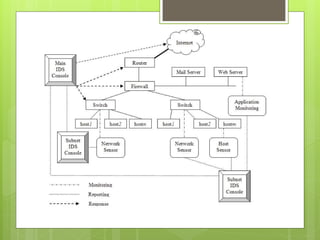
The document discusses various architectures of Intrusion Detection Systems (IDS), categorizing them into centralized, distributed, and agent-based systems. It outlines the components, advantages, and disadvantages of different IDS approaches, such as agent-based systems and multi-agent architectures like AAFID and Hummingbird. The text emphasizes the use of intelligent and mobile agents for efficient intrusion detection while addressing challenges like overhead and security vulnerabilities associated with mobile agents.