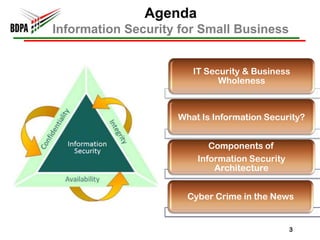
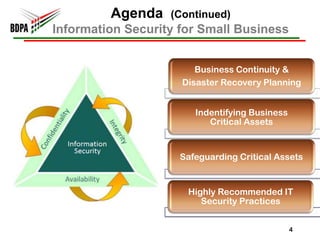
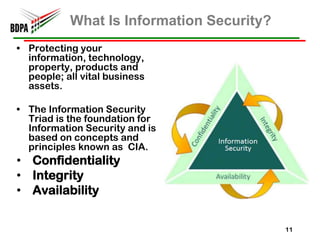
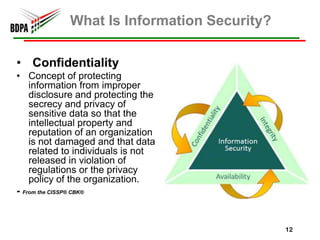
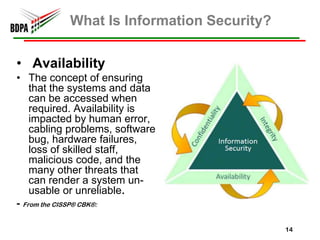
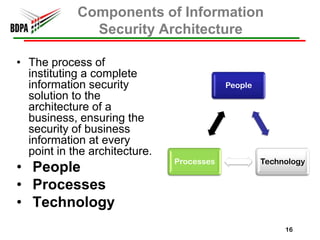
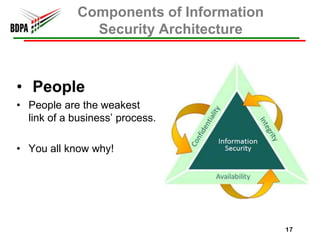
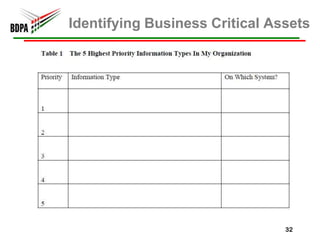
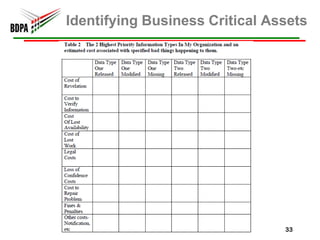
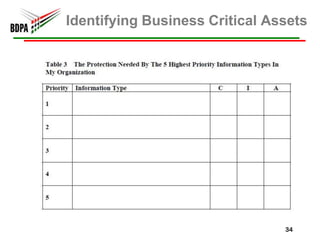
This document provides information security recommendations and best practices for small businesses. It discusses identifying critical business assets, safeguarding people, processes, and technology. Specific recommendations include implementing policies, access controls, backups, antivirus software, firewalls, wireless security, software patching, and employee training. The document emphasizes establishing a strong security foundation through assessing risks and prioritizing asset protection based on confidentiality, integrity, and availability needs.