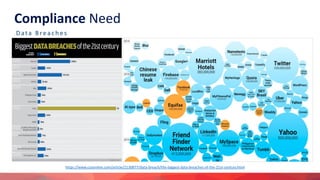
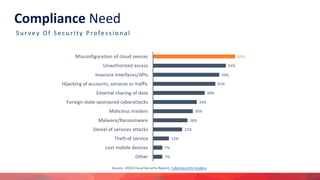
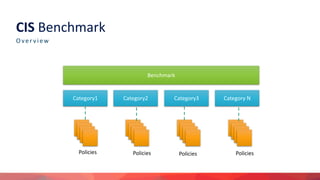
Rahul Khengare gave a presentation on the CIS Security Benchmark to the DevOps-Pune Meetup Group. The agenda included an introduction to the CIS Benchmark, a discussion of the need for compliance, and a demonstration of automation tools. The CIS Benchmark provides consensus-based security configuration guides for technologies including cloud platforms, operating systems, containers, and SaaS products. It defines policies across categories such as identity and access management, logging, and networking. Open source tools like Prowler and Cloudneeti can be used to automate compliance checks against the CIS Benchmark.