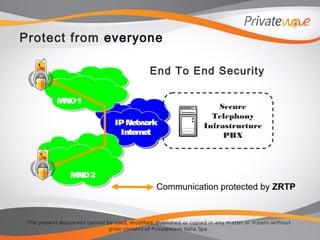
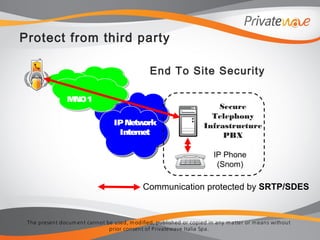
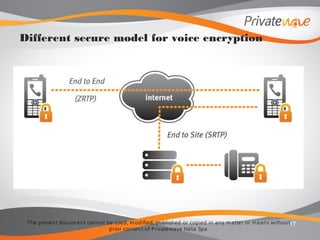
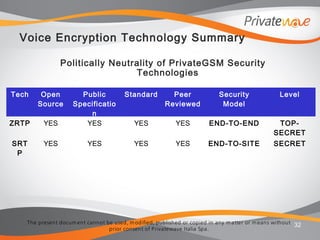
The document discusses PrivateWave's mobile voice encryption solutions. It describes PrivateGSM software that provides encryption for phone calls on smartphones using VoIP over mobile data. PrivateGSM uses the ZRTP standard to provide end-to-end encryption with human authentication and key agreement. It can also use SRTP and provide end-to-site encryption when integrated with telephony infrastructure. The document emphasizes that PrivateWave's solutions use open standards like ZRTP and SRTP to ensure the technologies are politically neutral and not subject to backdoors.