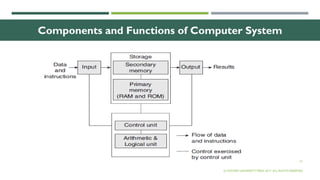
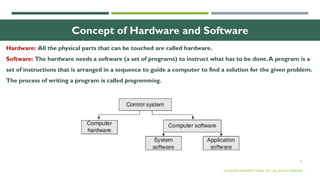
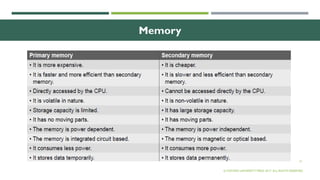
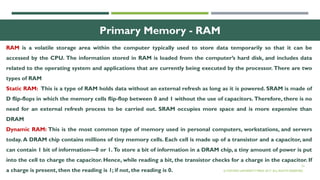
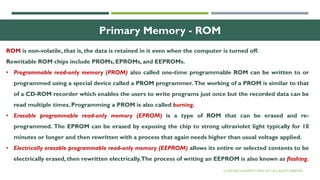
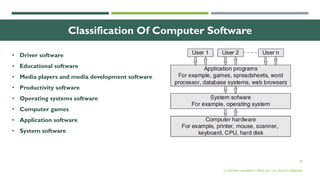
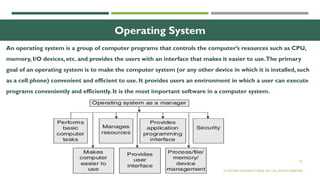
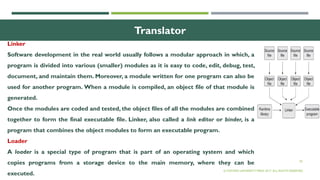
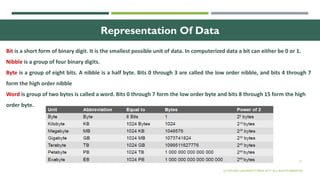
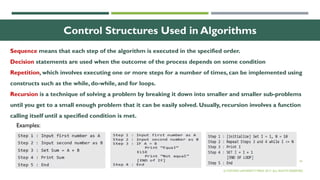
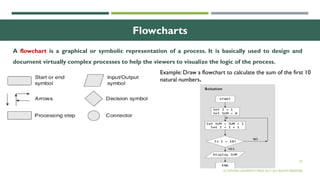
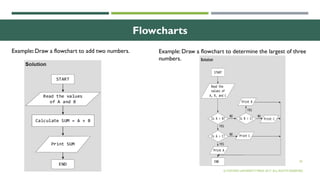
The document outlines the evolution of computer technology across five generations, detailing advancements in hardware and software from vacuum tubes to ultra-large scale integrated circuits. It explains characteristics of computers, classifications, key components, and applications, emphasizing the transition from technical complexity to user-friendly systems. The document further describes memory types, input and output devices, and the role of operating systems and compilers in computer functionality.