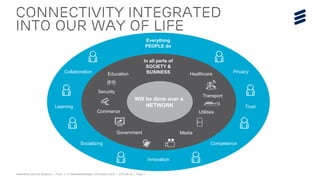
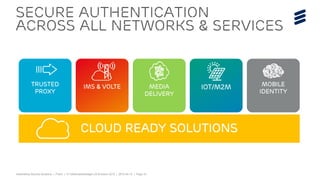
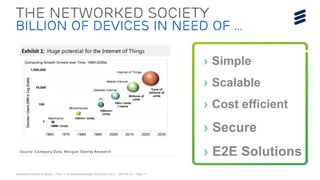
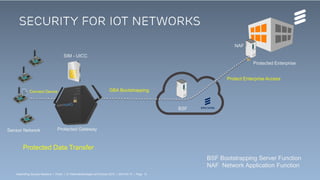
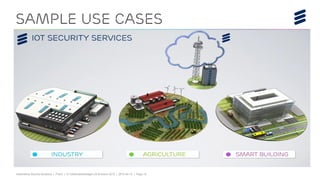
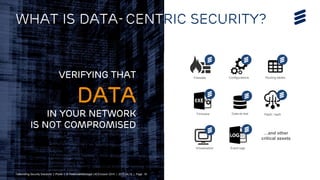
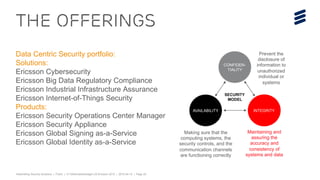
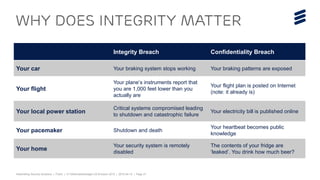
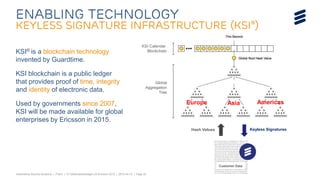
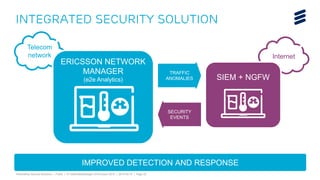
The document summarizes Ericsson's security solutions presentation from April 2015. It discusses the growing connectivity in society and new opportunities and challenges this brings about. Ericsson's approach focuses on securing large networks and ensuring services are always available, security requires minimum user effort, communications are protected, and privacy and data integrity are maintained. Specific solutions discussed include authentication and identity management, network analytics for mobile network security, and using keyless signature infrastructure to verify data integrity across networks.