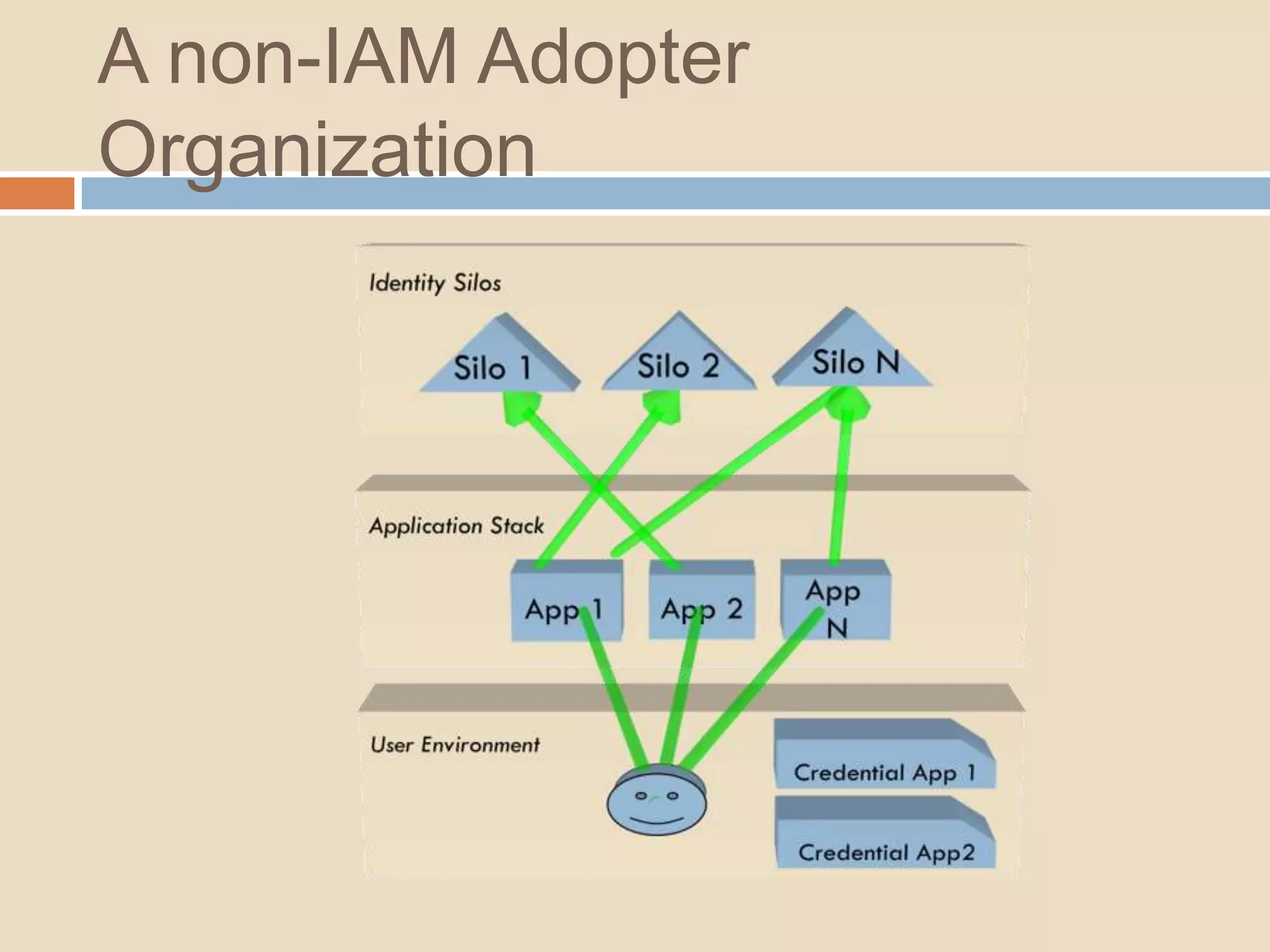
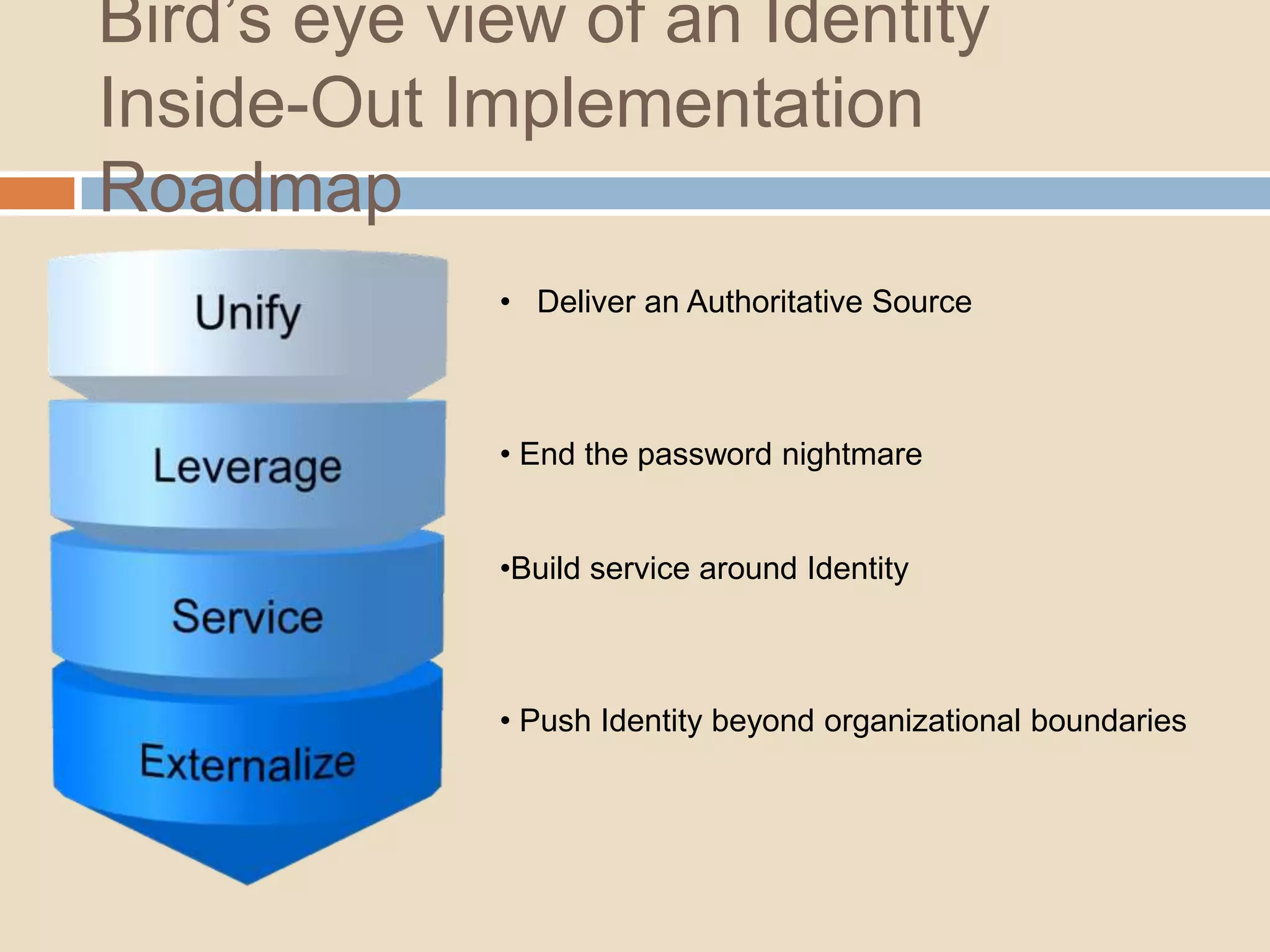
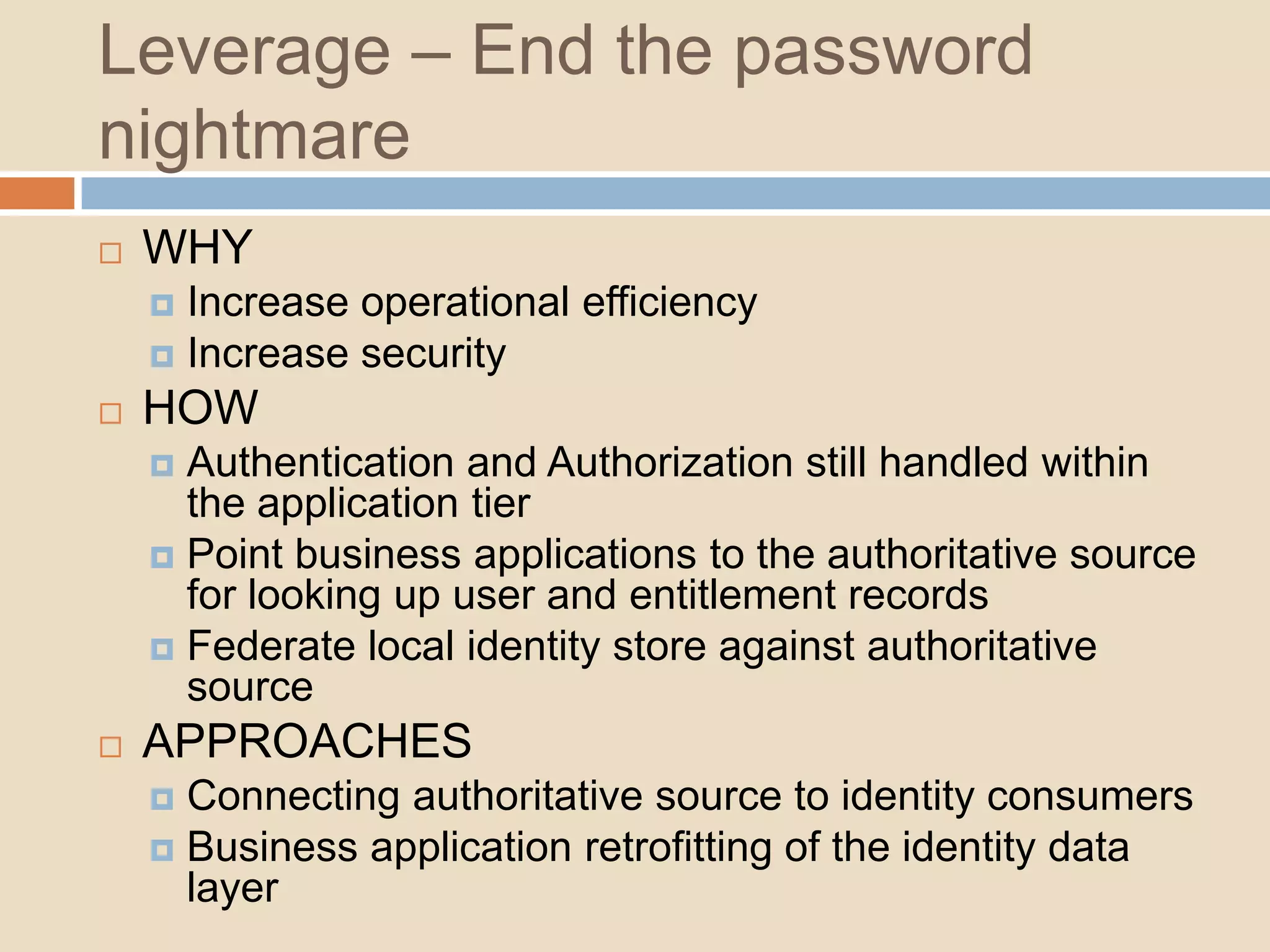
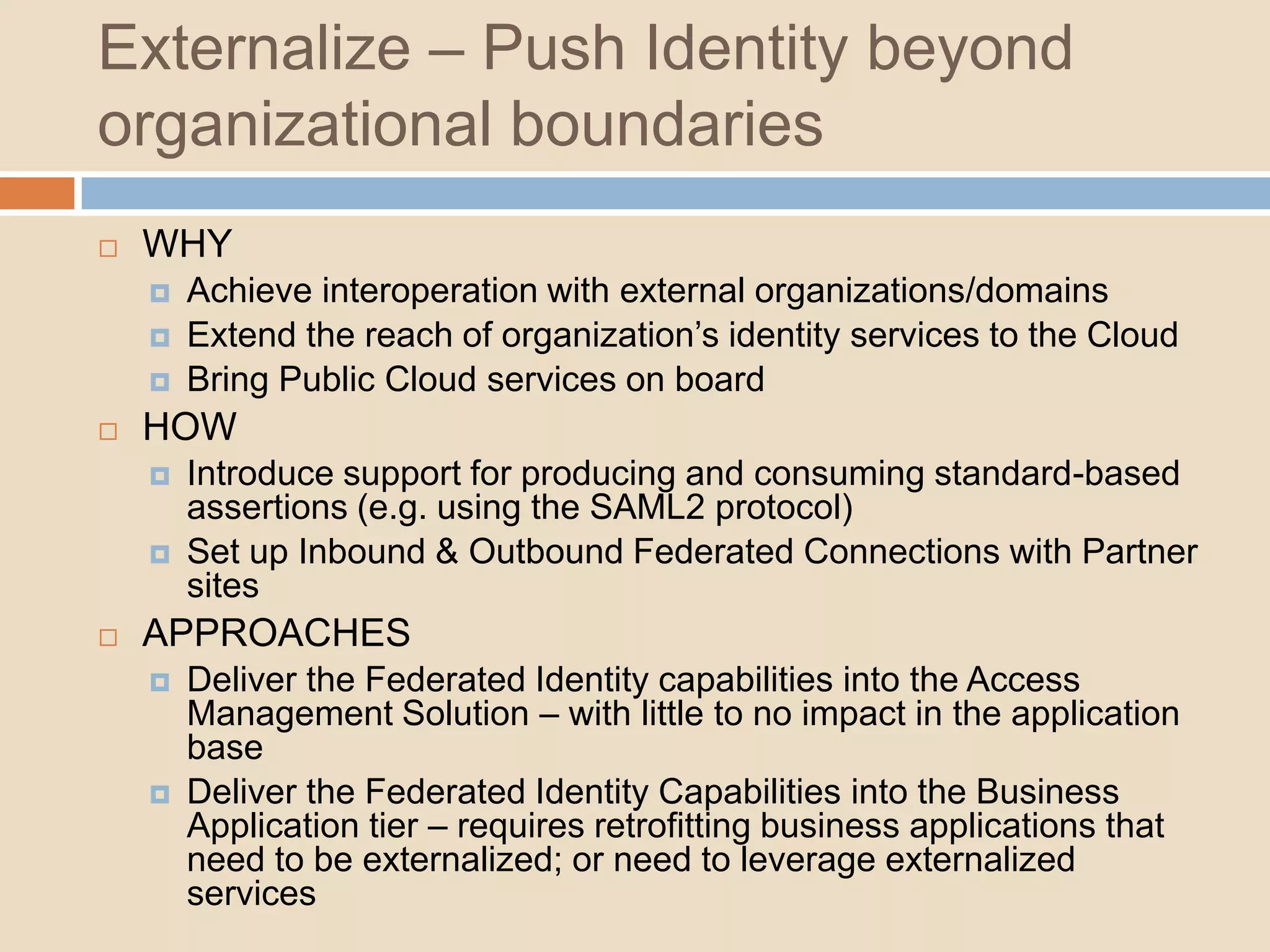
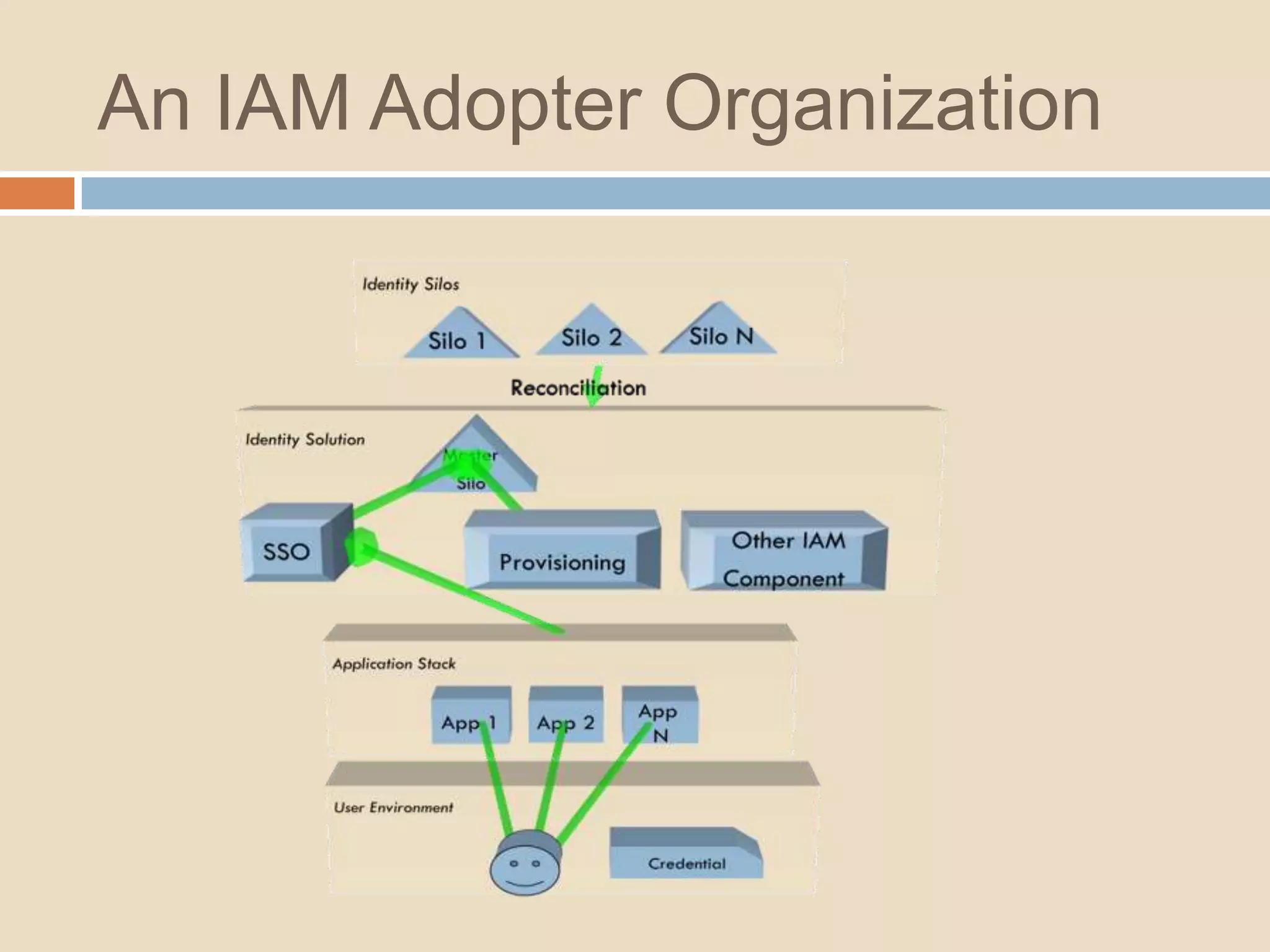
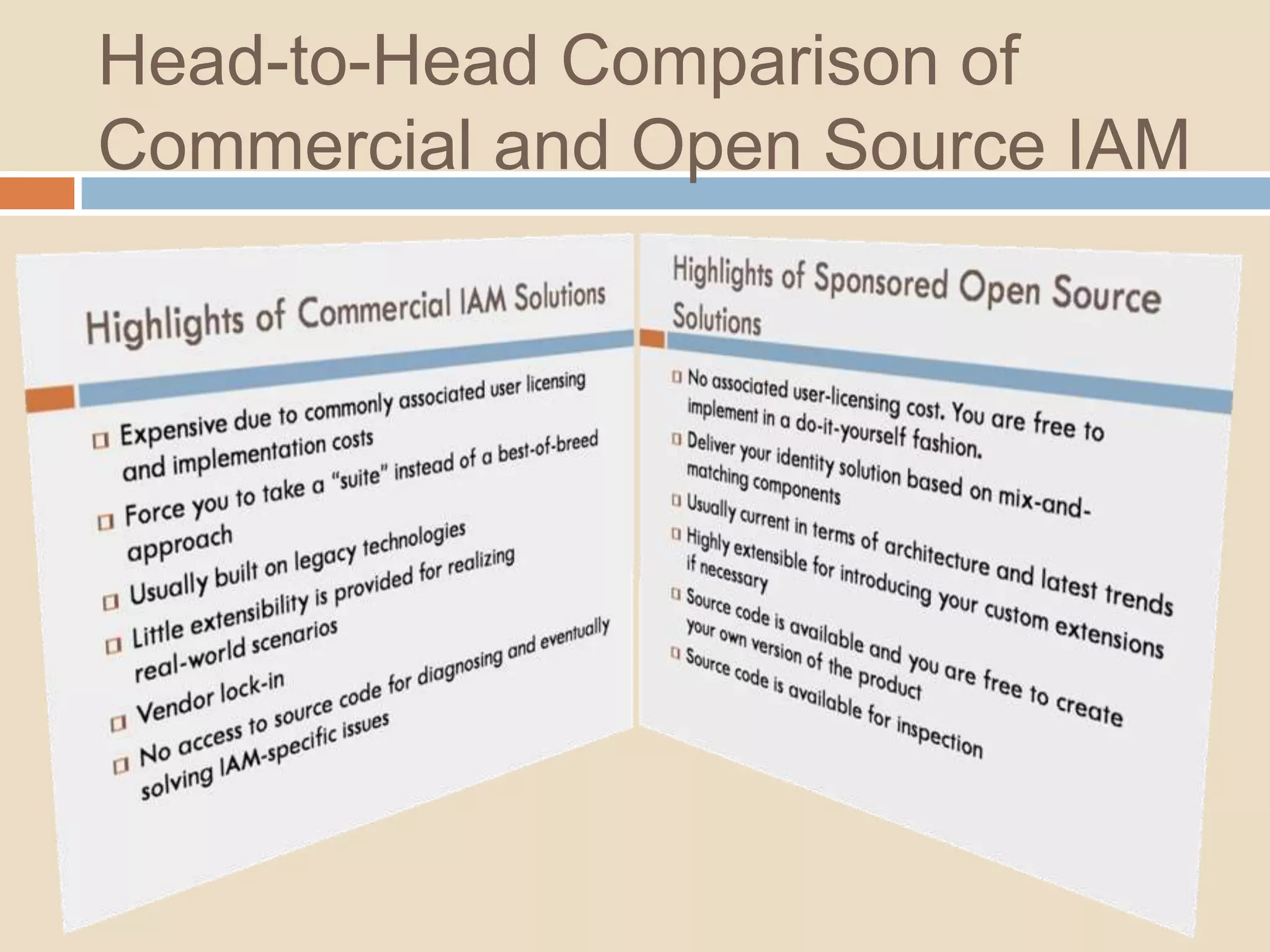
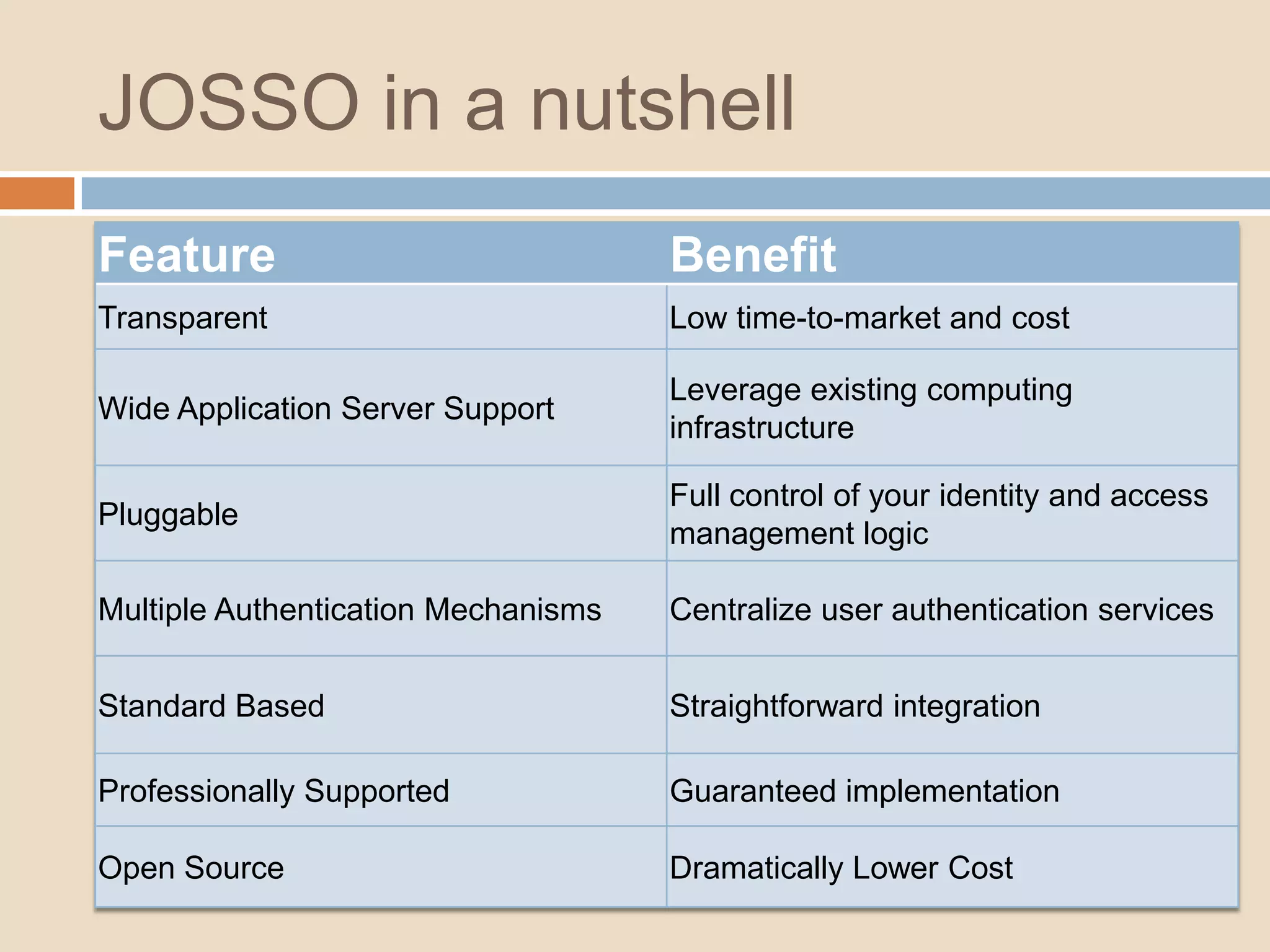
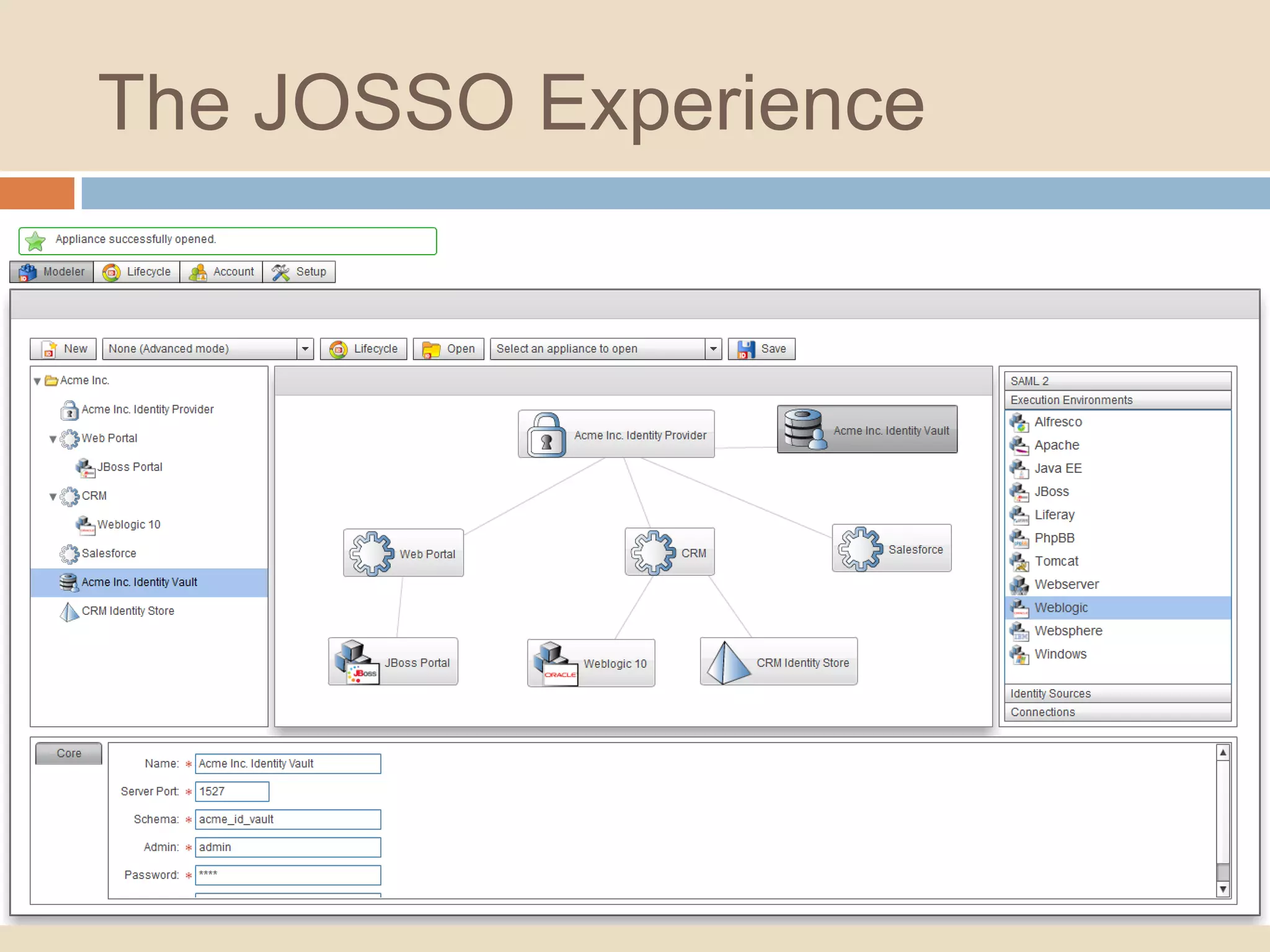
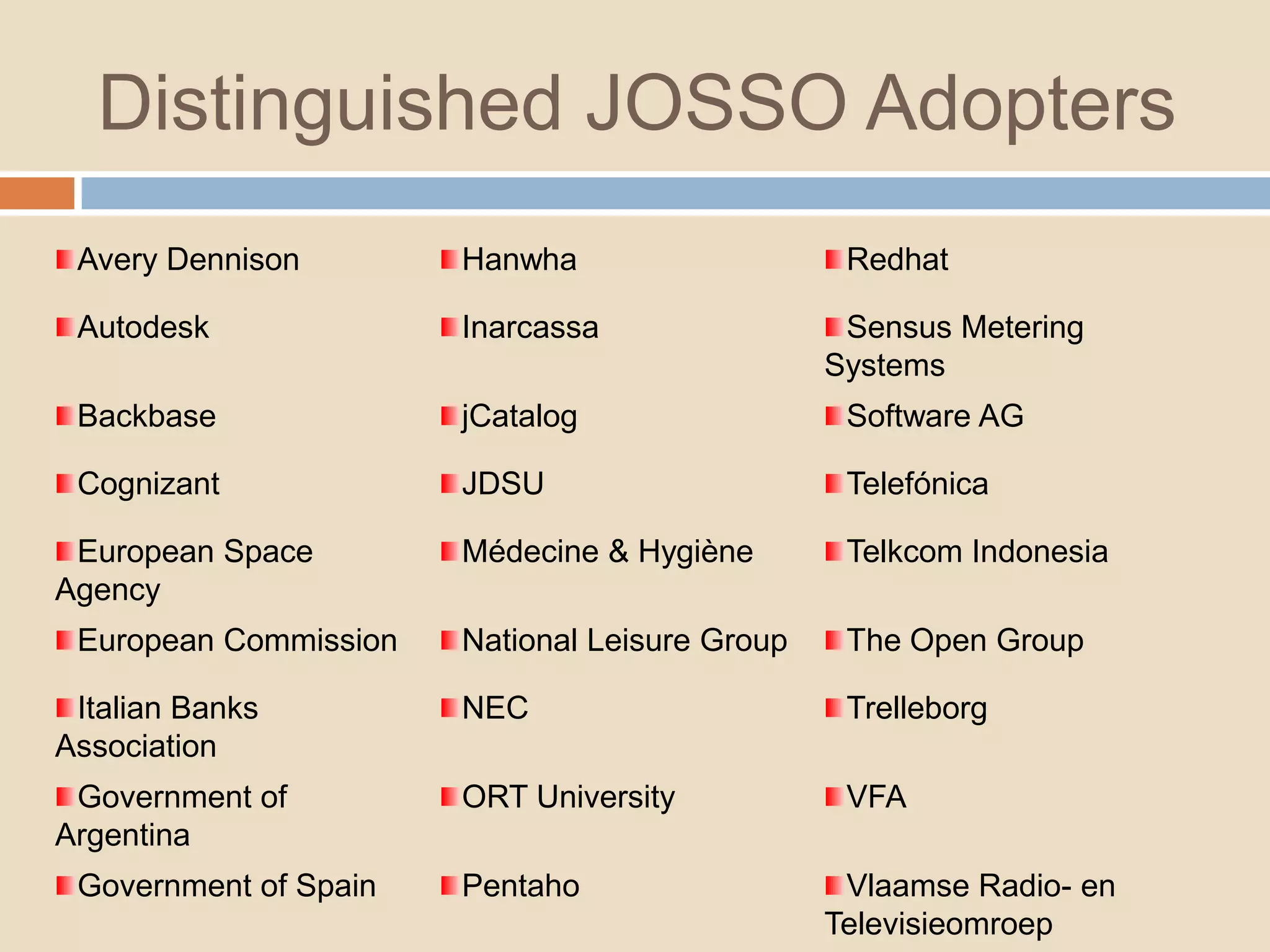
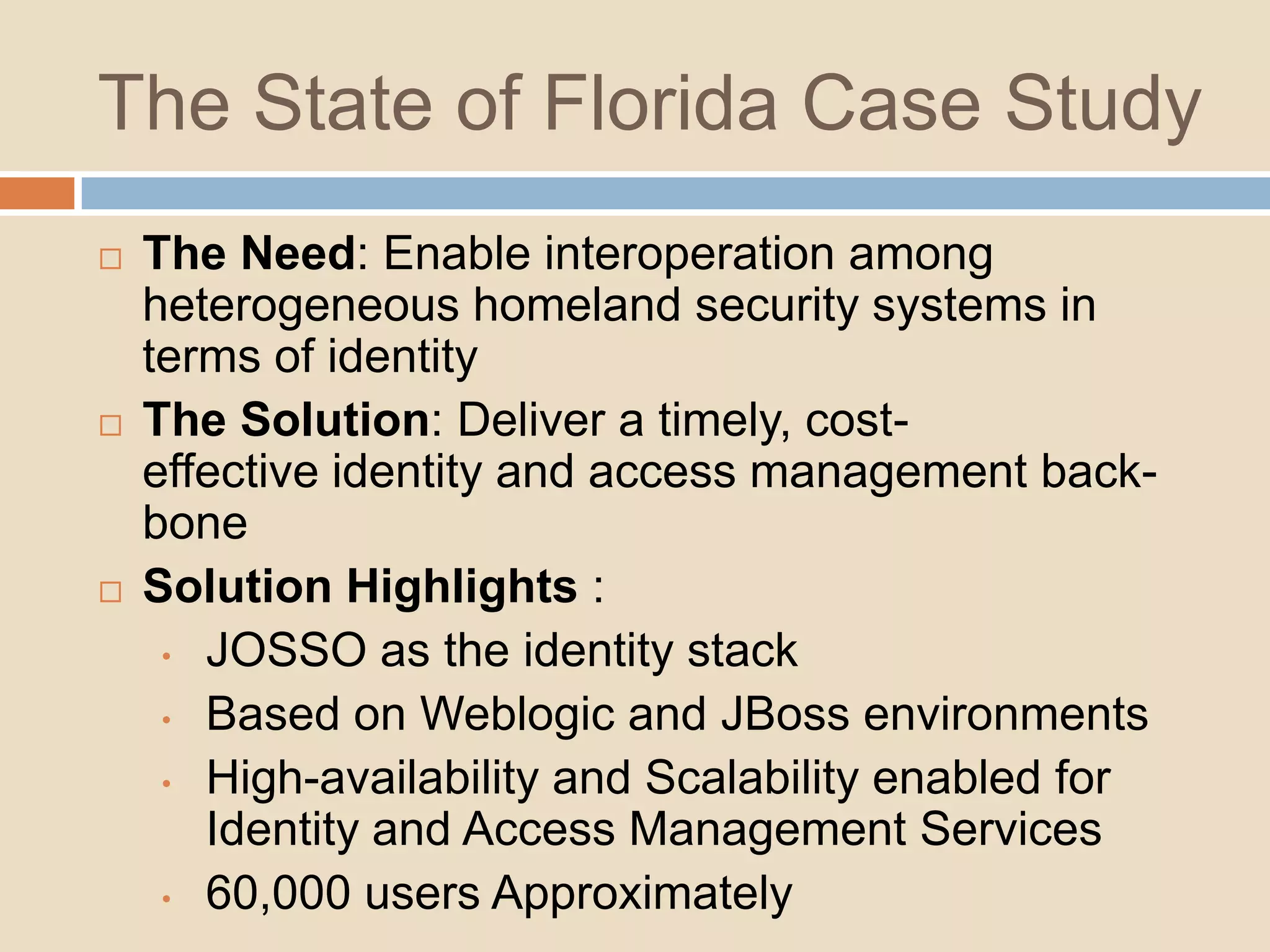
This document introduces a 4-step identity implementation roadmap and compares commercial and open source identity management solutions. It discusses common identity management project mistakes and how to avoid them. It also provides an overview of the open source JOSSO identity management product, highlighting case studies of its use by organizations like the State of Florida and Software AG. The document concludes with contact information for learning more about JOSSO and its certified implementation partner in Brazil.