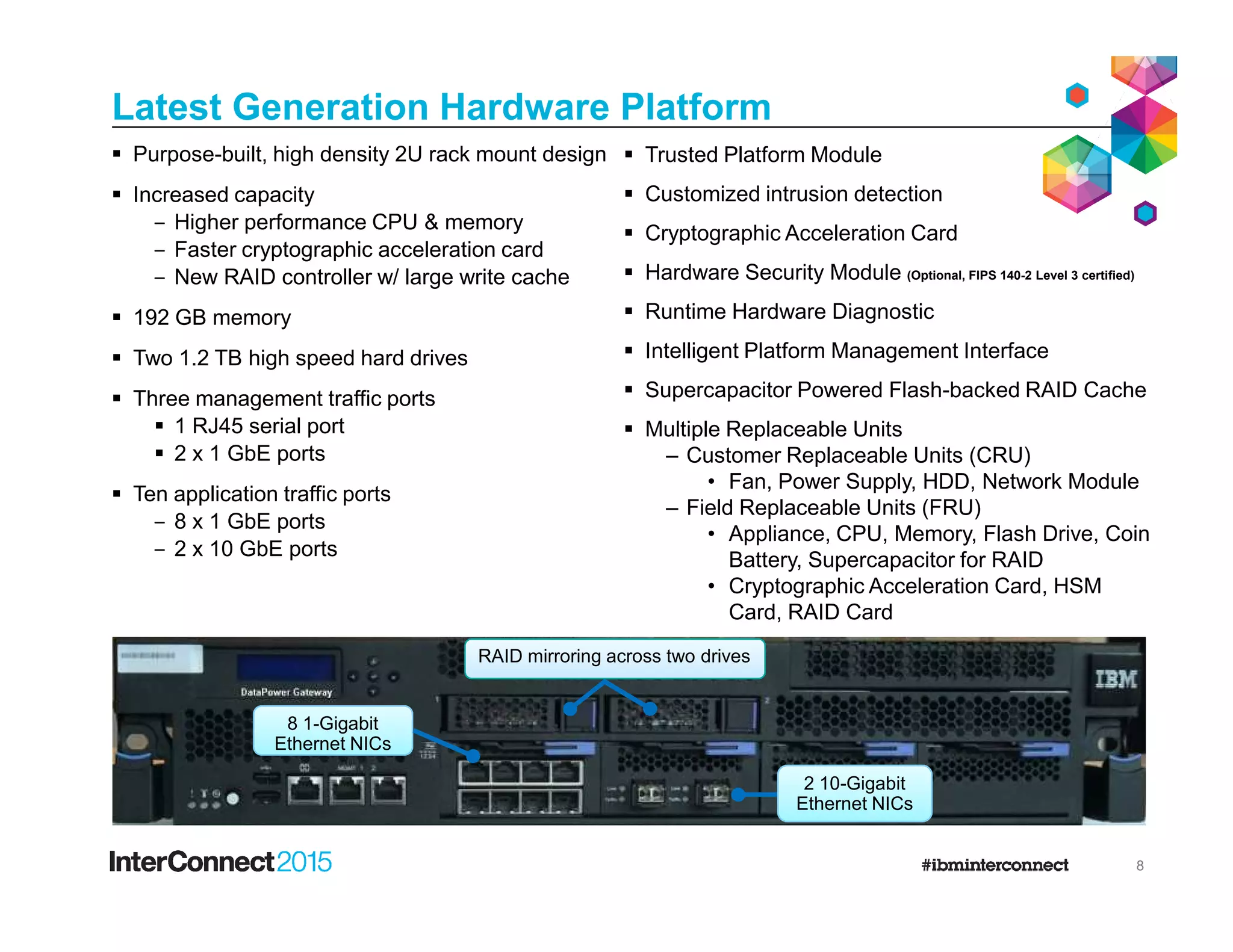
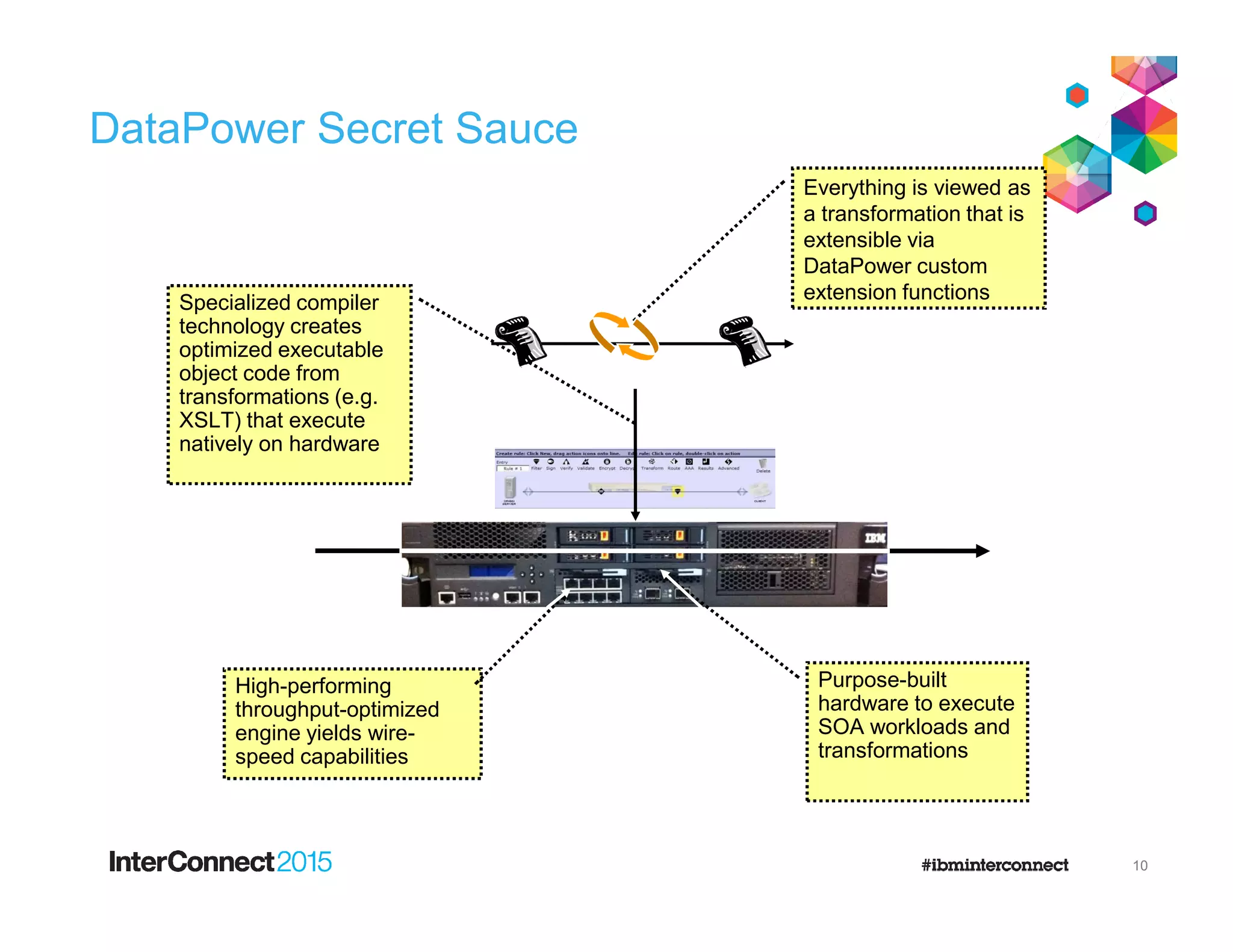
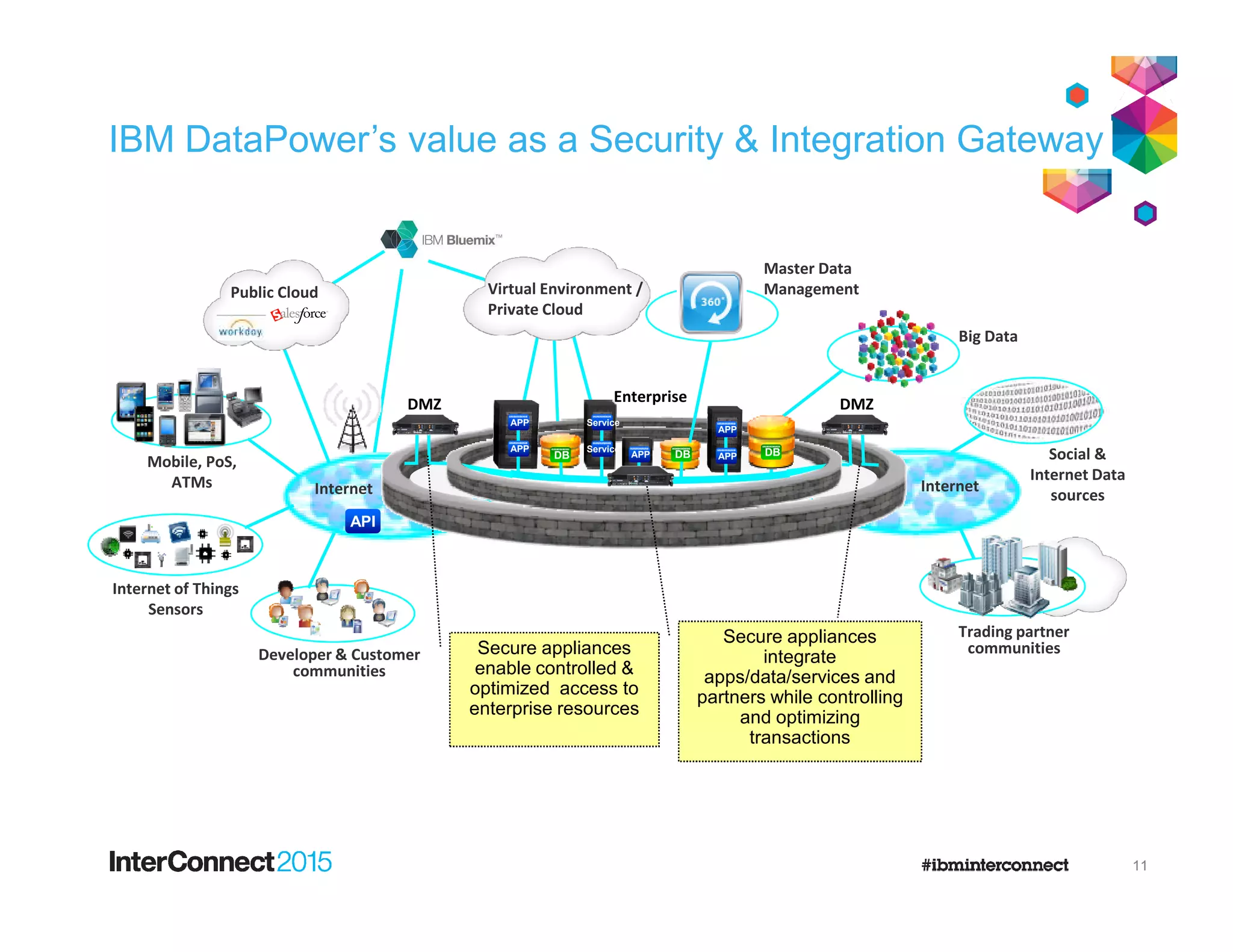
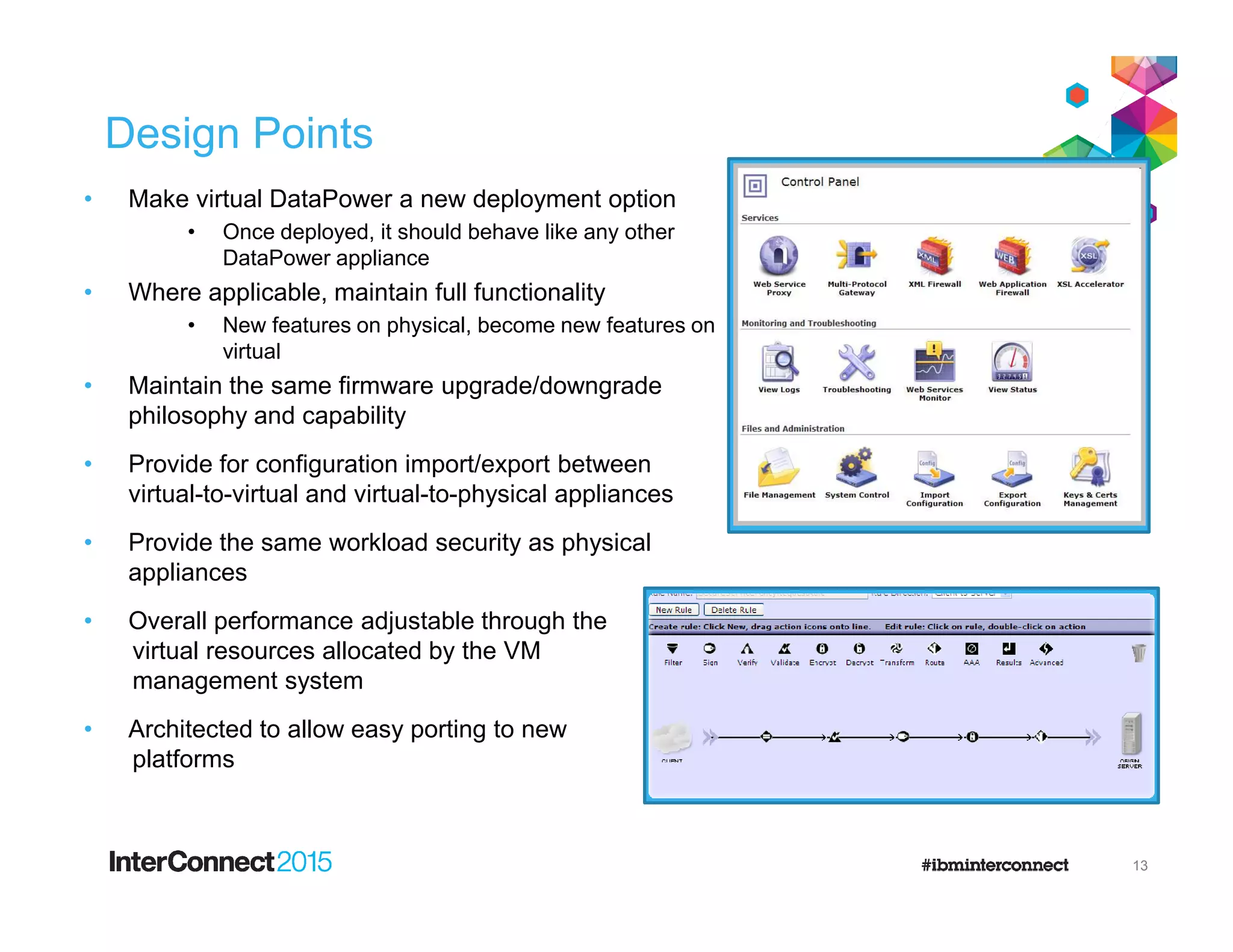
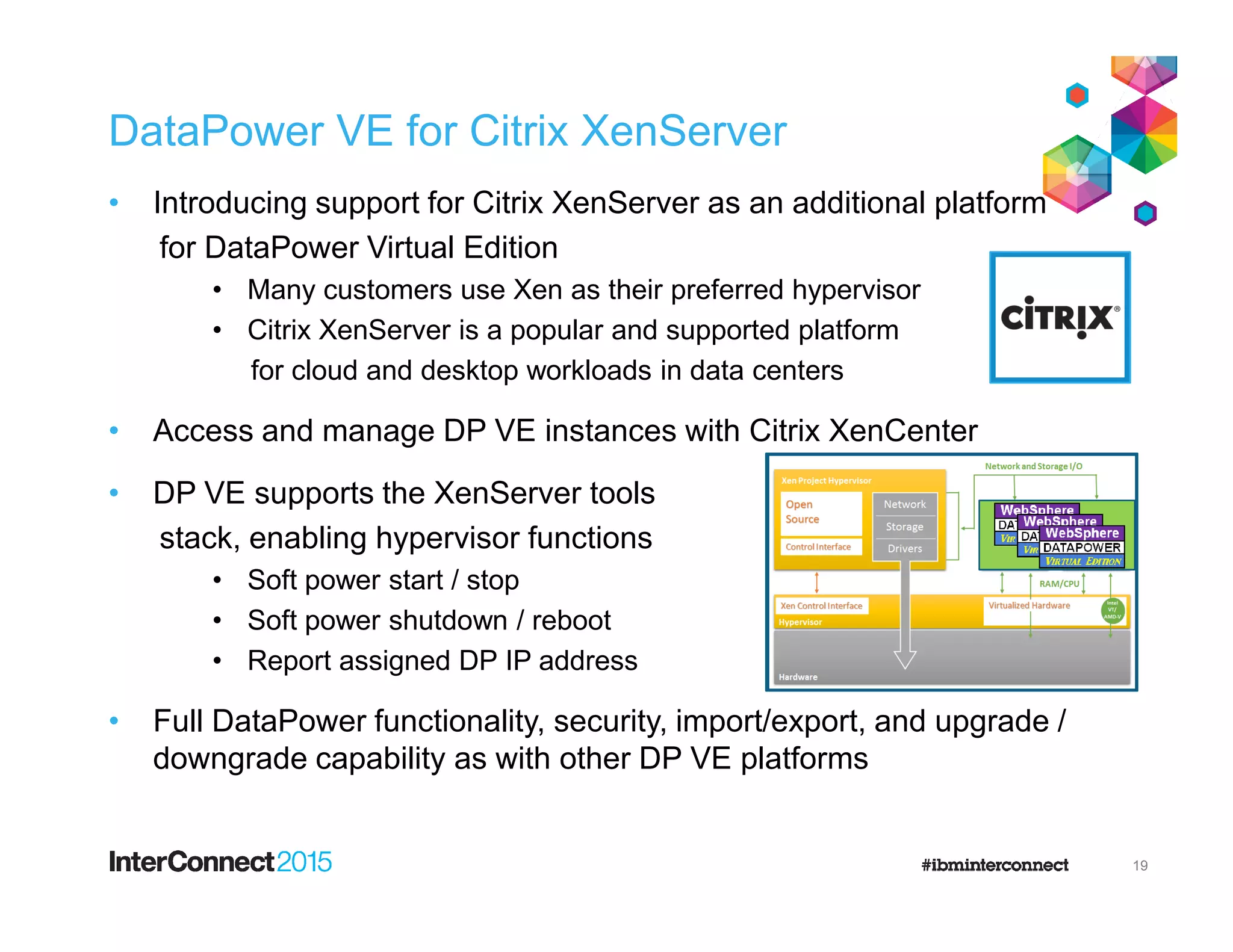
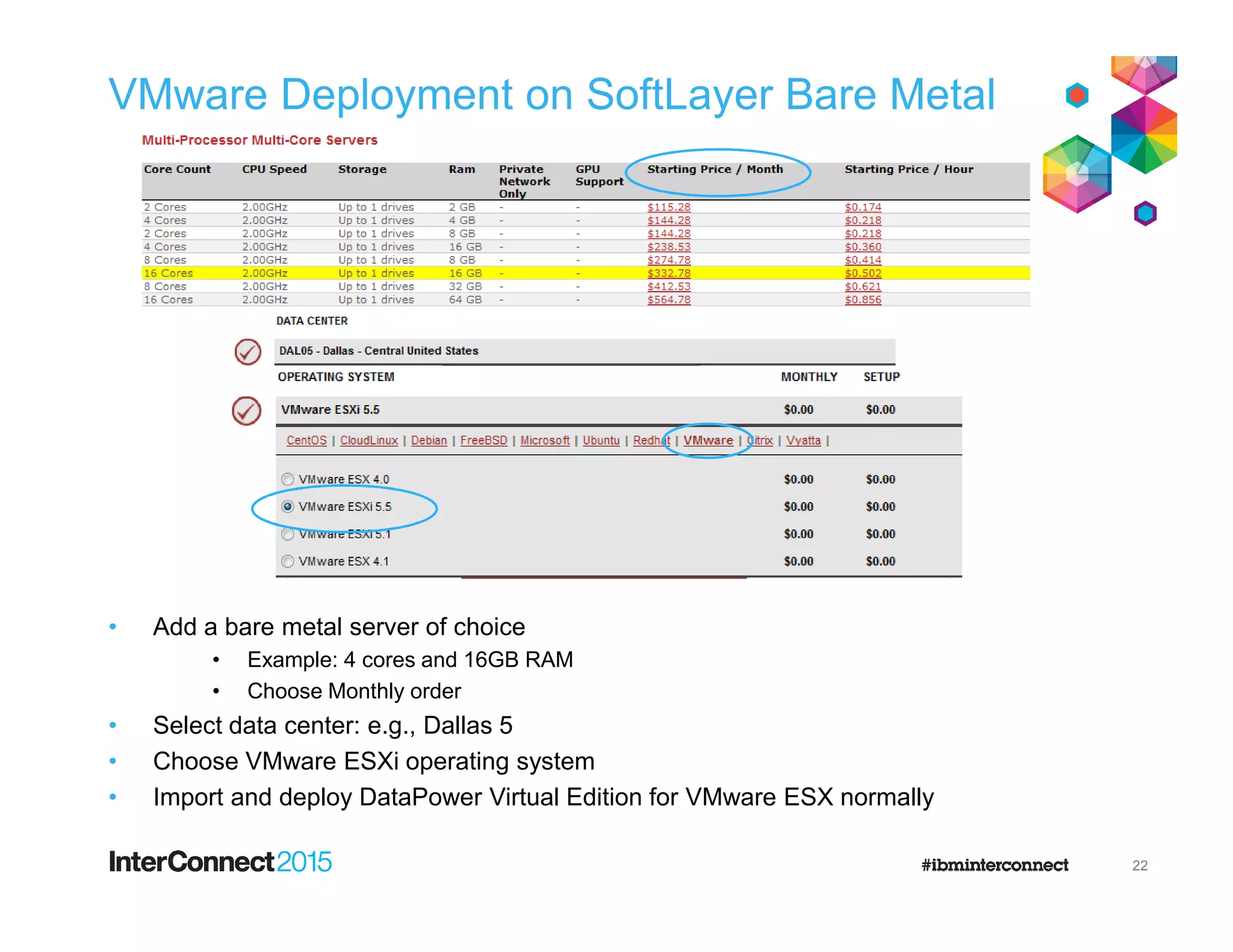
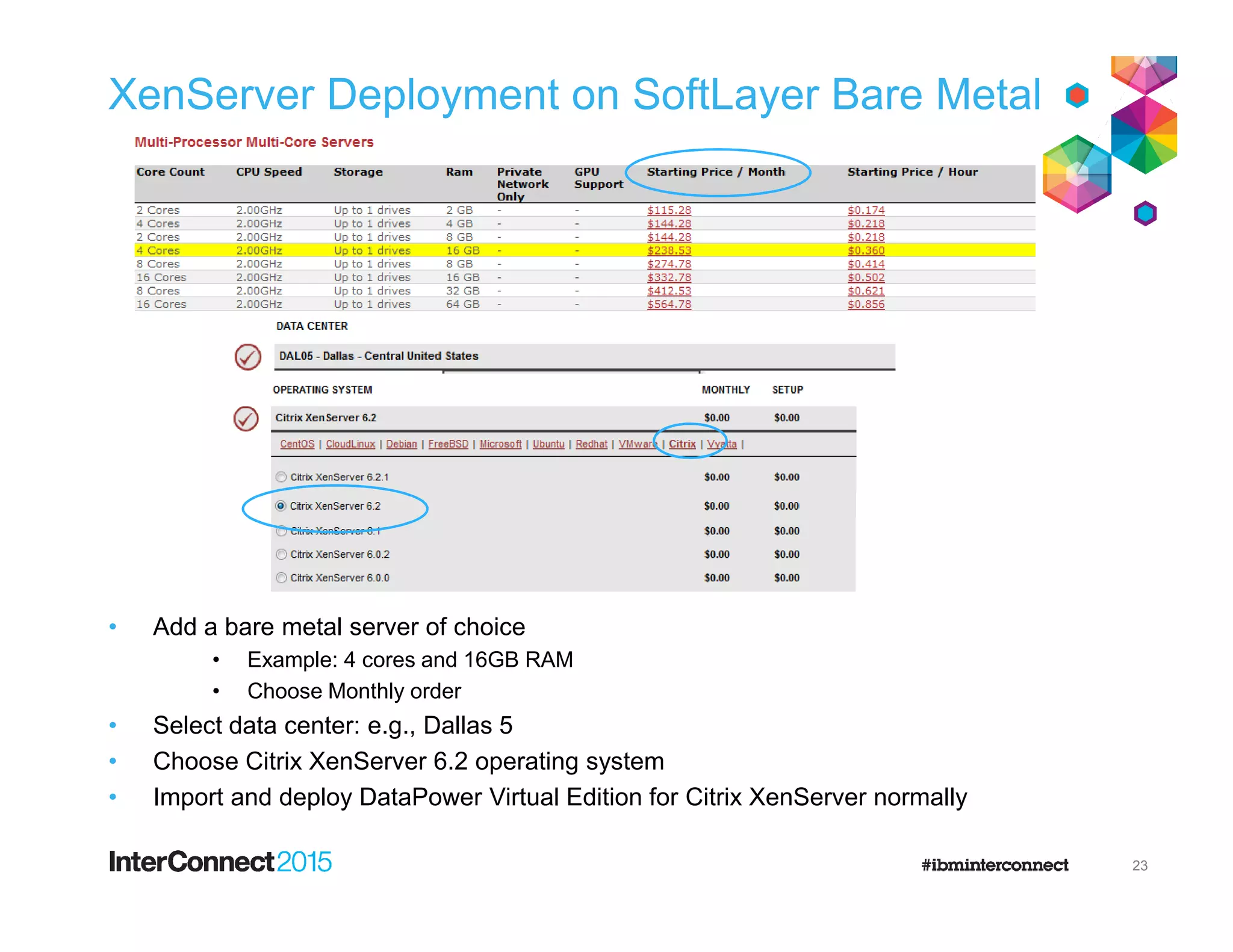
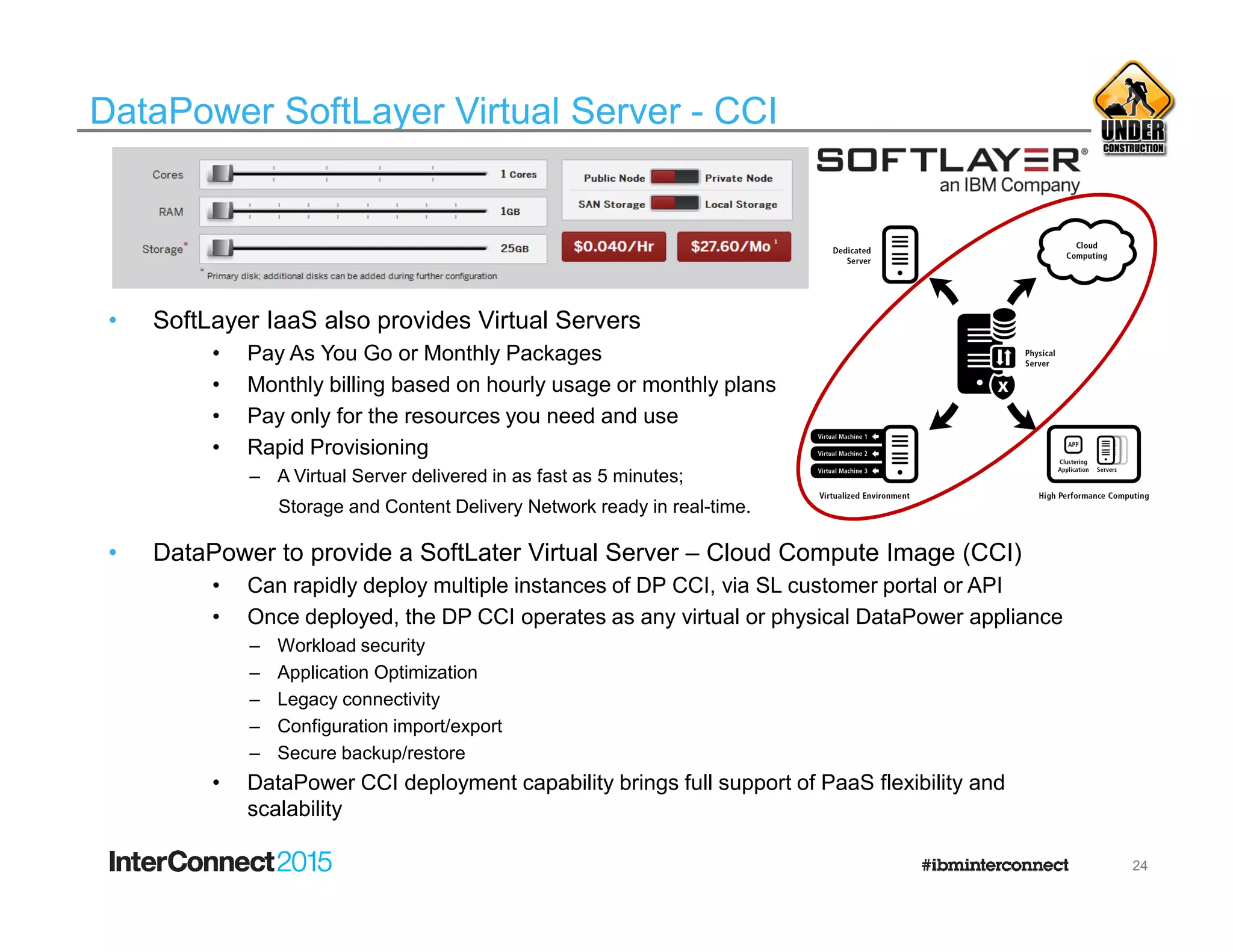
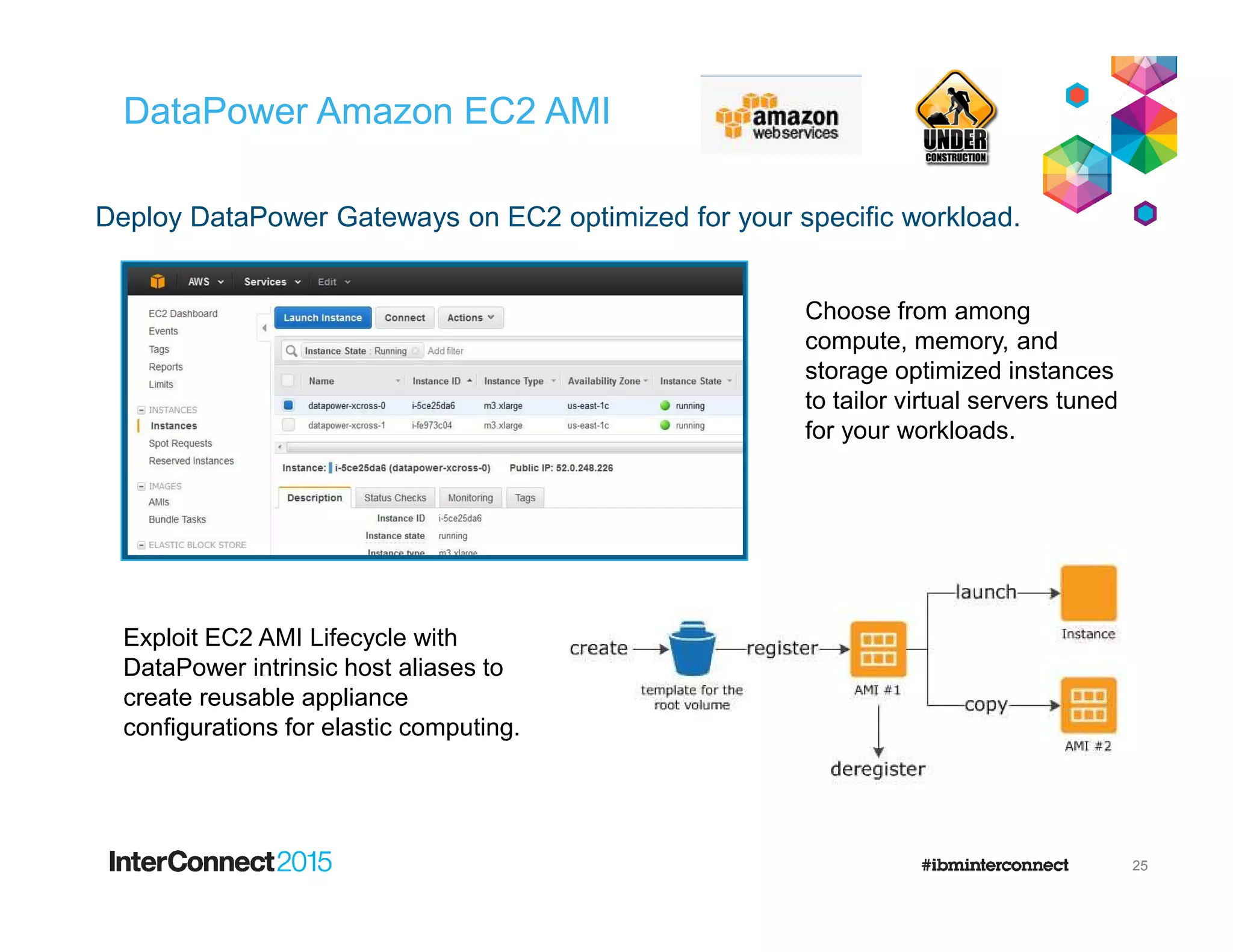
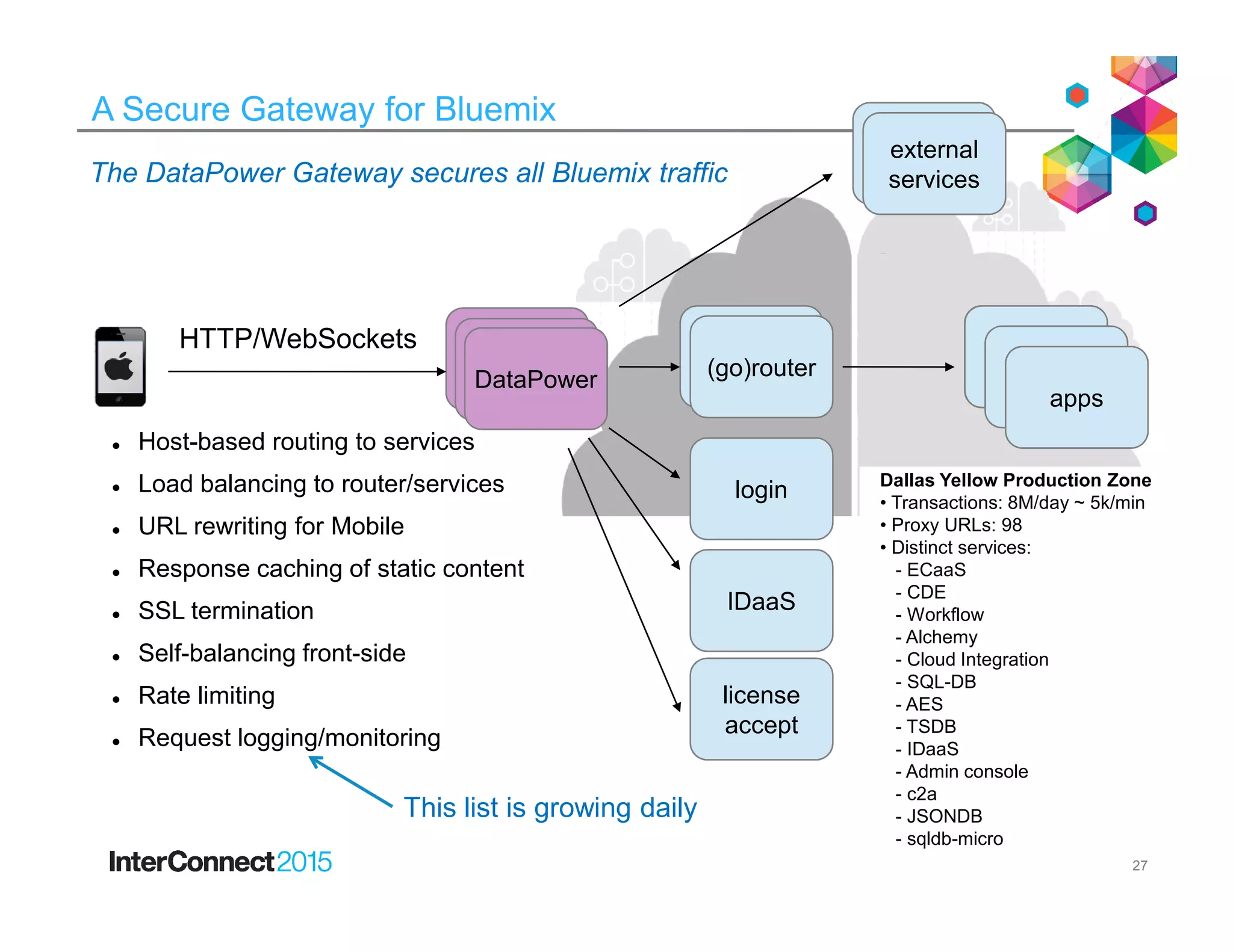
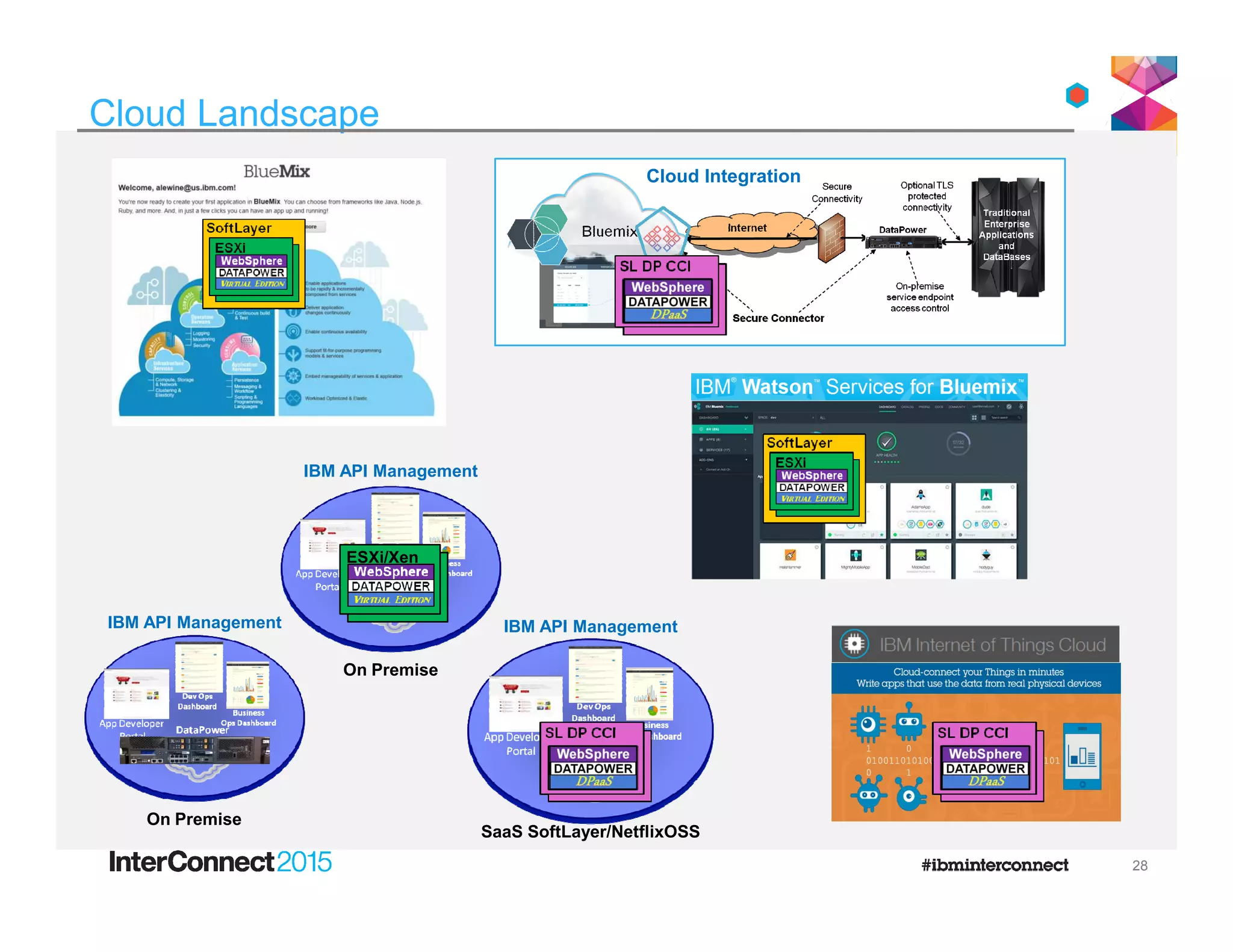
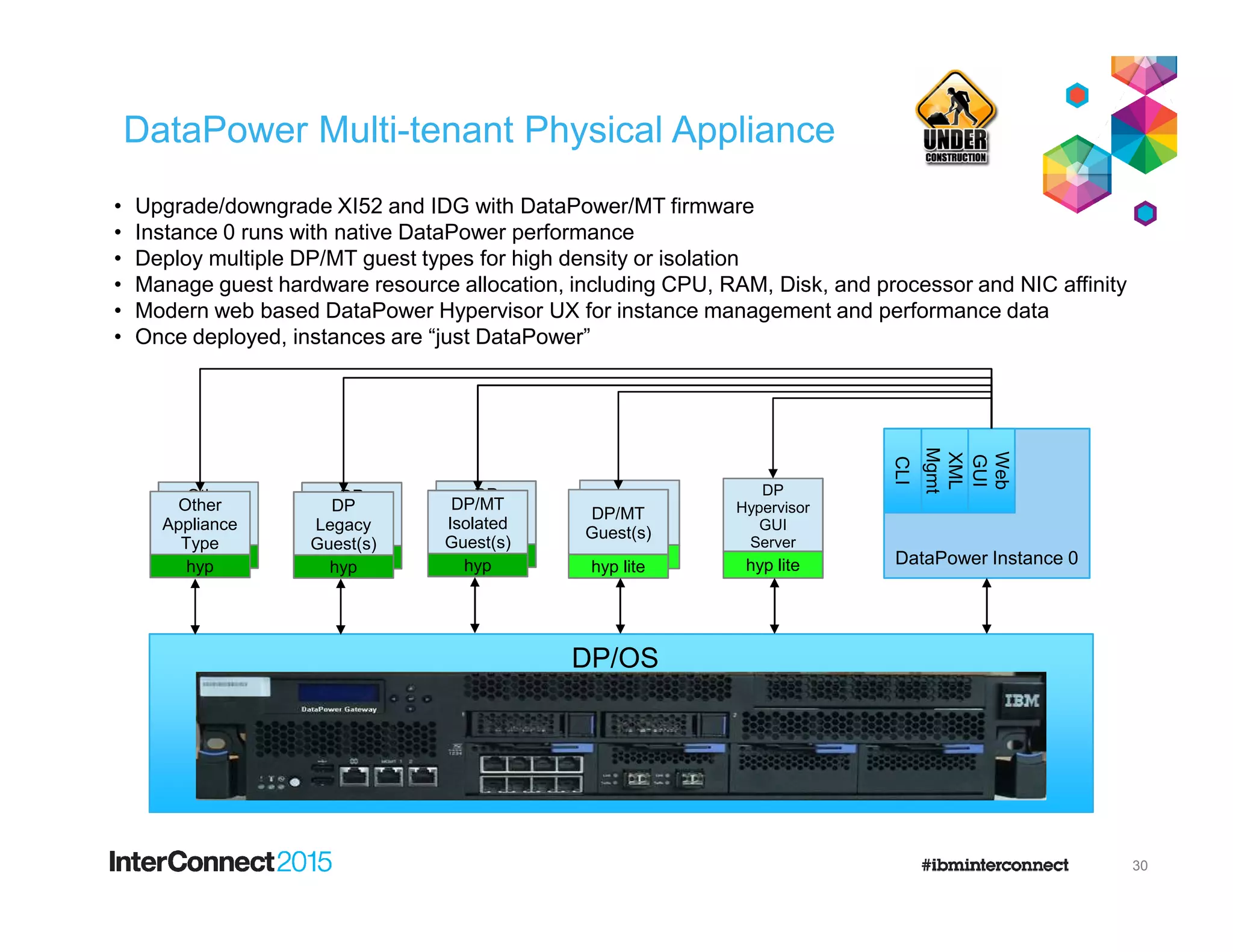
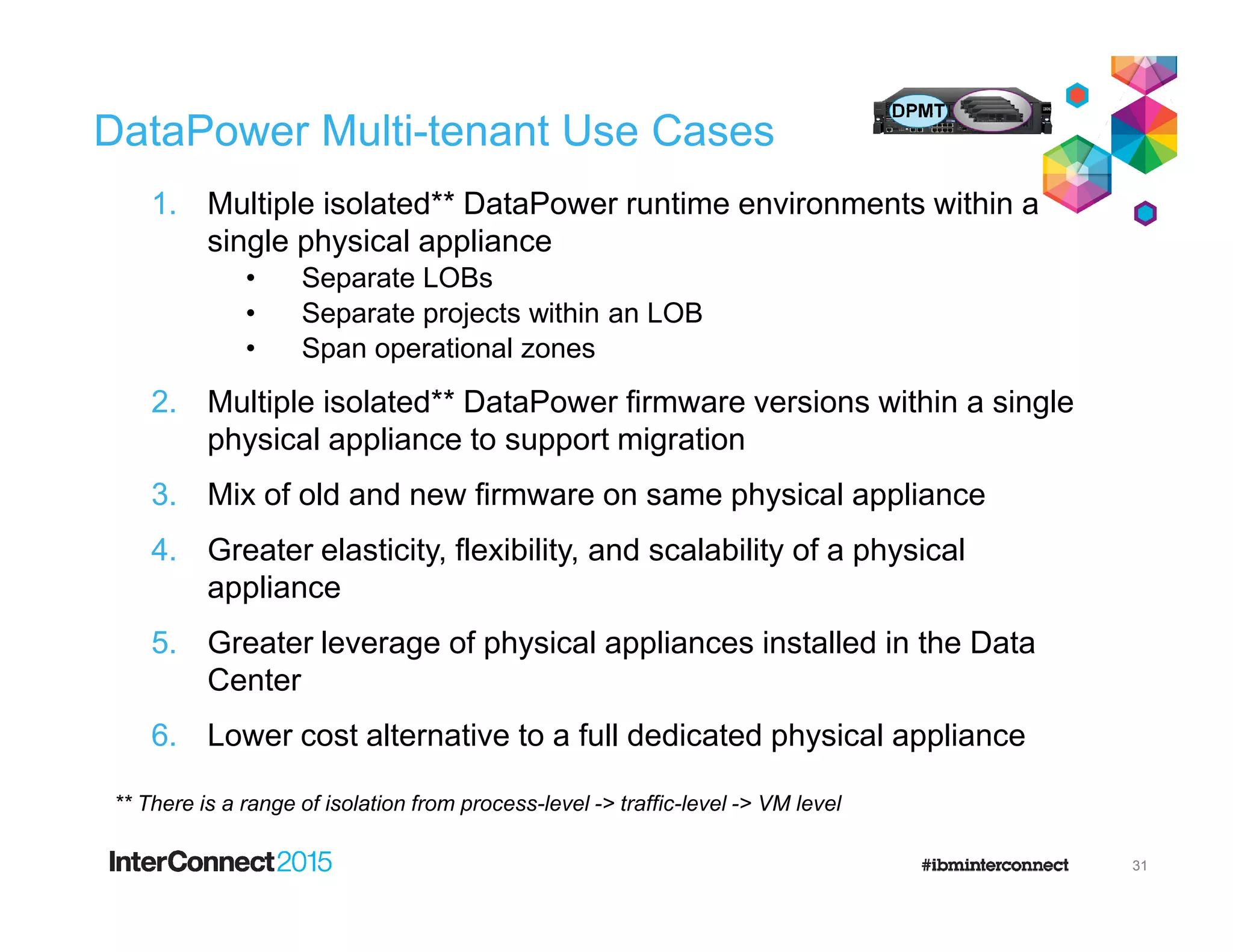
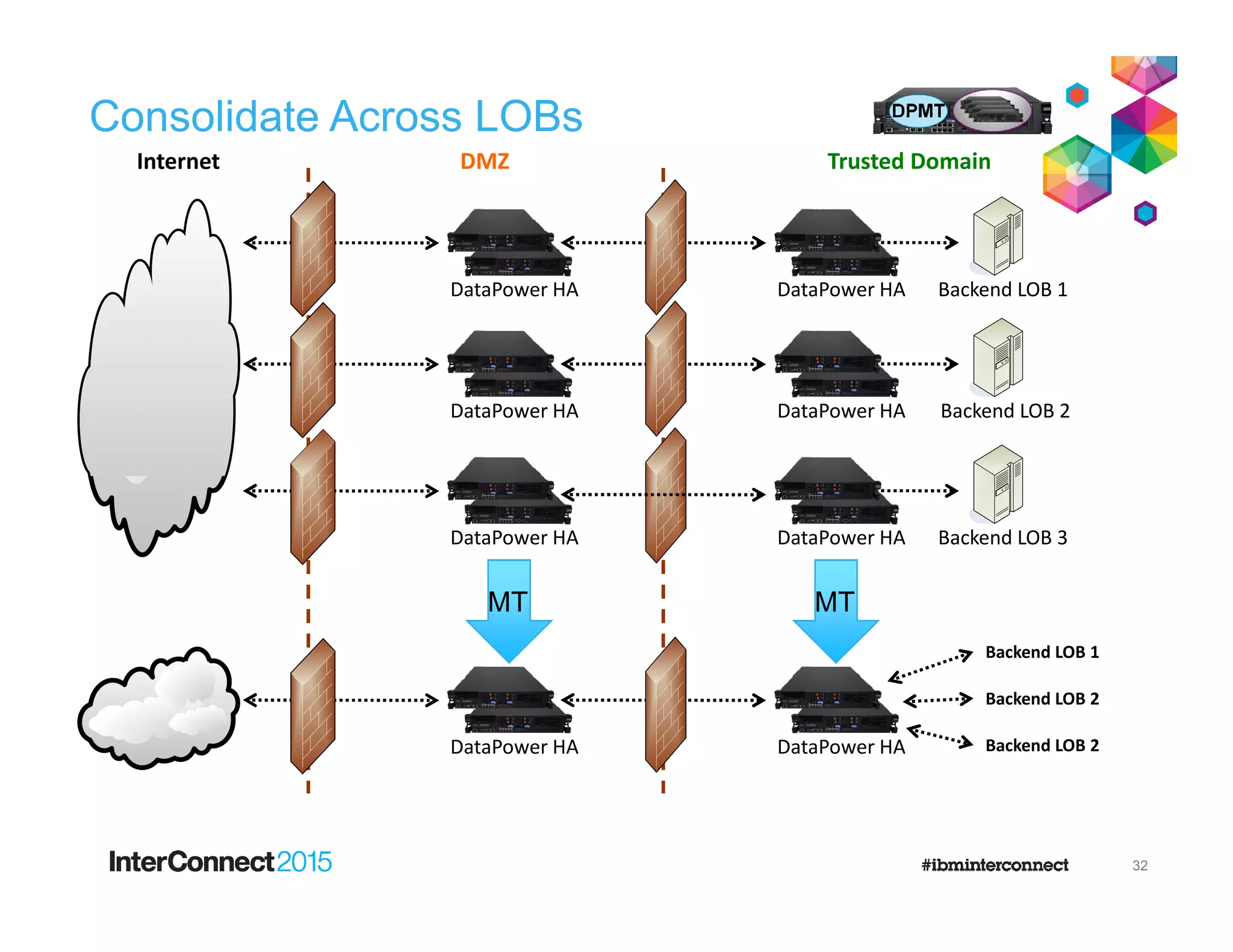
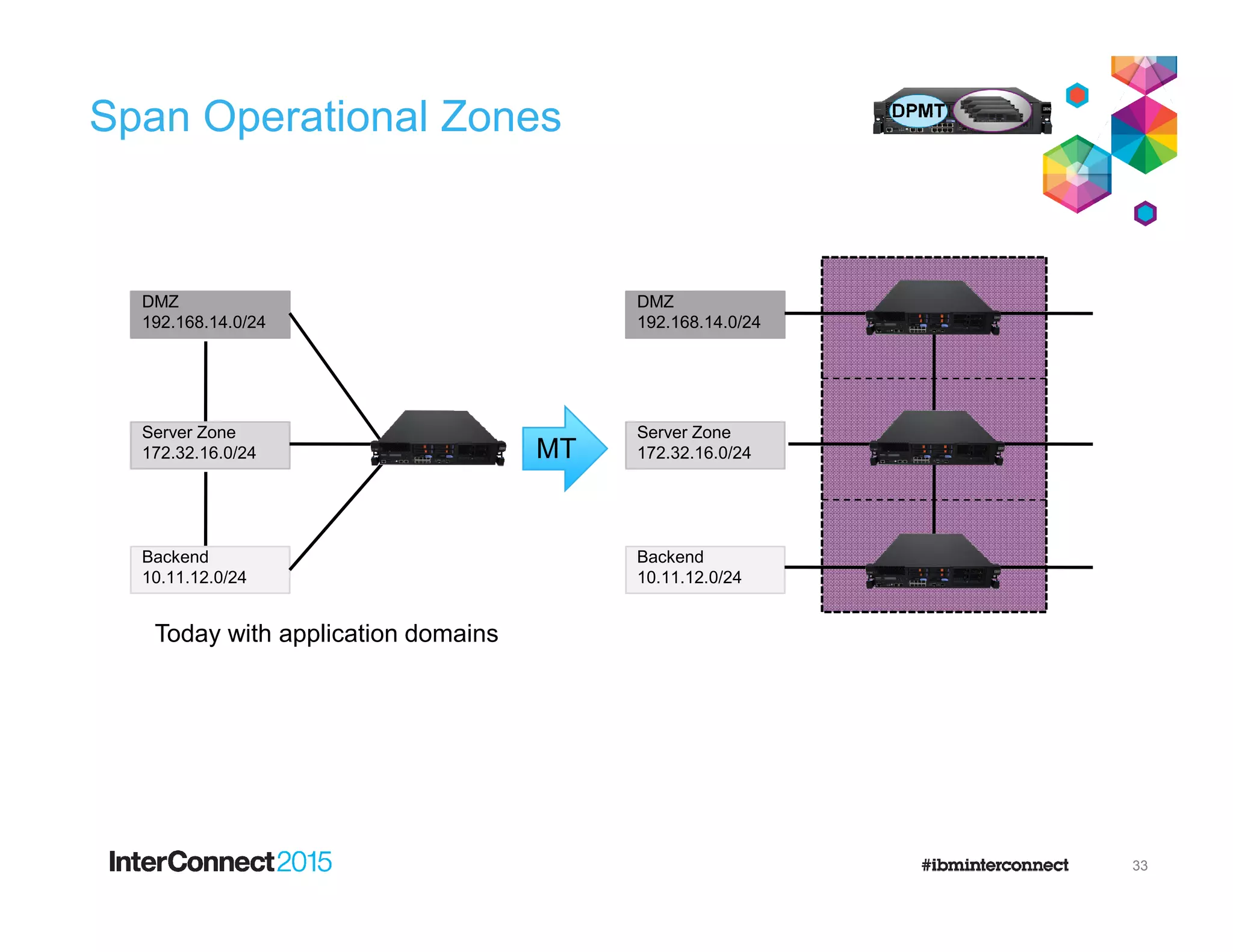
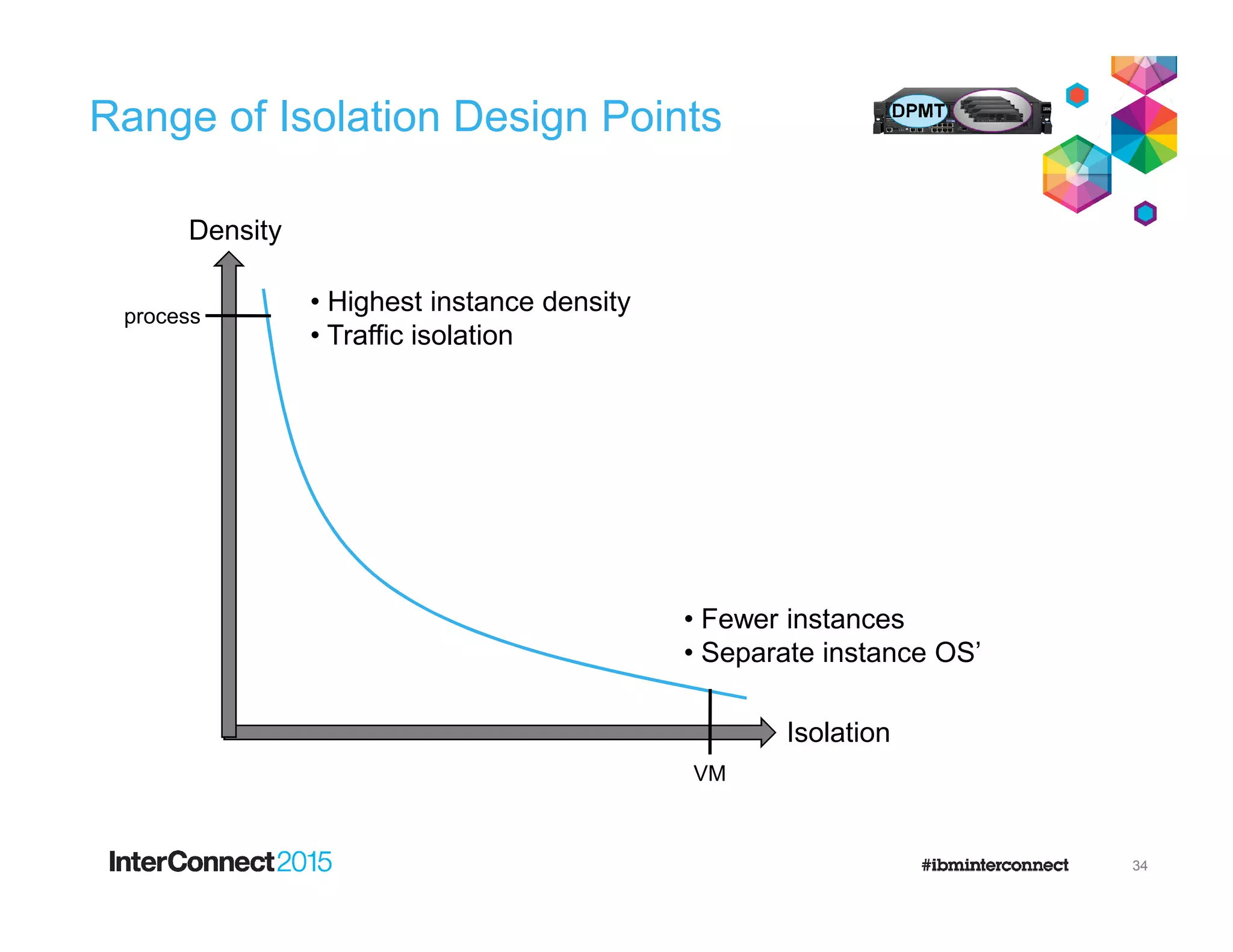
The document discusses IBM's DataPower Virtual Editions, which provide the functionality of IBM's DataPower gateway appliances in a virtualized format. Key points include:
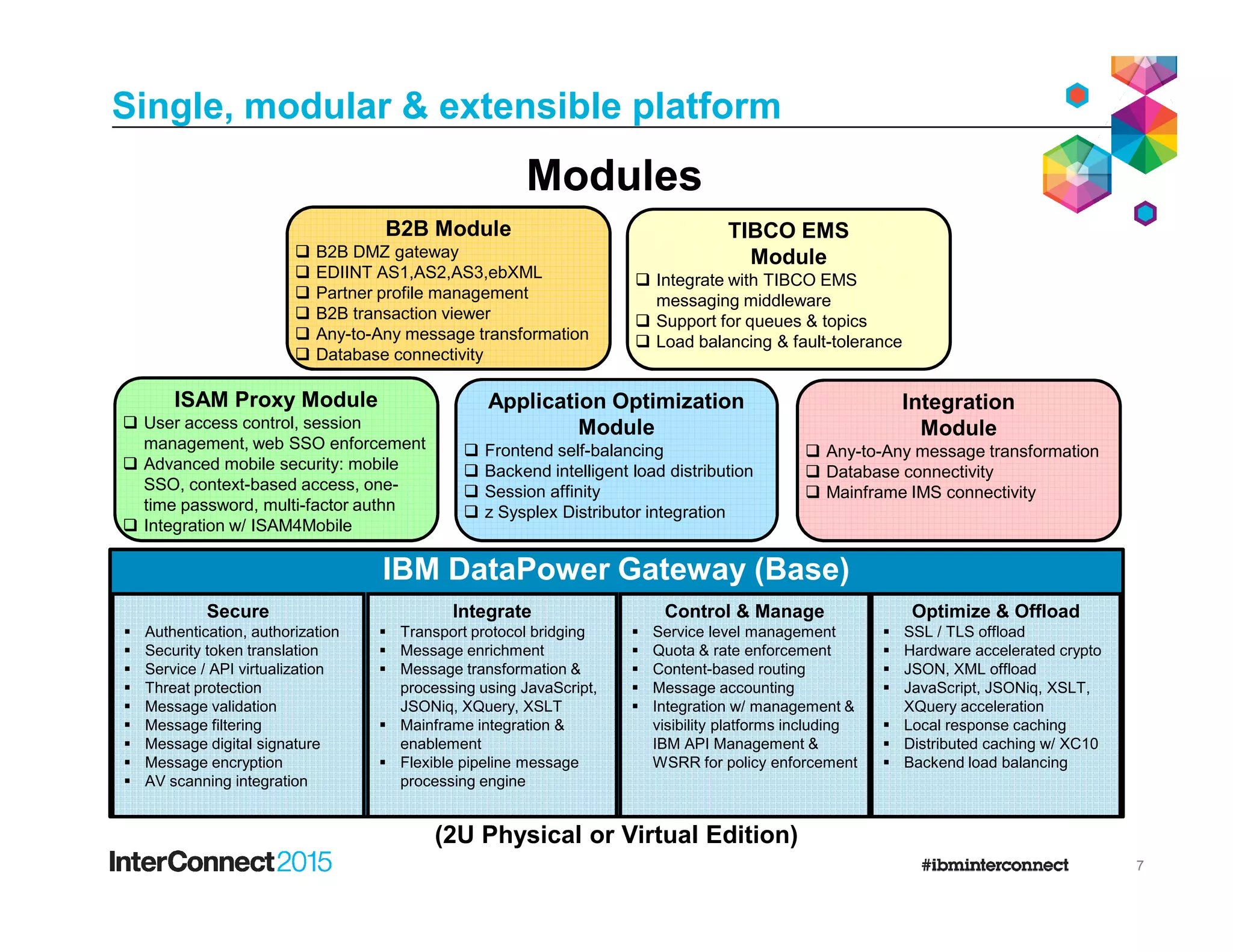
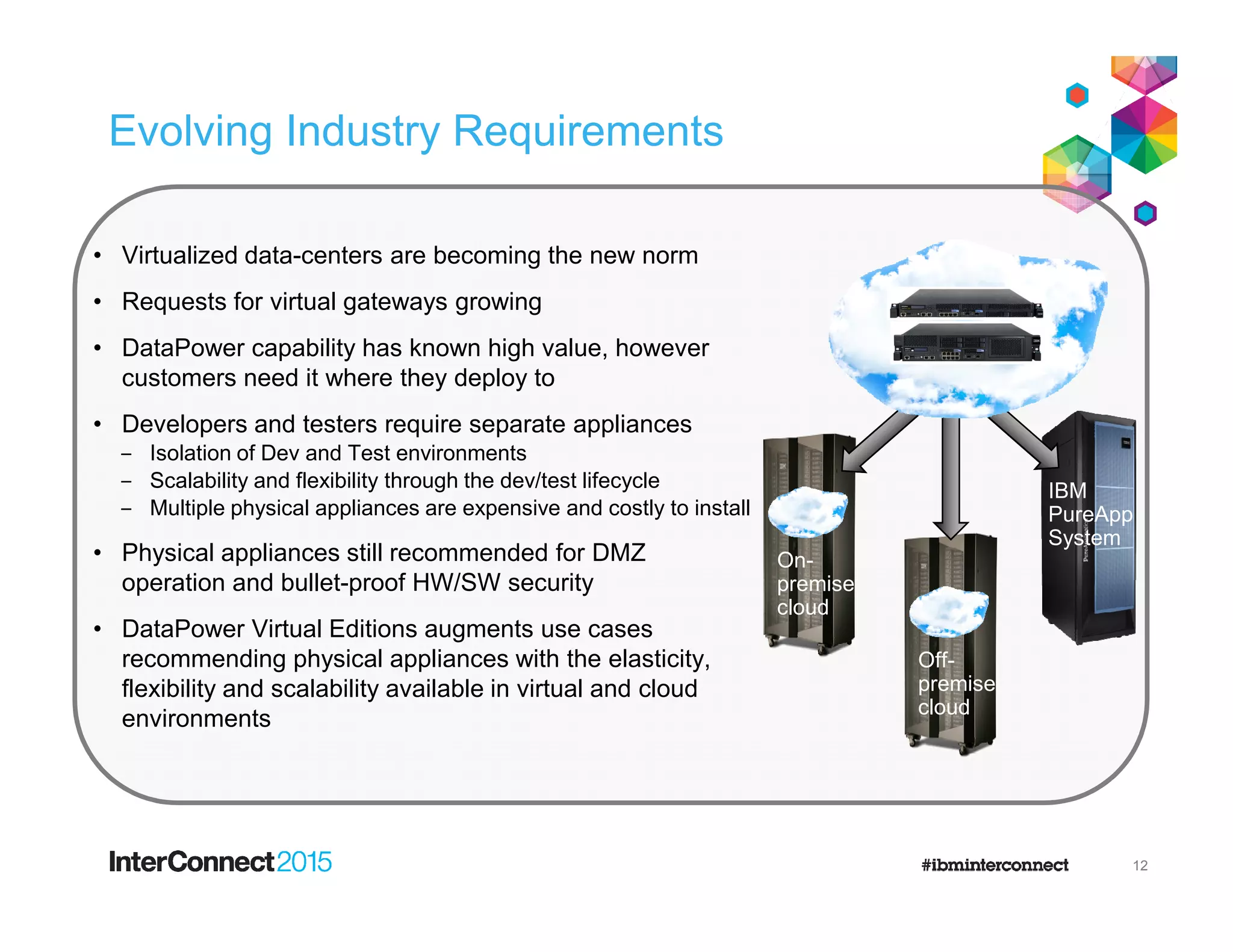
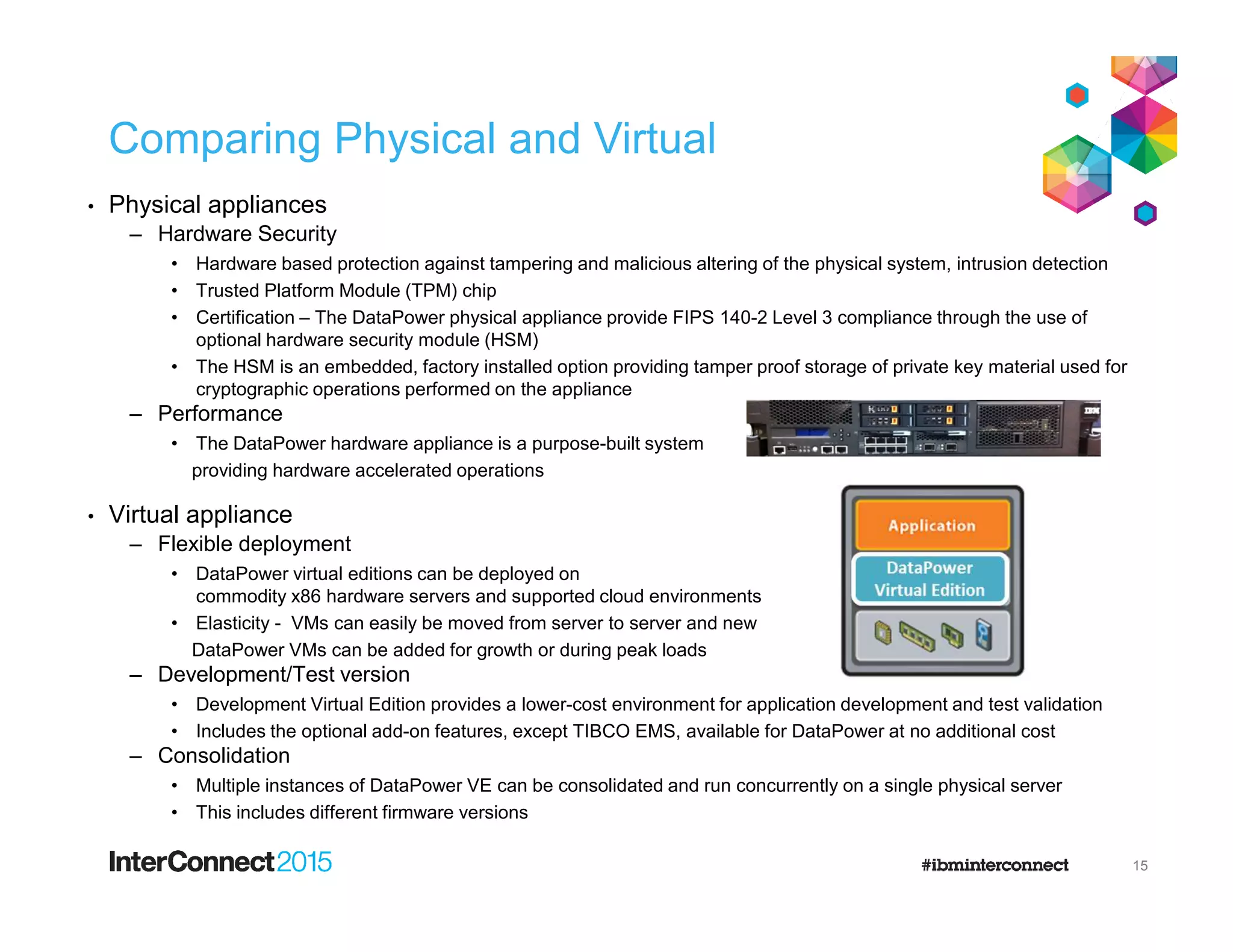
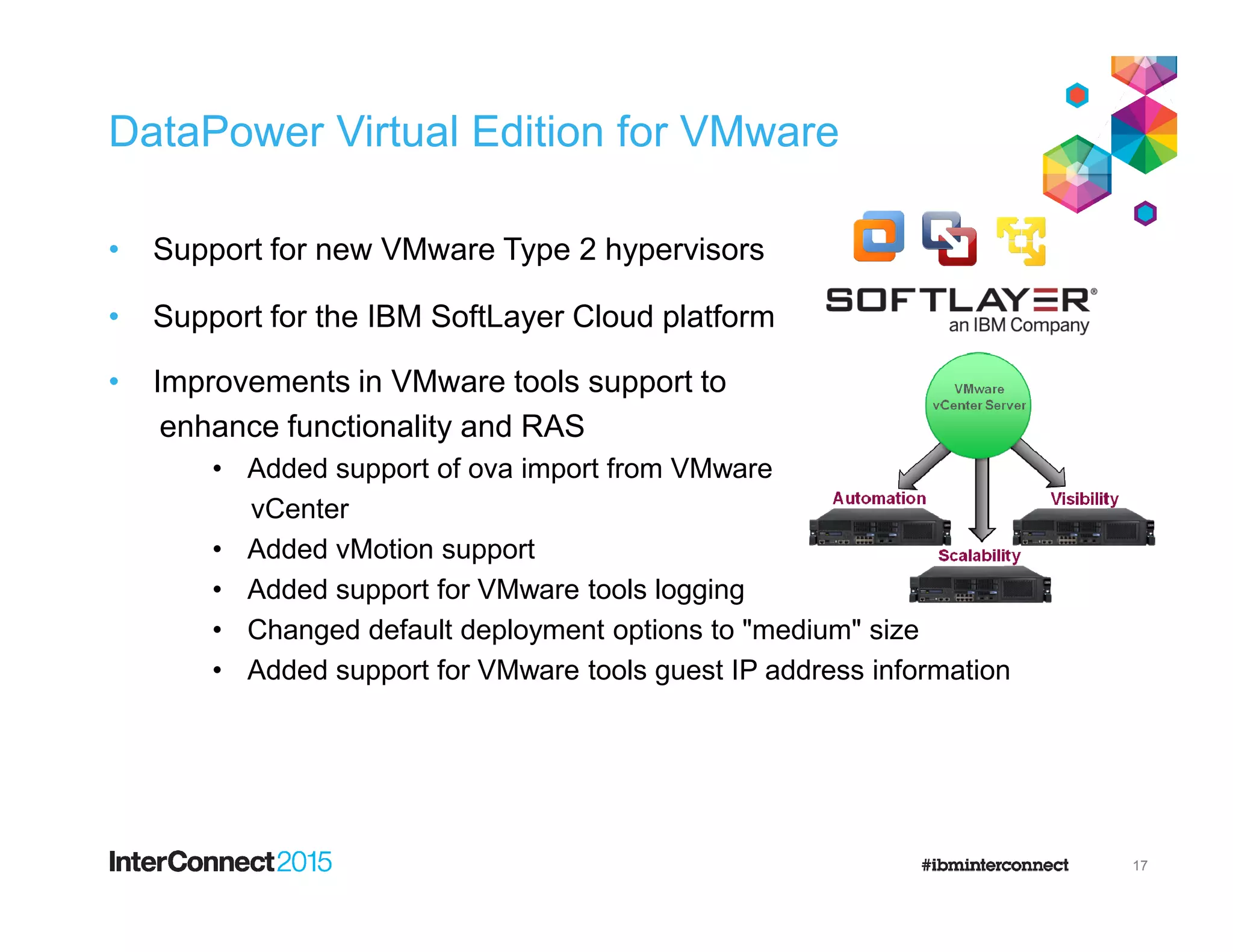
- DataPower Virtual Editions can be deployed on VMware, Citrix XenServer, and IBM SoftLayer bare metal servers, providing flexibility compared to physical appliances.
- Functionality remains the same between physical and virtual appliances, though some hardware-dependent features are not supported virtually.
- New versions add support for additional hypervisors and platforms like VMware Workstation and Fusion to aid development and testing.