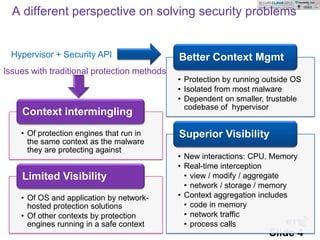
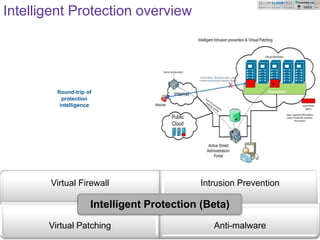
This document discusses challenges in protecting virtual data centers and cloud systems. It describes emerging solutions like running protection engines outside the operating system context in a hypervisor to gain better visibility and context. Intelligent Protection is introduced as a solution using a hypervisor to intercept interactions and apply security controls like a virtual firewall, intrusion prevention, and anti-malware. Future extensions are outlined like integrating multiple anti-malware engines and applying these techniques beyond clouds to mobile devices.