The document discusses corporate demand for secure voice encryption products. A market research study was conducted through phone surveys with 40 senior managers across industries. Key findings include:
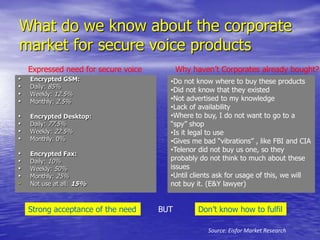
- Corporates are largely unaware of voice encryption products despite expressed concerns about confidential calls being monitored.
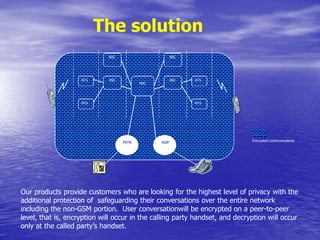
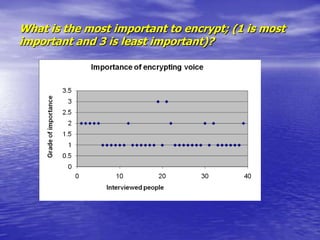
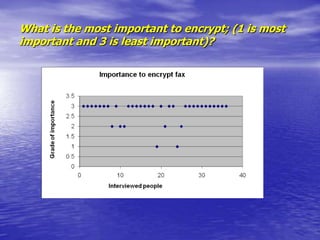
- There is significant demand to encrypt voice, data, and faxes, especially for business calls.
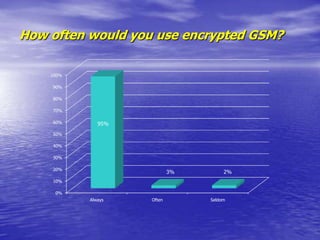
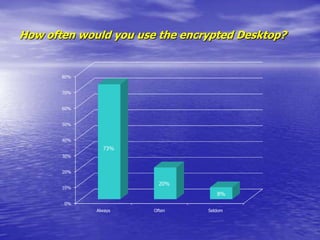
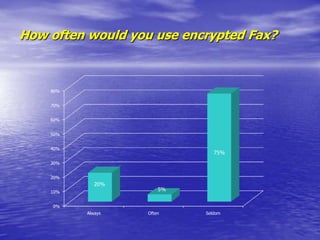
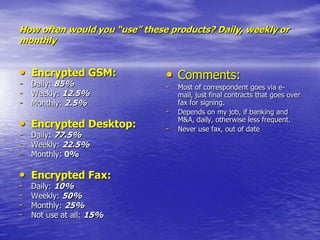
- Encrypted GSM phones and desktop phones would likely be used daily by most respondents. Encrypted faxes would be used less frequently.
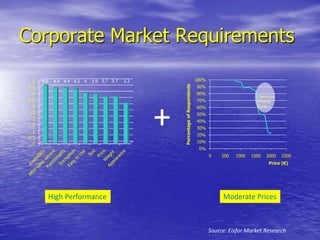
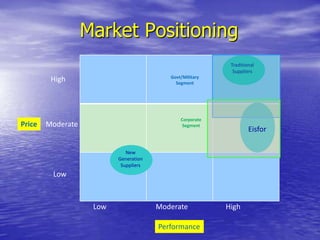
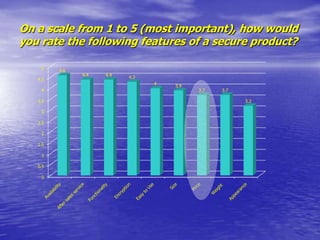
- Ease of use, availability, functionality, and price are important factors that would influence purchase decisions for secure communication products.