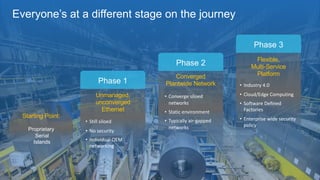
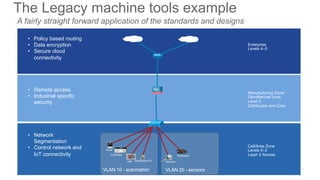
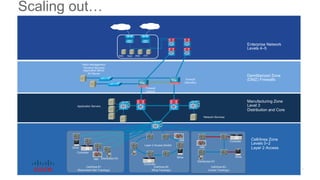
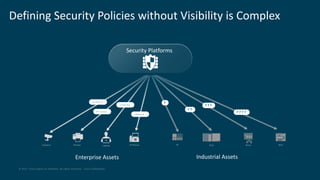
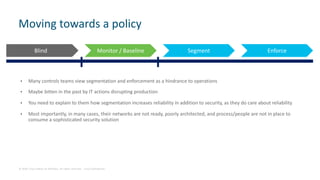
The document discusses several challenges in securing industrial networks for Industry 4.0, including enabling internet connectivity, legacy vulnerable devices, and the need for remote access. It describes moving networks from proprietary and isolated "islands" to a converged plantwide network with flexible multi-service platforms. The document provides an example of applying network standards and designs to segment a legacy machine tools network. It emphasizes that defining security policies requires network visibility and moving through stages from blind monitoring to segmentation and enforcement.