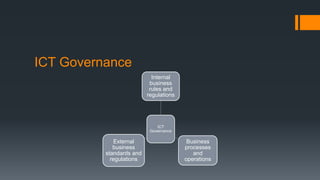
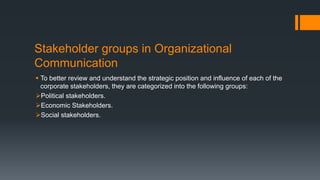
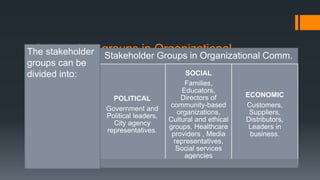
The document discusses ICT governance and the role of compliance officers. It notes that ICT governance involves directing IT resources to align with strategic goals. Compliance officers ensure adherence to policies and monitor for compliance. They promote ethical conduct and help create business value. Effective communication is also important for ICT governance. Compliance officers must understand stakeholders and craft clear messaging to support organizational objectives.