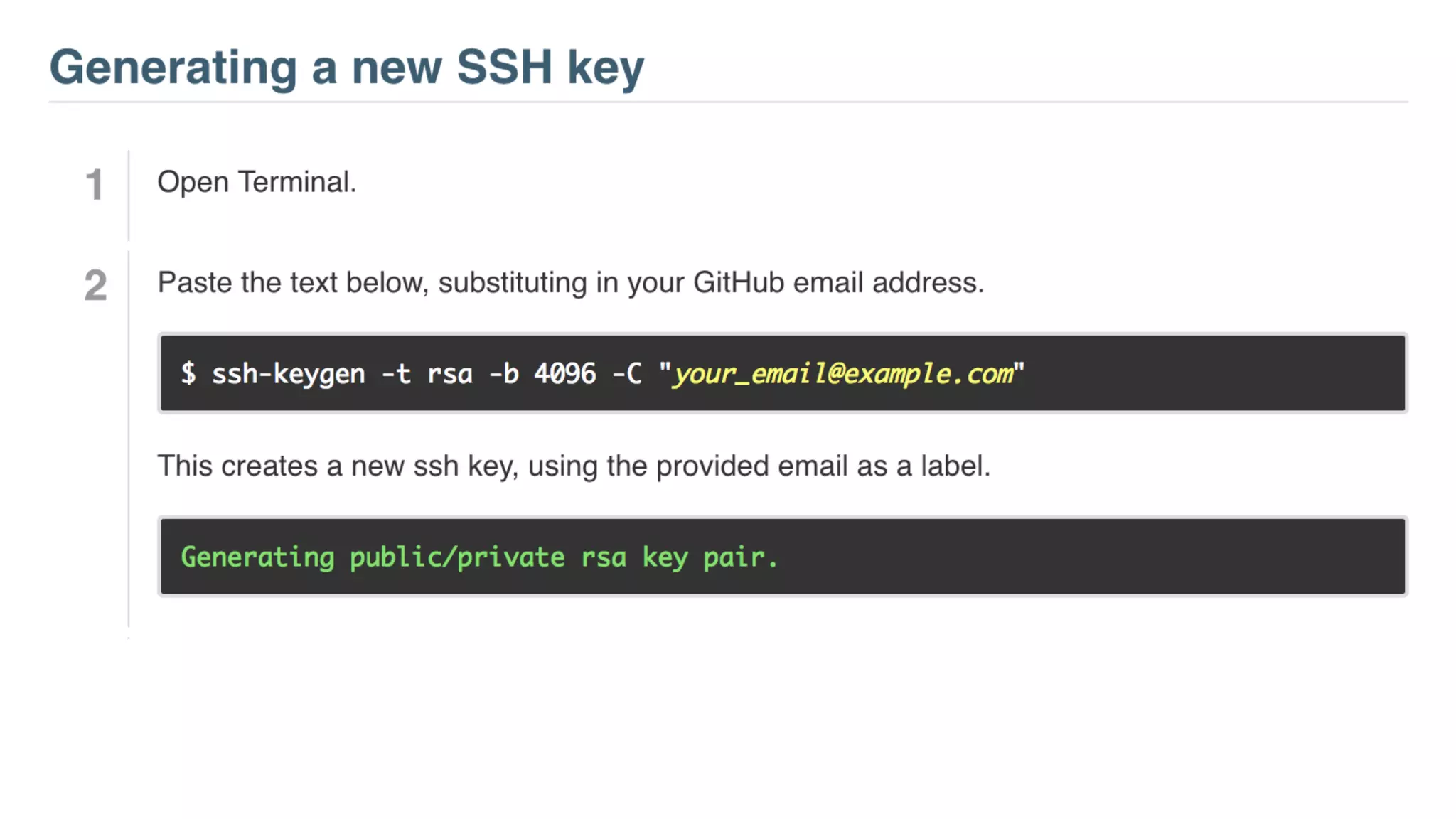
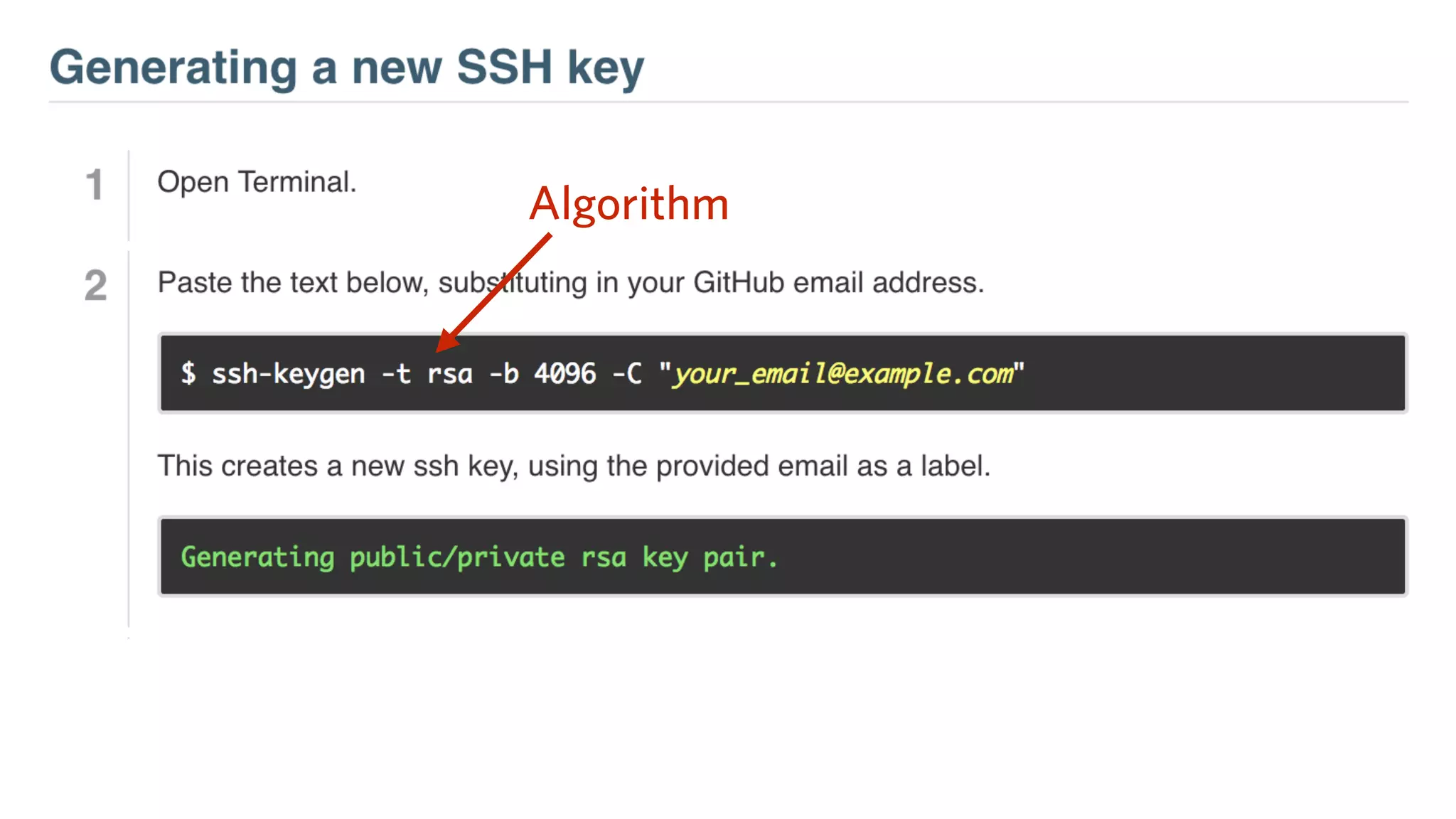
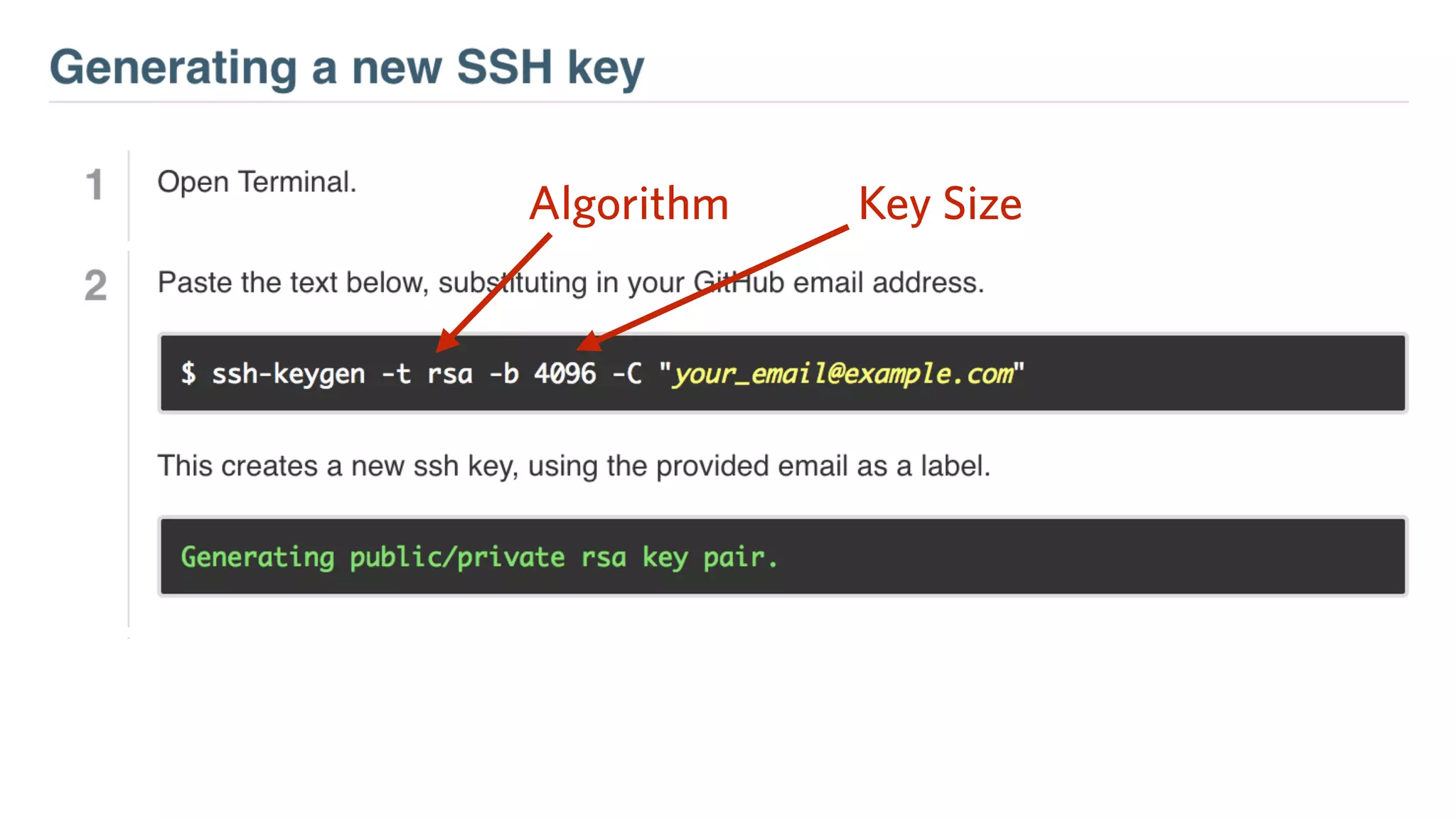
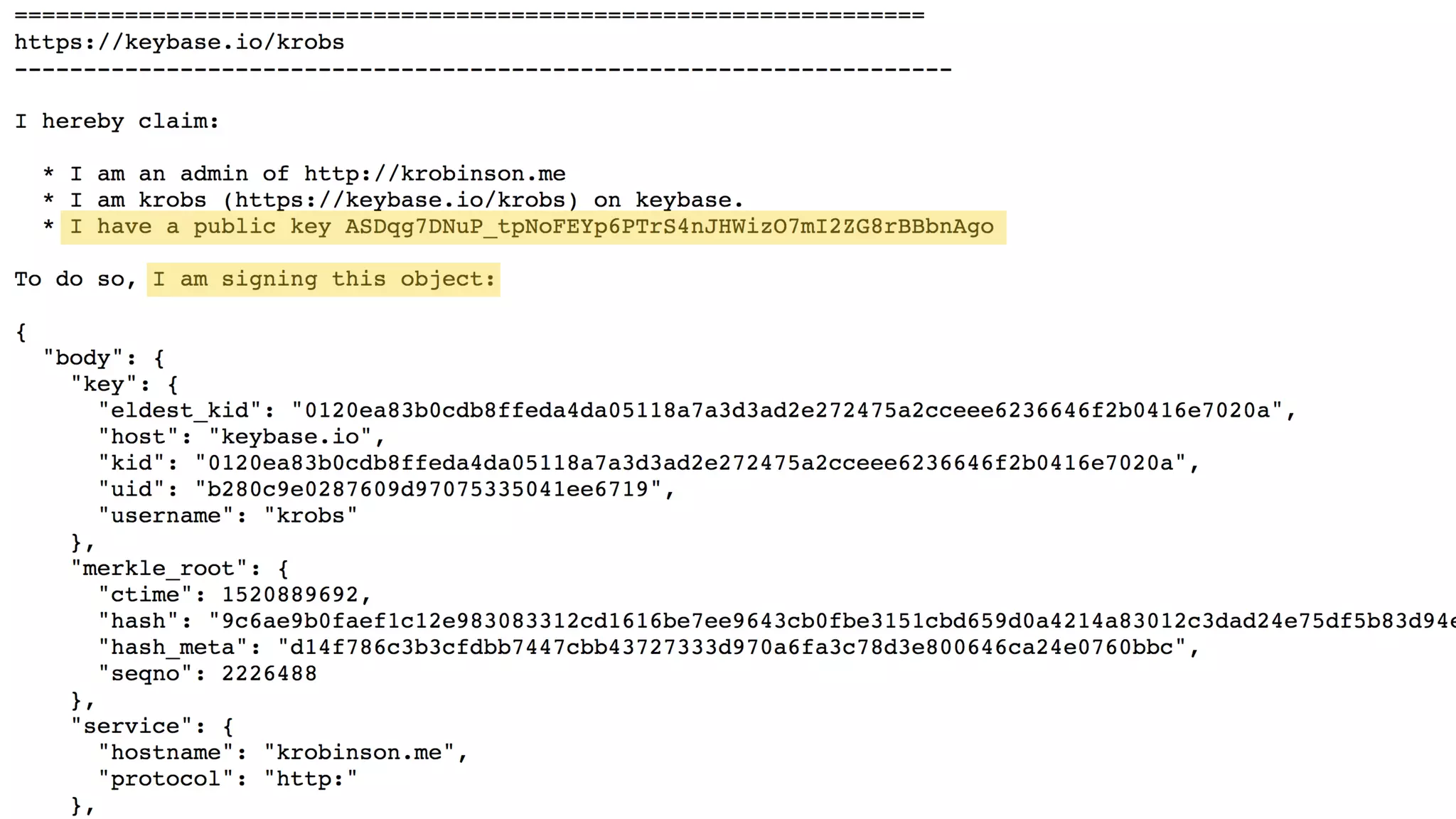
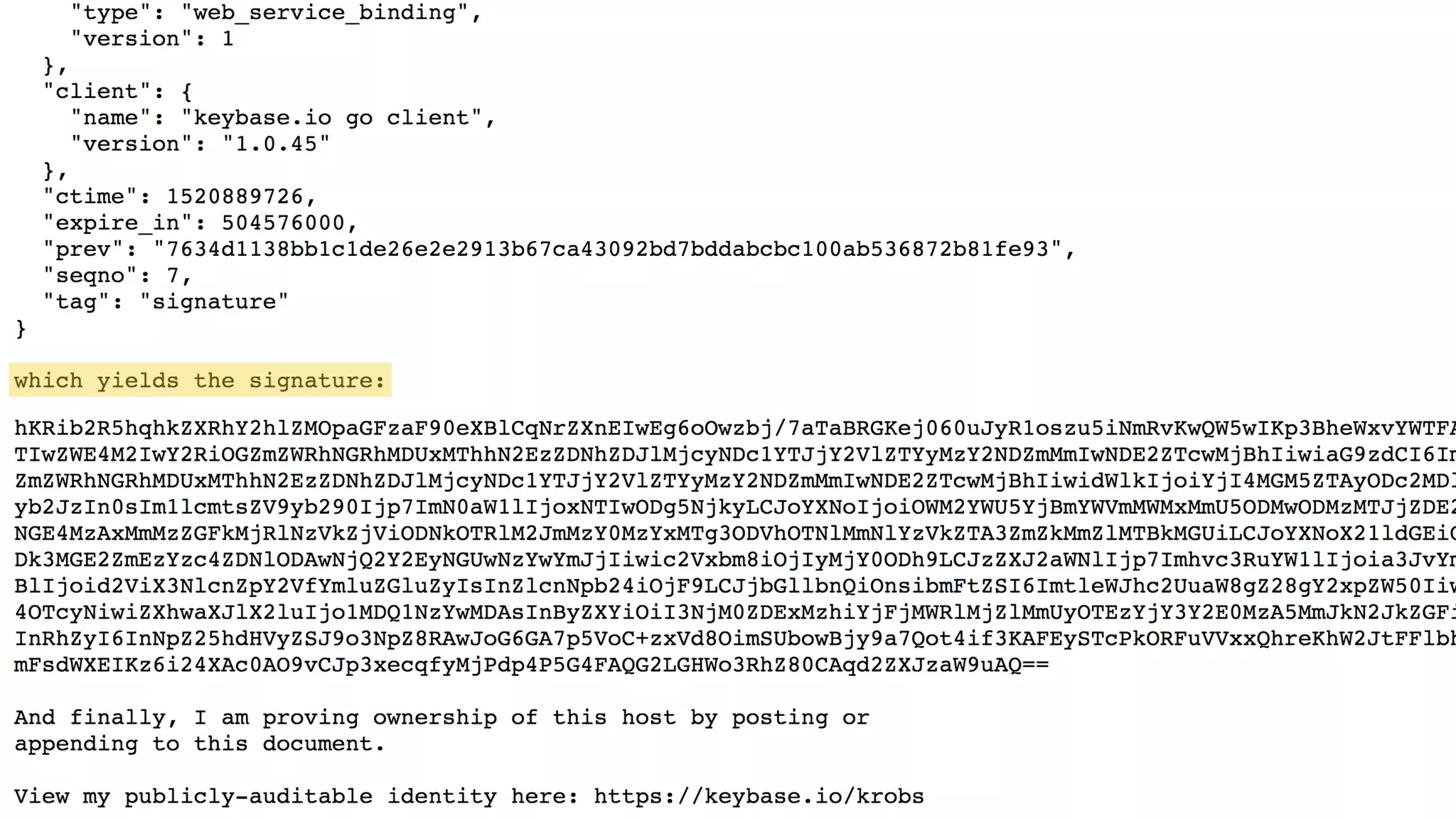
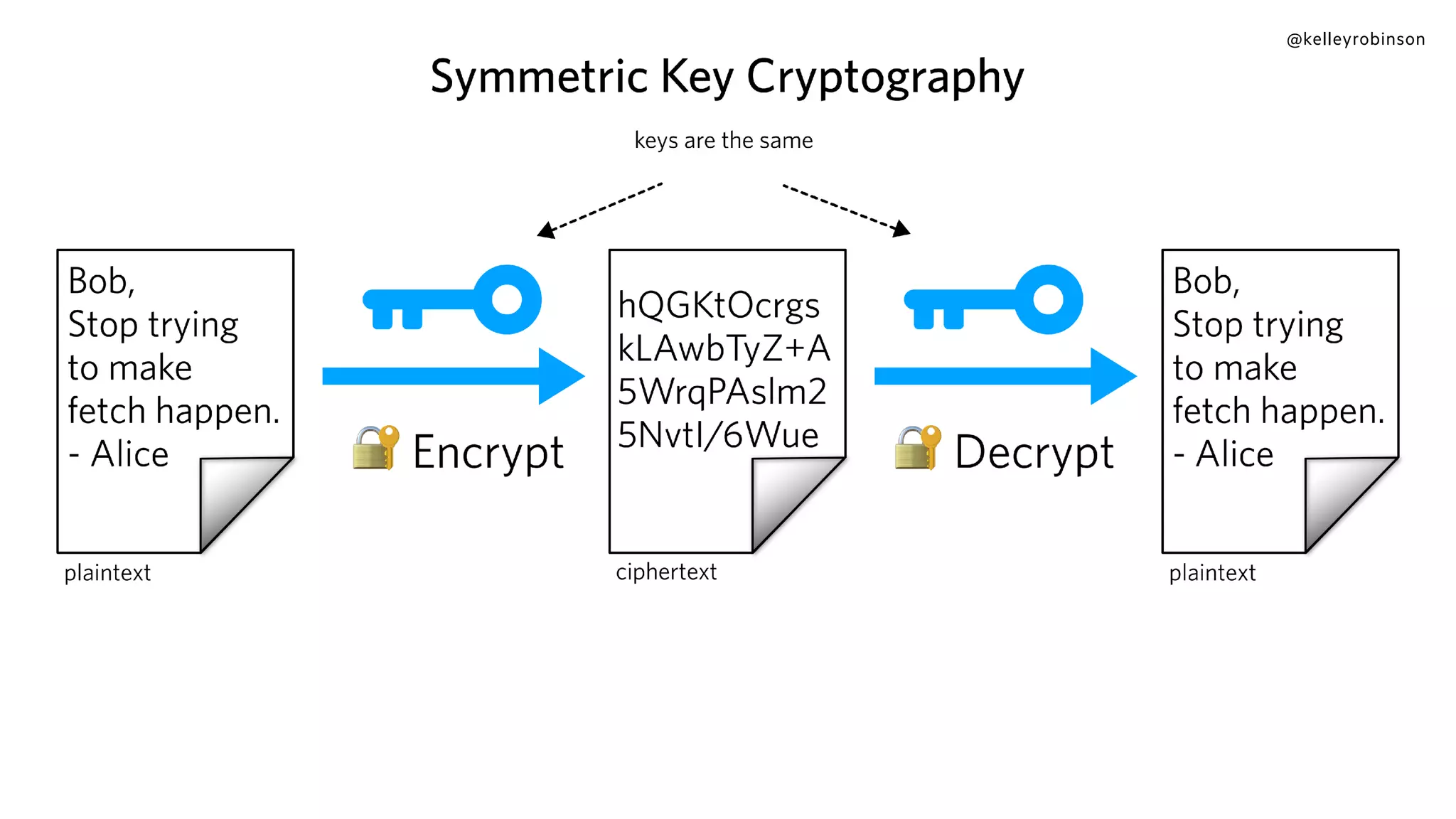
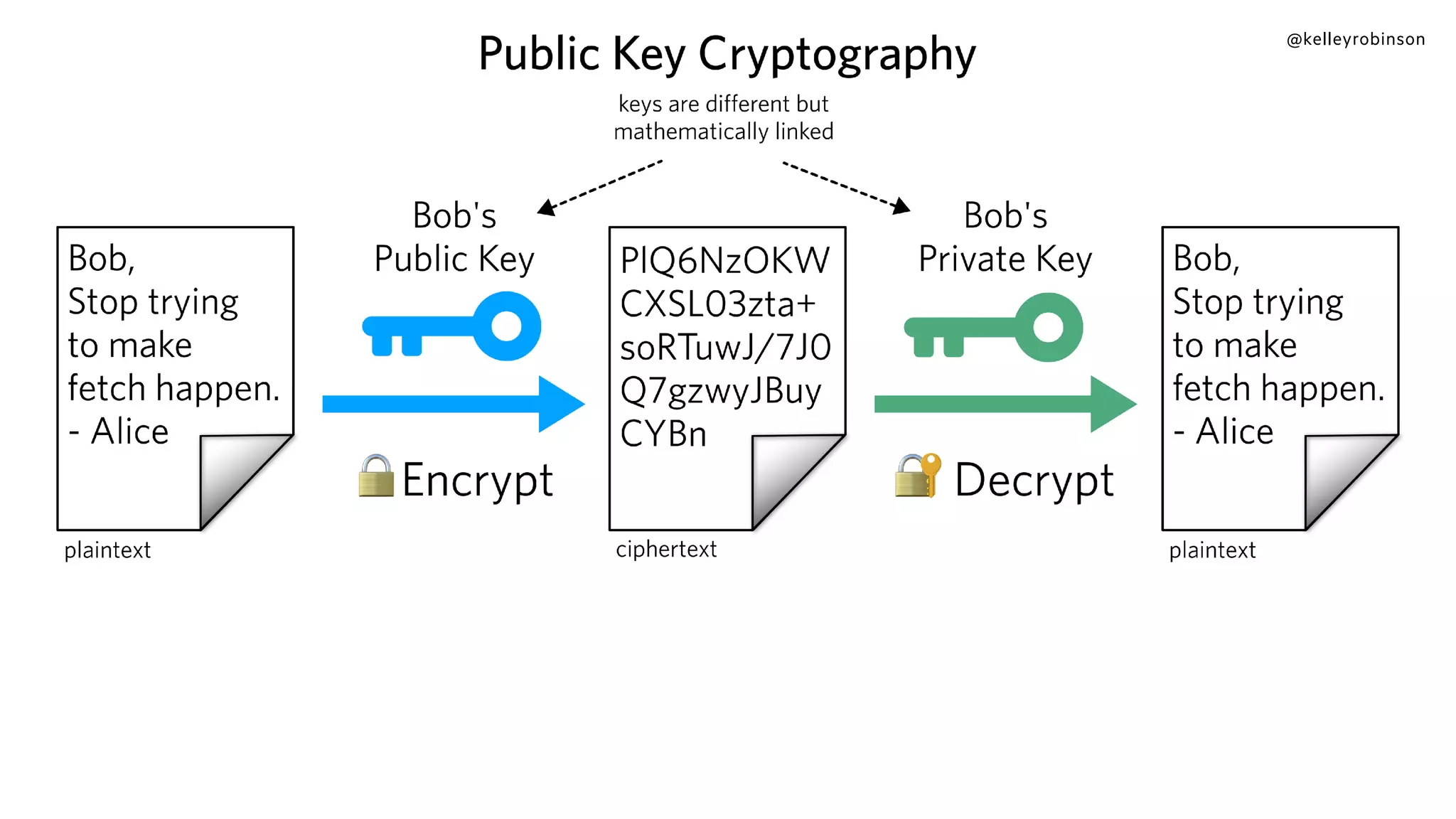
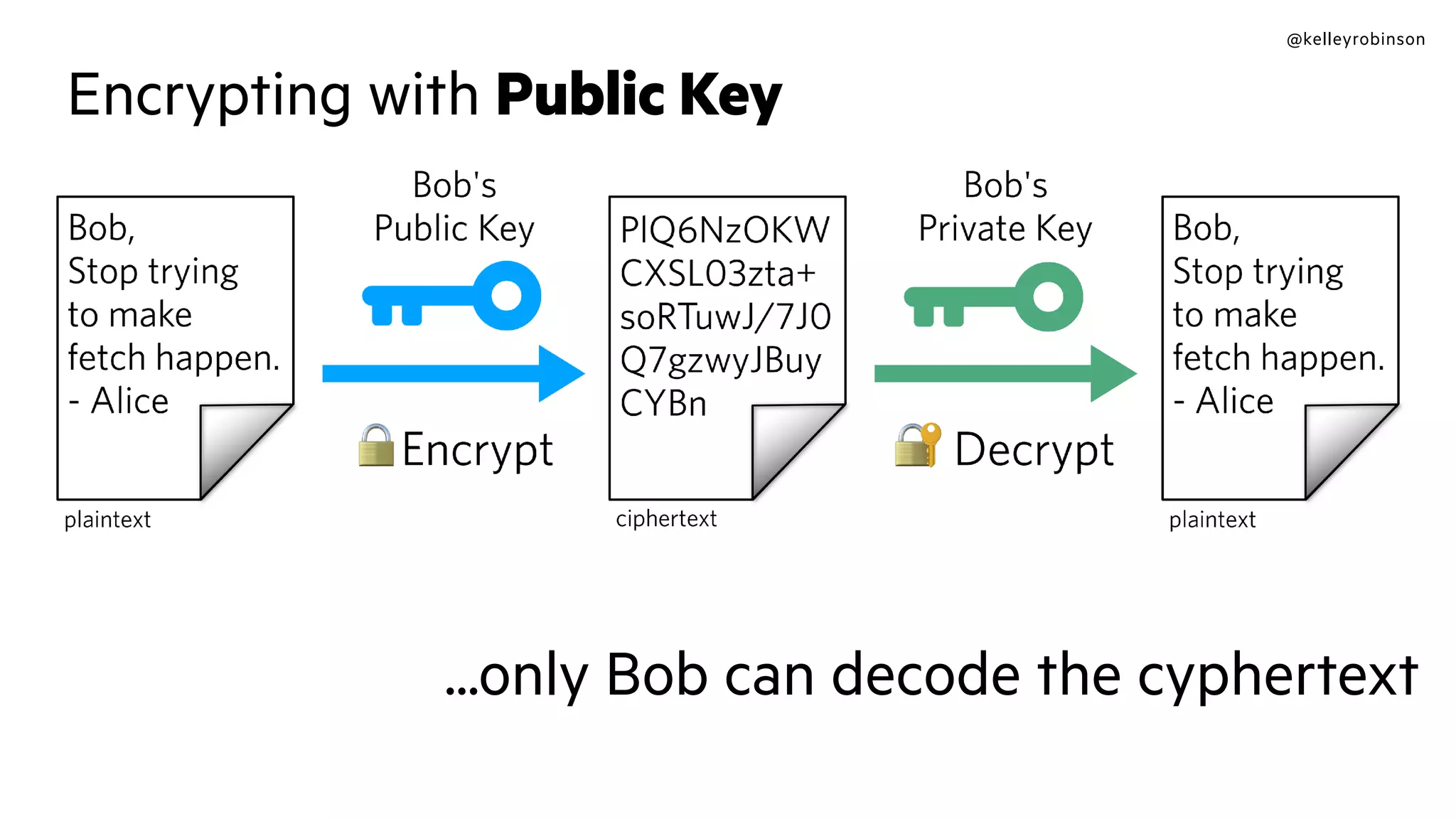
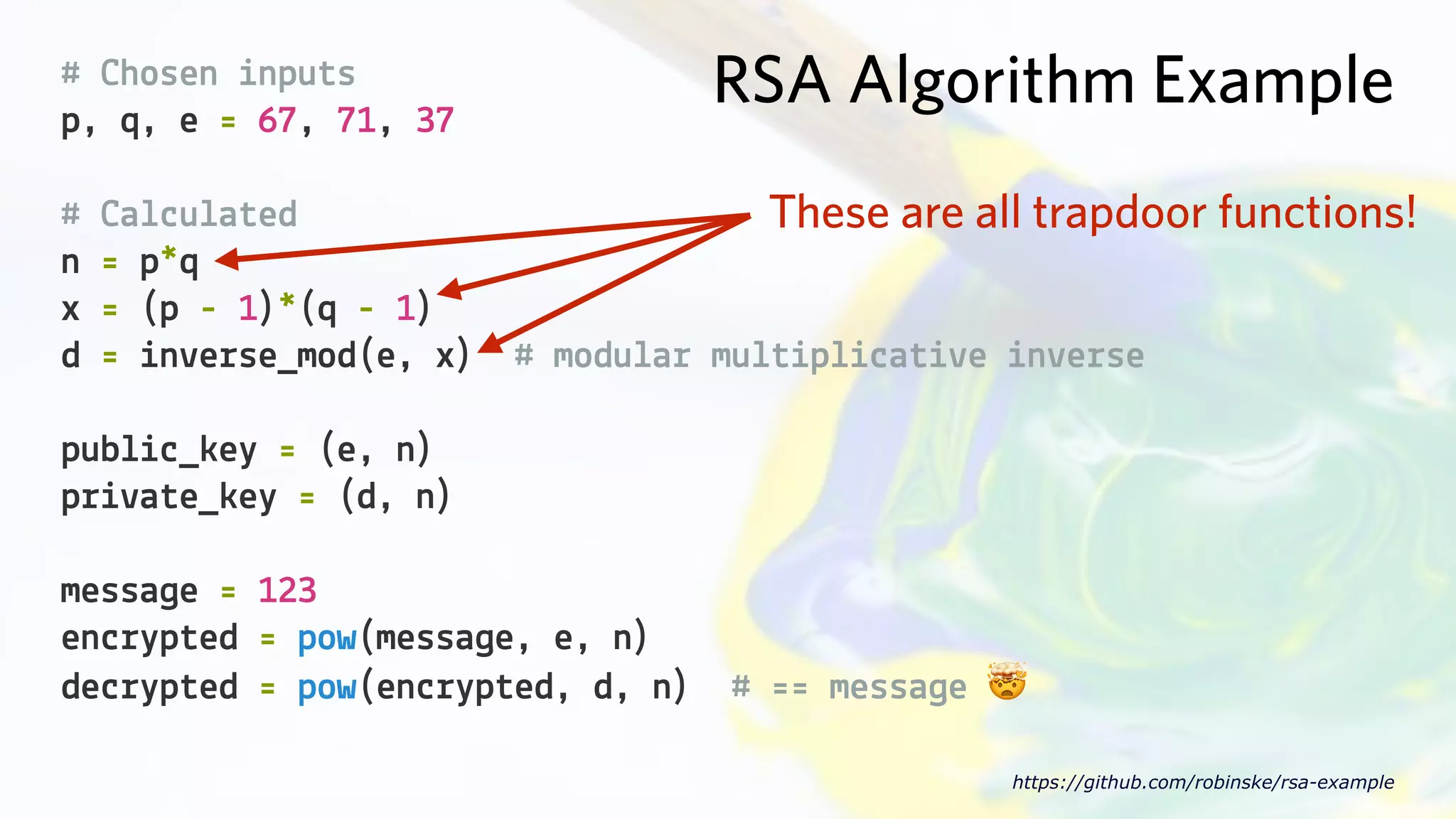
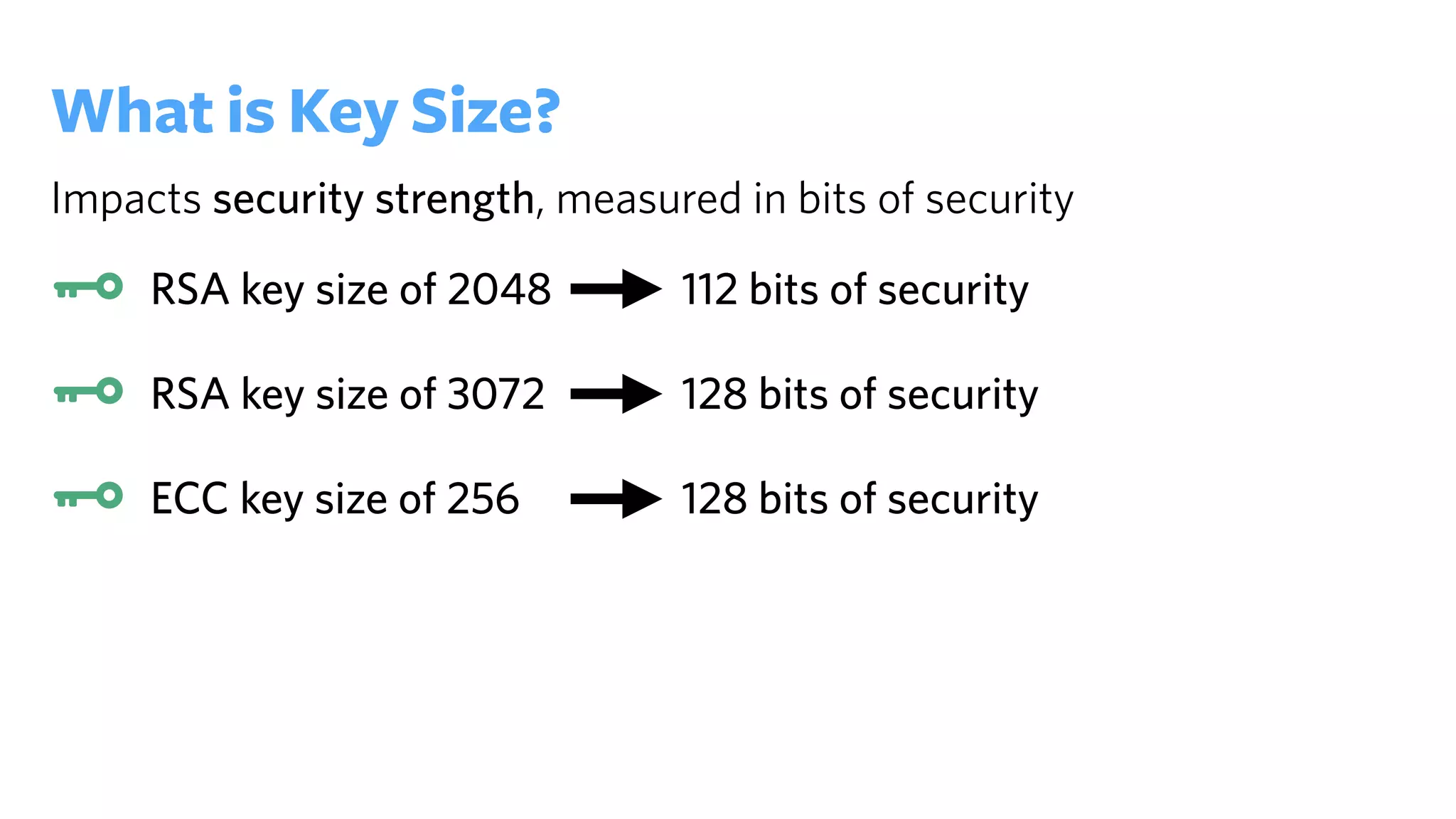
The document provides an introduction to public key cryptography (PKC), including key generation, usage, and algorithms like RSA and Diffie-Hellman. It outlines two major use cases: encrypting messages and signing digital documents, along with examples and best practices for implementation in Python. Additionally, it emphasizes the importance of key size for security and mentions everyday applications such as TLS, Bitcoin, and SSH.













![Elliptic-Curve Cryptography (ECC)
y2 = x3 + ax + b
Elliptic Curve Addition (Image By SuperManu [GFDL or CC BY-SA 3.0], via Wikimedia Commons)](https://image.slidesharecdn.com/pygotham-publickeycrypto-181005155900/75/Practical-Cryptography-22-2048.jpg)



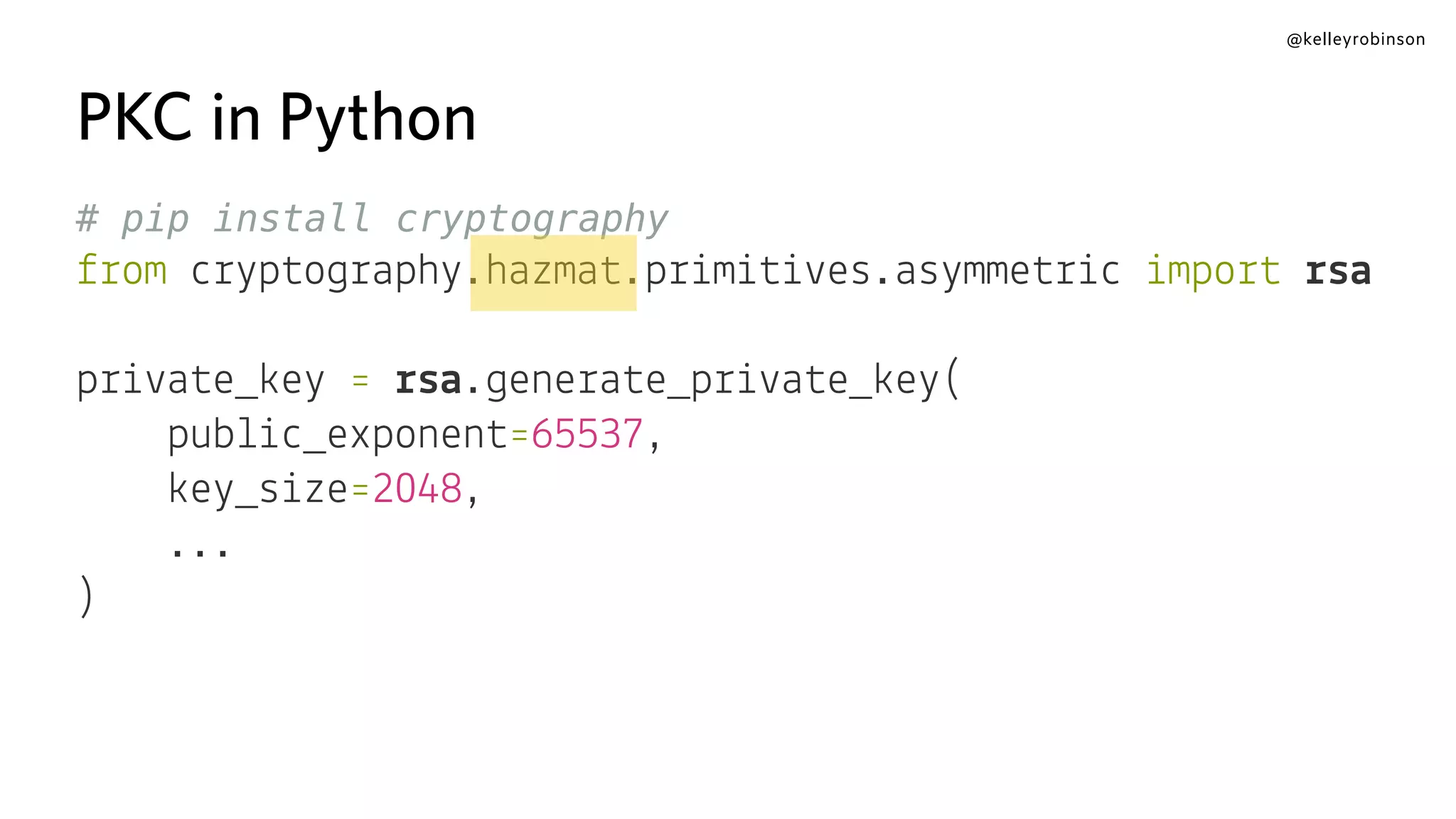
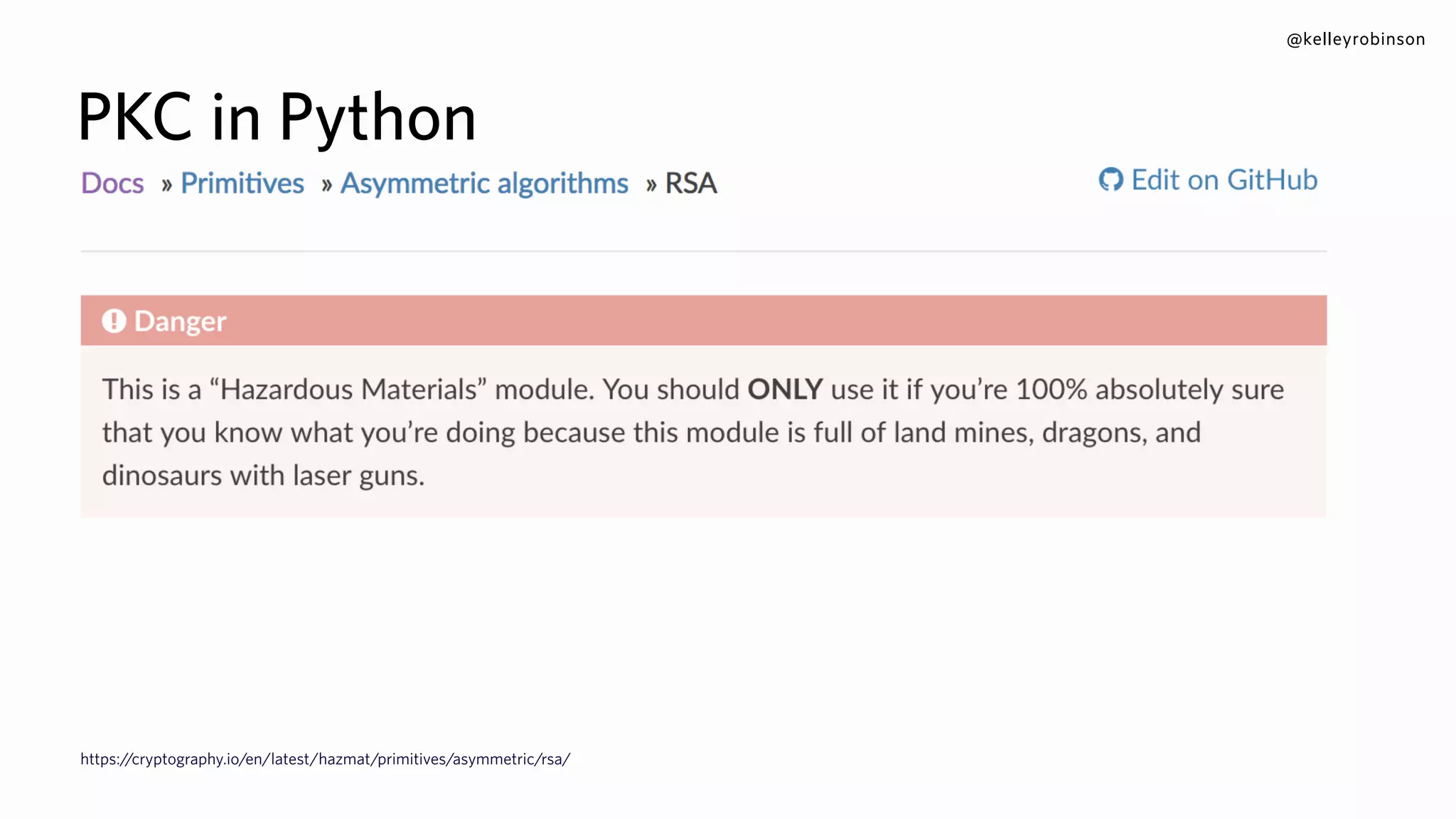



![@kelleyrobinson
]](https://image.slidesharecdn.com/pygotham-publickeycrypto-181005155900/75/Practical-Cryptography-32-2048.jpg)
![@kelleyrobinson
]
@kelleyrobinson
Public key
on the Authy
servers](https://image.slidesharecdn.com/pygotham-publickeycrypto-181005155900/75/Practical-Cryptography-33-2048.jpg)
![@kelleyrobinson
]
@kelleyrobinson
Private key
on your device](https://image.slidesharecdn.com/pygotham-publickeycrypto-181005155900/75/Practical-Cryptography-34-2048.jpg)
![@kelleyrobinson
]
@kelleyrobinson
Your device
signs with your
private key](https://image.slidesharecdn.com/pygotham-publickeycrypto-181005155900/75/Practical-Cryptography-35-2048.jpg)