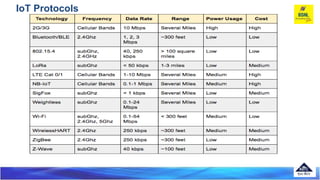
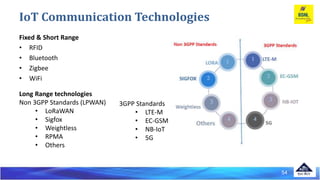
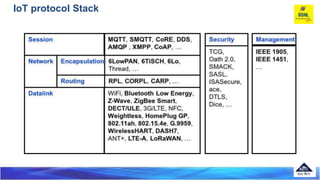
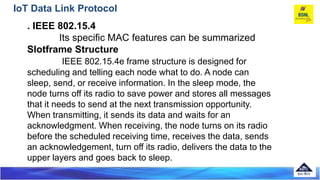
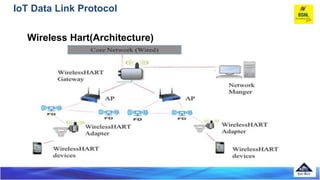
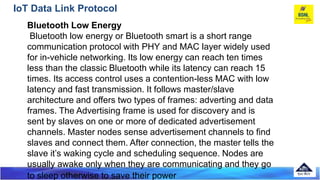
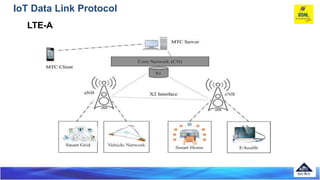
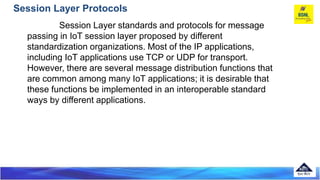
The document discusses several Internet of Things (IoT) data link protocols, including IEEE 802.15.4, WirelessHART, Z-Wave, Bluetooth Low Energy, Zigbee Smart Energy, DASH7, LTE-A, LoRaWAN, and DECT/ULE. It provides details on their network architectures, medium access control methods, and suitability for various IoT applications.
























![Network Layer Encapsulation Protocols
IPv6 over Bluetooth Low Energy
Bluetooth Low Energy is also known as Bluetooth Smart
and was introduced in Bluetooth V4.0 and enhanced in
V4.1. RFC 7668 [RFC7668], which specifies IPv6 over
Bluetooth LE, reuses most of the 6LowPAN compression
techniques. However, since the Logical Link Control and
Adaptation Protocol (L2CAP) sublayer in Bluetooth
already provides segmentation and reassembly of larger
payloads in to 27 byte L2CAP packets, fragmentation
features from 6LowPAN standards are not used.](https://image.slidesharecdn.com/iotprotocols-230727051544-b1c07194/85/IoT-_protocols-ppt-36-320.jpg)






![Session Layer Protocols
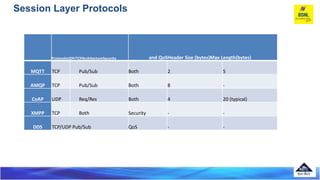
DDS
Data Distribution Service (DDS) is another
publish/subscribe protocol that is designed by the Object
Management Group (OMG) for M2M communications
[DDS]. The basic benefit of thisprotocol is the excellent
quality of service levels and reliability guarantees as it
relies on a broker-less architecture, which suits IoT and
M2M communication. It offers 23 quality-of-service levels
which allow it to offer a variety of quality criteria
including: security, urgency, priority, durability, reliability,
etc](https://image.slidesharecdn.com/iotprotocols-230727051544-b1c07194/85/IoT-_protocols-ppt-47-320.jpg)