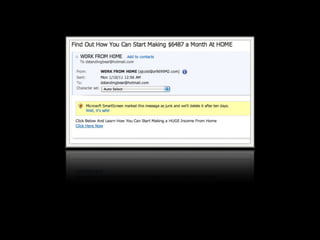
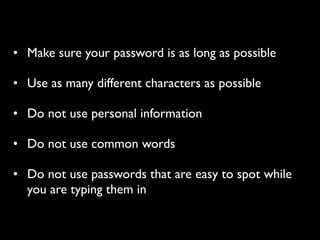
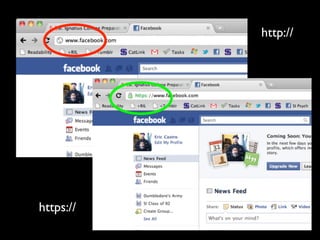
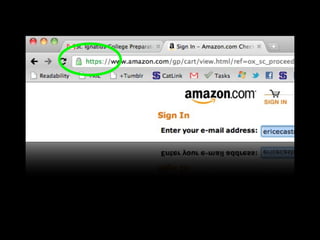
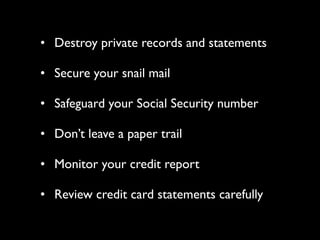
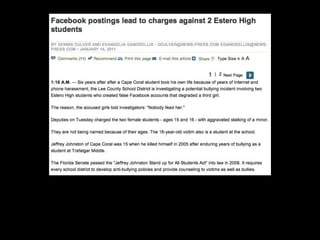
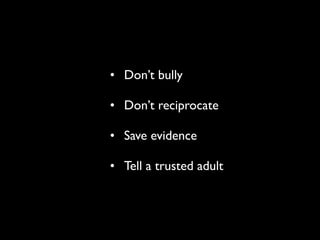
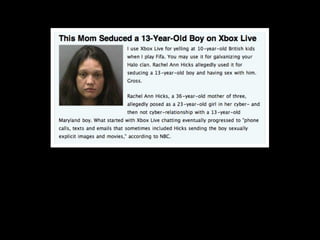
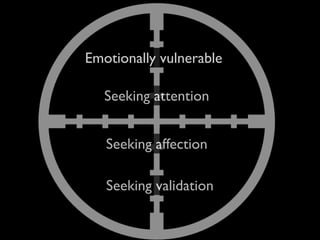
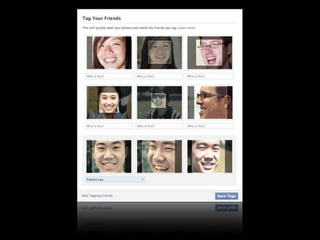
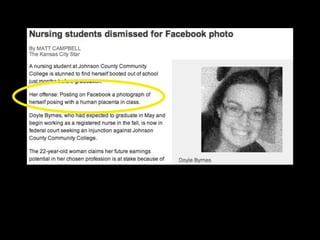
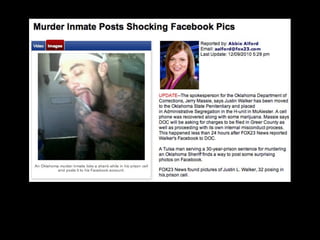
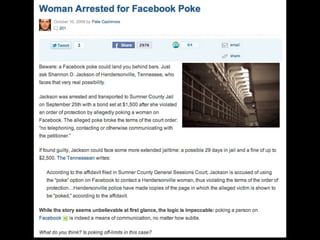
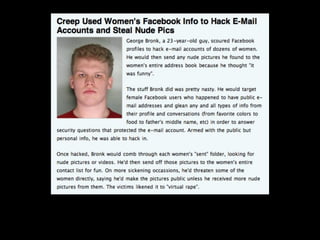
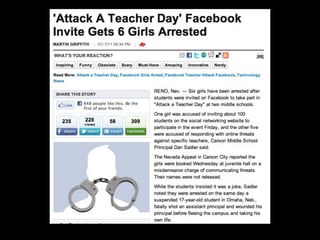
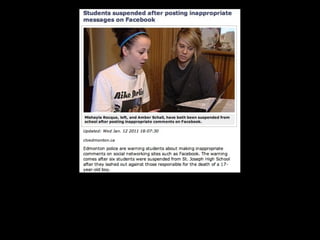
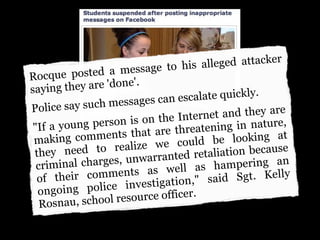
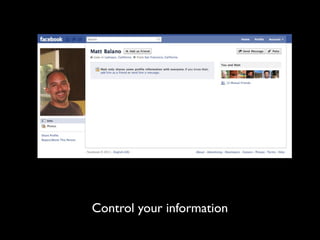
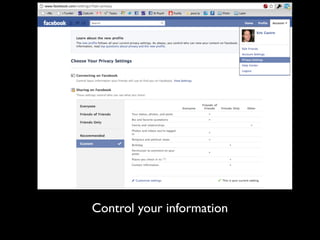
This document provides tips on internet safety. It discusses creating a positive digital footprint, protecting privacy, protecting against identity theft, bullying, predators, and yourself. Some key tips include using strong and unique passwords, monitoring credit reports, not engaging with bullies online, and being cautious about what personal information you share.