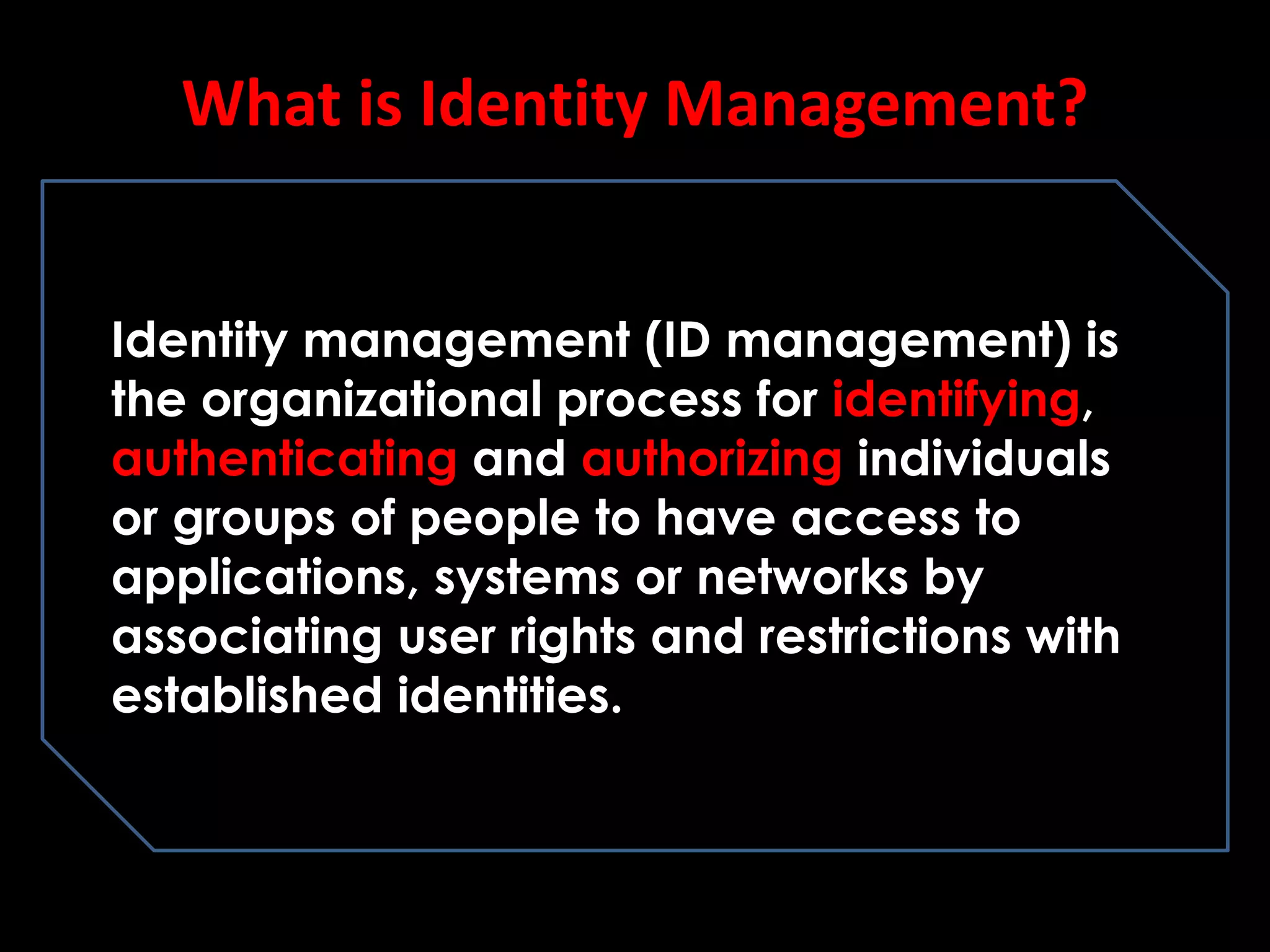
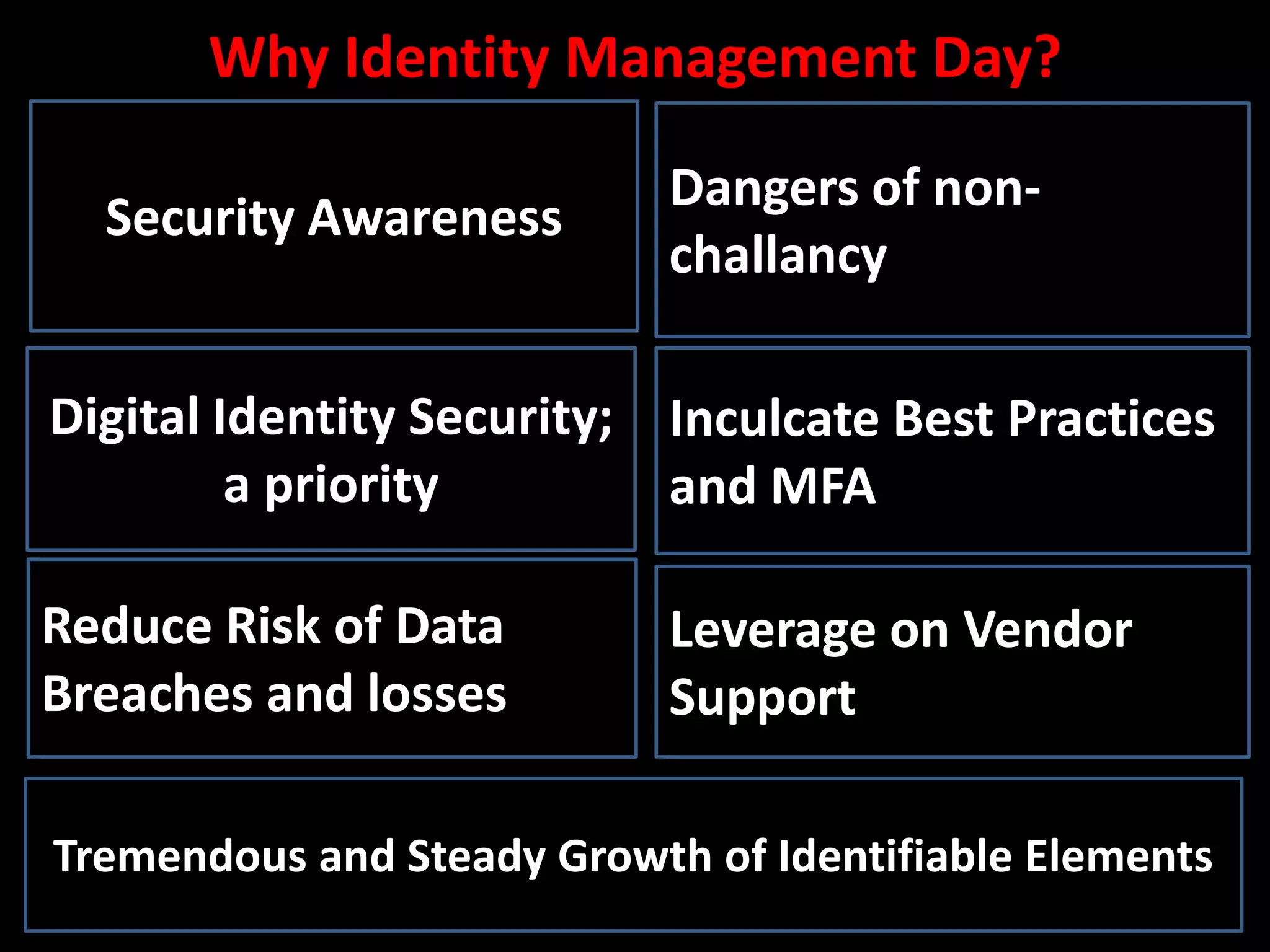
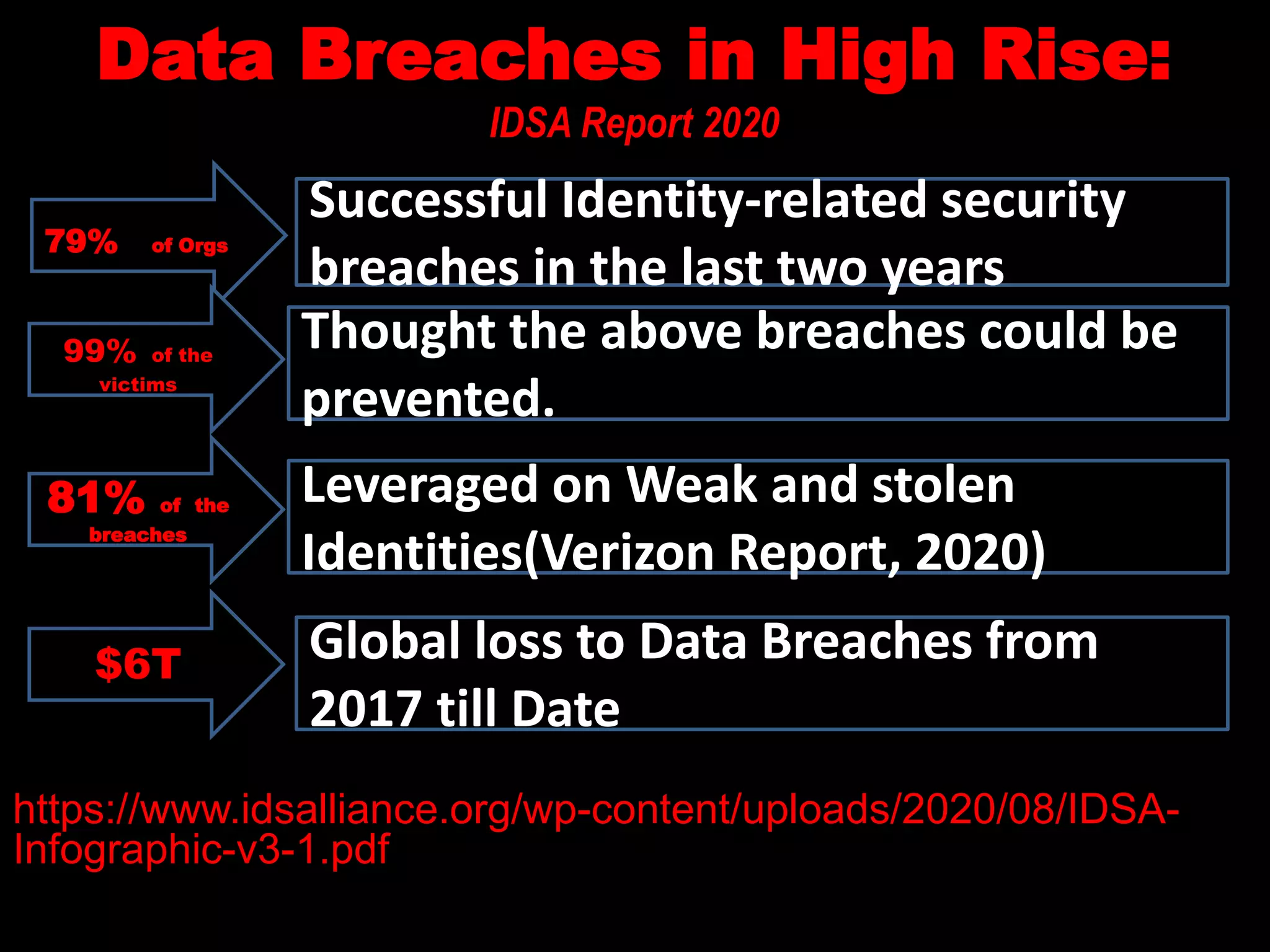
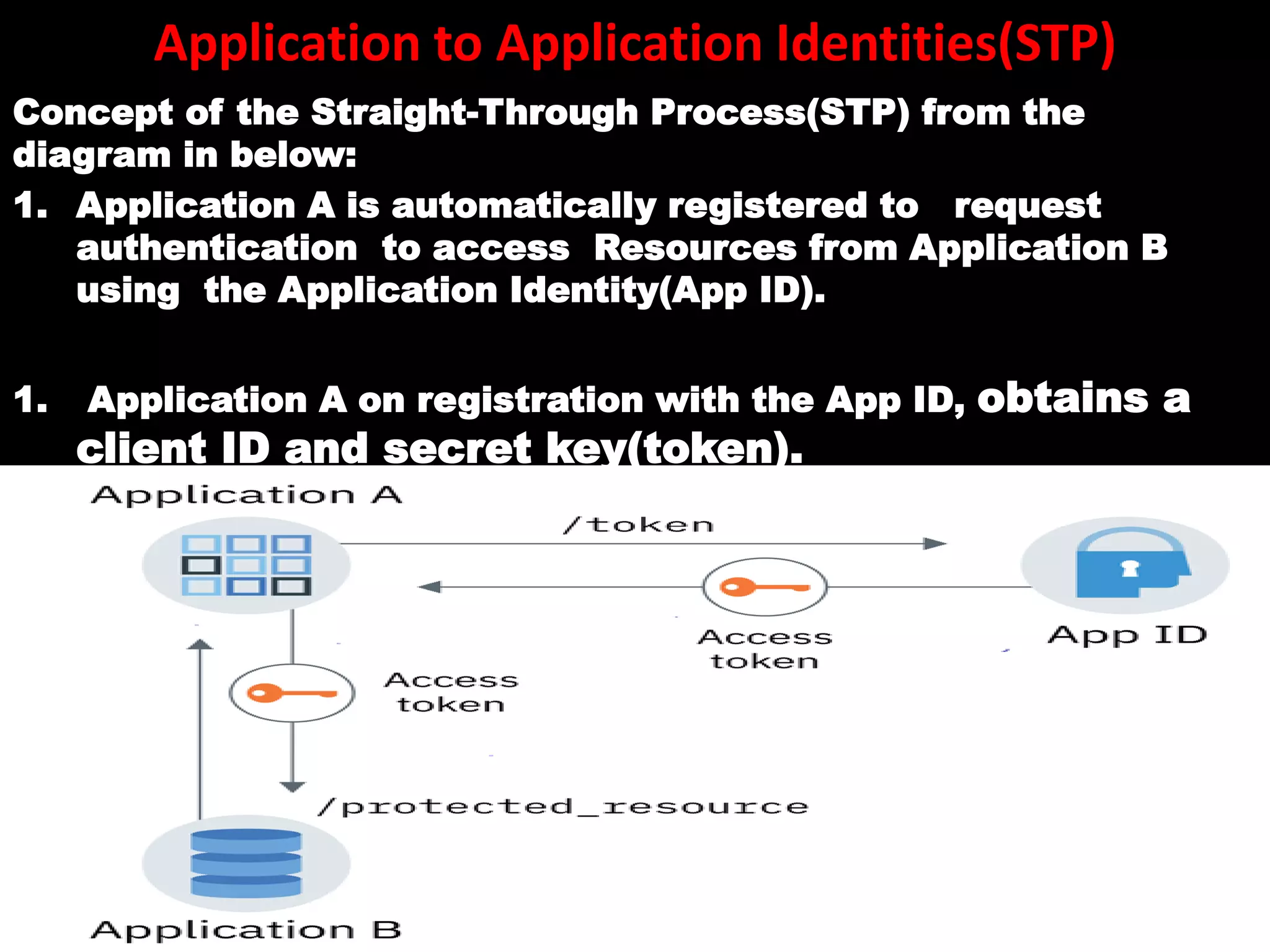
The document discusses identity management and security, emphasizing its importance in mitigating data breaches and enhancing organizational security practices. It highlights the roles of identity verification, authentication, and authorization, along with best practices such as multi-factor authentication (MFA) and zero trust architecture. The document also underlines the need for businesses to adopt resilient identity and access management systems and to ensure strict accountability for identity management roles within organizations.