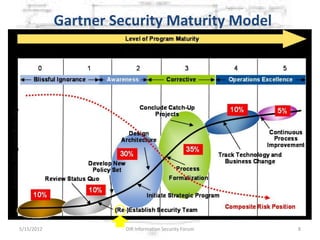
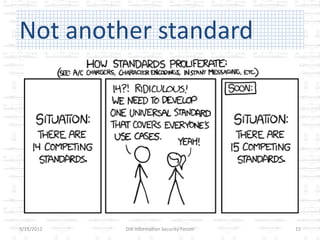
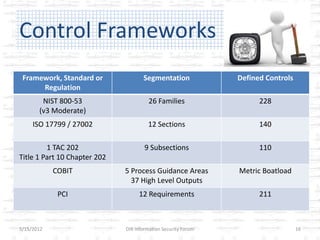
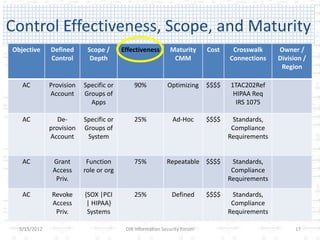
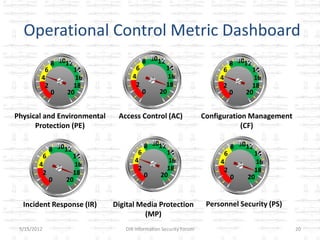
The document discusses the gap between perception and reality in security. It notes that many factors contribute to widening this gap, including inconsistent standards implementation, ambiguous regulations, and subjective risk assessments. The author proposes using standardized security metrics to narrow this gap and build bridges between perception and reality. Specifically, metrics should measure what security controls are implemented, how effective they are, and the residual risks remaining. This can help organizations determine if they are truly secure and provide a framework for a sustainable security program.