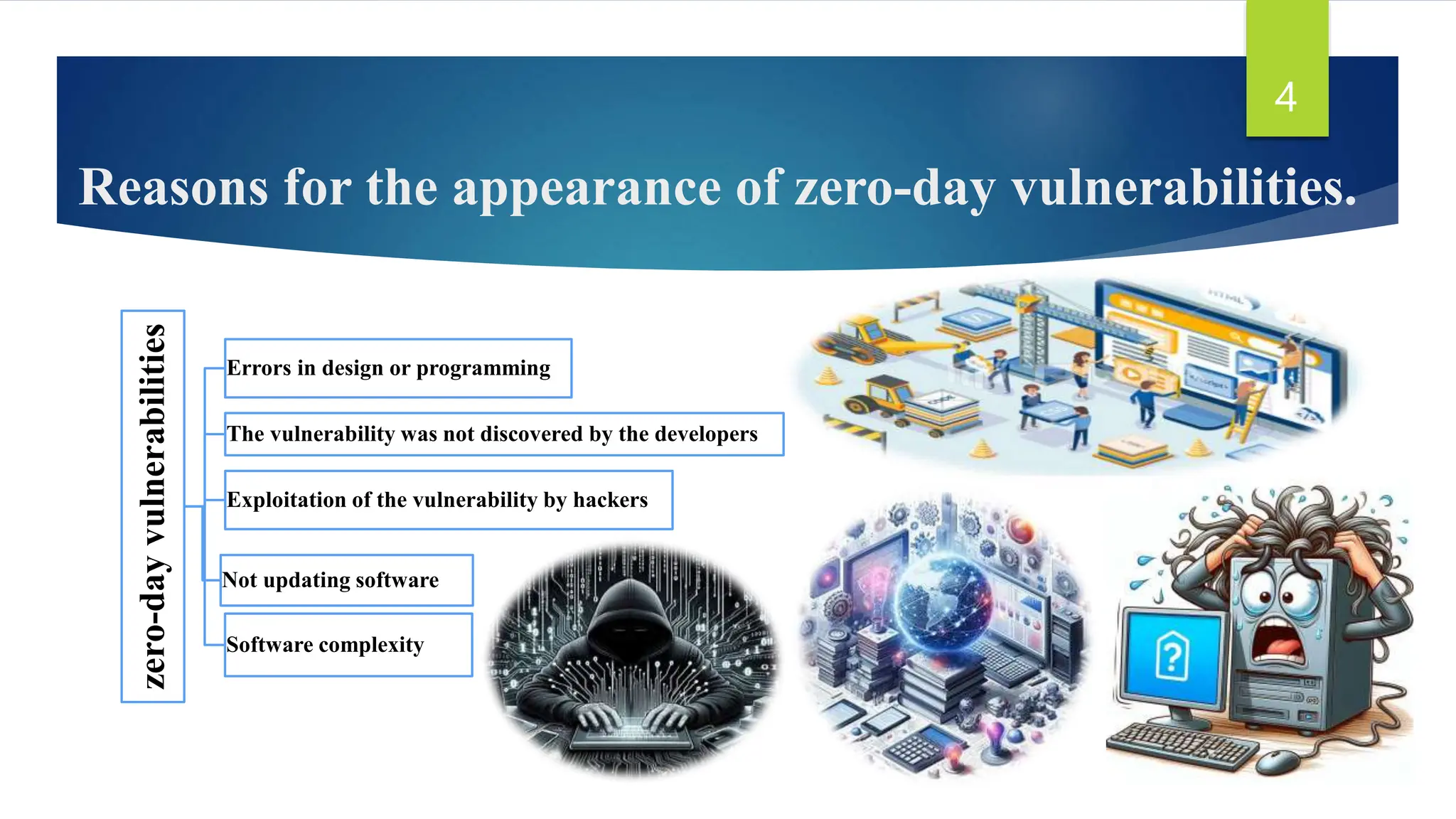
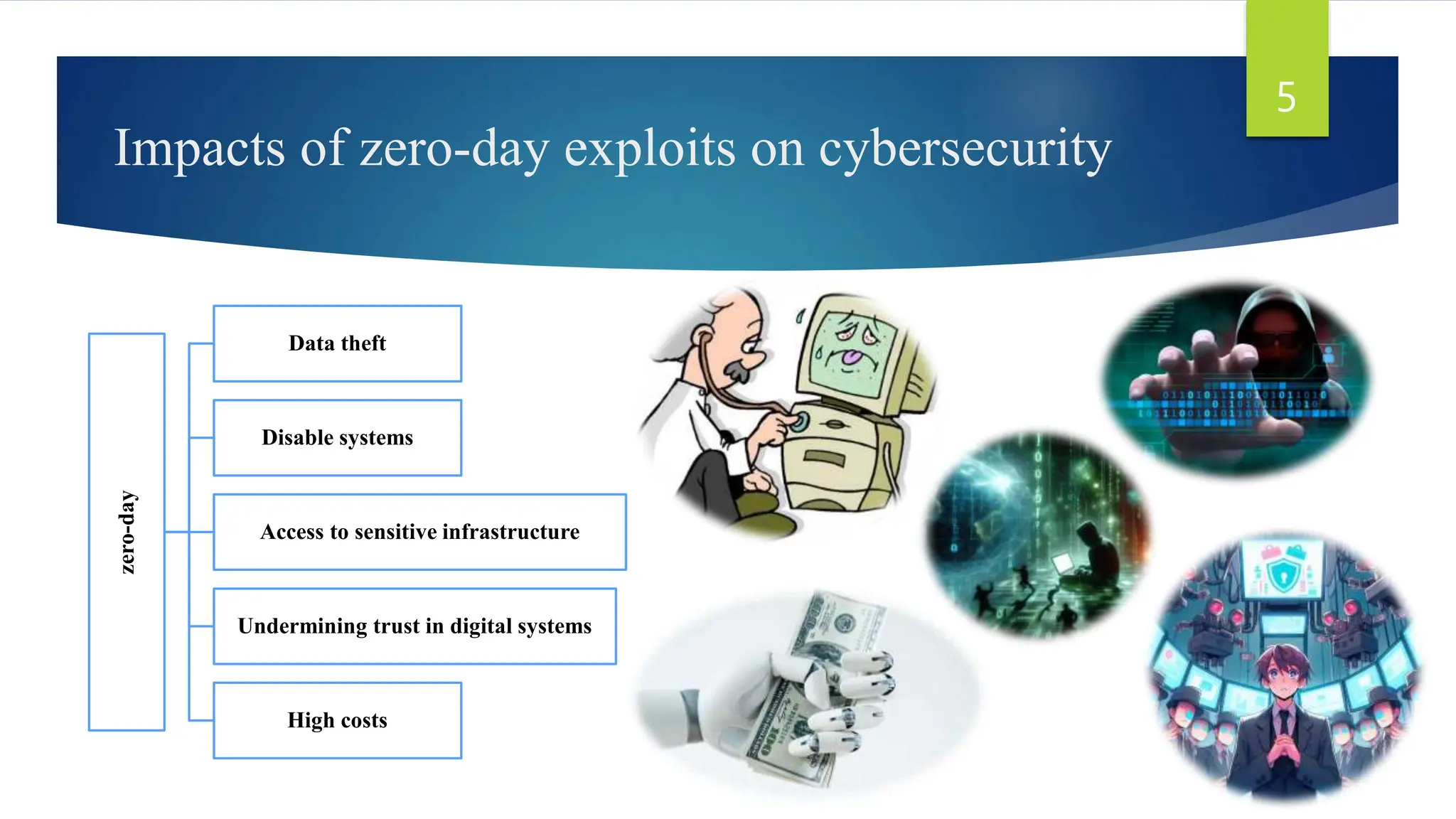
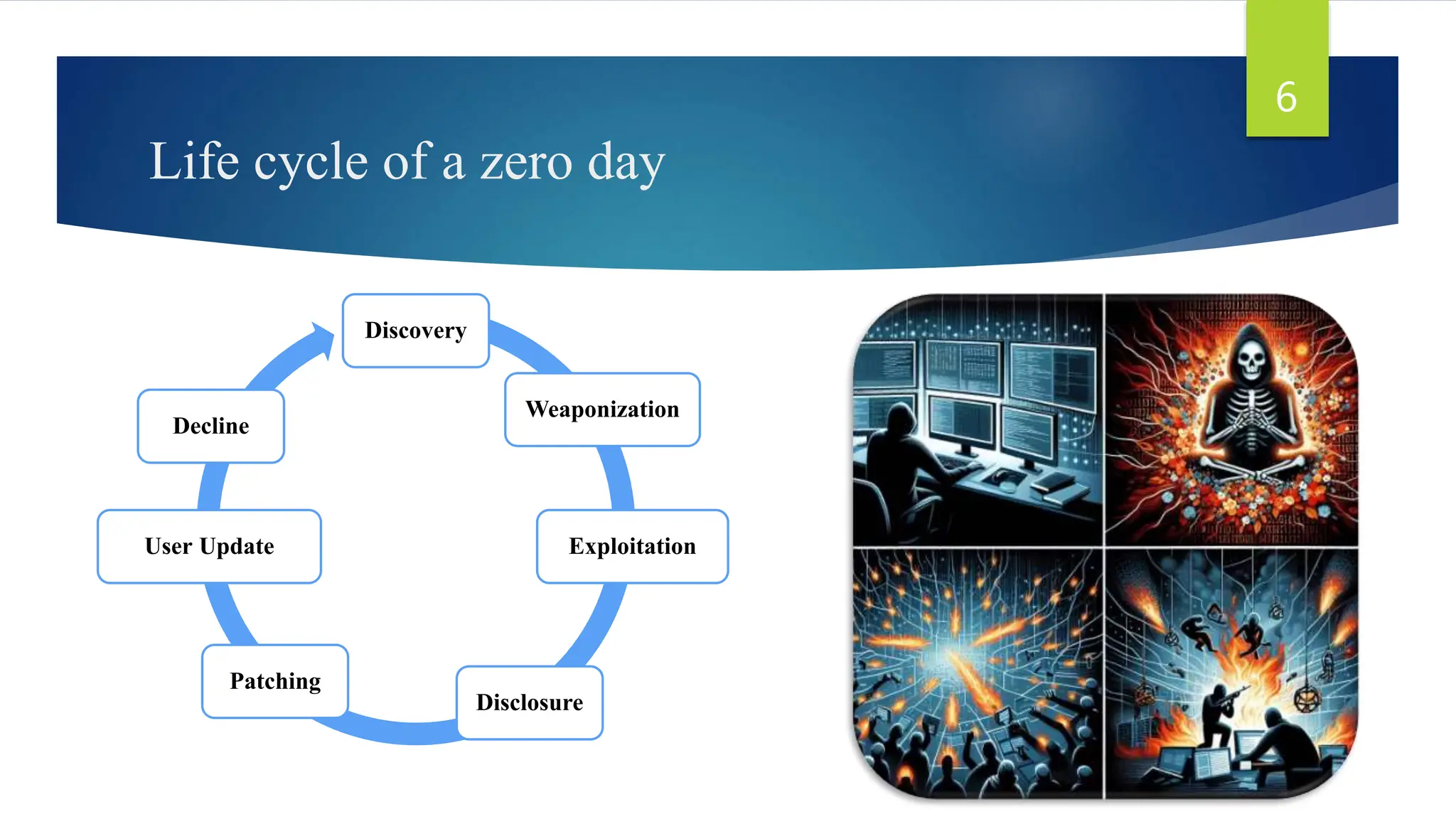
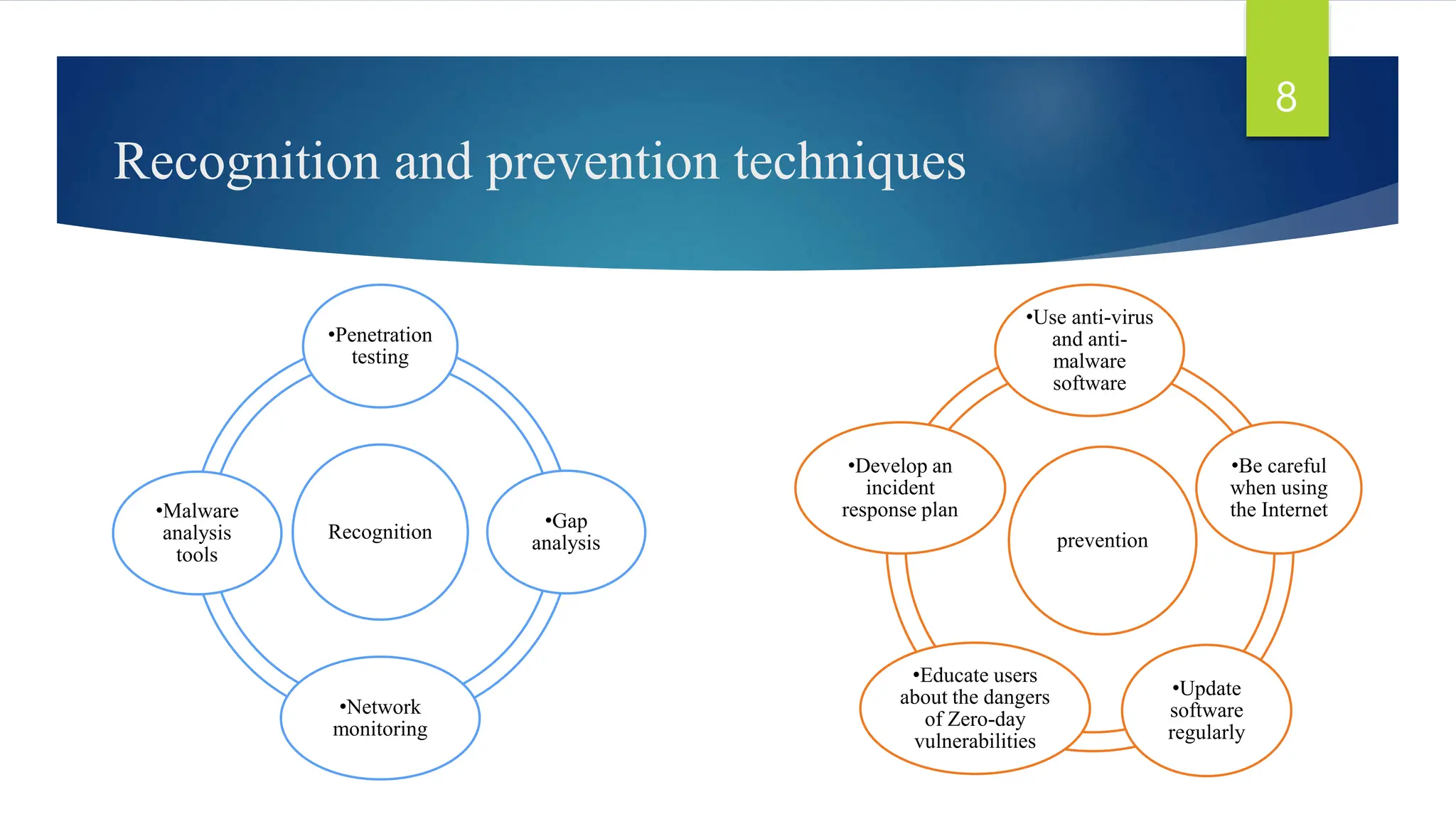
This document discusses zero-day vulnerabilities, which are unpatched security flaws that can be exploited by attackers before developers become aware of them. It outlines the reasons these vulnerabilities appear, their impacts on cybersecurity, examples of notable attacks, and techniques for recognition and prevention. The conclusion highlights the importance of understanding zero-day vulnerabilities for enhancing data security and encourages further research and awareness.