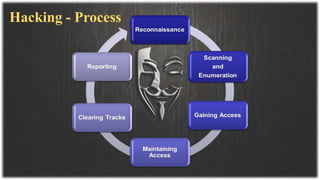
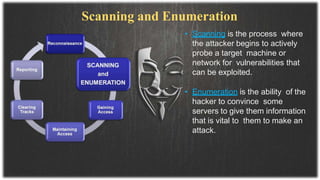
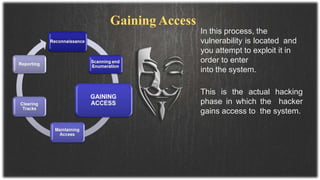
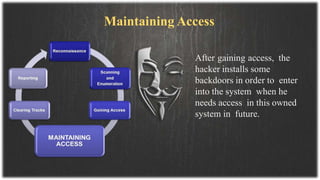
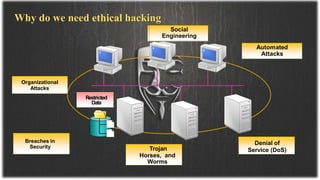
This document presents information on ethical hacking. It discusses the types of ethical hacking including white hat, grey hat, and black hat hackers. The ethical hacking process is described including reconnaissance, scanning and enumeration, gaining access, maintaining access, clearing tracks, and reporting. Reasons for needing ethical hacking are provided such as security breaches and denial of service attacks. Tips are given on how to protect yourself from hacking. Advantages include strengthening security, while disadvantages include cost. The conclusion emphasizes the importance of staying updated on software and educating users to be aware of hacking techniques.