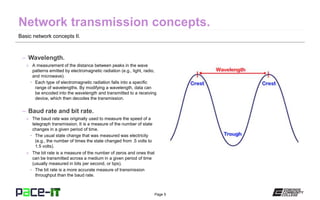
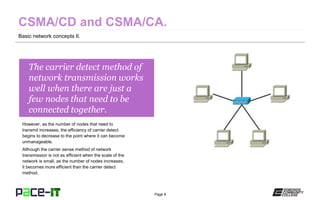
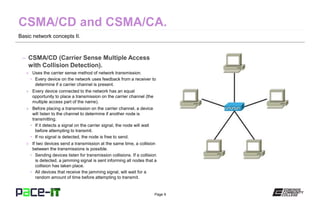
The document discusses basic network concepts and various methods of network transmission, focusing on carrier detect and carrier sense techniques. It explains the differences between CSMA/CD and CSMA/CA, highlighting their applications in wired and wireless networks. The document also includes the author's qualifications and a brief overview of electromagnetic radiation properties related to networking.