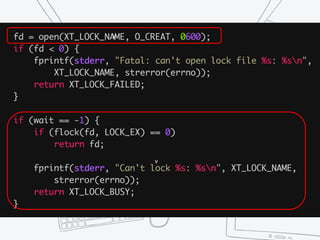
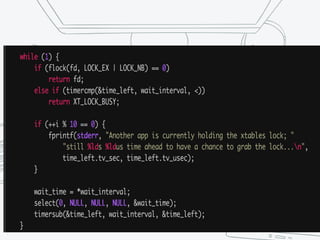
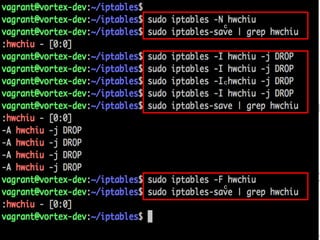
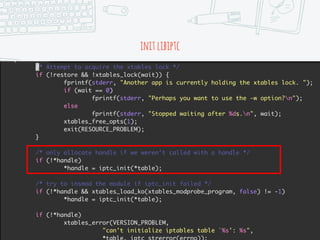
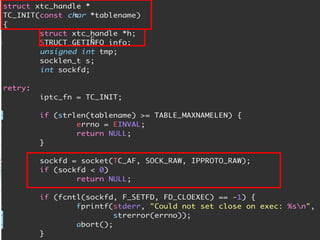
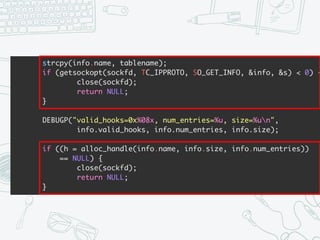
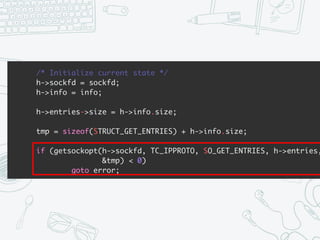
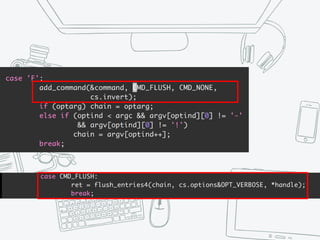
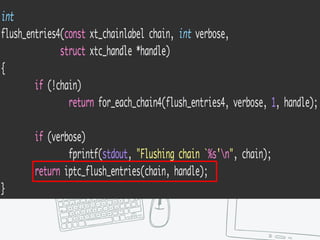
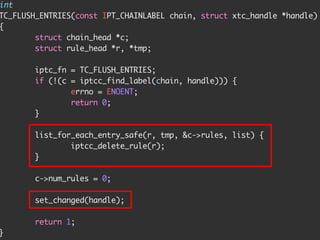
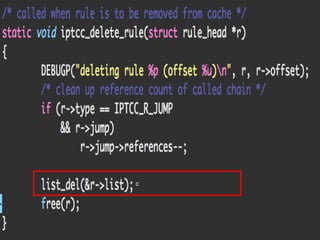
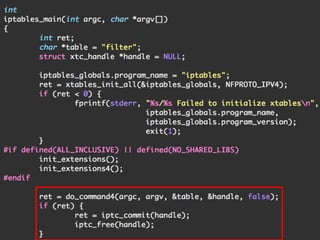
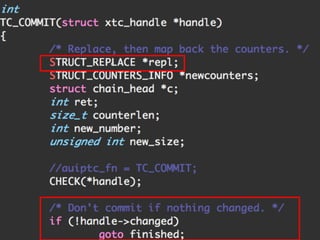
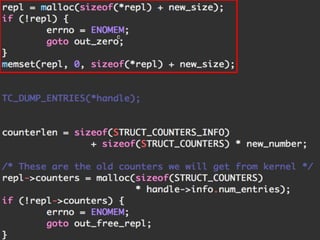
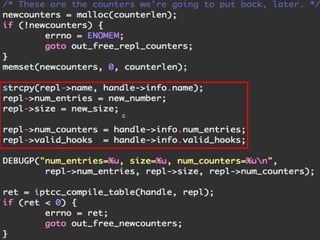
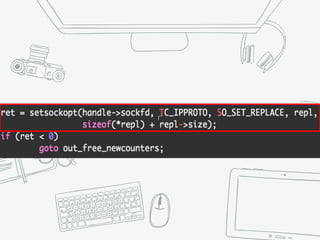
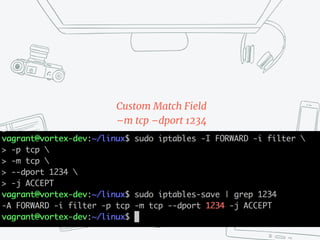
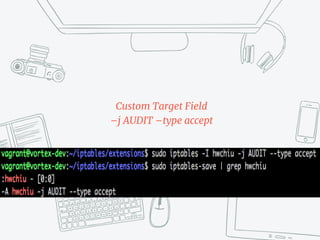
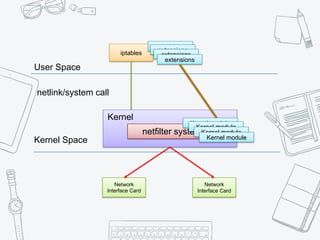
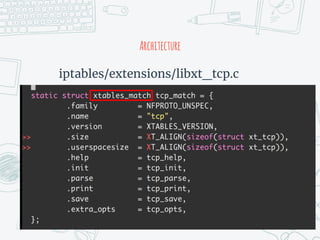
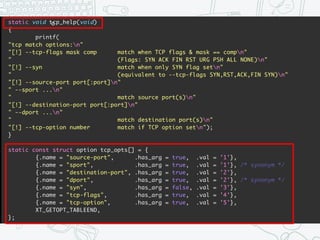
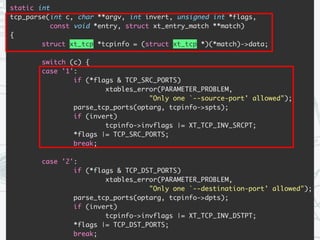
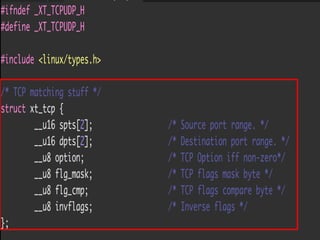
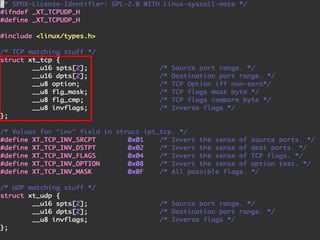
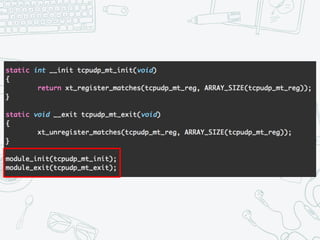
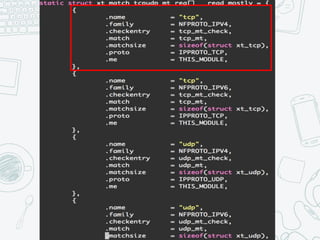
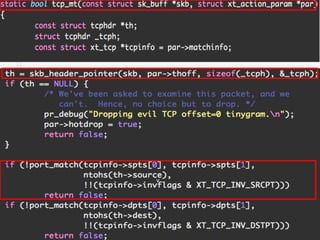
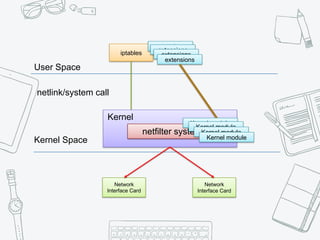
The document provides an overview of iptables, discussing its architecture, functionality, and usage. It explains how iptables operates with the Linux kernel, including the role of user-space tools and the importance of file locking to maintain consistency. Additionally, it covers the extension system for adding custom match and target functions in iptables.