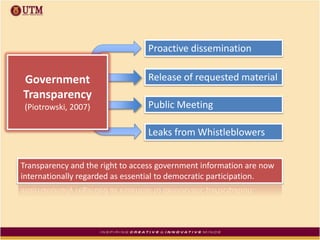
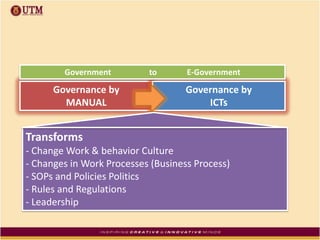
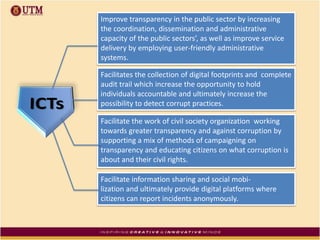
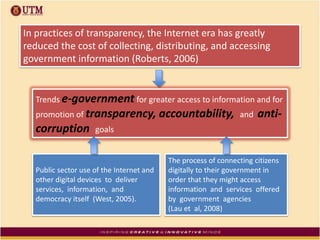
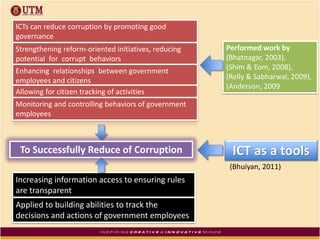
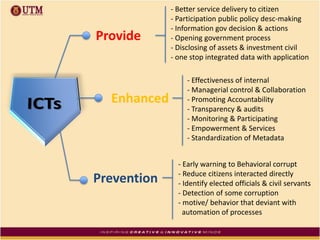
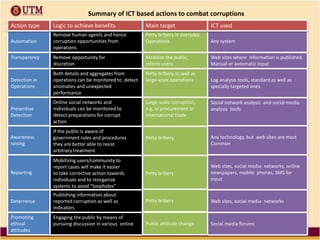
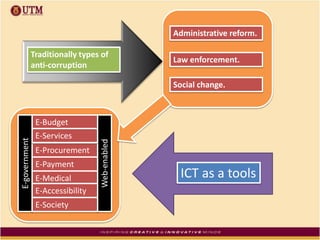
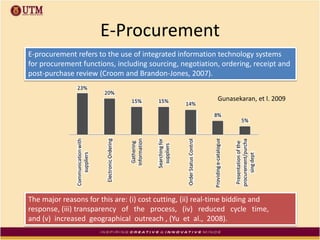
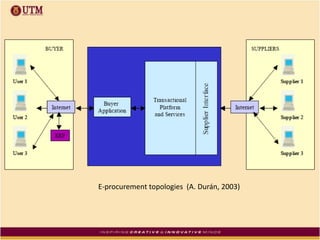
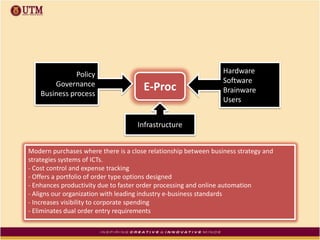
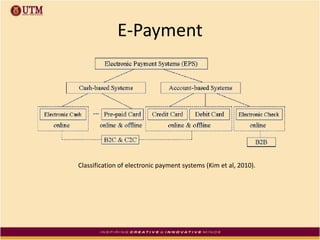
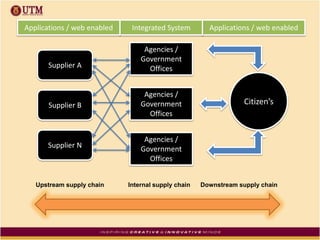
This document discusses how ICT can be used to fight corruption in government. It provides examples of e-government systems and initiatives that several countries have implemented to increase transparency and reduce opportunities for corruption. These include putting rural property records online in India, restructuring the tax system in Pakistan to reduce direct citizen-official contact, and establishing e-procurement systems to prevent price fixing and allow public accountability. The document also outlines some of the challenges of implementing e-government systems, such as overcoming social, political, and infrastructure constraints. Overall, the document advocates for the use of ICT tools like e-government, e-procurement, and e-payment to enhance transparency, accountability, and anti-corruption goals in the public