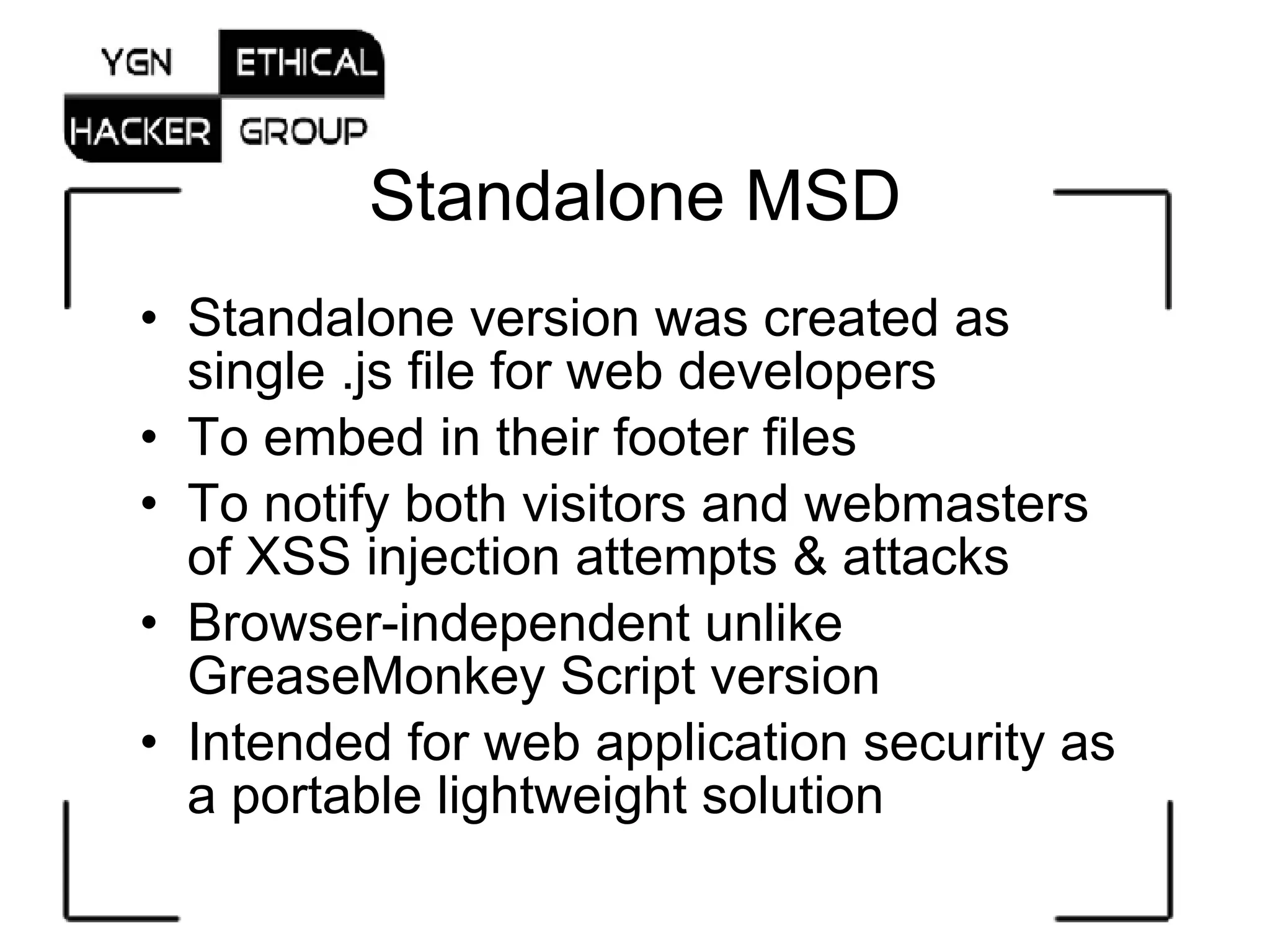
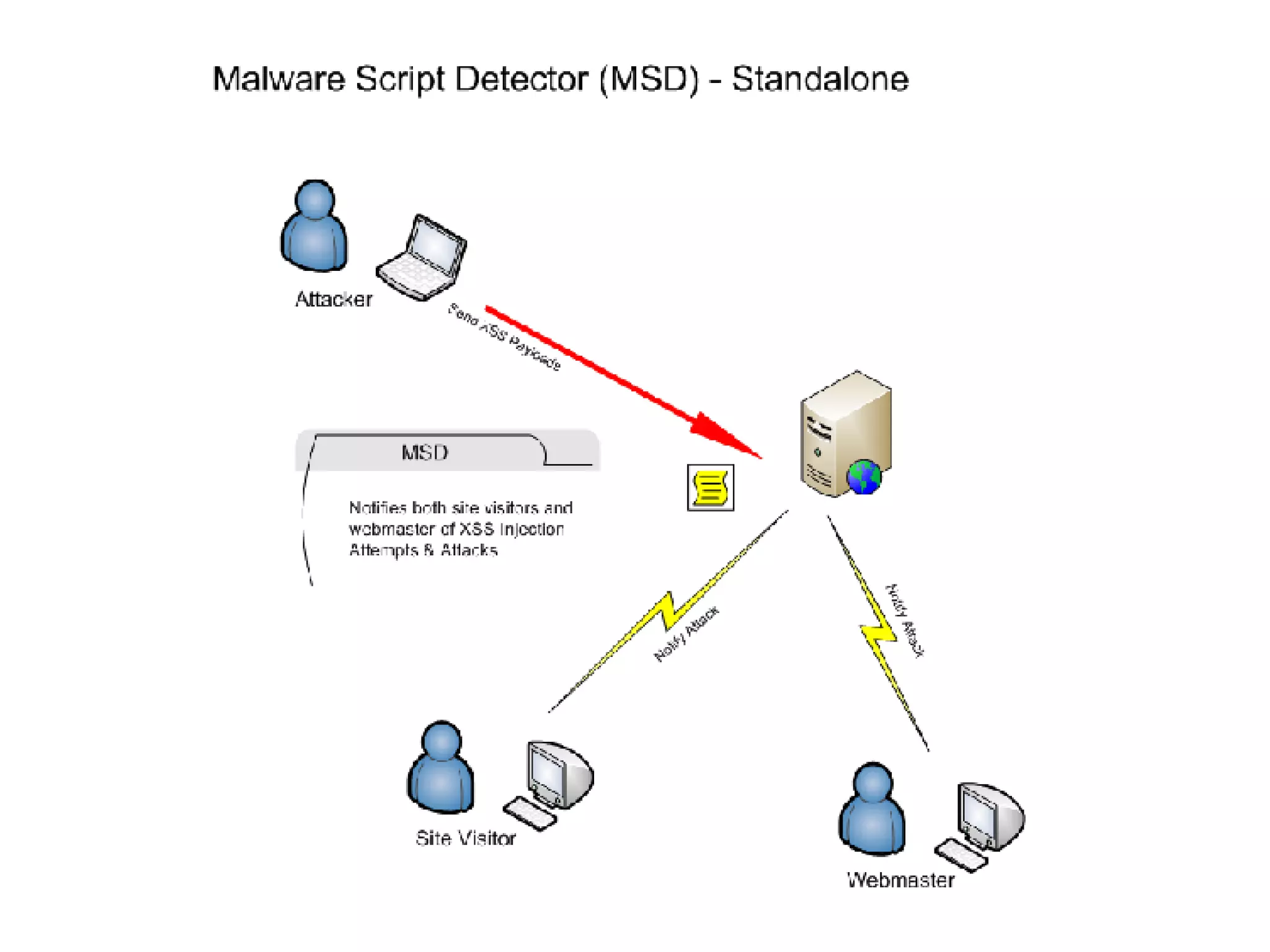
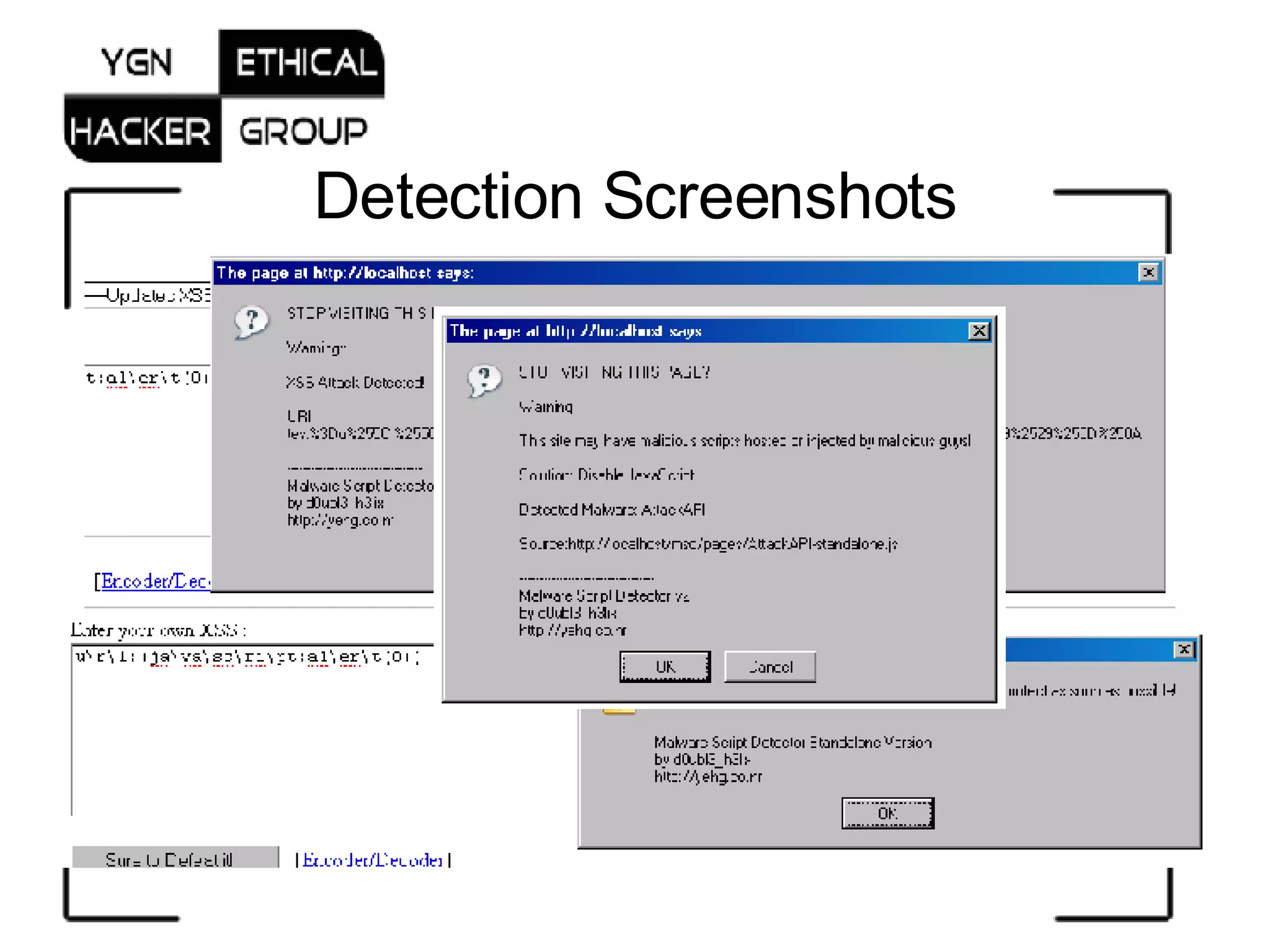
The document introduces the Malware Script Detector (MSD) designed by d0ubl3_h3lix, which focuses on identifying malicious JavaScript and XSS threats to enhance web client security. It outlines the functionality of MSD as a browser-independent solution, including its versioning, detection capabilities, and limitations, specifically within Gecko browsers with the Greasemonkey addon. Additionally, it encourages user contributions and discusses the inadequacies of traditional security measures against embedded malicious scripts.