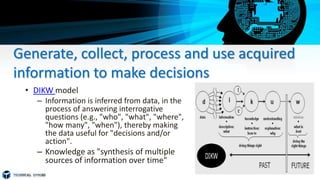
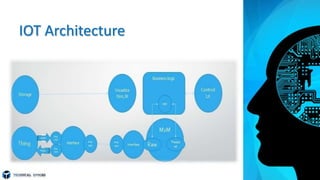
The document provides an overview of the Internet of Things (IoT). It defines IoT as the network of physical objects embedded with sensors, software and other technologies that connect and exchange data with other devices and systems over the Internet. It discusses where IoT is used in various industries like healthcare, smart homes and more. The reasons for IoT include generating and using data to make better decisions and enabling devices that were not designed to interact to do so intelligently. It also covers IoT security issues, the rapid growth of the IoT market, and the need for standards and interoperability to realize its full potential while mitigating risks.