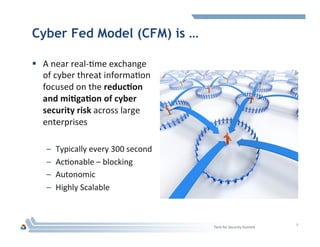
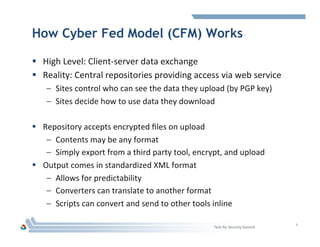
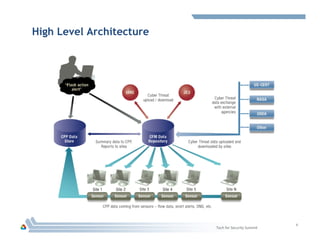
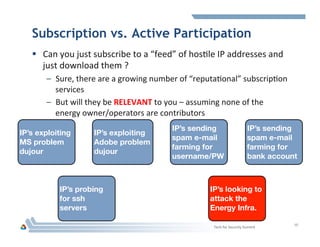
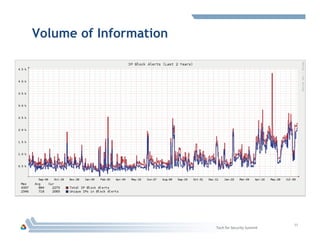
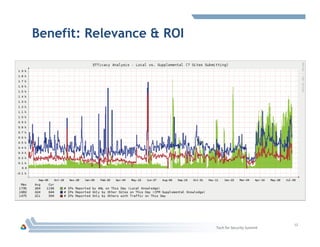
The document discusses DOE's Cyber Fed Model (CFM), which enables near real-time sharing of structured cyber threat information between large enterprises to help reduce cybersecurity risks. CFM uses a client-server model to exchange encrypted threat data in XML format every 5 minutes. It maximizes local detection and global response by allowing enterprises to focus on threats affecting their infrastructure while benefiting from others' threat information. The document argues collaboration will be key to future cyber defense and a CFM pilot could assess its ability to enhance collective defense between the energy sector and DOE laboratories.