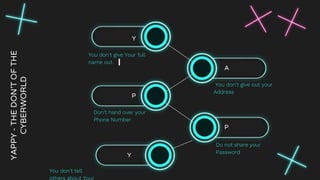
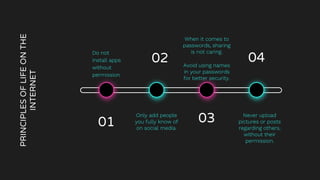
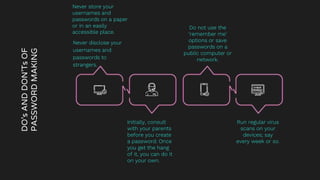
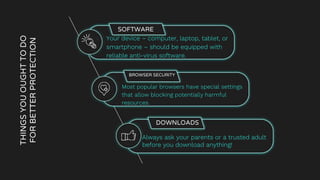
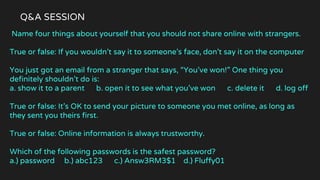
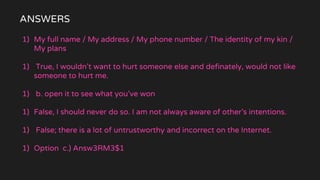
The document is a comprehensive guide on internet security and cybersecurity, highlighting the importance of protecting personal data and understanding cyber threats. It covers definitions of cybersecurity and cybercrime, common online dangers, and safety tips for internet usage, particularly for children. Additionally, it emphasizes the significance of strong passwords, cautious behavior online, and the role of parental guidance in ensuring safe internet practices.