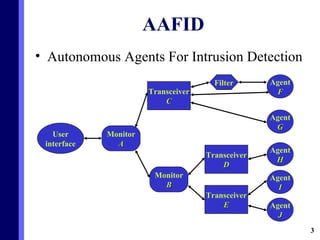
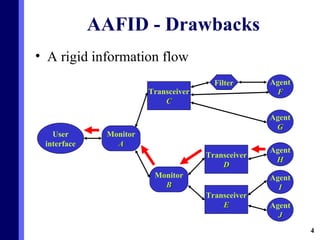
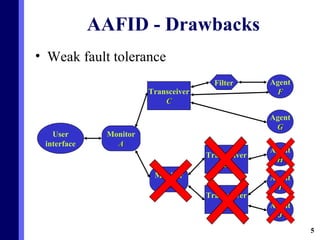
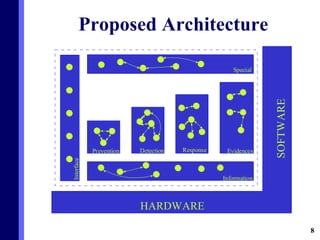
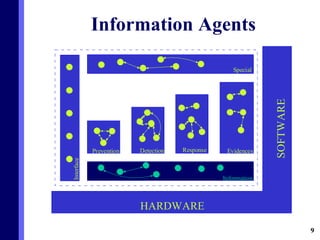
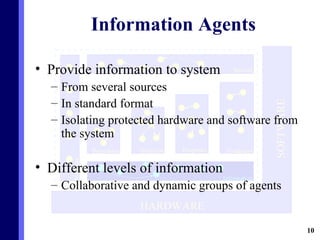
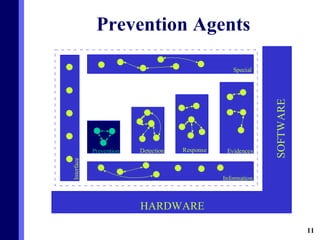
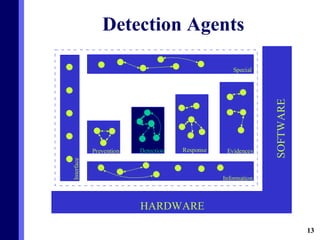
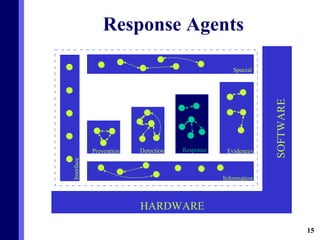
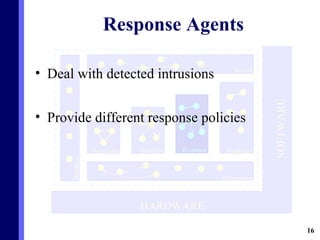
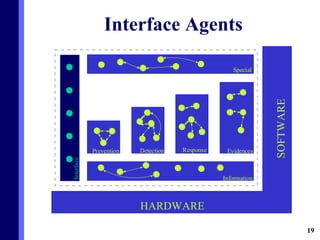
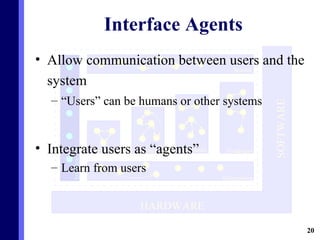
The document proposes a new multi-agent architecture for intrusion detection that improves upon previous rigid systems. It describes seven classes of agents - information, prevention, detection, response, evidence-search, interface, and special agents - that would dynamically cooperate using both domain and social knowledge to detect intrusions. The architecture aims to provide a more flexible and fault-tolerant system compared to earlier work.