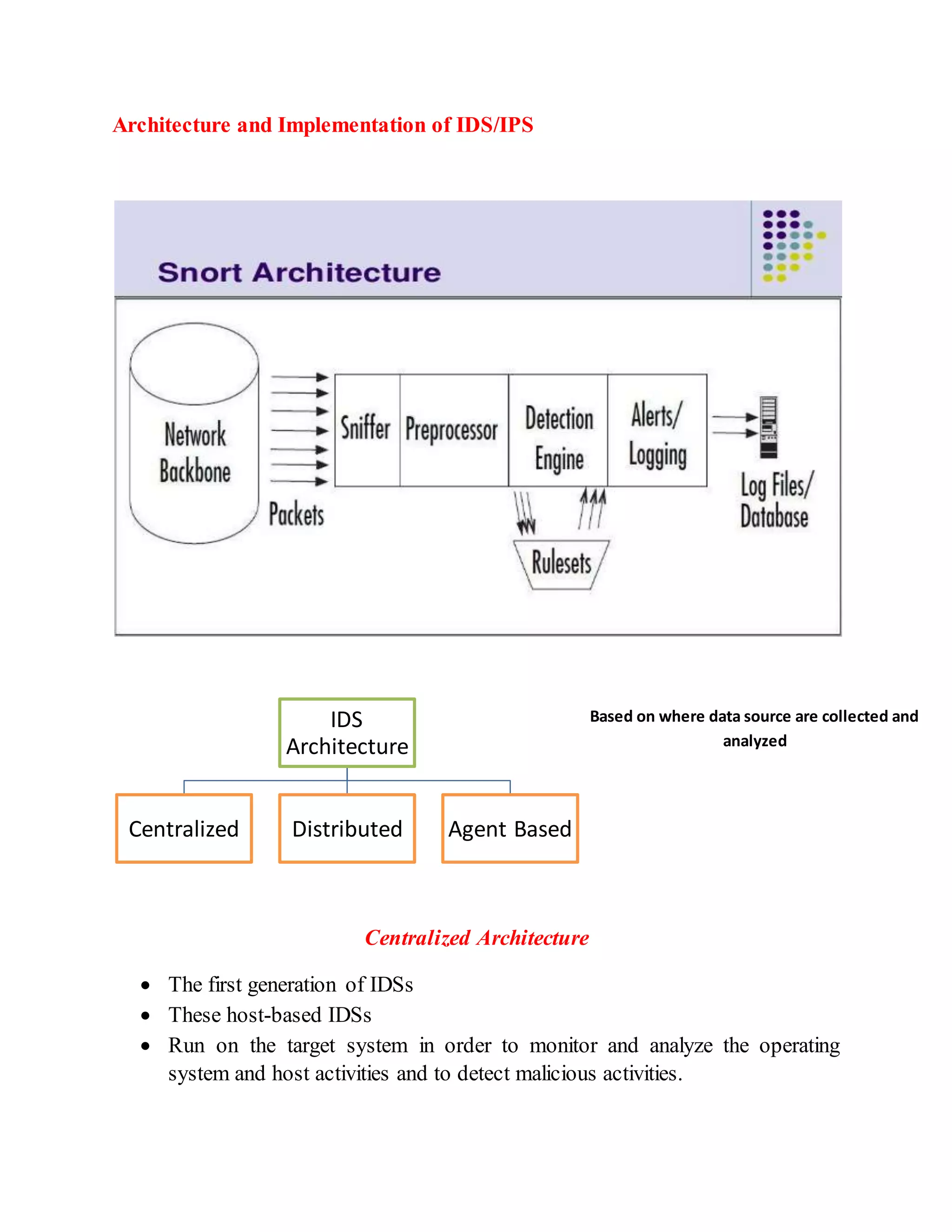
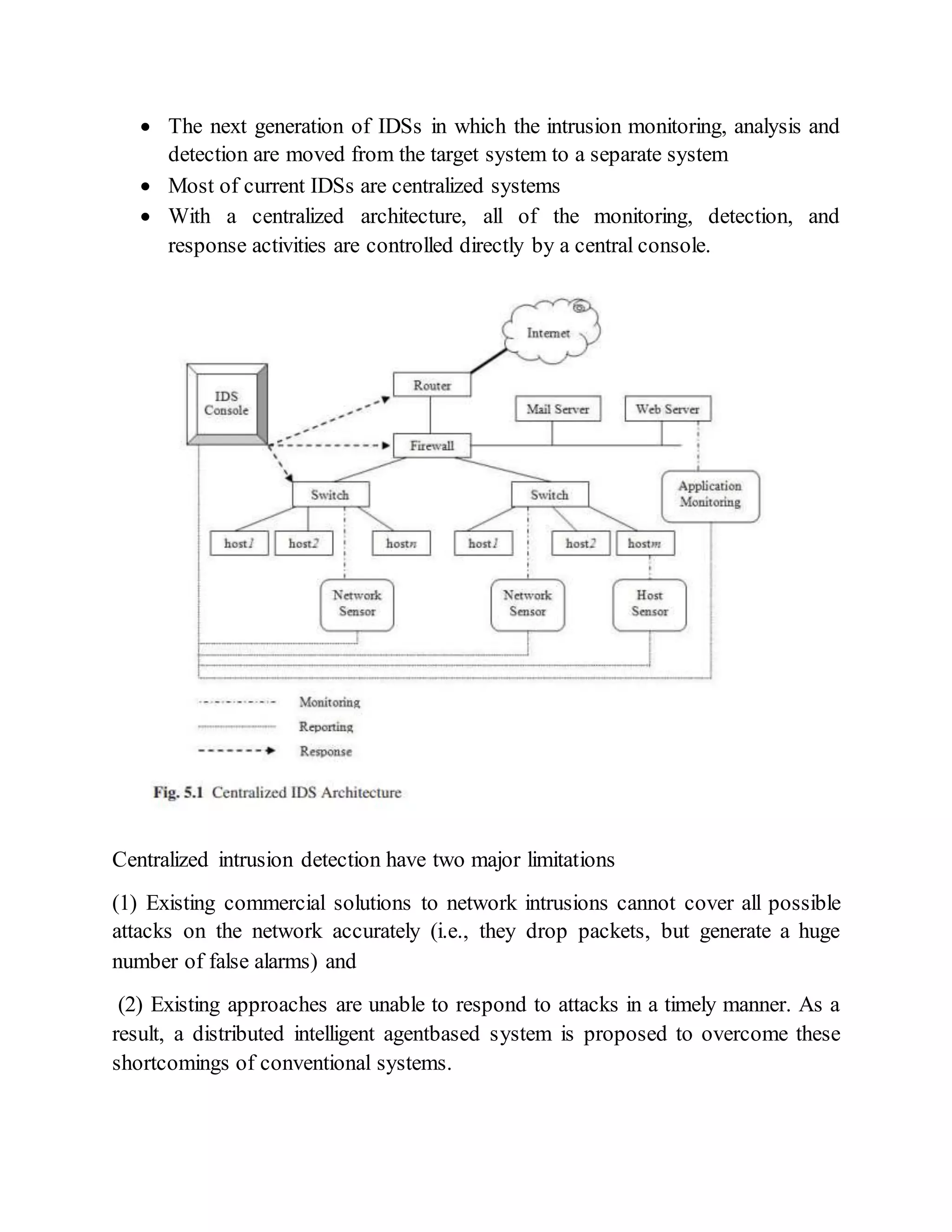
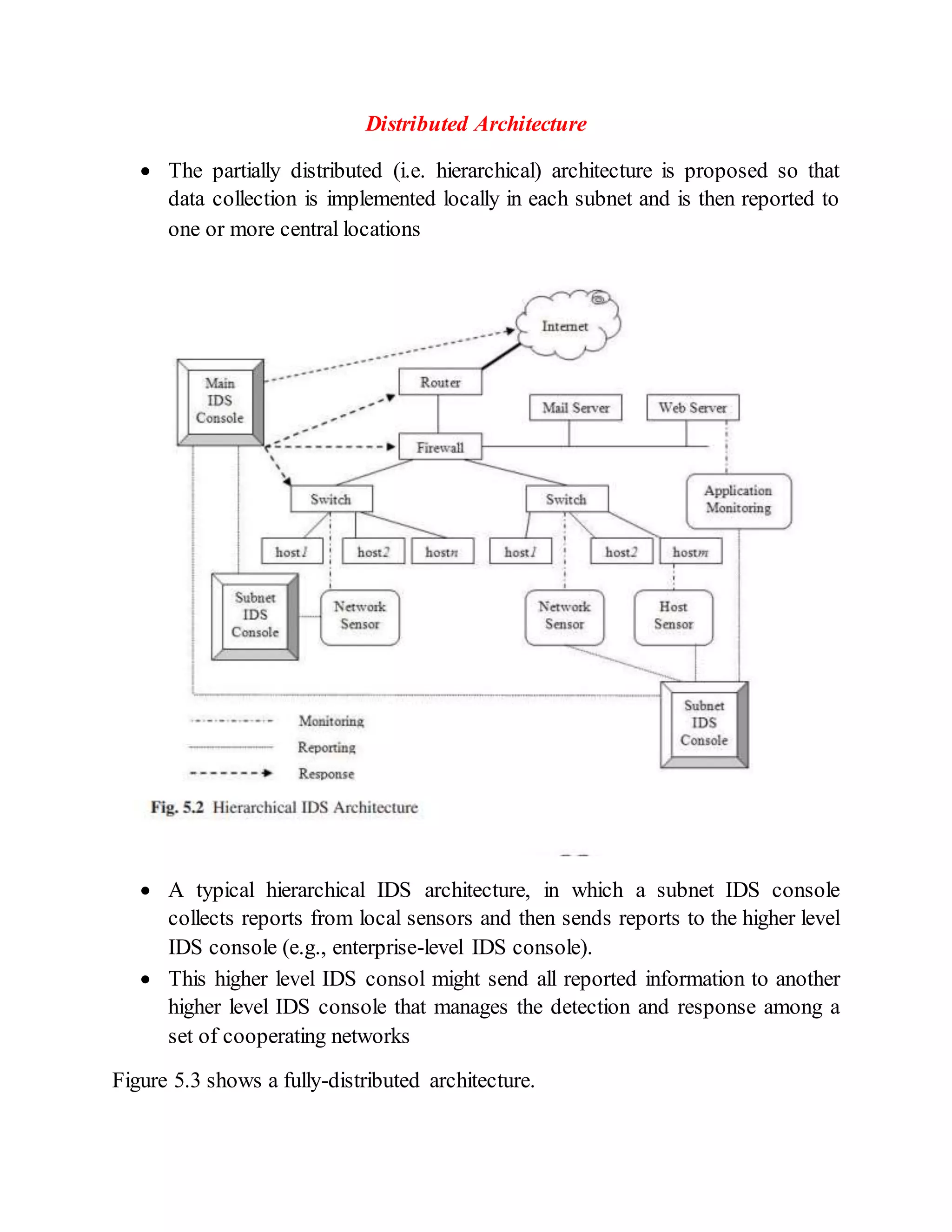
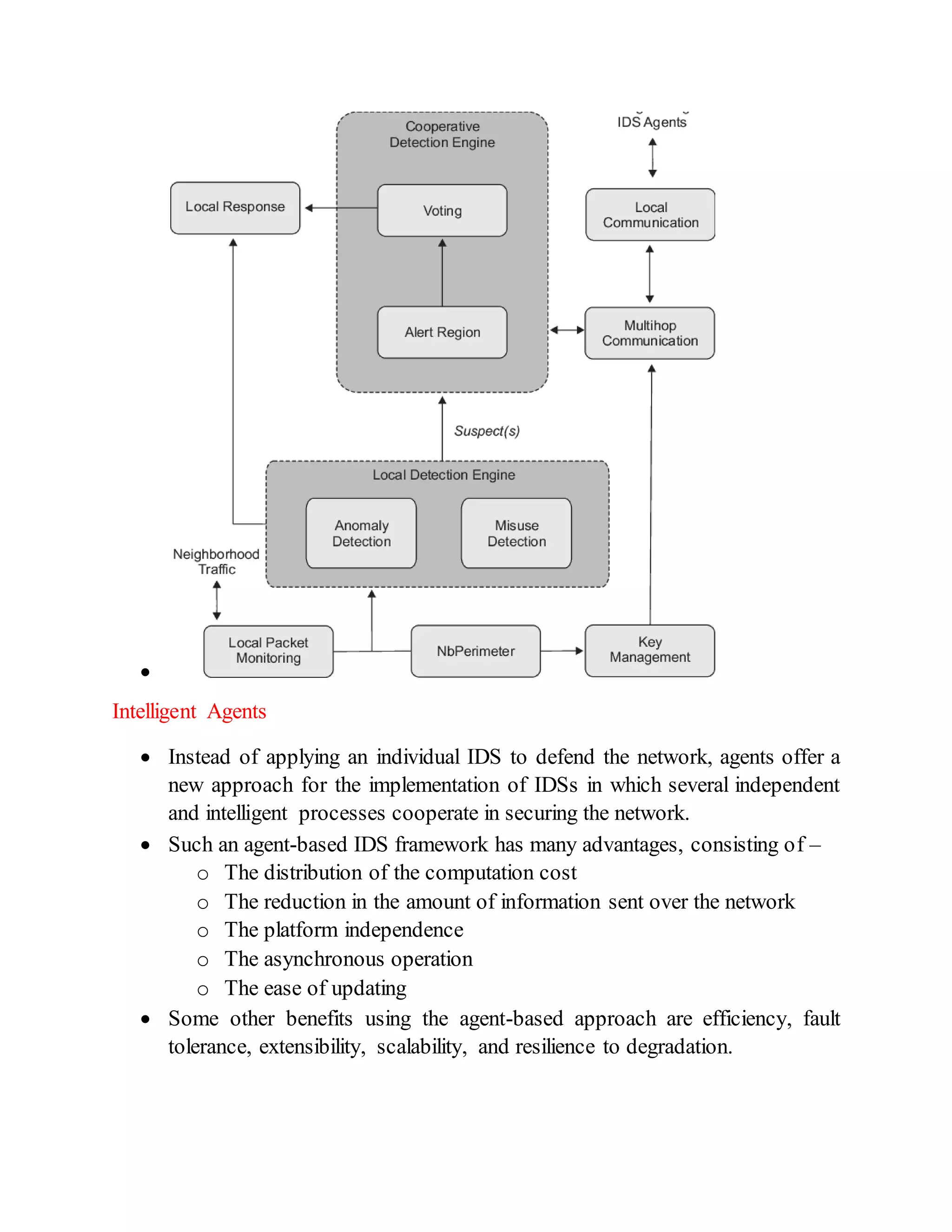
This document discusses different architectures for intrusion detection systems (IDS), including centralized, distributed, and agent-based architectures. Centralized IDS have limitations around coverage of attacks and response time. Distributed architectures improve on this by collecting data locally and reporting to central locations. Agent-based IDS distribute the computation cost by using independent, intelligent agents that cooperate to secure the network. Two examples of agent-based IDS are described: Autonomous Agents for Intrusion Detection (AAFID) and Multi-Agent System-based Network Security Management Architecture (MANSMA).