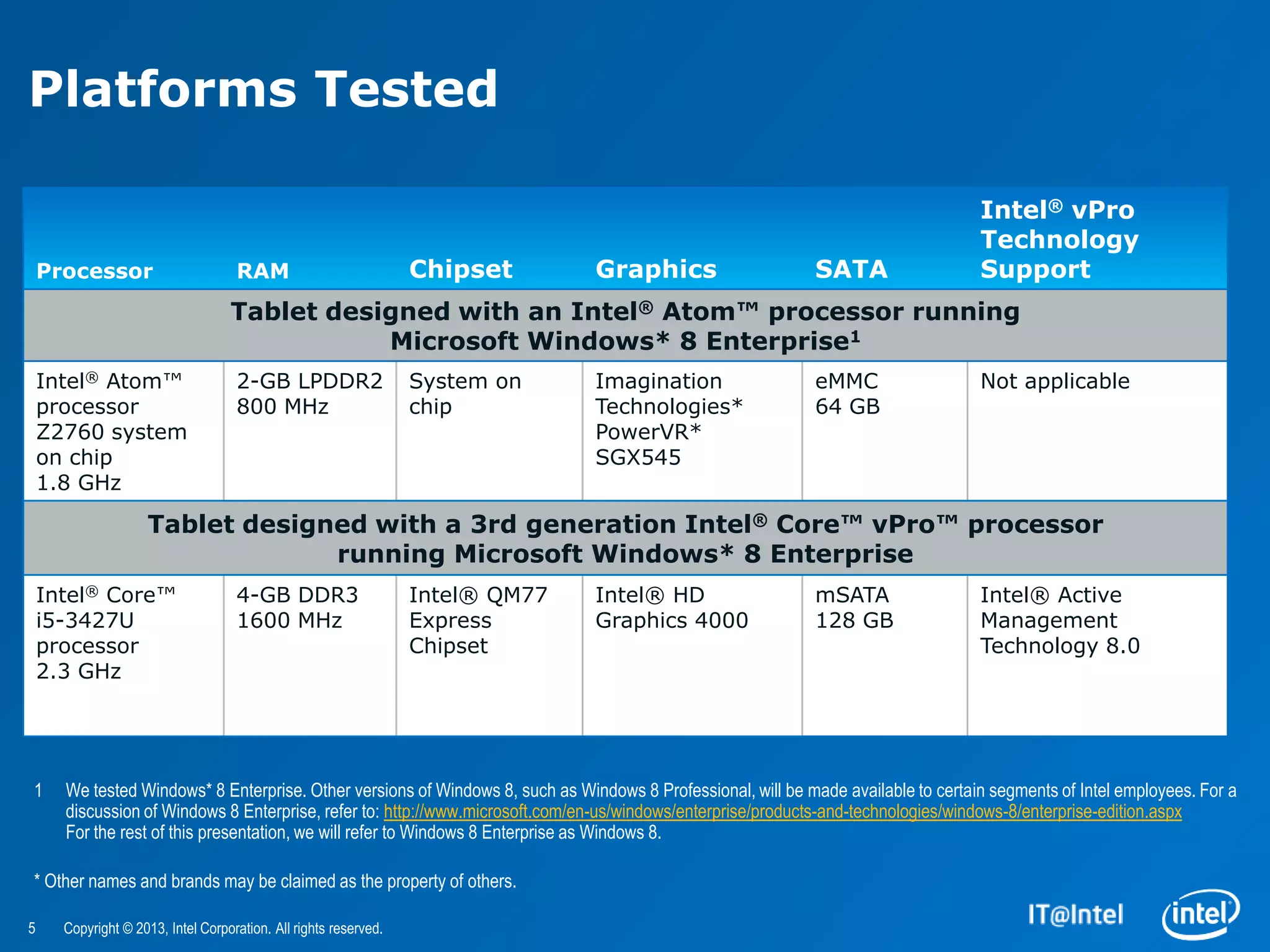
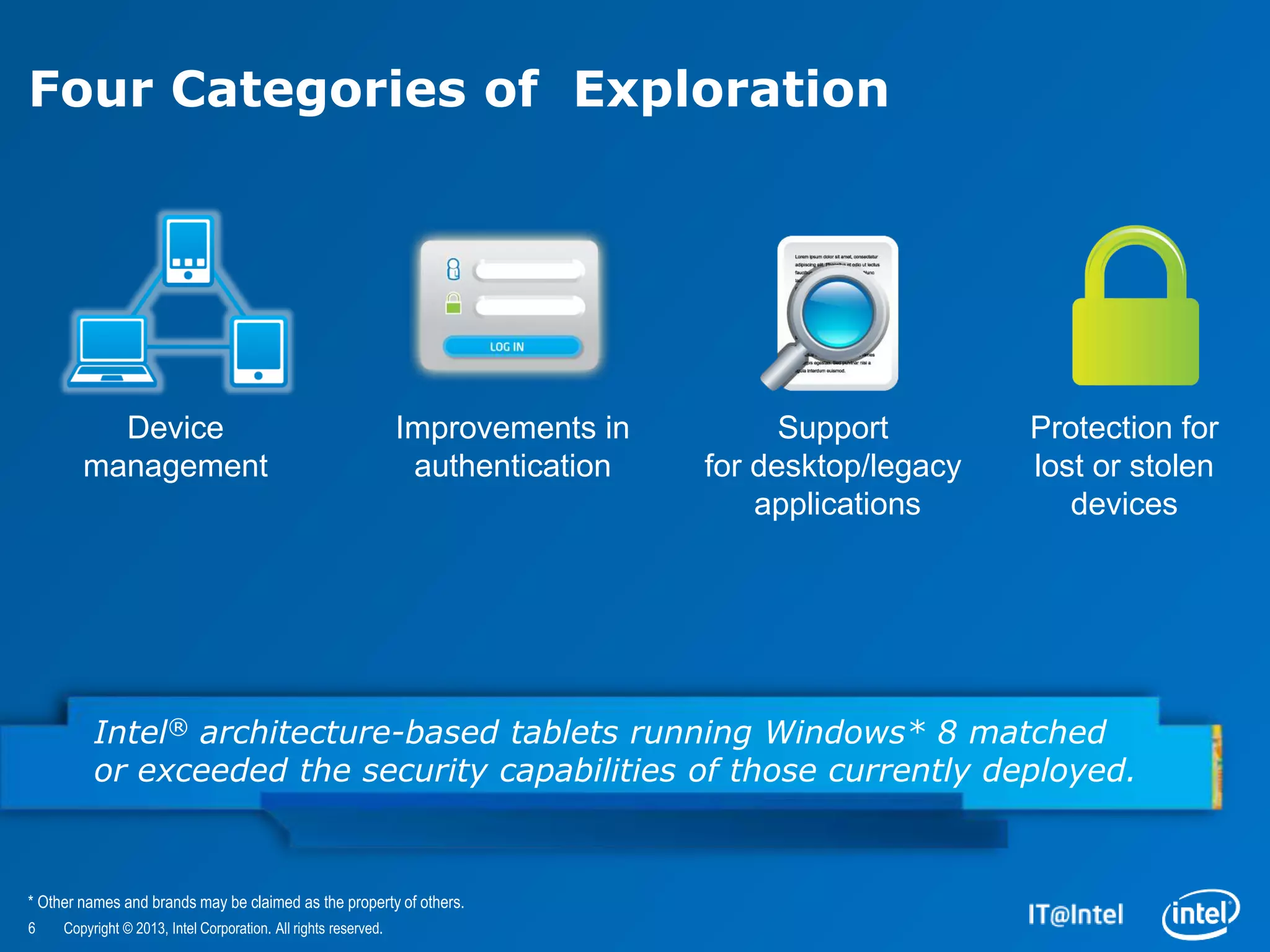
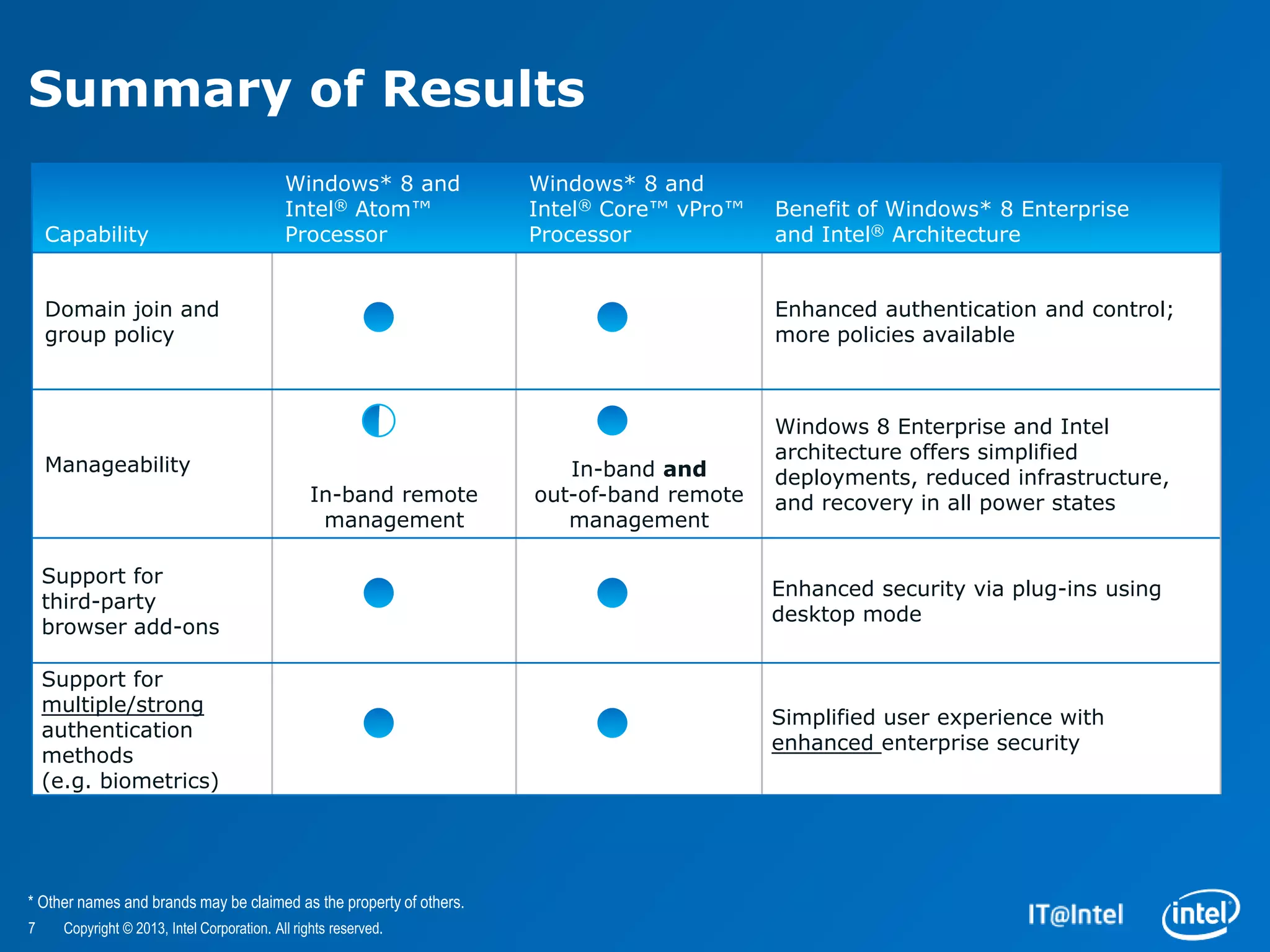
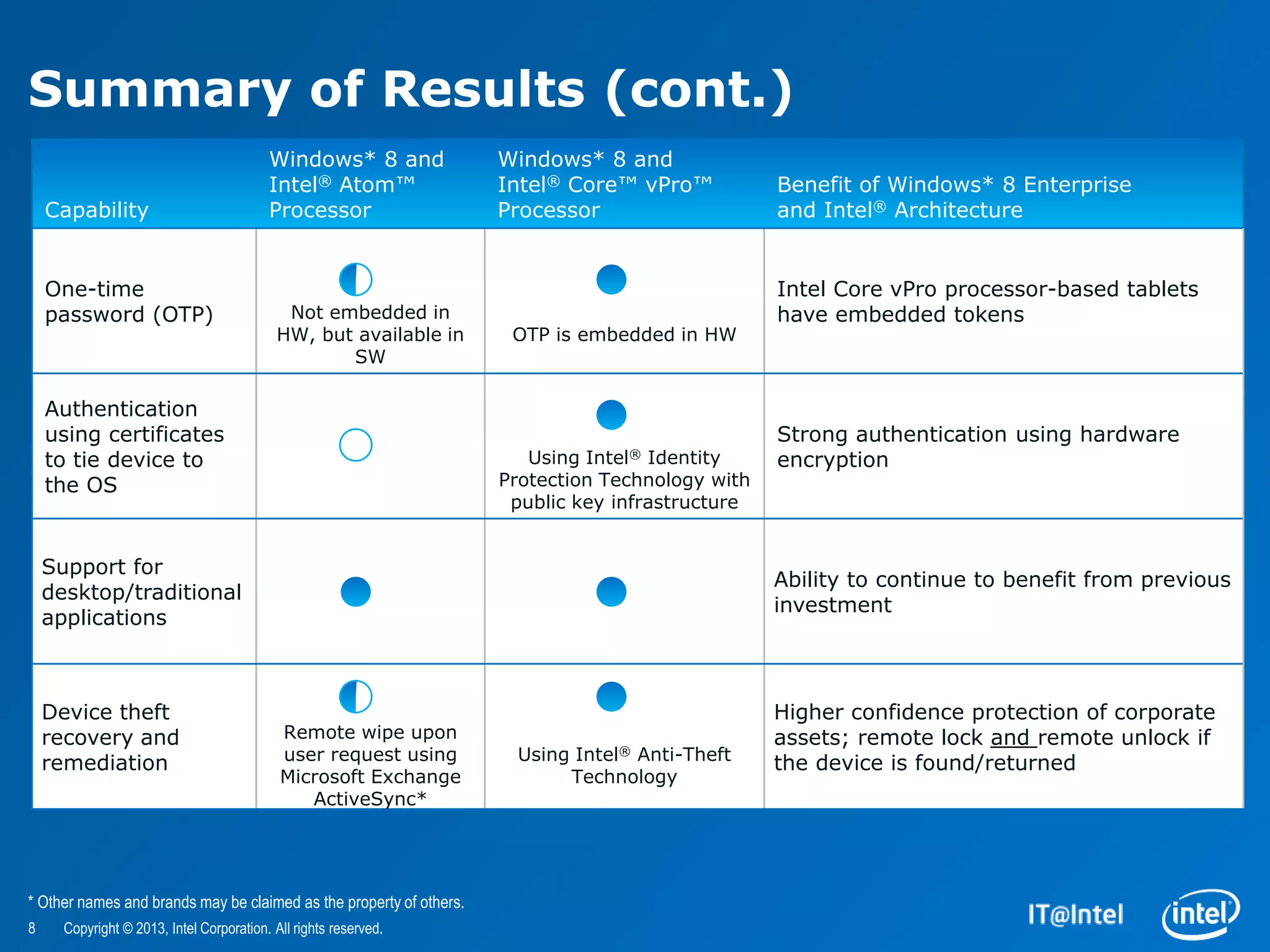
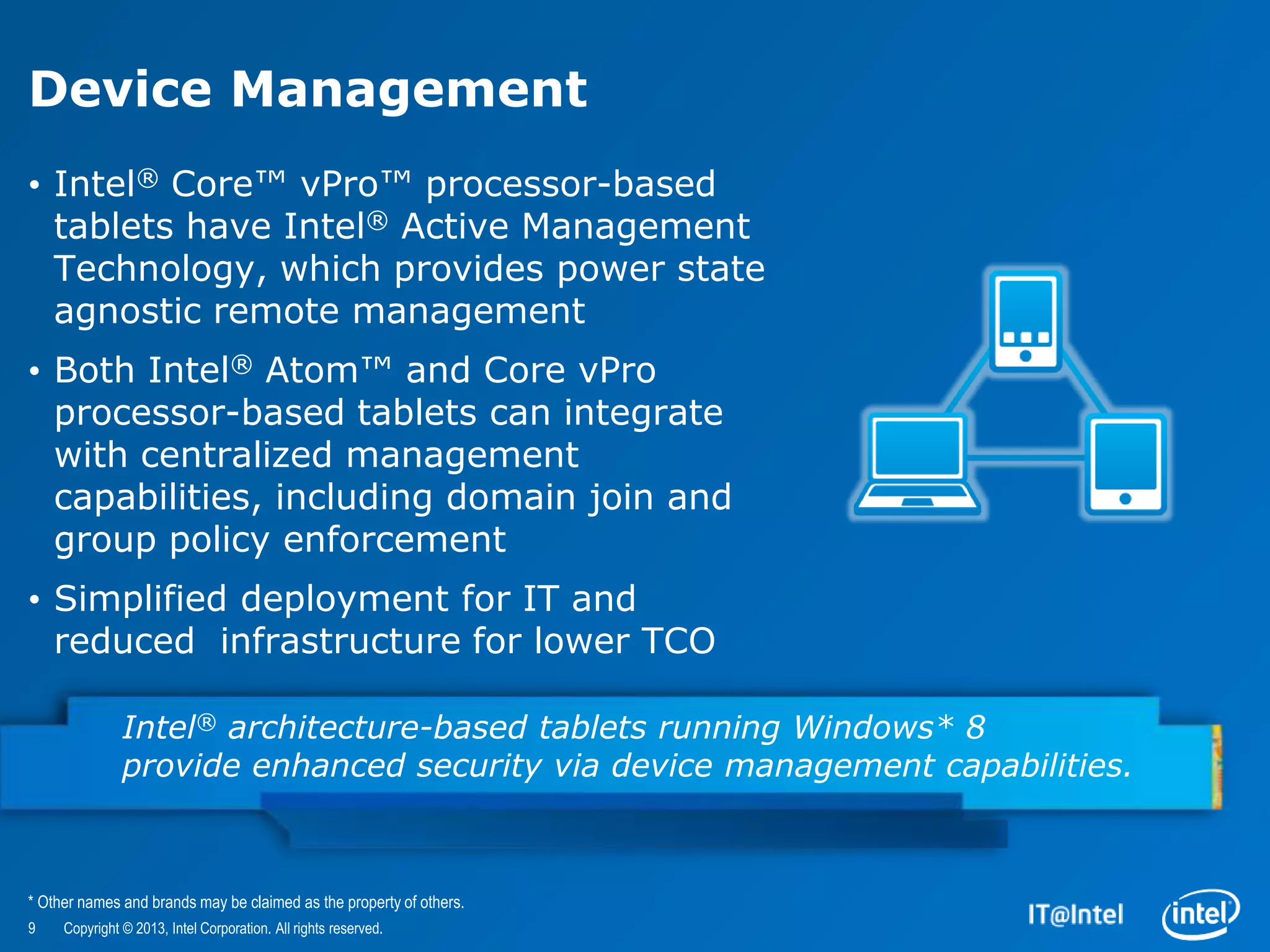
The document evaluates the security features and management capabilities of Microsoft Windows 8 on Intel architecture-based tablets. It highlights improvements in security, device management, and user experience, demonstrating that these devices are suitable for enterprise use. Key technologies discussed include Intel's identity protection and anti-theft technologies designed to enhance corporate security and productivity.