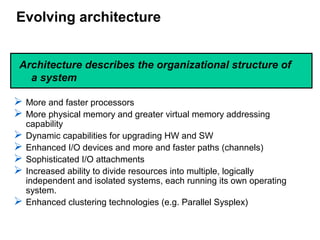
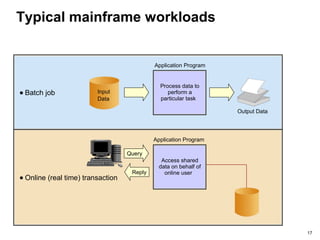
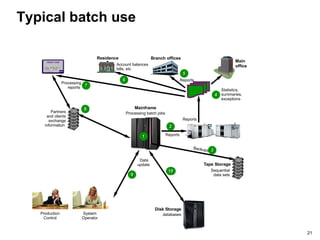
The document provides an introduction to mainframe computers, including their history and significance. It defines a mainframe as a large computer system that businesses use to host commercial databases and applications requiring high security and availability. Mainframes are designed to support thousands of users and input/output devices simultaneously through centralized control of resources and clustering technologies. They can process large workloads like batch jobs and online transactions concurrently.