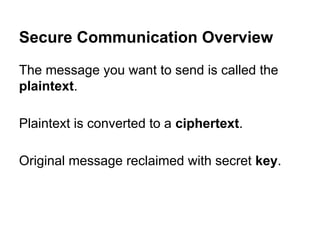
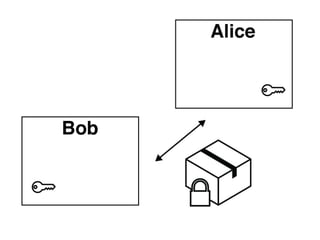
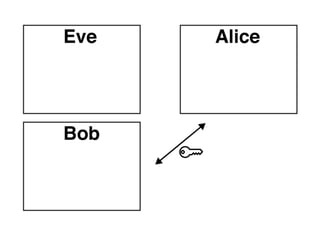
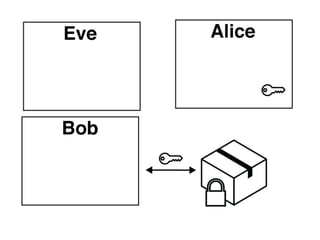
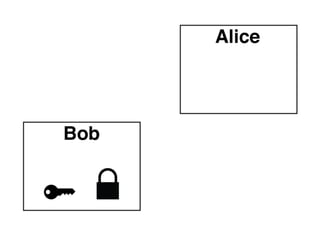
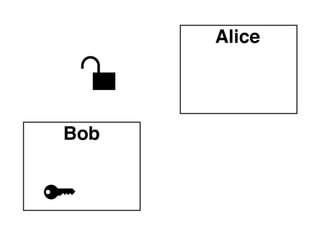
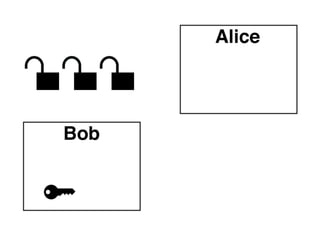
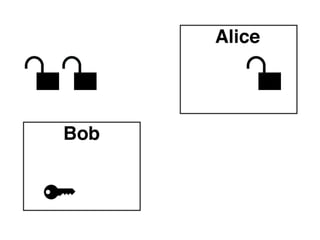
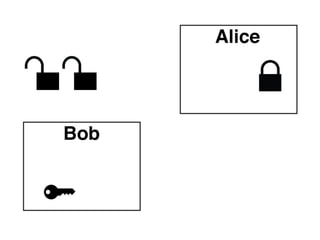
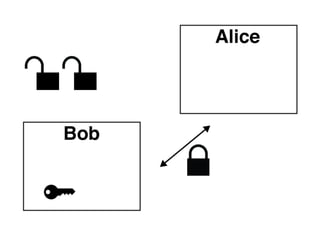
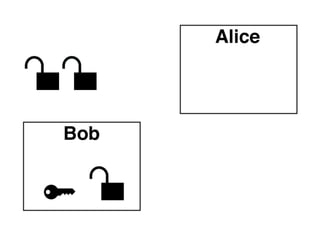
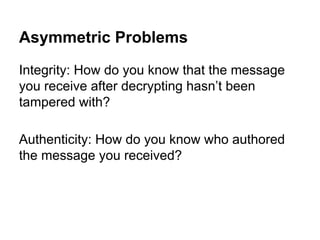
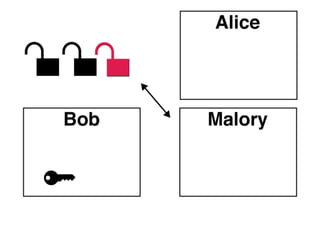
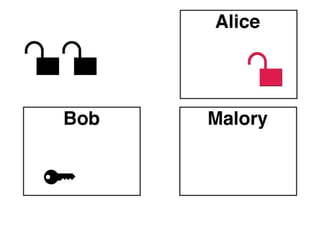
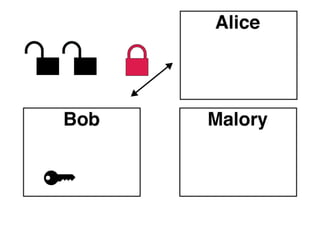
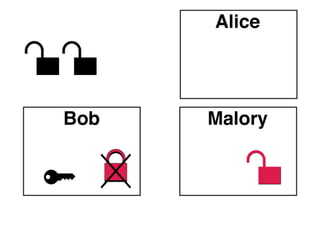
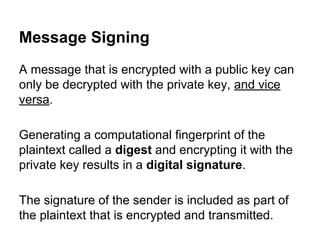
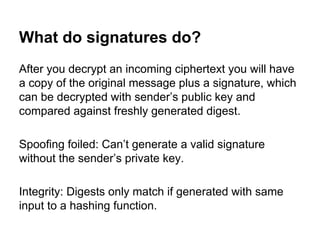
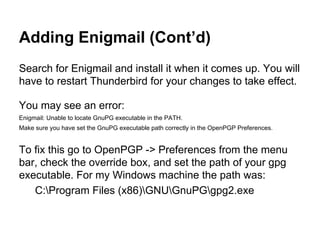
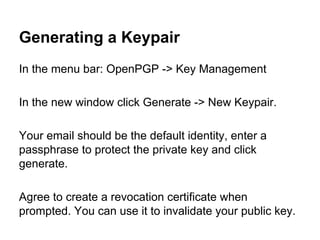
The document presents an introductory workshop on Pretty Good Privacy (PGP) and its application in secure communication, highlighting the three major aspects of security: privacy, integrity, and authenticity. It explains the differences between symmetric and asymmetric encryption, as well as the importance of digital signatures and certificate authorities in verifying identities. Additionally, it provides practical guidance on using GUI tools like GPGTools and Gpg4win for securely sending and receiving encrypted emails.