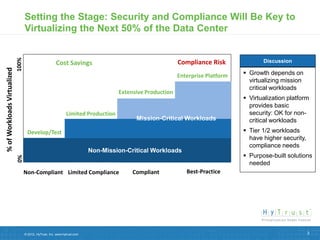
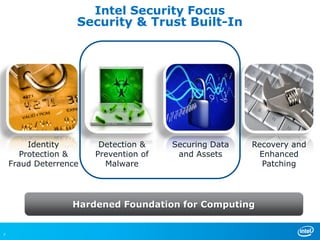
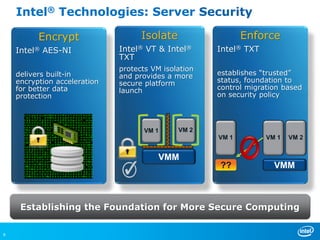
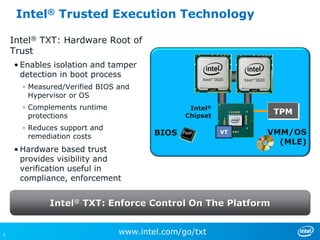
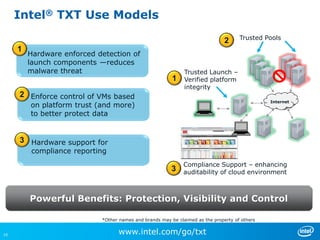
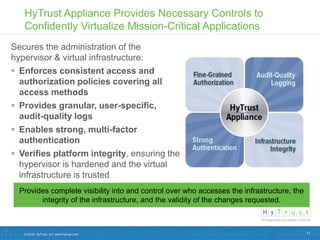
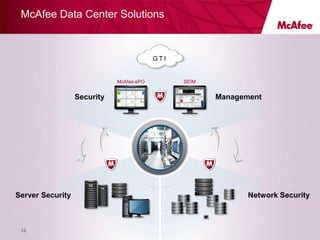
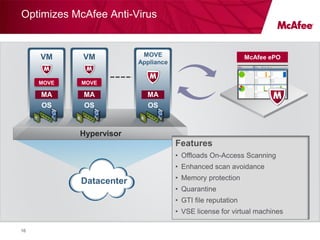
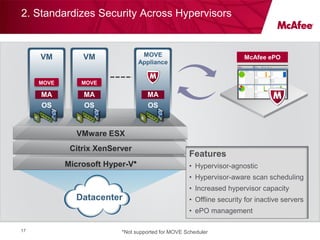
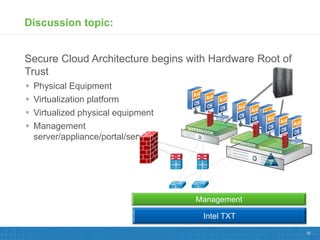
Virtualizing more of an organization's workloads presents both opportunities and risks. As more mission-critical workloads are virtualized, security and compliance become greater priorities. Purpose-built solutions that provide security, visibility, and control over virtual infrastructure and assets are needed. Intel, HyTrust, and McAfee are partnering to provide comprehensive solutions through technologies like Intel TXT, the HyTrust Appliance, and McAfee security products to help organizations securely virtualize more workloads while improving their security posture and compliance.