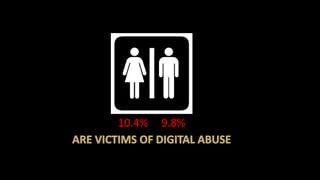
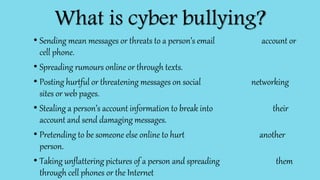
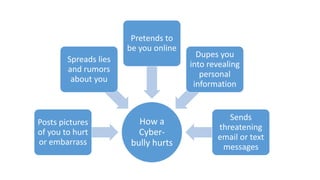
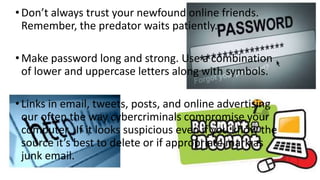
The document discusses cyber safety and cyberbullying. It notes that the internet is a vast source of information but also has dangers, like cyberbullying. Cyberbullying involves sending mean or threatening messages online and can include spreading rumors, posting embarrassing photos, or stealing accounts. Cyberbullying can have severe consequences, as 20% of cyberbullied kids consider suicide. The document provides tips to stay safe online, like using privacy settings, not sharing personal information, blocking bullies, and reporting any issues to parents or authorities. While the internet is useful, people need to be aware of potential risks and take precautions to have positive online experiences.